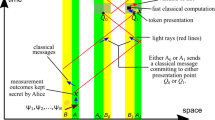
Abstract
A protocol is said to be device-independent when the level of its performance can be inferred without making any assumptions regarding the inner workings of the apparatus used to implement it. In this paper we introduce a device-independent weak coin flipping protocol based on a single GHZ test. Interestingly, the protocol calls for the exchange of (quantum) systems between participants; a feature which is not trivial to incorporate in a device-independent setting where a system’s behavior may depend on the time, location, and its history. Alice’s and Bob’s maximal cheating probabilities are given by \(\simeq 0.974\) and \(\cos ^2(\frac{\pi }{8}) \simeq 0.854\).
N. Aharon— Racah Institute of Physics, The Hebrew University of Jerusalem, Jerusalem 91904, Israel
A. Chailloux— SECRET Project Team, INRIA Paris-Recquencourt, 78153 Le Chesnay Cedex, France.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Barrett, J., et al.: Phys. Rev. Lett. 95, 010503 (2005)
Acín, A., et al.: Phys. Rev. Lett. 98, 230501 (2007)
Pironio, S., et al.: New J. Phys. 11, 045021 (2009)
McKague, M.: New J. Phys. 11, 103037 (2009)
Masanes, Ll., Pironio, S., Acín, A.: Nat. Commun. 2, 238 (2011)
Hanggi, E., Renner, R.: arXiv:1009.1833
Magniez, F., Mayers, D., Mosca, M., Ollivier, H.: Self-testing of quantum circuits. In: Bugliesi, M., Preneel, B., Sassone, V., Wegener, I. (eds.) ICALP 2006. LNCS, vol. 4051, pp. 72–83. Springer, Heidelberg (2006)
Acín, A., Gisin, N., Masanes, Ll.: Phys. Rev. Lett. 97, 120405 (2006)
Xu, F., et al.: New J. Phys. 12, 113026 (2010) arXiv:1005.2376 [quant-ph]
Lydersen, L., et al.: Nat. Photonics 4, 686 (2010)
Colbeck, R., Kent, A.: J. Phys. A: Math. Theor. 44, 095305 (2011)
Pironio, S., et al.: Nature 464, 1021 (2010)
Mayers, D., Yao, A.: Quantum Inform. Comput. 4, 273 (2004)
McKague, M., Mosca, M.: Generalized self-testing and the security of the 6-state protocol. In: van Dam, W., Kendon, V.M., Severini, S. (eds.) TQC 2010. LNCS, vol. 6519, pp. 113–130. Springer, Heidelberg (2011)
Bancal, J.-D., et al.: Phys. Rev. Lett. 106, 250404 (2011) arXiv:1102.0197 [quant-ph]
Silman, J., et al.: Phys. Rev. Lett. 106, 220501 (2011)
Greenberger, D.M., Horne, M.A., Zeilinger, A.: Going beyond Bell’s theorem. In: Kafatos, M. (ed.) Bell’s Theorem, Quantum Theory, and Conceptions of the Universe, p. 74. Kluwer, Dordrecht (1989)
Mermin, N.D.: Phys. Today 43, 9 (1990)
Mochon, C.: arXiv:0711.4114 [quant-ph]
Chailloux, A., Kerenidis, I.: In: Proceedings of the 50th Annual IEEE Symposium on Foundations of Computer Science, p. 527. CS Press (2009)
Chailloux, A., Kerenidis, I.: In: Proceedings of the 52nd Annual IEEE Symposium on Foundations of Computer Science, p. 354. CS Press (2011) arXiv:1102.1678v1 [quant-ph]
Blum, M.: In: Gersho, A., Santa Barbara, U.C. (eds.) Advances in Cryptology: a report on CRYPTO 81. Department of Electrical and Computer Engineering, ECE Report No. 82–04, 1982, p. 11
Aharonov, D., et al.: In: Proceedings of the 32nd Annual ACM Symposium on the Theory of Computing, p. 705. ACM Press (2000)
Ambainis, A.: In: Proceedings of the 33rd Annual ACM Symposium on the Theory of Computing, p. 134. ACM Press (2001)
Kitaev, A.: Unpublished. Proof reproduced in [29]
Spekkens, R.W., Rudolph, T.: Phys. Rev. A 65, 012310 (2001)
Spekkens, R.W., Rudolph, T.: Phys. Rev. Lett. 89, 227901 (2002)
Mochon, C.: In: Proceedings of the 45th Annual IEEE Symposium on the Foundations of Computer Science, p. 2. CS Press (2004)
Mochon, C.: Phys. Rev. A 72, 022341 (2005)
Ambainis, A., et al.: In: Proceedings of the 19th Annual IEEE Conference on Computational Complexity, p. 250. CS Press (2004)
Barrett, J., Massar, S.: Phys. Rev. A 69, 022322 (2004)
Barrett, J., Massar, S.: Phys. Rev. A 70, 052310 (2004)
Aharon, N., Silman, J.: New J. Phys. 12, 033027 (2010)
Ganz, M.: arXiv:0910.4952 [quant-ph]
Kent, A.: Phys. Rev. Lett. 83, 5382 (1999)
Vaidman, L.: Found. Phys. 29, 615 (1999)
Clauser, J.F., et al.: Phys. Rev. Lett. 23, 880 (1969)
Cirel’son, B.S.: Lett. Math. Phys. 4, 93 (1980)
Tsirelson, B.: Hadronic J. Suppl. 8, 329 (1993)
Masanes, Ll.: Phys. Rev. Lett. 97, 050503 (2006)
Acknowledgements
We acknowledge support from the BSF (grant no. 32/08) (N.A.), the Inter-University Attraction Poles Programme (Belgian Science Policy) under Project IAP-P6/10 (Photonics@be) (S.M., S.P., J.S), a BB2B grant of the Brussels-Capital region (S.P.), the Fonds de la Recherche Scienitifique – FNRS (J.S.), the projects ANR-09-JCJC-0067-01, ANR- 08-EMER-012 (A.C., I.K.), and the project QCS (grant 255961) of the E.U. (A.C., I.K., S.M., S.P., J.S.).
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2014 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Aharon, N., Chailloux, A., Kerenidis, I., Massar, S., Pironio, S., Silman, J. (2014). Weak Coin Flipping in a Device-Independent Setting. In: Bacon, D., Martin-Delgado, M., Roetteler, M. (eds) Theory of Quantum Computation, Communication, and Cryptography. TQC 2011. Lecture Notes in Computer Science(), vol 6745. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-54429-3_1
Download citation
DOI: https://doi.org/10.1007/978-3-642-54429-3_1
Published:
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-54428-6
Online ISBN: 978-3-642-54429-3
eBook Packages: Computer ScienceComputer Science (R0)