Abstract
We consider the question of constructing pseudorandom generators that simultaneously have linear circuit complexity (in the output length), exponential security (in the seed length), and a large stretch (linear or polynomial in the seed length). We refer to such a pseudorandom generator as an asymptotically optimal PRG. We present a simple construction of an asymptotically optimal PRG from any one-way function f:{0,1}n → {0,1}n which satisfies the following requirements:
1. f can be computed by linear-size circuits;
2. f is 2βn-hard to invert for some constant β > 0, and the min-entropy of f(x) on a random input x is at least γn for a constant γ > 0 such that β/3 + γ > 1.
Alternatively, building on the work of Haitner, Harnik and Reingold (SICOMP 2011), one can replace the second requirement by:
2 ′ . f is 2βn-hard to invert for some constant β > 0 and it is regular in the sense that the preimage size of every output of f is fixed (but possibly unknown).
Previous constructions of PRGs from one-way functions can do without the entropy or regularity requirements, but even the best such constructions achieve slightly sub-exponential security (Vadhan and Zheng, STOC 2012).
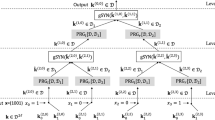
Our construction relies on a technical result about hardcore functions that may be of independent interest. We obtain a family of hardcore functions \(\mathcal H = \{h:\{0,1\}^n\to\{0,1\}^{\alpha n}\}\) that can be computed by linear-sized circuits for any 2βn-hard one-way function f:{0,1}n → {0,1}n where β > 3α. Our construction of asymptotically optimal PRGs uses such hardcore functions, which can be obtained via linear-size computable affine hash functions (Ishai, Kushilevitz, Ostrovsky and Sahai, STOC 2008).
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Alekhnovich, M.: More on average case vs approximation complexity. In: Proc. FOCS 2003, pp. 298–307 (2003)
Alekhnovich, M., Hirsch, E.A., Itsykson, D.: Exponential lower bounds for the running time of DPLL algorithms on satisfiable formulas. J. Autom. Reasoning. 35(1-3), 51–72 (2005)
Applebaum, B.: Pseudorandom Generators with Long Stretch and Low Locality from Random Local One-Way Functions. In: Proc. STOC 2012, pp. 805–816 (2012)
Applebaum, B., Bogdanov, A., Rosen, A.: A Dichotomy for Local Small-Bias Generators. In: Cramer, R. (ed.) TCC 2012. LNCS, vol. 7194, pp. 600–617. Springer, Heidelberg (2012)
Applebaum, B., Ishai, Y., Kushilevitz, E.: Cryptography in NC0. SIAM J. on Computing 36(4), 845–888 (2006)
Applebaum, B., Ishai, Y., Kushilevitz, E.: On Pseudorandom Generators with Linear Stretch in NC0. J. Comp. Compl. 17(1), 38–69 (2008)
Blum, M., Micali, S.: How to Generate Cryptographically Strong Sequences of Pseudo-Random Bits. SIAM J. on Computing 13(4), 850–864 (1985)
Bogdanov, A., Qiao, Y.: On the Security of Goldreich’s One-Way Function. In: Dinur, I., Jansen, K., Naor, J., Rolim, J. (eds.) APPROX and RANDOM 2009. LNCS, vol. 5687, pp. 392–405. Springer, Heidelberg (2009)
Cook, J., Etesami, O., Miller, R., Trevisan, L.: Goldreich’s One-Way Function Candidate and Myopic Backtracking Algorithms. In: Reingold, O. (ed.) TCC 2009. LNCS, vol. 5444, pp. 521–538. Springer, Heidelberg (2009)
Cook, J., Etesami, O., Miller, R., Trevisan, L.: On the One-Way Function Candidate Proposed by Goldreich. ECCC, Report No. 175 (2012)
Cryan, M., Miltersen, P.B.: On Pseudorandom Generators in NC0. In: Sgall, J., Pultr, A., Kolman, P. (eds.) MFCS 2001. LNCS, vol. 2136, pp. 272–284. Springer, Heidelberg (2001)
Goldreich, O.: Candidate One-Way Functions Based on Expander Graphs. ECCC, Report No. 90 (2000)
Goldreich, O.: Foundations of Cryptography. Cambridge U. Press, Cambridge (2001)
Goldreich, O., Krawczyk, H., Luby, M.: On the Existence of Pseudorandom Generators. SIAM J. on Computing 22(6), 1163–1175 (1993)
Goldreich, O., Levin, L.A.: Hard-core Predicates for any One-Way Function. In: Proc. STOC 1989, pp. 25–32 (1989)
Haitner, I.: New Implications and Improved Efficiency of Constructions Based on One-way Functions. Ph.D. Thesis (March 2008)
Haitner, I., Harnik, D., Reingold, O.: Efficient Pseudorandom Generators from Exponentially Hard One-Way Functions. In: Bugliesi, M., Preneel, B., Sassone, V., Wegener, I. (eds.) ICALP 2006. LNCS, vol. 4052, pp. 228–239. Springer, Heidelberg (2006)
Haitner, I., Harnik, D., Reingold, O.: On the Power of the Randomized Iterate. In: Dwork, C. (ed.) CRYPTO 2006. LNCS, vol. 4117, pp. 22–40. Springer, Heidelberg (2006)
Haitner, I., Harnik, D., Reingold, O.: On the Power of the Randomized Iterate. SIAM J. on Computing 40(6), 1486–1528 (2011)
Haitner, I., Reingold, O., Vadhan, S.: Efficiency Improvements in Constructing Pseudorandom Generators from One-way Functions. In: Proc. STOC 2010, pp. 437–446 (2010)
Hastad, J., Impagliazzo, R., Levin, L.A., Luby, M.: A Psedorandom Generator From Any One-Way Function. SIAM J. on Computing 28(4), 1364–1396 (1999)
Holenstein, T.: Pseudorandom Generators from One-Way Functions: A Simple Construction for Any Hardness. In: Halevi, S., Rabin, T. (eds.) TCC 2006. LNCS, vol. 3876, pp. 443–461. Springer, Heidelberg (2006)
Holenstein, T., Maurer, U., Sjödin, J.: Complete Classification of Bilinear Hard-Core Functions. In: Franklin, M. (ed.) CRYPTO 2004. LNCS, vol. 3152, pp. 73–91. Springer, Heidelberg (2004)
Impagliazzo, R., Levin, L.A., Luby, M.: Pseudo-Random Generation From One-Way Functions (Extended Abstract). In: Proc. STOC 1989, pp. 12–24 (1989)
Ishai, Y., Kushilevitz, E., Ostrovsky, R., Sahai, A.: Cryptography with Constant Computational Overhead. In: Proc. STOC 2008, pp. 433–442 (2008)
Mossel, E., Shpilka, A., Trevisan, L.: On epsilon-biased generators in NC0. Random Struct. Algorithms 2(1), 56–81 (2006)
Näslund, M.: Universal Hash Functions & Hard Core Bits. In: Guillou, L.C., Quisquater, J.-J. (eds.) EUROCRYPT 1995. LNCS, vol. 921, pp. 356–366. Springer, Heidelberg (1995)
Panjwani, S.K.: An experimental evaluation of goldreich’s one-way function. Technical report, IIT, Bombay (2001)
Vadhan, S., Zheng, C.J.: Characterizing Pseudoentropy and Simplifying Pseudorandom Generator Constructions. In: Proc. STOC 2012, pp. 817–836 (2012)
Yao, A.C.: Theory and application of trapdoor functions. In: Proc. FOCS 1982, pp. 80–91 (1982)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2013 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Baron, J., Ishai, Y., Ostrovsky, R. (2013). On Linear-Size Pseudorandom Generators and Hardcore Functions. In: Du, DZ., Zhang, G. (eds) Computing and Combinatorics. COCOON 2013. Lecture Notes in Computer Science, vol 7936. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-38768-5_17
Download citation
DOI: https://doi.org/10.1007/978-3-642-38768-5_17
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-38767-8
Online ISBN: 978-3-642-38768-5
eBook Packages: Computer ScienceComputer Science (R0)