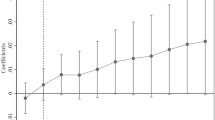
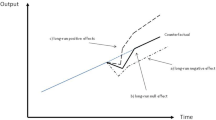
Abstract
Although there are some studies on inter-sectoral information security interdependency, the lack of regional interdependency analysis is one of their limitations. In this empirical study, we used an inter-regional input–output table in order to analyze both sectoral and regional interdependencies under the influence of information technology and the information security of Japanese firms. Our analysis showed that the economic scale of a region has a great influence on the characteristics of the interdependency. Furthermore, we found that the demand-side sectors can be classified into five classes based on the characteristics. Among them, the groups with high self-dependency get more benefits from simultaneous understanding of regional characteristics; for the sectors in these classes, investment advice obtained from sectoral characteristics only is very limited, whereas they can obtain much more from regional characteristics. Since these classes include a majority of the sectors, we can recognize the importance of regional interdependency analysis. In the above basic study, what we see is the situation before the Great East Japan Earthquake on March 11, 2011.As an extended study, we estimated the impact of the earthquake on the interdependency. Our main finding from the regional perspective is that the interdependency characteristics of the most damaged region (Tohoku) and of the economically largest region (Kanto) are impacted most significantly. This feature is not changed by the limitation of damage through prior security investment.Both in the basic study and in the extended study, we can see that considering not only sectoral but also regional characteristics is an effective approach to the task of empirically deriving implications related to the interdependency. There are many possibilities of more extended studies based on our methodology.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
In our raw result, the average mean value of ISBD is 0.00754 %. By considering this mean value and the standard deviation, we set the threshold.
References
Anderson, R., Moore, T.: The economics of information security. Science 314(5799), 610–613 (2006)
Aoyama, Y., Ratick, S.J.: Trust, transactions, and information technologies in the U.S. logistics industry. Econ. Geogr. 83(2), 159–180 (2007)
Bandyopadhyay, T., Jacob, V., Raghunathan, S.: Information security in networked supply chains: impact of network vulnerability and supply chain integration on incentives to invest. Inf. Technol. Manage. 11(1), 7–23 (2010)
Boot, A.W.A., Marinc, M.: The evolving landscape of banking. Ind. Corpor. Change 17(6), 1173–1203 (2008)
Cabineet Office, Government of Japan: Gross capital stock by industry. Available via DIALOG. http://www.esri.cao.go.jp/jp/sna/sonota/minkan/kekka/20110107/h21y_stock_all.xls (2009)
Cabinet Office, Government of Japan: Special Cabinet Meeting Material on Monthly Economic Report due to the Earthquake. Available via DIALOG. http://www5.cao.go.jp/keizai3/getsurei-s/1103.pdf (2011)
Dedrick, J., Kraemer, K.L.: The impacts of IT on firm and industry structure: the personal computer industry. Calif. Manage. Rev. 47(3), 122–142 (2005)
Dietzenbacher, E., Linder, J.A.: Sectoral and spatial linkages in the EC production structure. J. Reg. Sci. 37(2), 235–257 (1997)
Fearon, C., Philip, G.: An empirical study of the use of EDI in supermarket chains using a new conceptual framework. J. Inf. Technol. 14(1), 3–21 (1999)
Fearon, C., Philip, G.: Measuring success of electronic trading in the insurance industry: operationalising the disconfirmation of expectations paradigm. Behav. Inf. Technol. 27(6), 483–493 (2008)
Gordon, L.A., Loeb, M.P., Lucyshyn, W., Richardson, R.: 2005 CSI/FBI Computer crime and security survey. Available via DIALOG. http://www.cpppe.umd.edu/Bookstore/Documents/2005CSISurvey.pdf (2005)
Haimes, Y.Y., Jiang, P.: Leontief-based model of risk in complex interconnected infrastructures. Int. J. Netw. Virtual Organ. 4(3), 130–144 (2001)
Haimes, Y.Y., Horowitz, B.M., Lambert, J.H., Santos, J.R., Crowther, K., Lian, C.: Inoperability input–output model for interdependent infrastructure sectors. II: Case studies. J. Infrastruct. Syst. 11(2), 80–92 (2005)
Haimes, Y.Y., Horowitz, B.M., Lambert, J.H., Santos, J.R., Lian, C., Crowther, K.G.: Inoperability input–output model for interdependent infrastructure sectors. I: Theory and methodology. J. Infrastruct. Syst. 11(2), 67–79 (2005)
Han, K., Kauffman, R.J., Nault, B.R.: Information exploitation and interorganizational systems ownership. J. Manage. Inf. Syst. 21(2), 109–135 (2004)
Hausken, K.: Income, Interdependence, and substitution effects affecting incentives for security investment. J. Account. Public Policy 25(6), 629–665 (2006)
King, J.L., Lyytinen, K.: Automotive Informatics: Information Technology and Enterprise Transformation in the Automobile Industry. Transforming Enterprise: The Economic and Social Implications of Information Technology, pp. 283–312. MIT, Cambridge (2005)
Klein, R., Rai, A.: Interfirm Strategic Information Flows in Logistics Supply Chain Relationships. Manage. Inf. Syst. Q. 33(4), 735–762 (2009)
Kunreuther, H., Heal, G.: Interdependent security. J. Risk Uncertain. 26(2–3), 231–249 (2003)
Ministry of Economic, Trade and Industry: Inter-regional input–output tables 2005. Available via DIALOG. http://www.meti.go.jp/statistics/tyo/tiikiio/result/result_02.html (2005)
Ministry of Economic, Trade and Industry: The 2006 Survey of Information Technology. Available via DIALOG. http://www.meti.go.jp/statistics/zyo/zyouhou/result-2/h18jyojitsu.html (2007)
Office of the Manager, National Communications System: Supervisory Control and Data Acquisition (SCADA) Systems: Technical information bulletin 04-1, National communications system. Available via DIALOG. http://www.ncs.gov/library/tech_bulletins/2004/tib_04-1.pdf (2004)
Ogut, H., Menon, N., Raghunathan, S.: Cyber insurance and IT security investment: impact of interdependent risk. In: 4th Workshop on the Economics of Information Security (WEIS), Cambridge (2005)
Pierre, R., Timothy, D.: Modular strategies: B2B technology and architectural knowledge. Calif. Manage. Rev. 47(4), 86–113 (2005)
Research Institute of Economy, Trade and Industry: Japan industrial productivity database 2008. Available via DIALOG. http://www.rieti.go.jp/jp/database/JIP2008/index.html (2008)
Shinozaki, A., Yamamoto, Y., Yamazaki, S.: Technical papers on ICT related economics. No. 11-1: Estimation on the amount of damage on ICT-related capital stock. Available via DIALOG. http://www.icr.co.jp/ICT/report/TP_201106.pdf (2011)
Tanaka, H.: Geography and information security: does location affect information security effort? In: Fourth Forum on Financial Systems and Cyber Security: A Public Policy Perspective, Smith School of Business, University of Maryland (2007)
Tanaka, H.: Quantitative analysis of information security interdependency between industrial sectors. In: Proceedings of the 3rd International Symposium on Empirical Software Engineering and Measurement, Lake Buena Vista, pp. 574–583 (2009)
The Institute for Information Infrastructure Protection (I3P): Security Solution for the Oil and Gas Industry, Technology Fact Sheet. Inoperability input–output model (IIM). Available via DIALOG. http://www.dartmouth.edu/~i3p/docs/publications/IIM-factsheet-Feb2007.pdf (2007)
Acknowledgements
We would like to express our sincere gratitude to the Volkswagen Foundation for their kind support with a travel grant to attend the Workshop on the Economics of Information Security (WEIS 2012) in Berlin. We would like to also thank the anonymous reviewers for their valuable comments.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2013 Springer-Verlag Berlin Heidelberg
About this chapter
Cite this chapter
Jenjarrussakul, B., Tanaka, H., Matsuura, K. (2013). Sectoral and Regional Interdependency of Japanese Firms Under the Influence of Information Security Risks. In: Böhme, R. (eds) The Economics of Information Security and Privacy. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-39498-0_6
Download citation
DOI: https://doi.org/10.1007/978-3-642-39498-0_6
Published:
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-39497-3
Online ISBN: 978-3-642-39498-0
eBook Packages: Computer ScienceComputer Science (R0)