Abstract
Access Control Encryption (ACE) is a novel paradigm for encryption which allows to control not only what users in the system are allowed to read but also what they are allowed to write.
The original work of Damgård et al. [DHO16] introducing this notion left several open questions, in particular whether it is possible to construct ACE schemes with polylogarithmic complexity (in the number of possible identities in the system) from standard cryptographic assumptions.
In this work we answer the question in the affirmative by giving (efficient) constructions of ACE for an interesting class of predicates which includes equality, comparison, interval membership, and more.
We instantiate our constructions based both on standard pairing assumptions (SXDH) or more efficiently in the generic group model.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves.
1 Introduction
Access Control Encryption (ACE) is a novel paradigm for encryption that was introduced by Damgård, Haagh and Orlandi [DHO16]. (A similar concept had previously been introduced in [IPV10].) The main difference between ACE and other advanced encryption primitives (such as identity-based [Sha84, BF01, Sak00], attribute-based [SW05] or functional encryption [BSW11]) is that while previous concepts for encryption prevent parties from receiving messages (or functions of these) that are not meant for them, ACE also prevents unauthorized parties from sending messages to others they are not allowed to communicate with.
In a nutshell, ACE considers a set of senders \(\{S_i\}_{i\in {\{0,1\}^n}}\) and a set of receivers \(\{R_j\}_{j\in {\{0,1\}^n}}\). An ACE scheme is parameterized by a predicate P and \(P(i,j)=1\) indicates that \(S_i\) is allowed to communicate with \(R_j\) while \(P(i,j)=0\) means that no communication should be possible. All communication is assumed to be routed through a special party, called the sanitizer, which is assumed to be semi-honest; in particular, the sanitizer will follow the protocol specification but might try to learn additional information by colluding with other parties in the system.
During the key distribution phase each sender \(S_i\) is given an encryption key \(\textit{ek}_i\) while each receiver is given a decryption key \(dk_j\). A sender can then create a ciphertext \(c=\mathsf {Enc}(\textit{ek}_i,m)\) which is sent to the sanitizer. The sanitizer need not know (nor does he learn) the message which is being transmitted nor the identity of the sender, but performs a simple sanitization of the ciphertext and broadcasts the output \(c'=\mathsf {San}(\textit{pp},c)\) to all receivers. Correctness of the ACE scheme guarantees that if \(P(i,j)=1\) then \(\mathsf {Dec}(\textit{dk}_j,c)=m\) i.e., authorized receivers should be able to recover the message.
ACE also imposes two security requirements: the first, called the no-read rule, requires any set of unauthorized receivers (even colluding with the sanitizer) to be unable to learn any information from ciphertexts that they are not allowed to decrypt. The second (and more interesting) one is called the no-write rule and guarantees that no set of corrupt senders \(\{S_i\}\) can transfer any information to any set of corrupt receivers \(\{R_j\}\) under the condition that \(P(i,j)=0\) for each combination of sender-receiver pair.
In [DHO16] the authors present two ACE schemes which can implement any predicate \(P : {\{0,1\}^n}\times {\{0,1\}^n}\rightarrow {\{0,1\}}\). However, both constructions have severe limitations. The first construction can be instantiated under standard number-theoretic assumptions, such as the decisional Diffie-Hellman (DDH) assumption or the decisional composite residuosity (DCR) assumption underlying Paillier encryption. However, its complexity, e.g. in terms of key and ciphertext size, is exponential in n and can therefore only be used when the number of identities in a system is very small. The second construction, whose complexity is polynomial in n, relies on a special flavor of general-purpose functional encryption (defined in [DHO16]) that, to the best of our knowledge, can only be instantiated using indistinguishability obfuscation [GGH+13]; the scheme is therefore not practically useful at this time.
The authors of [DHO16] left as an open question whether it is possible to construct asymptotically efficient ACE schemes without obfuscation, even for limited classes of predicates. In this work we answer this question in the affirmative by showing asymptotically efficient constructions for interesting predicates such as equality, comparison, and interval membership, as summarized in Table 1 which are based on standard pairing assumptions (SXDH). (The construction can be instantiated even more efficiently in the generic group model, see Table 2 for the exact constants involved in the constructions).
Technical Overview of Our Contributions. Our first technical contribution is an ACE scheme for the equality predicate i.e.,
The scheme can be instantiated using generic assumptions (see Sect. 3.2) and very efficiently using cryptographic pairings and in particular structure-preserving signatures on equivalence classes [HS14] (see Sect. 3.3). We show how to instantiate this construction based on standard pairing assumptions (SDXH) or more efficiently in the generic group model. See Table 2 for a detailed efficiency comparison.
We then show how to use the scheme for equality in a black-box way to implement ACE for a predicate defined in the following way. Let \(\mathsf {S}\) and \(\mathsf {R}\) be two efficient functions which map identities into sets of identities:
under the constraint that \(\max _{i,j}\{|\mathsf {S}(i)|,|\mathsf {R}(j)|\}=\mathsf {poly}(n)\). Then we can construct efficient ACE for the predicate defined by
We show that this class of predicates is quite rich (using results from [SBC+07, GMW15]) and includes useful predicates such as comparison (i..e, the predicate \(\mathsf {P}_{\textsf {comp}}(i,j)=1\Leftrightarrow i\le j\)) and interval membership (i.e., the predicate \(\mathsf {P}_{\textsf {range}}\) defined for all points \(z \in [N]\) and intervals \(I \subset [N]\) as \(\mathsf {P}_{\textsf {range}}(z,I) = 1 \Leftrightarrow z \in I\)).
In a nutshell, the composed ACE scheme works as follows: assuming an ACE for equality, sender i is given all the encryption keys corresponding to the identities contained in the set \(\mathsf {S}(i)\) and receiver j is given all the decryption keys for identities contained in the set \(\mathsf {R}(j)\). To encrypt a message, the sender encrypts it under all his encryption keys (padding to the size of the largest possible set). Now if the intersection of \(\mathsf {S}(i)\) and \(\mathsf {R}(j)\) is not empty, the receiver can decrypt at least one of the ciphertexts and therefore learn the message; the scheme thus satisfies correctness. Intuitively, the scheme also satisfies the no-read and no-write rule since \(\mathsf {P}_{\textsf {disj}}(i,j)=0 \Rightarrow \mathsf {S}(i)\cap \mathsf {R}(j)= \emptyset \), which allows us to use the security property of the underlying equality ACE scheme.
For correctness, the receiver must be able to tell when decryption of the underlying ACE succeeds. This can be achieved using standard techniques, e.g., by using a sparse message space. The trivial implementation of decryption, where the receiver tries all keys on all ciphertexts, would lead to a decryption complexity quadratic in the size of \(\mathsf {R}(j)\). In Sect. 4 we overcome this shortcoming by defining the overall predicate with disjunction of equalities instead of disjointness of sets.
We note that the linear construction from [DHO16] might at first glance look similar to the one proposed here, with \(\mathsf {R}(j)=\{j\}\) (each receiver is given a single key) and \(\mathsf {S}(i)=\{j \,|\, P(i,j)=1\}\) (each sender is given a key for every receiver she is allowed to talk to). Note however that the complexity of this construction is inherently exponential, due to the way that ciphertexts are constructed and sanitized: in the linear construction of [DHO16], ciphertexts contain one entry for every possible receiver in the system (senders encrypt the message using the keys of all the receivers they are allowed to talk to and add random ciphertexts for the other receivers), and the sanitization process treats each component of the ciphertext differently (i.e., the sanitizer sanitizes each component of the ciphertext using a receiver-dependent procedure). Our approach is to start with an ACE for equality with the property that the sanitizer’s algorithm is oblivious of the identity of the sender/receiver.
Finally, we note that all constructions in [DHO16] require the sanitizer to store some secret information, the knowledge of which would allow the adversary to break the no-write rule. In contrast, for the schemes presented in this paper, the sanitizer does not need to store any secret information, thereby significantly reducing the chances for an adversary to break the security of the system. In particular, the adversary must perform an active corruption of the sanitizer in order to break the no-write rule.
2 Defining ACE
ACE Notation. An access control encryption (ACE)Footnote 1 scheme is defined by the following PPT algorithms:
-
Setup: \(\mathsf {Setup}\) is a randomized algorithm that on input the security parameter \(\kappa \) and a policy \(P:{\{0,1\}^n}\times {\{0,1\}^n}\rightarrow {\{0,1\}}\) outputs a master secret key \(\textit{msk}\) and public parameters \(\textit{pp}\) (which include the message space \(\mathcal {M}\) and ciphertext spaces \(\mathcal {C},\mathcal {C}'\)).
-
Key Generation: \(\mathsf {Gen}\) is a deterministic algorithmFootnote 2 that on input the master secret key \(\textit{msk}\), a type \(t\in \{\mathsf {sen},\mathsf {rec}\}\) and an identity \(i\in {\{0,1\}^n}\), outputs a key k. We use the following notation for the two kinds of keys in the system:
-
– \(\textit{ek}_i\leftarrow \mathsf {Gen}(\textit{msk},i,\mathsf {sen})\) and call it an encryption key for \(i\in {\{0,1\}^n}\)
-
– \(\textit{dk}_j\leftarrow \mathsf {Gen}(\textit{msk},j,\mathsf {rec})\) and call it a decryption key for \(j\in {\{0,1\}^n}\)
We remark that, as opposed to [DHO16], there is no need for a private sanitizer key in our schemes.
-
-
Encrypt: \(\mathsf {Enc}\) is a randomized algorithm that, on input an encryption key \(\textit{ek}_i\) and a message m, outputs a ciphertext c.
-
Sanitizer: \(\mathsf {San}\) is a randomized algorithm that using the public parameters \(\textit{pp}\) transforms an incoming ciphertext \(c\in \mathcal {C}\) into a sanitized ciphertext \(c'\in \mathcal {C}'\).
-
Decryption: \(\mathsf {Dec}\) is a deterministic algorithm that recovers a message \(m' \in \mathcal {M}\cup \{\bot \}\) from a ciphertext \(c'\in \mathcal {C}'\) using a decryption key \(\textit{dk}_j\).
Definition 1
(Correctness). For all \(m\in \mathcal {M}\), \(i,j \in {\{0,1\}^n}\) with \(P(i,j)=1\):
with \((\textit{pp},\textit{msk})\leftarrow \mathsf {Setup}(1^\kappa ,P)\), \(\textit{ek}_i\leftarrow \mathsf {Gen}(\textit{msk},i,\mathsf {sen})\), \(\textit{dk}_j\leftarrow \mathsf {Gen}(\textit{msk},j,\mathsf {rec})\), and the probability is taken over the random coins of all algorithms.
Complementary to correctness, we require that it is detectable when decryption does not succeed, formalized as follows.
Definition 2
(Detectability). For all \(m\in \mathcal {M}\), \(i,j \in {\{0,1\}^n}\) with \(P(i,j)=0\):
with \((\textit{pp},\textit{msk})\leftarrow \mathsf {Setup}(1^\kappa ,P)\), \(\textit{ek}_i\leftarrow \mathsf {Gen}(\textit{msk},i,\mathsf {sen})\), \(\textit{dk}_j\leftarrow \mathsf {Gen}(\textit{msk},j,\mathsf {rec})\), and the probability is taken over the random coins of all algorithms.
Definition 3
(No-Read Rule). Consider the following game between a challenger C and a stateful adversary A:

We say that A wins the No-Read game if \(b=b'\) , \(|m_0|=|m_1|\) , \(i_0,i_1\in {\{0,1\}^n}\) and for all queries q to \(\mathcal {O}_G\) with \(q=(j,\mathsf {rec})\) it holds that
We say an ACE scheme satisfies the No-Read rule if for all PPT A

Remark: The definition in [DHO16] requires \(2\cdot |\Pr [A \) wins the No-Read game\(]-\frac{1}{2}|\le \mathsf {negl}(\kappa )\), which is unachievable, since any A whose output satisfies \(|m_0|\ne |m_1|\) has advantage \(=1\) (the same also applies to their version of Definition 4).
Our definition of the no-read rule is also weaker in that it does not guarantee anonymity of the sender against an adversary who can decrypt the ciphertext (in the context of attribute-based encryption a similar property is called weak attribute hiding [OT12]). However, none of the applications of ACE described in [DHO16] require this property.
Definition 4
(No-Write Rule). Consider the following game between a challenger C and a stateful adversary A:

Let \(Q_S\) (resp. Q ) be the set of all queries \(q=(j,t)\) that A issues to \(\mathcal {O}_S\) (resp. both \(\mathcal {O}_S\) and \(\mathcal {O}_R\) ). Let \(I_S\) be the set of all \(i\in {\{0,1\}^n}\) such that \((i,\mathsf {sen})\in Q_S\) and let J be the set of all \(j\in {\{0,1\}^n}\) such that \((j,\mathsf {rec})\in Q\) . Then we say that A wins the No-Write game if \(b'=b\) and all of the following hold:
-
1.
\(i'\in I_S \cup \{0\}\);
-
2.
\(\forall i\in I_S,j\in J\), \(P(i,j)=0\);
-
3.
\(\mathsf {San}(\textit{pp},c_0)\ne \bot \).
We say an ACE scheme satisfies the No-Write rule if for all PPT A

Remark: Note that the no-write rule as defined in [DHO16] does not require the third condition above, which essentially just requires the ciphertext output by the adversary to be well-formed relative to the public parameters \(\textit{pp}\) (which crucially means that the adversary already knows if the ciphertext is well-formed or not). The constructions in [DHO16] deal with this by letting the sanitizer output a random encryption when running on an malformed ciphertext instead. We find the notion presented here to be more natural.
3 ACE for Equality
Here, we show two how to build an ACE for the equality predicate defined by \(\mathsf {P}_{\textsf {eq}}:\{0,1\}^n \times \{0,1\}^n \rightarrow {\{0,1\}}\) and
We present two constructions, one based on generic assumptions and a second (more efficient) one based on cryptographic pairings.
3.1 Generic Construction Preliminaries
We start with reviewing the notation we will use for standard cryptographic building blocks and we refer to standard textbooks in cryptography (such as [Gol09, KL14]), for formal definitions of security. For real functions f and g, we write \(f(\kappa ) \approx g(\kappa )\) if \(|f(\kappa ) - g(\kappa )| \le \mathsf {negl}(\kappa )\), where \(\mathsf {negl}\) is a negligible function in \(\kappa \).
Non-interactive Zero-Knowledge Proofs. Let L be a language and R a relation s.t. \(x \in L\) if and only if there exists a witness w such that \((x,w) \in R\). A non-interactive proof system [BFM88] for a relation R is defined by the PPT algorithms \((\mathsf {NIZK.Gen},\mathsf {NIZK.Prove},\mathsf {NIZK.Ver})\) with \(\textit{crs}\leftarrow \mathsf {NIZK.Gen}(1^\kappa ,L)\), \(\pi \leftarrow \mathsf {NIZK.Prove}(\textit{crs},x,w)\) and \(\mathsf {NIZK.Ver}(\textit{crs},x,\pi )\in {\{0,1\}}\). We require correctness, (perfect) soundness, knowledge extraction, and zero-knowledge.
Correctness. For all PPT adversaries A:
Soundness. For all PPT adversaries A:
Knowledge Extraction. We say that a system \((\mathsf {NIZK.Gen},\mathsf {NIZK.Prove},\mathsf {NIZK.Ver})\) has knowledge-extraction security if there exists a knowledge extractor, which is a pair of PPT algorithms \((E_1, E_2)\) with the following two properties:
-
1.
For all PPT adversaries A:

-
2.
For all PPT adversaries A:
$$\Pr \,\left[ \begin{array}{l}(\textit{crs}, \tau ) \leftarrow E_1(1^\kappa ,L) ; \\ (x, \pi )\leftarrow A(\textit{crs}); \\ w \leftarrow E_2(\textit{crs}, \tau , x, \pi )\end{array} : \; \mathsf {NIZK.Ver}(\textit{crs},x,\pi ) = 0 \text { or } (x,w) \in R \right] \approx 1.$$
Zero-Knowledge. We say that proof system \((\mathsf {NIZK.Gen},\mathsf {NIZK.Prove},\mathsf {NIZK.Ver})\) has zero-knowledge security if there exists a simulator, which is a pair of PPT algorithms \((S_1, S_2)\) with the following property: For all PPT adversaries A:

where \(S'(\textit{crs}, \tau , x, w) = S_2(\textit{crs}, \tau , x)\) if \((x,w) \in R\) and outputs failure otherwise.
We speak of perfect correctness, perfect soundness, perfect knowledge extraction, and perfect zero-knowledge if for sufficiently large security parameters, and for all adversaries (unbounded, and not just PPT), we have equalities in the respective definitions.
Digital Signatures. A signature scheme is a tuple of PPT algorithms \((\mathsf {Sig.Gen}, \mathsf {Sig.Sig}, \mathsf {Sig.Ver})\) with \((\textit{sk},\textit{vk})\leftarrow \mathsf {Sig.Gen}(1^\kappa )\), \(\sigma = \mathsf {Sig.Sig}(\textit{sk},m)\), and \(\mathsf {Sig.Ver}(\textit{vk}, m,\sigma )\in {\{0,1\}}\). We require correctness and existential unforgeability under chosen-message attacks. (Note that we defined the signature algorithm to be deterministic. Any randomized signature scheme can be de-randomized using a pseudorandom tape generated with a PRF on the message).
Anonymous and Weakly Sanitizable Public-Key Encryption. We use a public-key encryption (PKE) scheme which must satisfy semantic security, anonymity, and which must be weakly sanitizable. The syntax is as follows: \(\textit{pp}\leftarrow \mathsf {PKE.Par}(1^\kappa )\) outputs public parameters, \((\textit{ek},\textit{dk})\leftarrow \mathsf {PKE.Gen}(\textit{pp})\) outputs an encryption/decryption key pair, \(c\leftarrow \mathsf {PKE.Enc}(\textit{ek},m)\) outputs an encryption of m, \(c'\leftarrow \mathsf {PKE.San}(\textit{pp},c)\) outputs a sanitized version of c and \(m'\leftarrow \mathsf {PKE.Dec}(\textit{dk},c)\) decrypts ciphertext c.
Anonymity can be formalized as in [BBDP01] via a game where the adversary receives \((\textit{pp},\textit{ek}_0,\textit{ek}_1)\), chooses a message m, receives \(c\leftarrow \mathsf {PKE.Enc}(\textit{ek}_b,m)\) and must guess b.
In [DHO16] the notion of sanitizable encryption is introduced as a relaxation of rerandomizable encryption. Here we only require an even weaker property: we define an encryption scheme to be weakly sanitizable if the adversary cannot win a game where he is given \((\textit{pp},\textit{ek})\), chooses \((m_0,r_0),(m_1,r_1)\), receives
with uniform randomness \(r'\) and must guess b.
The weakening lies in the fact that sanitizations only have to be computationally indistinguishable, whereas in the sanitizable PKE of [DHO16], sanitizations of encryptions of the same message must be statistically indistinguishable.
An Anonymous and Weakly Sanitizable Scheme. An encryption scheme that satisfies the above properties under the DDH assumption is the following simple variation of ElGamal [Gam85]. As for the original scheme, the parameters \(\textit{pp}=(\mathbb {G},p,g)\) consist of the description of a DDH-hard group \(\mathbb {G}\) of order p generated by g; the decryption key is a random element \(\textit{dk}\in \mathbb {Z}_p\) and the encryption key is defined as \(\textit{ek}=g^{\textit{dk}}\). Encryption of a message \(m\in \mathbb {G}\) is now defined as picking random \(r\in \mathbb {Z}_p^*\) and \(s\in \mathbb {Z}_p\) and defining a ciphertext as
A ciphertext \((d_0,d_1,c_0,c_1)\) is sanitized by first checking if \(d_0= 1\) or \(d_1=1\), in which case the sanitizer outputs two random group elements; otherwise it picks a random \(t\in \mathbb {Z}_p^*\) and returns \((d_0^{\,t}\cdot c_0 ,\,d_1^{\,t}\cdot c_1)=(g^{rt+s},\,\textit{ek}^{rt+s}\cdot m)\), which is (statistically close to) a fresh encryption of m.
This scheme can be made detectable (see Definition 2) using standard techniques, e.g. by choosing a sparse message space \(\mathcal {M}'\), that is, with \(\frac{|\mathcal {M}'|}{p} \le \mathsf {negl}(\kappa )\), where p is the order of \(\mathbb {G}\). Decryption of a sanitized ciphertext \((d_0^t c_0 ,d_1^t c_1) = (g^{rt +s}, \textit{ek}^{rt + s} \cdot m)\) with a different key \(\textit{dk}' \ne \textit{dk}\) yields: \((g^{rt +s})^{-\textit{dk}'} \cdot \textit{ek}^{rt + s} \cdot m = (g^{\textit{dk}- \textit{dk}'})^{rt + s} \cdot m\), which is statistically close to a random element of \(\mathbb {G}\). If \(\frac{|\mathcal {M}'|}{p} \le \mathsf {negl}(\kappa )\), the probability that this element is in \(\mathcal {M}'\) is negligible and so:
meeting our definition for detectability.
Proposition 1
The above encryption scheme is anonymous and weakly sanitizable.
Proof
For anonymity, notice that we can define a hybrid anonymity game where the adversary is given an encryption of its message m under a new encryption key \(e_x = g^{x}\) (where x is a random element of \(\mathbb {Z}_p\)) instead of \(\textit{ek}_0\) or \(\textit{ek}_1\) and move from the game that uses \(\textit{ek}_0\) to encrypt the challenge ciphertext to one that uses \(\textit{ek}_x\) using DDH. Given a DDH challenge \(g, g^{a}, g^{b}\), and \(g^{ab + x}\) where either \(x = 0\) or x is a random element in \(\mathbb {Z}_p\), one can play the game using \(\textit{ek}_0 = g^{a}\) and create the challenge ciphertext as \(((g^{b})^{\tilde{r}}, (g^{ab+x})^{\tilde{r}}, g^{b}, g^{ab+x} \cdot m)\). If \(x = 0\), then this is distributed like the game that uses \(\textit{ek}_0\) (where \(dk = a\), \(r = b \tilde{r}\) and \(s = b\)). If x is a random element of \(\mathbb {Z}_p\), then this is distributed like the game that uses \(\textit{ek}_x\). (Moving from \(\textit{ek}_x\) to \(\textit{ek}_1\) follows symmetrically).
To see that the variant is weakly sanitizable, notice that we can similarly define a hybrid sanitizability game where the adversary is given two random group elements as its challenge sanitized ciphertext. In such a game, the challenge sanitized ciphertext is independent of b, so the adversary cannot achieve any advantage. We can move to this game using DDH. Given a DDH challenge \(g, g^{a}, g^{b}\), and \(g^{ab + x}\) where either \(x = 0\) or x is a random element in \(\mathbb {Z}_p\), one can play the game using \(\textit{ek}= g^{a}\) and create the challenge sanitized ciphertext as \((g^b, g^{ab + x} \cdot m_b)\) (unless \(r_b\) causes \(d_0\) or \(d_1\) to be the identity, in which case it uses two random group elements). If \(x = 0\), then this is distributed like the normal game (a sanitized ciphertext \((d_0^{\,t}\cdot c_0 ,\,d_1^{\,t}\cdot c_1)=(g^{rt+s},\,\textit{ek}^{rt+s}\cdot m_b)\) looks like an ElGamal encryption of \(m_b\) when \(d_0 \ne 1\) and \(d_1 \ne 1\)). If x is a random element of \(\mathbb {Z}_p\), then the challenge sanitized ciphertext is distributed as two random group elements. \(\square \)
3.2 Generic Construction
Construction 1
(ACE for Equality – Generic). We construct an ACE scheme  defined by the following algorithms:
defined by the following algorithms:
-
Setup: Compute \(\textit{pp}^\mathsf {pke}\leftarrow \mathsf {PKE.Par}(1^\kappa )\) and \((\textit{vk},\textit{sk})\leftarrow \mathsf {Sig.Gen}(1^\kappa )\).
Let L be the language defined by the following NP relation: for \(x=(\textit{vk},c)\) and \(w=(\textit{pk},\sigma ,m,r)\), define \(R(x,w)=1\) iff
$$\mathsf {Sig.Ver}(\textit{vk},\textit{pk},\sigma )=1\ \wedge \ c=\mathsf {PKE.Enc}(\textit{pk},m;r). $$Compute
 . Pick a random PRF key K for a PRF F. Output
. Pick a random PRF key K for a PRF F. Output  and \(\textit{msk}=(\textit{sk},K)\).
and \(\textit{msk}=(\textit{sk},K)\). -
Key Generation: Given the master secret key \(\textit{msk}\) and an identity i, the encryption and decryption keys are computed as follows: run

and define

-
Encryption: On input a message m and an encryption key \(\textit{ek}_i=(\textit{pk},\sigma )\) pick encryption randomness r, compute \(c'=\mathsf {PKE.Enc}(\textit{pk},m;r)\), let \(x=(\textit{vk},c')\), \(w=(\textit{pk},\sigma ,m,r)\) and compute \(\pi \leftarrow \mathsf {NIZK.Prove}(\textit{crs},x,w)\). Output \(c=(c',\pi )\).
-
Sanitizer: On input \(\textit{pp}=(\textit{pp}^\mathsf {pke},\textit{vk},\textit{crs})\) and a ciphertext \(c=(c',\pi )\) the sanitizer outputs \(\bot \) if \(\mathsf {NIZK.Ver}(\textit{crs},x=(\textit{vk}, c'),\pi )=0\); otherwise it returns \(c''\leftarrow \mathsf {PKE.San}(\textit{pp},c')\).
-
Decryption: Given a ciphertext \(c'\) and a decryption key \(\textit{dk}_j = \textit{dk}\) output
$$m' = \mathsf {PKE.Dec}(\textit{dk},c').$$
Theorem 1
Construction 1 satisfies the No-Read Rule if the underlying PKE scheme satisfies semantic security and anonymity, if the proof system is zero-knowledge and the PRF is pseudorandom.
Proof
We assume that A makes queries \(\mathcal{O}_G(i_0,\mathsf {sen})\) and \(\mathcal{O}_G(i_1,\mathsf {sen})\) (this is w.l.o.g., as any A can be transformed into such an adversary without affecting its winning probability). We define a hybrid game which guesses A’s oracle queries that lead to the creation of the encryption keys of users \(i_0\) and \(i_1\). If the guess was wrong, the game outputs a random bit. (The differences to the original game are items 0. and 6. below.) Let \(q_\text {max}\) be an upper bound on the number of \(\mathcal{O}_G(\cdot ,\mathsf {sen})\) plus the number \(\mathcal{O}_E\) queries that A makes during the game. (The keys could also be first created during an encryption query.) Since A is PPT, it is clear that \(q_\text {max}\) is polynomial in \(\kappa \).

Lemma 1
An adversary that wins the no-read game with non-negligible advantage also wins the hybrid game with non-negligible advantage.
Proof
Assume an adversary breaks the no-read rule, that is, there exists c s.t.
for infinitely many \(\kappa \). Let E denote the event that in the hybrid game \(Q[q_0] = i_0\) and \(Q[q_1]=i_1\). Note that this event is independent of A’s view; moreover, conditioned on E occurring, the hybrid game and the original No-Read-Rule game are equivalent; finally \(\Pr [E] = {q_\text {max}^{-2}}\). We thus have
for infinitely many \(\kappa \). Thus, \(\mathsf {adv}^{A}_\text {hybrid}(ACE)\) is not negligible in \(\kappa \). \(\square \)
Assuming an arbitrary PPT A, we will now show that \(H_0\), the hybrid above with b fixed to 0, is computationally indistinguishable from \(H_1\) (b fixed to 1). By Lemma 1, A cannot have won the original game, thus proving the theorem. We define a sequence of hybrid games between \(H_0\) and \(H_1\) and show that each one is computationally indistinguishable from the previous one (i.e., the probability that the hybrid game returns 1 only changes negligibly).
-
Game \(H_{b,1}\) (for \(b\in {\{0,1\}}\)) is defined as \(H_b\), except we use a truly random function instead of F to generate all secret keys.
-
\(H_{b,0}\approx _c H_{b,1}\!\) (which we use as shorthand for \(\Pr [A\text {\,wins}\,H_{b,0}]\approx \Pr [A\,\text {wins}\,H_{b,1}]\)): Indistinguishability follows from PRF security (as K is never revealed to A).
-
Game \(H_{b,2}\) is the same as \(H_{b,1}\), except \(\textit{crs}\), contained in \(\textit{pp}\), and \(\pi \) in the challenge ciphertext c are simulated.
-
\(H_{b,1}\approx _c H_{b,2}\) : Indistinguishability follows from the zero-knowledge property of the proof system.
-
Game \(H_{0,3}\) is the same as \(H_{0,2}\), except c is computed as encryption of \(m_1\) (instead of \(m_0\)) under identity \(i_0\)’s key.
-
\(H_{0,2}\approx _c H_{0,3}\) : Indistinguishability follows from semantic security of the encryption scheme: We construct a PPT reduction B that receives a challenge \(\textit{pk}\) and simulates game \(H_{0,2}\). When A makes the query that generates the \(q_0\)-th encryption key, B sets this key to \(\textit{pk}\). If A queries the corresponding decryption key, B aborts (outputting a random bit). When A outputs \((m_0,m_1,i_0,i_1)\) and \(i_0\) is not the identity corresponding to the \(q_0\)-th key, B aborts. Otherwise, B submits \((m_0,m_1)\) as challenge to receive c from its challenger (which is either \(m_0\) or \(m_1\) encrypted under \(\textit{pk}\)) and forwards c to A together with a simulated proof \(\pi \). Reduction B perfectly simulates either \(H_{0,2}\) or \(H_{0,3}\), depending on its own challenge: if B guesses \(q_0\) and \(q_1\) correctly, it does not abort and otherwise it outputs a random bit anyway.
-
\(H_{0,3}\approx _c H_{1,2}\) : The two games differ in that \(m_1\) is encrypted under \(i_0\)’s key in \(H_{0,3}\) and \(i_1\)’s key in \(H_{1,2}\). Indistinguishability follows from anonymity of the encryption scheme: We construct a PPT reduction B, which receives \(\textit{pk}_0\) and \(\textit{pk}_1\) and simulates \(H_{1,2}\) for A, except that it sets the \(q_0\)th key to \(\textit{pk}_0\) and the \(q_1\)th key to \(\textit{pk}_1\). If A queries a corresponding decryption key or if in A’s output \((m_0,m_1,i_0,i_1)\), \(i_0\) does not correspond to the \(q_0\)th key or \(i_1\) does not correspond to the \(q_1\)th key then B aborts. Otherwise, B submits \(m_1\) as a challenge to receive c from its challenger (which is \(m_1\) encrypted under \(\textit{pk}_0\) or \(\textit{pk}_1\)), which it forwards to A together with a simulated proof \(\pi \). Depending on its own challenge, B perfectly simulates either \(H_{1,2}\) or \(H_{1,3}\): if B guesses \(q_0\) and \(q_1\) correctly, it does not abort and otherwise it outputs a random bit anyway.
We have thus shown \(H_0\approx _c H_{0,1}\approx _c H_{0,2}\approx _c H_{0,3}\approx _c H_{1,2}\approx _c H_{1,1}\approx _c H_{1}\), which concludes the proof. \(\square \)
Theorem 2
Construction 1 satisfies the No-Write Rule if the underlying PKE scheme is anonymous and weakly sanitizable, if the proof system is perfectly sound and has knowledge extraction security, the signature scheme is unforgeable and the PRF is pseudorandom.
Proof
Let \(H_0\) denote the No-Write-Rule game. W.l.o.g. we assume that A makes a query \(\mathcal{O}_S(i',\mathsf {sen})\) and that \(I_S \cap J = \emptyset \) (i.e., A satisfies the 2nd item in the winning condition in Definition 4). We start with defining two hybrid games whose indistinguishability from \(H_0\) is immediate:
-
Game \(H_{1}\) is defined as \(H_0\), except we use a truly random function instead of F to generate all secret keys.
-
\(H_{0}\approx _c H_{1}\) : Indistinguishability follows from PRF security.
-
Game \(H_{2}\) is the same as \(H_{1}\), except that \(\textit{crs}\) is computed via the knowledge extractor: \((\textit{crs},\tau )\leftarrow E_1(1^\kappa , L)\) (where \(\tau \) is the extraction trapdoor). When A outputs \(c_0 = (c, \pi )\), we run the second part of the extractor: \(w\leftarrow E_2(\textit{crs},\tau ,x=(vk,c),\pi )\), where \(\textit{vk}\) is contained in \(\textit{pp}\).
-
\(H_{1}\approx _c H_{2}\) : Indistinguishability follows from the first property of knowledge extraction (i.e., a CRS output by \(E_1\) is indistinguishable from one output by \(\mathsf {NIZK.Gen}\)) of the proof system. (Running \(E_2\) has no effect on the outcome of the game.)

For a particular run of game \(H_2\) (which is determined by the coins used by the adversary and the challenger when running the probabilistic algorithms), we now differentiate four types. We let \(w=(\textit{pk},\sigma ,m,r)\) denote the output of \(E_2\).
-
Type 1: A outputs \(c_0 = (c, \pi )\) with \(\mathsf {NIZK.Ver}(\textit{crs},(\textit{vk}, c),\pi )=0\) (where \(\textit{crs}, \textit{vk}\) come from the public parameters used in the game).
-
Type 2: A outputs \(c_0 = (c, \pi )\) with \(\mathsf {NIZK.Ver}(\textit{crs},(\textit{vk}, c),\pi )=1\) but \(R((\textit{vk},c),w)=0\), i.e. \( \mathsf {Sig.Ver}(\textit{vk},\textit{pk},\sigma )\ne 1\) or \(c\ne \mathsf {PKE.Enc}(\textit{pk},m;r)\).
-
Type 3: A outputs \(c_0 = (c, \pi )\) with \(\mathsf {NIZK.Ver}(\textit{crs},(\textit{vk}, c),\pi )=1\), we have
$$\begin{aligned} \mathsf {Sig.Ver}(\textit{vk},\textit{pk},\sigma )=1\ \wedge \ c =\mathsf {PKE.Enc}(\textit{pk},m;r) \end{aligned}$$(1)and \(\textit{pk}\) was not issued in an oracle query by \(\mathcal{O}_S\).
-
Type 4 is defined as Type 3 except \(\textit{pk}\) was issued in an oracle query by \(\mathcal{O}_S\).
The 4 types are a partitioning of the coin space of the experiment, which we denote by \(T_1,\ldots ,T_4\). Let \(W_2\) denote the event that A wins hybrid game \(H_2\).
Lemma 2
\(\Pr [W_2\wedge T_1] = 0\).
Proof
\(T_1\) means A outputs \(c_0 = (c, \pi )\) with \(\mathsf {NIZK.Ver}(\textit{crs},(\textit{vk}. c),\pi )=0\). In this case, the \(\mathsf {San}\) procedure aborts, and by definition A loses the game. \(\square \)
Lemma 3
\(\Pr [T_2] \approx 0\).
Proof
In case \(T_2\) occurs A broke property 2 of knowledge-extraction security of the proof system: it output a valid proof \(\pi \) for statement \(x=(\textit{vk},c)\) but the extractor \(E_2\) failed to extract a witness w with \(R(x,w)=1\). \(\square \)
Lemma 4
\(\Pr [T_3] \approx 0\).
Proof
\(T_3\) implies that A output \((c,\pi )\) from which \(E_2\) extracted \(w=(\textit{pk},\sigma ,m,r)\) with \(\mathsf {Sig.Ver}(\textit{vk},\textit{pk},\sigma )=1\) and \(\textit{pk}\) was not issued in an oracle query.
If \(T_3\) occurred with non-negligible probability then we could construct a PPT adversary B that achieves the same advantage in the signature forging game as follows: B simulates \(H_2\) for A, creating a \(\textit{crs}\) with an extraction trapdoor \(\tau \) and using its signature oracle to respond to send key queries, i.e., queries of the form \((\cdot ,\mathsf {sen})\) to \(\mathcal{O}_S\). When A outputs \(c_0=(c,\pi )\), B runs \((\textit{pk},\sigma ,m,r)\leftarrow E_2(\textit{crs},\tau , (\textit{vk}, c),\pi )\) and returns \((\textit{pk},\sigma )\). If \(T_3\) occurred then B did not query \(\textit{pk}\) to its signing oracle, meaning B output a valid forgery. Assuming our signature scheme is unforgeable, this (and thus \(T_3\)) can only occur with negligible probability. \(\square \)
Lemma 5
\(\left| \Pr [W_2\,|\,T_4]-\textstyle \frac{1}{2}\right| \approx 0\).
Proof
\(T_4\) implies that A outputs \(c_0 = (c, \pi )\) from which \(E_2\) extracted \(w=(\textit{pk},\sigma , m,r)\) with \(c =\mathsf {PKE.Enc}(\textit{pk},m;r)\) and \(\textit{pk}\) was issued in an oracle query by \(\mathcal{O}_S\).
Similarly to the proof of Theorem 1, we first define a hybrid game which guesses A’s oracle queries that lead to the creation of the encryption keys of users \(i'\) (from A’s output \((c_0, i')\)) and i (the identity corresponding to \(\textit{pk}\) extracted by \(E_2\)). If the guess was wrong, the game outputs a random bit.
Let \(q_\text {max}\) be an upper bound on the number of \(\mathcal{O}_S(\cdot ,\mathsf {sen})\) plus the number of \(\mathcal{O}_E\) queries that A makes during the game. Since A is PPT, \(q_\text {max}\) is polynomial in \(\kappa \). (The differences to the original game are items 0., 6., and 7. below.)

Following the argument from Lemma 1, we have that an adversary that wins \(H_2\) with non-negligible advantage also wins \(H_3\) (event which we denote by \(W_3\)) with non-negligible advantage. Thus,
Assuming an arbitrary PPT A we will now show that if \(T_4\) occurs then \(H_3^{(0)}\), the hybrid \(H_3\) with b fixed to 0, is indistinguishable from \(H_3^{(1)}\) (b fixed to 1). Thus \(|\Pr [W_3\,|\, T_4]-\textstyle \frac{1}{2}|\approx 0\) and the lemma follows via (2).
To show indistinguishability of \(H_3^{(0)}\) and \(H_3^{(1)}\), we define an intermediate hybrid game \(H_4\) and show that, conditioned on \(T_4\), it is computationally indistinguishable from both \(H_3^{(0)}\) and \(H_3^{(1)}\) (i.e., the probability that the hybrid game returns 1 only changes negligibly).
In \(H_3^{(0)}\), A is given the challenge ciphertext \(c'\leftarrow \mathsf {San}(\textit{pp},c_0)\). If \(T_4\) occurs then (cf. (1)) the ciphertext contained in \(c_0=(c,\pi )\) satisfies \(c =\mathsf {PKE.Enc}(\textit{pk},m;r)\) (with \(\textit{pk}\), m and r extracted by \(E_2\)). Moreover, \(T_4\) implies that \(\pi \) is valid and A thus receives \(c'\leftarrow \mathsf {PKE.San}(\textit{pp},\mathsf {PKE.Enc}(\textit{pk},m;r))\).
-
Game \(H_4\) is the same as \(H_3^{(0)}\), except that we define the ciphertext given to A as \(c'\leftarrow \mathsf {PKE.San}(\textit{pp},\mathsf {PKE.Enc}(\textit{pk}, m^*, r^* ))\) where \(m^*, r^*\) are random.
-
\(\Pr [1\leftarrow H_3^{(0)}\,|\,T_4]\approx \Pr [1\leftarrow H_4\,|\,T_4]\) : Indistinguishability follows from sanitizing security of the encryption scheme: We construct a PPT reduction B that receives a challenge \(\textit{pk}\) and simulates game \(H_3^{(0)}\). When A makes the query that generates the \(q\)-th encryption key, B sets this key to \(\textit{pk}\). If A queries the corresponding decryption key, B aborts (outputting a random bit). Note that B will never abort if it guesses \(q\) and \(q'\) correctly, since a correct guess means that \(\textit{pk}\) will be given out as a call to \(\mathcal {O}(i, \mathsf {sen})\), and the security game then prohibits a request for the decryption key for i.
Upon receiving \((c_0 = (c, \pi ),i')\) from A, B runs \((\textit{pk}',\sigma ,m_0,r_0) \leftarrow E_2(\textit{crs}, \tau , (\textit{vk}, c), \pi )\) (where \(T_4\) implies that \(\textit{pk}'\) was queried in an oracle call).
If \(\textit{pk}' \ne \textit{pk}\) or \(i' \ne Q[q']\) (B has not guessed \(q, q'\) correctly), then B aborts.
Otherwise B submits \((m_0,r_0,m^*,r^*)\) for random \(m^*, r^*\) and receives a sanitized ciphertext \(c'\), which it gives to A. The received \(c'\) is a sanitization of either A’s output \(c_0\) (for which we have \(c_0 =\mathsf {PKE.Enc}(\textit{pk}, m_0;r_0)\)) or of \(\mathsf {PKE.Enc}(\textit{pk},m^*;r^*)\) (always assuming B’s guesses were correct). B can answer decryption key oracle queries for all allowed queries.
Reduction B perfectly simulates either \(H_3^{(0)}\) or \(H_4\), depending on its own challenge: if B guesses \(q\) and \(q'\) correctly, it does not abort and otherwise it outputs a random bit anyway.
-
\(\Pr [1\leftarrow H_4\,|\,T_4]\approx \Pr [1\leftarrow H_3^{(1)}\,|\,T_4]\) : Letting \(((c,\pi ),i')\) denote A’s output, the two games differ in that \(m^*\) is encrypted under \(\textit{pk}\) in \(H_4\) (where \(\textit{pk}\) is such that \(c =\mathsf {PKE.Enc}(\textit{pk},m;r)\)) and under \(i'\)’s key in \(H_3^{(1)}\). Indistinguishability follows from anonymity of the encryption scheme: We construct a PPT B, which receives \(\textit{pk}_0\) and \(\textit{pk}_1\), and simulates \(H_3^{(1)}\) for A, except that it sets the q-th and the \(q'\)-th created keys to \(\textit{pk}_0\) and \(\textit{pk}_1\), respectively. (If \(q=q'\) then it sets both to \(\textit{pk}_0\).) If A queries a corresponding decryption key, B aborts.
Upon receiving \((c_0 = (c, \pi ),i')\) from A, B runs \((\textit{pk},\sigma ,m,r) \leftarrow E_2(\textit{crs},\tau , (\textit{vk}, c),\pi )\) and aborts if \(\textit{pk}\ne \textit{pk}_0\) or if \(i'\) does not correspond to the \(q'\)th key (B’s guess was wrong). If \(q\ne q'\) then B submits a random \(m^*\) as a challenge to receive \(\hat{c}\) from its challenger (which is \(m^*\) encrypted under \(\textit{pk}_0\) or \(\textit{pk}_1\)); if \(q=q'\) then B sets \(\hat{c}=\mathsf {PKE.Enc}(\textit{pk}_0,m^*,r^*)\). Next, B gives \(c'\leftarrow \mathsf {PKE.San}(\textit{pp},\hat{c})\) to A.
Reduction B perfectly simulates either \(H_3^{(1)}\) or \(H_4\) (which are the same if \(q=q'\)), depending on its own challenge: if B guesses \(q\) and \(q'\) correctly, it does not abort and otherwise it outputs a random bit anyway. \(\square \)
The theorem now follows from Lemmas 2–5. Letting \(W_0\) denote the event that A wins the No-Write game \(H_0\), we have

\(\square \)
Here we show how to instantiate the generic construction, based on the SXDH assumption (Corollary 1), or based on the generic group model (Corollary 2). Both instantiation use structure-preserving signatures (SPS) [AFG+10], Groth-Sahai proofs [GS08] and the weakly sanitizable version of ElGamal encryption [Gam85] described in Sect. 3.3. In Corollary 1, we use the most efficient SPS scheme from SXDH, namely the one from [KPW15]. In Corollary 2, we use the most efficient SPS scheme with a security proof in the generic group model, which is [AGHO11]. The exact efficiency of the resulting ACE schemes are given in Table 2 on p. 23.
Corollary 1
If the SXDH assumption holds, then by Theorems 1 and 2, Construction 1 instantiated with the signature scheme from [KPW15], Groth-Sahai proofs [GS08] and the weakly sanitizable version of ElGamal encryption [Gam85] from Sect. 3.3 satisfies the No-Read and No-Write rules.
Corollary 2
Theorems 1 and 2 imply that Construction 1 instantiated with the signature scheme from [AGHO11], Groth-Sahai proofs [GS08] and the weakly sanitizable version of ElGamal encryption [Gam85] satisfies the No-Read and No-Write rules in the generic group model.
3.3 A More Efficient Construction from Pairings
Our next construction is based on ElGamal encryption, which is anonymous and re-randomizable; however, re-randomization of a ciphertext requires knowledge of its public key, so the sanitizer, who will randomize ciphertexts before passing them on, would be able to link ciphertexts to receivers.
Under a public key \(\textit{pk}=g^{\textit{sk}}\), a message m is encrypted as \(c_0=g^r,\ c_1=\textit{pk}^r\cdot m\). In order to enable randomization without revealing the public key, the sender will randomize the public key as \(d=(g^s,\,\textit{pk}^s)\) for some random \(s\ne 0\). Given c and d, the sanitizer now picks a random t and defines \(c':=(c_0\cdot d_0^t,\,c_1\cdot d_1^t)\). Since \(c'=(g^{r+st},\,\textit{pk}^{r+st}\!\cdot \! m)\) is an ElGamal encryption of m under \(\textit{pk}\), the receiver, who knows the corresponding secret key, can decrypt. On the other hand, t randomizes the ciphertext, thus to someone computationally bounded and not knowing \(\textit{sk}\), the pair looks random. This ensures anonymity towards the sanitizer and thus the no-read rule.
However, the no-write rule can easily be violated: a sender could send ciphertexts under any key and since the key is hidden, this would even be hard to detect. To enforce sending ciphertexts under legitimate keys, in the previous construction keys were signed; but without again resorting to proofs, it seems hard to verify that the key underlying the randomized key d was signed.
Fortunately, structure-preserving signatures on equivalence classes (SPS-EQ) [HS14] achieve precisely what is needed here, so the sketched construction goes through without including any proofs in the ciphertext. This primitives allows signing of pairs \((d_0,d_1)\) of group elements and adapting such signatures to multiples of the message. In particular, given a signature \(\sigma \) on \((d_0,d_1)\), anyone can adapt the signature to \((d_0^s,d_1^s)\) for any s. On the other hand, unforgeability guarantees that these are the only transformations one can do. The signatures are thus valid on all messages from the equivalence class
Adaptivity of SPS-EQ requires that signatures that were adapted to a multiple of the original message are indistinguishable from a fresh signature on the multiple.
Enforcement of the no-read rule follows in a straightforward fashion from DDH (the tuple \((g^r,\,\textit{pk}^r\cdot m,\,g^s,\,\textit{pk}^s)\) is indistinguishable from random under DDH and an instance can be embedded by using the adaptivity property of SPS-EQ). Enforcement of the no-write rule is harder to prove and relies on unforgeability for SPS-EQ (which precludes the attack sketched above). The latter ensures that the values \((d_0,d_1)\) sent by the adversary must be multiples of \((g,\textit{pk}_i)\) for some \(\textit{pk}_i\) obtained from the key oracle.
The tricky part is that once the reduction embeds a DDH challenge, it cannot find out which public key was used, and so cannot simulate the game. We thus rely on the knowledge-of-exponent assumption which implies that for any adversary that is given \((g,\textit{pk})\) and returns \((g^s,\textit{pk}^s)\) there exists an extractor that extracts s from the adversary. Now the reduction can guess which public key \(\textit{pk}_i\) the adversary randomizes and efficiently check whether its guess was correct. If it is not the case, the reduction can abort and output a random bit. (If the reduction does not abort when its simulation is incorrect, we do not have any guarantees as to the adversary’s behavior.)
Bilinear Groups. A bilinear-group generator \(\mathsf {BG. Gen}\) is a PPT algorithm that takes input a security parameter \(1^\kappa \) and outputs a description \(BG\) of a bilinear group \((p,\mathbb {G}_1,\mathbb {G}_2,\mathbb {G}_T,e,g,\hat{g})\), where p is a prime of length \(\kappa \); \(\mathbb {G}_1\), \(\mathbb {G}_2\) and \(\mathbb {G}_T\) are groups of order p; \(g\) generates \(\mathbb {G}_1\), \(\hat{g}\) generates \(\mathbb {G}_2\) and \(e:\mathbb {G}_1\times \mathbb {G}_2\rightarrow \mathbb {G}_T\) is a bilinear map that is non-degenerate, i.e. \(e(g,\hat{g})\) generates \(\mathbb {G}_T\).
We say that the DDH assumption holds in \(\mathbb {G}_1\) for \(\mathsf {BG. Gen}\) if no PPT adversary A, given \((p,\mathbb {G}_1,\mathbb {G}_2,\mathbb {G}_T,e,g,\hat{g})\leftarrow \mathsf {BG. Gen}(1^\kappa )\), and (S, T, U) with \(s,t,u\leftarrow \mathbb {Z}_p^*\), \(b\leftarrow {\{0,1\}}\) and \(S=g^s\), \(T=g^t\), \(U=g^{(1-b)u+bst}\), can decide b with non-negligible advantage. It holds in \(\mathbb {G}_2\) if the same is true when g is replaced by \(\hat{g}\). We say that SXDH holds for \(\mathsf {BG. Gen}\) if DDH holds in both \(\mathbb {G}_1\) and \(\mathbb {G}_2\).
SPS-EQ. A structure-preserving signature scheme on equivalence classes [HS14, FHS15] consists of the following PPT algorithms:
\(\mathsf {EQS. Gen}\), on input a bilinear group \(BG\) and a vector length \(\ell >1\) (in unary) outputs a key pair \((\textit{sk},\textit{pk})\). \(\mathsf {EQS. Sig}\) takes a secret key \(\textit{sk}\) and a representative \(M = (m_1,\ldots ,m_\ell )\in (\mathbb {G}_1^*)^\ell \) of class \([M]_\mathcal {R}\) and outputs a signature \(\sigma \) for the equivalence class \([M]_\mathcal {R}\). \(\mathsf {EQS. Adp}\), on input a representative \(M \in (\mathbb {G}_1^*)^\ell \), a signature \(\sigma \) for M, a scalar \(\mu \) and a public key \(\textit{pk}\), returns an updated signature \(\sigma '\) for the new representative \(M'= M^\mu := (m_1^\mu ,\ldots ,m_\ell ^\mu )\). \(\mathsf {EQS. Ver}\) takes a representative \(M \in (\mathbb {G}_1^*)^\ell \), a signature \(\sigma \) and a public key \(\textit{pk}\) and outputs \(1\) if \(\sigma \) is valid for M under \(\textit{pk}\) and \(0\) otherwise. \(\mathsf {EQS. VfK}\) checks if a secret key \(\textit{sk}\) corresponds to a public key \(\textit{pk}\) and if so returns \(1\) and \(0\) otherwise.
The scheme should satisfy correctness, existential unforgeability under chosen-message attacks (EUF-CMA) and perfect signature adaptation. Let \(M\in \mathbb {G}_1^*\), \(\mu \in \mathbb {Z}_p^*\), and \((\textit{sk},\textit{pk})\) be output by \(\mathsf {EQS. Gen}\); \(\sigma \) by \(\mathsf {EQS. Sig}(\textit{sk},M)\); and \(\sigma '\) by \(\mathsf {EQS. Adp}(M,\sigma ,\mu ,\textit{pk})\). Then the scheme is correct if \(\mathsf {EQS. VfK}(\textit{sk},\textit{pk})=1\), \(\mathsf {EQS. Ver}(M,\sigma )=1\) and \(\mathsf {EQS. Ver}(M^\mu ,\sigma ')=1\).
Unforgeability is defined w.r.t. equivalence classes, i.e., a forgery must be on a message from an equivalence class for which the forger has not seen signatures.
Definition 5
(EUF-CMA). Consider the following game for an adversary A:

Let Q be the set of all queries that A issues to \(\mathcal O\) . Then we say that A wins the EUF-CMA game if the following hold:
-
1.
For all \(M \in Q\): \([M^*]_\mathcal {R}\ne [M]_\mathcal {R}\);
-
2.
\(\mathsf {EQS. Ver}(M^*,\sigma ^*,\textit{pk}) = 1\)
An SPS-EQ scheme is EUF-CMA if for all \(\ell > 1\) and all PPT algorithms \(A\)

The final property requires that signatures adapted by \(\mathsf {EQS. Adp}\) are distributed like fresh signatures from \(\mathsf {EQS. Sig}\).
Definition 6
(Signature Adaptation). An SPS-EQ scheme perfectly adapts signatures if for all tuples \(\ell >1\), \((\textit{sk},\textit{pk},M,\sigma ,\mu )\) with
\(\mathsf {EQS. Adp}(M,\sigma ,\mu ,\textit{pk})\) and \(\mathsf {EQS. Sig}(\textit{sk},M^\mu )\) are identically distributed.
The most efficient construction of SPS-EQ is the following from [FHS14]. It has perfect signature adaptation and satisfies EUF-CMA in the generic group model (GGM).

KEA. The knowledge of exponent assumption [BP04] for a bilinear group generator \(\mathsf {BG. Gen}\) states that for every PPT algorithm A, which given the output \((p,\mathbb {G}_1,\mathbb {G}_2,\mathbb {G}_T,e,g,\hat{g})\) of \(\mathsf {BG. Gen}\) and a random \(h\leftarrow \mathbb {G}_1\) as input outputs \(g^s,h^s\) for some s, there exists a PPT extractor which, when given the coins of A as input, extracts s with non-negligible probability. Note that KEA trivially holds in the GGM, and since for our most efficient construction we already work in the GGM to use SPS-EQ, this is not an extra assumption.
Construction 2
(ACE for Equality – Pairing). We construct an ACE scheme  defined by the following algorithms:
defined by the following algorithms:
-
Setup: Given a bilinear group \(BG=(p,\mathbb {G}_1,\mathbb {G}_2,\mathbb {G}_T,g,\hat{g},e)\), run \((\textit{sk},\textit{vk})\leftarrow \mathsf {EQS. Gen}(BG)\), pick a PRF key K and return \(\textit{pp}=(BG,\textit{vk})\) and \(\textit{msk}=(\textit{sk},K)\).
-
Key Generation: Define \(\textit{dk}_i = F_K(0||i)\) and \(\textit{pk}_i=g^{\textit{dk}_i}\), and compute \(\sigma _i=\mathsf {EQS. Sig}(\textit{sk},(g,\textit{pk}_i);F_K(1||i))\); Return \(\textit{ek}_i = (\textit{pk}_i,\sigma _i)\) and \(\textit{dk}_i\).
-
Encryption: On input a message m and an encryption key \(\textit{ek}_i=(\textit{pk}_i,\sigma _i)\), pick randomness \(r,s\leftarrow \mathbb {Z}_p^*\) and compute \(\sigma '\leftarrow \mathsf {EQS. Adp}(\textit{vk},(g,\textit{pk}_i),\sigma _i,s)\) and return
$$ c_0 = g^r, \ \ c_1 = \textit{pk}_i^r\cdot m, \ \ c_2 = g^s, \ \ c_3 = \textit{pk}_i^s, \ \ \sigma '. $$ -
Sanitizer: If \(\mathsf {EQS. Ver}(\textit{vk},(c_2,c_3),\sigma ')=0\) then output \(\bot \). Else choose a random t and return
$$ c'_0 = c_0\cdot c_2^t ,\ \ c'_1 = c_1\cdot c_3^t. $$ -
Decryption: Return \( m= c'_1 \cdot (c'_0)^{-\textit{dk}_j} \).
Correctness follows by inspection, and detectability of the ACE follows from the detectability of the underlying PKE we use, namely ElGamal. We will now show that the scheme also satisfies the no-read and the no-write rule.
Theorem 3
Construction 2 satisfies the No-Read Rule if the PRF is pseudorandom, the SPS-EQ scheme has perfect adaptivity and the DDH assumption holds in \(\mathbb {G}_1\).
Proof
Plugging Construction 2 into the security game yields the game in Fig. 1 (where we replaced PRF values by consistent random values). The proof is similar to that of Theorem 3 also proceeds by a series of hybrid games.
No-Read Rule for Construction 2 for fixed b and PRF outputs replaced by random
-
Game H : As the original game but at the beginning the challenger makes a random guess q from \(\{1,\ldots ,q_\text {max}\}\) where \(q_\text {max}\) is a bound on the number of \(\mathcal {O}_G(\cdot ,\mathsf {sen})\) queries plus the number of \(\mathcal {O}_E(\cdot ,\cdot )\) queries. Let \((j^*,\cdot )\) be the qth such query. If \(j^*\ne i_b\), the challenger returns a random bit as the output of the game.
-
No-Write Game \(\rightarrow H\) : This results in a polynomial loss \(\frac{1}{q_\text {max}}\) in the adversary’s winning probability, shown analogously to Lemma 1. If the latter was non-negligible before, it is so afterwards.
-
Game \(H_{b,1}\) : As hybrid H with b fixed and the values of the PRF replaced with (consistent) random values.
-
\(H_b\approx _c H_{b,1}\) : The games are indistinguishable by PRF security.
-
Game \(H_{b,2}\) : As \(H_{b,1}\), but instead of running \(\mathsf {EQS. Adp}\), \(\sigma '\) is computed as a fresh signature on \((g^s,\textit{pk}_{i_b}^s)\).
-
\(H_{b,1}\approx _c H_{b,2}\) : The two games are equally distributed by the perfect signature-adaptation property of SPS-EQ.
-
Game \(H_{b,3}\) : Defined as \(H_{b,2}\), except c is replaced by \(c=(g^r,\textit{pk}_{i_b}^r m_b,g^s,\textit{pk}_{i_b}^t,\sigma ')\), that is, the 4th component is random.
-
\(H_{b,2}\approx _c H_{b,3}\) : Indistinguishable under DDH. Note that \(\textit{pk}_{i_b}\) is known in advance (as \(i_b\) is guessed as \(j^*\)) and that \(\textit{dk}_i\) is not revealed and s is not used anywhere else (since \(H_{b,2}\)). The reduction can thus replace the values \((g,\textit{pk}_{i_b},g^s,\textit{pk}_{i_b}^s)\) with a DDH challenge.
-
Game \(H_{b,4}\) : Defined as \(H_{b,3}\), except c is replaced by \(c=(g^r,\textit{pk}_{i_b}^u m_b,g^s,\textit{pk}_{i_b}^t,\sigma ')\), that is, the 2nd component is random.
-
\(H_{b,3}\approx _c H_{b,4}\) : Indistinguishable under DDH. The reduction replaces the values \((g,\textit{pk}_{i_b}, g^r,\textit{pk}_{i_b}^r)\) with a DDH challenge.
Since \(H_{0,4}\equiv H_{1,4}\) (in both the adversary receives c which consists of 4 random group elements and a signature on the last 2), we showed that \(H_0\) and \(H_1\) are indistinguishable, which contradicts the assumption that A distinguishes them. \(\square \)
Theorem 4
Construction 2 satisfies the No-Write Rule if the PRF is pseudorandom, the SPS-EQ scheme is unforgeable, and KEA and DDH hold in \(\mathbb {G}_1\).
Proof
As it is straightforward to prove indistinguishability to the original game, let us immediately assume that all calls to the PRF are replaced by (consistent) random values, which yields the game described in Fig. 2. (Note that in the definition of \(\mathcal {O}_E\), we need not generate \(\sigma \) in \(\mathsf {Gen}\), as it is then discarded by \(\mathsf {San}\) anyway.)
No-Write Rule for Construction 2 and PRF outputs replaced by random
We first distinguish between two types of PPT adversaries:
-
Type 1 returns \(c_0\), which contains an SPS-EQ forgery with non-negligible probability; that is, \((c_{0,2},c_{0,3})\) is not a multiple of any \((g,\textit{pk}_i)\) where \(\textit{pk}_i\) is the key obtained from oracle call \(\mathcal {O}_G(i,\mathsf {sen})\).
-
Type 2 returns such a forgery with negligible probability only.
Breaking EUF-CMA of SPS-EQ can be reduced to Type 1 forgeries in a straightforward fashion: the PPT reduction B simulates the no-write game using the given \(\textit{vk}\) and replacing all calls of \(\mathsf {EQS. Sig}(\textit{sk},(g,\textit{pk}_i))\) by queries to its signature oracle; when A outputs \(c_0=(c_{0,0},c_{0,1},c_{0,2},c_{0,3},\sigma _0)\) then B returns \(\sigma _0\) as a forgery on \(M=(c_{0,2},c_{0,3})\). By assumption (Type 1), with non-negligible probability M is not a multiple of the messages \((g,\textit{pk}_i)\) queried to the signing oracle; B thus breaks EUF-CMA.
We now show how to use Type 2 adversaries to break DDH assuming KEA. Let \(q_\text {max}\) denote an upper bound on the number of A’s queries \((\cdot ,\mathsf {sen})\) to \(\mathcal{O}_S\) and \(\mathcal{O}_R\) plus the number of queries to \(\mathcal{O}_E\).
We first construct a PPT algorithm B with input (g, h). B picks two uniform values \(q_0,q_1\leftarrow [q_\text {max}]\) and simulates the no-write game for A, except for the following changes: when the \(q_0\)th key \(\textit{pk}\) is created during an oracle query \((j_0,\cdot )\), B sets \(\textit{pk}_{j_0}=h\). Let \(j_1\) be the index of the \(q_1\)th key created. If A later queries \((j_0,\mathsf {rec})\) or \((j_1,\mathsf {rec})\) to \(\mathcal{O}_S\) or \(\mathcal{O}_R\) then B aborts. When A outputs \((c_0,i')\) then B stops and returns \((c_{0,2},c_{0,3})\).
Let us analyze B’s behavior: Since A is of Type 2, we know that with overwhelming (i.e. all except with negligible) probability, A outputs \((c_0,i')\) with \((c_{0,2},c_{0,c}) = (g^a,\textit{pk}_j^a)\), for some a and j s.t. \((j,\mathsf {sen})\) was queried to \(\mathcal{O}_S\) or \(\mathcal{O}_R\). Now with probability \(\frac{1}{q_\text {max}^2}\), we have \(j=j_0\) and \(i'=j_1\). This event is independent of A’s view and if it occurs then B’s simulation does not abort: by assumption A makes queries \((j,\mathsf {sen})\) and \((i',\mathsf {sen})\) and can therefore not make queries \((j,\mathsf {rec})\) and \((i',\mathsf {rec})\).
With probability at least \(\frac{1}{q_\text {max}^2}-\mathsf {negl}(\kappa )\), B thus returns \((g^a,h^a)\) for some a. Assuming KEA there exists thus an extractor X that, given B’s coins, outputs a.
We now consider the following hybrid H of the no-write-rule game: first choose \(h\leftarrow \mathbb {G}_1\) and \(j_0,j_1\leftarrow [q_\text {max}]\) then run the game setting \(\textit{pk}_{j_1}=h\). On the same coins as used to run the game run X and let a be its output. If A’s output \((c_0,i')\) satisfies
and \(i'=j_1\) then return A’s final output \(b'\). Else return a random bit \(b'\leftarrow {\{0,1\}}\)
Since H, until the event that A outputs \(c_0\) is defined as B, X’s output a satisfies (3) with non-negligible probability, as shown above. The probability that hybrid game H outputs A’s bit \(b'\) is thus non-negligible.
Further note that setting \(h=\textit{pk}_{j_0}\) is only a syntactical change, so H differs from the original game only in the event that the latter aborts (outputting a random bit). An analysis analogue to “\(0\rightarrow 1\)” in the proof of Theorem 3 shows that if A wins the original game with non-negligible probability then it wins H with non-negligible probability.
Define \(H_\beta \) as H with b fixed to \(\beta \). Our last step is now to show that under DDH A cannot distinguish \(H_0\) from \(H_1\), which contradicts A winning H and concludes the proof.
For this, we define another hybrid \(H'_\beta \) which modifies \(H_\beta \) in that \(c'_\beta \) is defined as \((c_{\beta ,0}\cdot c_{\beta ,2}^t,\,c_{\beta ,1}\cdot U)\), where U is a uniform group element. Thus, \(c'_\beta \) is a uniformly random pair and so the game \(H'_\beta \) is independent of \(\beta \). Therefore \(H'_0\) is distributed as \(H'_1\). What remains to show is that \(H_\beta \) is indistinguishable from \(H'_\beta \).
We first show that \(H_0\) is indistinguishable from \(H'_0\). The games only differ when X returns a satisfying (3) (otherwise both output a random bit). In this case \(h=\textit{pk}_{j_0}\). Consider a DDH adversary \(D_0\) that receives a challenge \((P,T=g^t,U)\) where either \(U=P^t\) or U is random. \(D_0\) simulates \(H_0\) setting \(h=P\) and associating the values t from the challenge and the game: it sets \(c_{0,2}^t = T^a\) and \(c_{0,3}=U^a\). If \(U=P^t\) then \(D_0\) simulates \(H_0\); otherwise it simulates \(H'_0\).
Finally, \(H'_1\) is shown indistinguishable from \(H_1\) by a similar reduction: on input a DDH challenge (P, T, U), \(D_1\) simulates \(H_1\), except that it sets \(\textit{pk}_{j_1}=P\) and \(c_{1,2}^t = T^s\) and \(c_{1,3}=U^s\). If \(U=P^t\) then \(D_1\) simulates \(H_1\); otherwise it simulates \(H'_1\). \(\square \)
Using Theorems 3 and 4 with the SPS-EQ from [FHS14], which has perfect signature adaptation and satisfies EUF-CMA in the generic group model (GGM), we obtain the following corollary. The concrete efficiency of the resulting scheme is given in Table 2.
Corollary 3
In the generic group model, Construction 2 instantiated with the SPS-EQ from [FHS14] satisfies the No-Read and No-Write rules.
3.4 Comparing the Two Constructions
In Table 2 we compare the efficiency and the assumptions required for our constructions. The most efficient way to instantiate the generic construction from Sect. 3.2 is via structure-preserving signatures (SPS) [AFG+16], Groth-Sahai proofs [GS08] and the weakly sanitizable version of ElGamal encryption [Gam85] described in Sect. 3.3. The security of the latter two relies on the SXDH assumption. The most efficient SPS scheme from SXDH is the one from [KPW15] (signatures from \(\mathbb {G}_1^6 \times \mathbb {G}_2\), public keys from \(\mathbb {G}_2^7\)). The most efficient SPS scheme with a security proof in the generic group model (GGM) is from [AGHO11] (signatures from \(\mathbb {G}_1^2 \times \mathbb {G}_2\), public keys from \(\mathbb {G}_1\times \mathbb {G}_2^3\)). See Corollaries 1 and 2. We also include Construction 2 from Sect. 3.3, which does not require zero-knowledge proofs, and which we proved secure in the GGM.
4 ACE for Disjunction of Equalities
In this section we show how to use the equality ACE scheme in a black-box way to implement more interesting predicates. Intuitively, as stated in the introduction, this is done by assigning sets of identities for the ACE scheme to each sender and receiver, in such a way that the intersection between the set \(\mathsf {S}(i)\) of identities given to sender i and the set \(\mathsf {R}(j)\) of identities given to receiver j is non-empty if and only if \(P(i,j)=1\). Note however that in this case a receiver, to be able to decrypt, would have to try each decryption key on each ciphertext, thus resulting in quadratic complexity. To avoid this, we compose our scheme using the following disjunction of equalities predicate instead: here each sender is assigned a vector of identities \(\mathbf {x}\) and each receiver a vector of identities \(\mathbf {y}\), and the predicate is defined as \(\mathsf {P}_{\textsf {or-eq}}: \mathcal {D}^\ell \times \mathcal {D}^{\ell } \rightarrow {\{0,1\}}\), and
We give a generic construction that relies on any ACE for equality, namely, for the predicate \(\mathsf {P}_{\textsf {eq}}: \left( \mathcal {D}\times [\ell ] \right) \times \left( \mathcal {D}\times [\ell ] \right) \rightarrow {\{0,1\}}\), defined by
such as those of Sect. 3.Footnote 3
Construction 3
(ACE for Disjunction of Equality–Generic). We construct an ACE scheme  for
for  from an ACE scheme
from an ACE scheme  for
for  .
.  is defined by the following algorithms:
is defined by the following algorithms:
-
Setup: Output
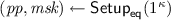 .
. -
Key Generation: Given the master secret key \(\textit{msk}\) and vectors \(\mathbf {x},\mathbf {y}\in \mathcal {D}^\ell \), the encryption and decryption keys are computed as follows:
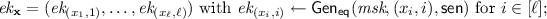

-
Encryption: On input a message m and an encryption key \(\textit{ek}_{\mathbf {x}}=(\textit{ek}_{(x_1,1)},\ldots ,\textit{ek}_{(x_\ell ,\ell )})\) pick some independent randomness \(r_1,\ldots ,r_\ell \), compute
$$c_i=\mathsf {Enc}(\textit{ek}_{(x_i,i)},m;r_i),$$for \(i \in [\ell ]\), and output \(c=(c_1,\ldots ,c_\ell )\).
-
Sanitizer: Given a ciphertext \(c=(c_1,\ldots ,c_\ell )\), apply
 component-wise.
component-wise. -
Decryption: Given a ciphertext \(c=(c_1,\ldots ,c_\ell )\) and a decryption key \(\textit{dk}_{\mathbf {y}} = (\textit{dk}_{(y_1,1)},\ldots ,\textit{dk}_{(y_\ell ,\ell )})\) for \(\mathbf {y}\in \mathcal {D}^\ell \), compute \(\mathsf {Dec}(\textit{dk}_{(y_i,i)},c_i)\) for \(i \in [\ell ]\). Let \(m_i=\mathsf {Dec}(\textit{dk}_{(y_i,i)},c_i)\), then output the first \(m_i\ne \bot \) or \(\bot \) if there is no such successful decryption.
Remark: Note that the complexity of the composed scheme, including the decryption algorithm, is linear in \(\ell \).
Lemma 6
(Correctness and Detectability). Construction 3 is correct, according to Definition 1.
Proof
For all \(i \in [\ell ]\) and \(x_i,y_i \in \mathcal {D}\) such that \(x_i=y_i\),

by correctness of  . Moreover, by detectability of
. Moreover, by detectability of  , for all \(x_i,y_i \in \mathcal {D}\) such that \(x_i \ne y_i\), we have:
, for all \(x_i,y_i \in \mathcal {D}\) such that \(x_i \ne y_i\), we have:

Therefore, by a union bound over the \(\ell \) disjunctions, we obtain that for all \(\mathbf {x},\mathbf {y}\in \mathcal {D}^\ell \) such that \(\mathsf {P}_{\textsf {or-eq}}(\mathbf {x},\mathbf {y})=1\):

that is,  is correct. A similar argument is used to show that
is correct. A similar argument is used to show that  is detectable. \(\square \)
is detectable. \(\square \)
Lemma 7
(No-Read-Rule). If the underlying  for
for  satisfies the No-Read-Rule from Definition 4, then so does
satisfies the No-Read-Rule from Definition 4, then so does  from Construction 3. In particular, for any PPT adversary A against the No-Read-Rule for
from Construction 3. In particular, for any PPT adversary A against the No-Read-Rule for  , there exists a PPT adversary B such that
, there exists a PPT adversary B such that

Proof
We define \(\ell +1\) hybrid games, where for all \(i \in [\ell +1]\), Hybrid i is defined as in the table below.

We say an adversary A wins hybrid i if it returns 1 and \(|m_0|=|m_1|\), \(\mathbf {x}^{(0)}\), \(\mathbf {x}^{(1)}\in \mathcal {D}^\ell \), and for all queries q to \(\mathcal {O}_G\) with \(q=(\mathbf {y},\mathsf {rec})\) it holds that
Note that for any PPT adversary A,

For all \(i \in [\ell ]\), we build a PPT adversary \(B_i\), such that:

thereby proving the lemma. This comes from the facts that  satisfies the No-Read Rule, and that for all \(\mathbf {y}\in \mathcal {D}^\ell \), \(\mathsf {P}_{\textsf {or-eq}}(\mathbf {x}^{(0)},\mathbf {y})=\mathsf {P}_{\textsf {or-eq}}(\mathbf {x}^{(1)},\mathbf {y})=0\) implies \(\mathsf {P}_{\textsf {eq}}((x^{(0)}_i,i),(y_j,j))=\mathsf {P}_{\textsf {eq}}((x^{(1)}_i,i),(y_j,j))=0\) for all \(i,j \in [\ell ]\). \(\square \)
satisfies the No-Read Rule, and that for all \(\mathbf {y}\in \mathcal {D}^\ell \), \(\mathsf {P}_{\textsf {or-eq}}(\mathbf {x}^{(0)},\mathbf {y})=\mathsf {P}_{\textsf {or-eq}}(\mathbf {x}^{(1)},\mathbf {y})=0\) implies \(\mathsf {P}_{\textsf {eq}}((x^{(0)}_i,i),(y_j,j))=\mathsf {P}_{\textsf {eq}}((x^{(1)}_i,i),(y_j,j))=0\) for all \(i,j \in [\ell ]\). \(\square \)
Lemma 8
(No-Write Rule). If the underlying  for
for  satisfies the No-Write Rule from Definition 4 and the No-Read-Rule from Definition 3, then
satisfies the No-Write Rule from Definition 4 and the No-Read-Rule from Definition 3, then  from Construction 3 satisfies the No-Write rule. In particular, for any PPT adversary A against the No-Write Rule for
from Construction 3 satisfies the No-Write rule. In particular, for any PPT adversary A against the No-Write Rule for  , there exist PPT adversaries \(B_1\) and \(B_2\) such that
, there exist PPT adversaries \(B_1\) and \(B_2\) such that

Proof
As for the No-Read rule, we use a hybrid argument; for \(i \in [2\ell ]\) Hybrid i is defined in the tables below, where \(m_0 \in \mathcal {M}\) is an arbitrary, fixed message:


Let \(I_S\) and J be defined as in the No-Write Rule game from Definition 4. We say an adversary A wins Hybrid i, for \(i \in [2\ell ]\), if it returns 1 and all of the following hold:
-
1.
\(\mathbf {x}'\in I_S \cup \{0\}\);
-
2.
\(\forall \mathbf {x}\in I_S,\mathbf {y}\in J\), \(\mathsf {P}_{\textsf {or-eq}}(\mathbf {x},\mathbf {y})=0\).
We denote by \(\varepsilon _i\) the probability that A wins Hybrid i, for \(i \in [2\ell ]\). Note that for any PPT adversary A:

The proof proceeds in two steps:
First Step: for all \(i \in [\ell ]\), we build PPT adversaries \(B_{1.i}\) and \(B_{2.i}\) such that  .
.
First, the No-Write Rule allows to switch the sanitized ciphertext in Hybrid \(i-1\) from
where \(c_i^{(2)} := \mathsf {Enc}(\mathsf {Gen}(\textit{msk},(x'_i,i),\mathsf {sen}), m^*)\) and \(m^* \leftarrow \mathcal {M}\).
Namely, adversary \(B_{1.i}\) playing against the No-Write Rule for \(\mathsf {P}_{\textsf {eq}}\), after receiving the public parameters \(\textit{pp}\), sends them to A and simulates all the queries to \(\mathcal {O}_E(\cdot )\) and \(\mathcal {O}_S(\cdot )\) in the straightforward way: using its own oracles \(\mathcal {O}_E(\cdot )\) and \(\mathcal {O}_S(\cdot )\) for \(\mathsf {P}_{\textsf {eq}}\), coordinate-wise. Note that the restriction on A’s queries, namely \(\forall \mathbf {x}\in I_S,\mathbf {y}\in J\), \(\mathsf {P}_{\textsf {or-eq}}(\mathbf {x},\mathbf {y})=0\), implies that \(\mathsf {P}_{\textsf {eq}}((x_i,i),(y_j,j))=0\) for all \(i,j \in [\ell ]\). Thus, \(B_{1.i}\) can answer valid queries from A by valid queries to its own oracles.
Then, \(B_{1.i}\) receives the challenge \(((c_1^{(0)},\ldots ,c_\ell ^{(0)}),\mathbf {x}')\) from A, and it sends \((c_i^{(0)},(x'_i,i))\) to the challenger for \(\mathsf {P}_{\textsf {eq}}\), to receive \(\mathsf {ct}^b_i\) where \(b \leftarrow {\{0,1\}}\), and
for \(m^* \leftarrow \mathcal {M}\). Since \(B_{1.i}\) knows \(m_0\) (here we crucially rely on the fact that \(m_0\) is a fixed message, and not a random message as in the No-Write Rule experiment, since it would be unknown to \(B_{1.i}\)), it can compute
using its \(\mathcal {O}_E\) oracle on input \(((x'_j,j),m_0)\). Finally, it sets \(\mathsf {ct}_j := c_j^{(0)}\) for \(j > i\), and sends the sanitized ciphertext \((\mathsf {ct}_1,\ldots ,\mathsf {ct}_{i-1},\mathsf {ct}_i^b, \mathsf {ct}_{i+1},\ldots ,\mathsf {ct}_\ell )\) to A, and keeps simulating the oracles \(\mathcal {O}_E(\cdot )\) and \(\mathcal {O}_R(\cdot )\) as before.
Then, because  satisfies the No-Read Rule, and because for all \(\mathbf {y}\in J\), \(\mathsf {P}_{\textsf {or-eq}}(\mathbf {x}',\mathbf {y})=0\), which implies \(\mathsf {P}_{\textsf {eq}}((x'_i,i),(y_j,j))=0\) for all \(i,j \in [\ell ]\), we can switch a sanitized ciphertext from
satisfies the No-Read Rule, and because for all \(\mathbf {y}\in J\), \(\mathsf {P}_{\textsf {or-eq}}(\mathbf {x}',\mathbf {y})=0\), which implies \(\mathsf {P}_{\textsf {eq}}((x'_i,i),(y_j,j))=0\) for all \(i,j \in [\ell ]\), we can switch a sanitized ciphertext from
where \(c_i^{(1)} = \mathsf {Enc}(\mathsf {Gen}(\textit{msk},(x'_j,j),\mathsf {sen}), m_0)\), as in Hybrid i. Namely, adversary \(B_{2.i}\) simulates \(\textit{pp}\), \(\mathcal {O}_E(\cdot )\), \(\mathcal {O}_S(\cdot )\), \(\mathcal {O}_R(\cdot )\), and computes sanitized ciphertexts \(\mathsf {ct}_j\) for \(j > i\) as described previously for \(B_{1.i}\). For the ciphertexts \(\mathsf {ct}_j\) for \(j< i\), \(B_{2.i}\) uses its oracle \(\mathcal {O}_E\), and then, applies \(\mathsf {San}\) to obtain the sanitized ciphertexts. It can do so since applying \(\mathsf {San}\) only requires to know pp. Then, \(B_{2.i}\) sends \((m_0,m_1,(x'_i,i),(x'_i,i))\) to the No-Read Rule experiment, where \(m_1 \leftarrow \mathcal {M}\), to get back \(c \leftarrow \mathsf {Enc}(\mathsf {Gen}(\textit{msk}, (x'_i,i)),m_b)\). It sets \(\mathsf {ct}_i := \mathsf {San}(\textit{pp},c)\), and sends the sanitized \((\mathsf {ct}_1,\ldots ,\mathsf {ct}_\ell )\) to A.
Second Step: we build a PPT adversary \(B_{3.i}\) such that  .
.
We use the No-Read Rule as for the first step. Namely, \(B_{3.i}\) simulates \(\textit{pp}\), \(\mathcal {O}_E(\cdot )\), \(\mathcal {O}_S(\cdot )\), \(\mathcal {O}_R(\cdot )\) as descried previously for \(B_{2.i}\). Then, \(B_{3.i}\) ignores the challenge \(((c_1^{(0)},\ldots ,c_\ell ^{(0)}),\mathbf {x}')\) sent by A, samples \(m_1 \leftarrow \mathcal {M}\), computes
thanks to its oracle \(\mathcal {O}_E\). Then, \(B_{3.i}\) sends \((m_0,m_1,(x'_i,i),(x'_i,i))\) to the No-Read Rule experiment, to get back \(c \leftarrow \mathsf {Enc}(\mathsf {Gen}(\textit{msk},(x'_i,i)),m_b)\). It sets \(\mathsf {ct}_i := \mathsf {San}(\textit{pp},c)\), and sends the sanitized ciphertext \((\mathsf {ct}_1,\ldots ,\mathsf {ct}_\ell )\) to A. \(\square \)
5 Predicates in Disjunction of Equalities
We show how to reduce the predicate \(\mathsf {P}_{\textsf {range}}\) defined for all points \(z \in [N]\) and intervals \(I \subset [N]\) as:
to \(\mathsf {P}_{\textsf {or-eq}}\) described in Sect. 4. This requires writing intervals I and points z as vectors, using a standard tree structure [DVOS00].
Lemma 9
(Interval to Vector [DVOS00]). There is an efficient PPT algorithm \(\mathsf {IntVec}\), that on input an interval \(I\subset [N]\) outputs
where \(n:= \lceil \log N \rceil \), with the following properties:
-
for each \(i=1,\ldots ,n\), we have \(w_{2i-1},w_{2i} \in {\{0,1\}}^i \cup \{\bot \}\);
-
for all \(z \in [N]\), we have \(z \in I\) iff one of \(w_1,\ldots ,w_{2t}\) is a prefix of z.
Here, \(\bot \) is special symbol such that \(\bot \notin \bigcup _{i=1}^n \{0,1\}^i\).
For instance, \(\mathsf {IntVec}([010, 110]) = (\bot ,\bot ,01,10,110,\bot )\).
Remark 1
(Hashing bit strings into \(\mathcal {D}\) ). We want to use the ACE of Sect. 4, which requires finding an injective map from \(\bigcup _{i=1}^n {\{0,1\}}^i \cup \{\bot \}\) into \(\mathcal {D}\), where \(n := [\lceil \log N \rceil ]\). Such map exists as long as \( |\mathcal {D}| \ge 2^{n+1}-1\).
Now we give the description of algorithm \(\mathsf {PtVec}\), used to map points to vectors.
\(\mathsf {PtVec}\): On input \(z \in [N]\), output \((v_1,\ldots ,v_{2n})\), where

Tree structure [DVOS00] for interval [010, 110] (bar nodes), point 011 (hat nodes) and point 111 (tilde nodes). The common node 01 allows to decrypt for \(011 \in [010,110]\). No such node exists for \(111 \notin [010,110]\), which prevents decryption.
For instance, \(\mathsf {PtVec}(011) = (0,0,01,01,011,011)\) (See Fig. 3).
Remark 2
(Duplicate Entries). Note that some strings appear more than once in the vector. This is necessary since the predicate is a function of both the entries in the vector and their positions.
Lemma 10
For any point \(z \in [N]\) and any interval \(I \subseteq [N]\),
Notes
- 1.
This section is taken almost verbatim from [DHO16].
- 2.
This is without loss of generality, since we can always add a PRF key to \(\textit{msk}\) and derive the randomness for \(\mathsf {Gen}\) from the PRF and the identity of the party.
- 3.
To use an ACE for predicate \(\mathsf {P}_{\textsf {eq}}:\{0,1\}^n \times \{0,1\}^n \rightarrow \{0,1\}\), such as those in Sect. 3, one uses an injective hash function from \(\mathcal {D}\times [\ell ]\) to \(\{0,1\}^n\), which exists as long as \(2^n \ge |\mathcal {D}|\cdot [\ell ]\).
References
Abe, M., Fuchsbauer, G., Groth, J., Haralambiev, K., Ohkubo, M.: Structure-preserving signatures and commitments to group elements. In: Rabin, T. (ed.) CRYPTO 2010. LNCS, vol. 6223, pp. 209–236. Springer, Heidelberg (2010). doi:10.1007/978-3-642-14623-7_12
Abe, M., Fuchsbauer, G., Groth, J., Haralambiev, K., Ohkubo, M.: Structure-preserving signatures and commitments to group elements. J. Cryptol. 29(2), 363–421 (2016)
Abe, M., Groth, J., Haralambiev, K., Ohkubo, M.: Optimal structure-preserving signatures in asymmetric bilinear groups. In: Rogaway, P. (ed.) CRYPTO 2011. LNCS, vol. 6841, pp. 649–666. Springer, Heidelberg (2011). doi:10.1007/978-3-642-22792-9_37
Bellare, M., Boldyreva, A., Desai, A., Pointcheval, D.: Key-privacy in public-key encryption. In: Boyd, C. (ed.) ASIACRYPT 2001. LNCS, vol. 2248, pp. 566–582. Springer, Heidelberg (2001). doi:10.1007/3-540-45682-1_33
Boneh, D., Franklin, M.: Identity-based encryption from the Weil pairing. In: Kilian, J. (ed.) CRYPTO 2001. LNCS, vol. 2139, pp. 213–229. Springer, Heidelberg (2001). doi:10.1007/3-540-44647-8_13
Blum, M., Feldman, P., Micali, S.: Non-interactive zero-knowledge and its applications (extended abstract). In: 20th Annual ACM Symposium on Theory of Computing, pp. 103–112 (1988)
Bellare, M., Palacio, A.: The knowledge-of-exponent assumptions and 3-round zero-knowledge protocols. In: Franklin, M. (ed.) CRYPTO 2004. LNCS, vol. 3152, pp. 273–289. Springer, Heidelberg (2004). doi:10.1007/978-3-540-28628-8_17
Boneh, D., Sahai, A., Waters, B.: Functional encryption: definitions and challenges. In: Ishai, Y. (ed.) TCC 2011. LNCS, vol. 6597, pp. 253–273. Springer, Heidelberg (2011). doi:10.1007/978-3-642-19571-6_16
Damgård, I., Haagh, H., Orlandi, C.: Access control encryption: enforcing information flow with cryptography. In: Hirt, M., Smith, A. (eds.) TCC 2016. LNCS, vol. 9986, pp. 547–576. Springer, Heidelberg (2016). doi:10.1007/978-3-662-53644-5_21
De Berg, M., Van Kreveld, M., Overmars, M., Schwarzkopf, O.C.: Computational Geometry. Springer, Heidelberg (2000)
Fuchsbauer, G., Hanser, C., Slamanig, D.: Structure-preserving signatures on equivalence classes and constant-size anonymous credentials. IACR Cryptology ePrint Archive, 2014:944 (2014)
Fuchsbauer, G., Hanser, C., Slamanig, D.: Practical round-optimal blind signatures in the standard model. In: Gennaro, R., Robshaw, M. (eds.) CRYPTO 2015. LNCS, vol. 9216, pp. 233–253. Springer, Heidelberg (2015). doi:10.1007/978-3-662-48000-7_12
El Gamal, T.: A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inf. Theory 31(4), 469–472 (1985)
Garg, S., Gentry, C., Halevi, S., Raykova, M., Sahai, A., Waters, B.: Candidate indistinguishability obfuscation and functional encryption for all circuits. In: 54th Annual IEEE Symposium on Foundations of Computer Science, FOCS, pp. 40–49 (2013)
Gay, R., Méaux, P., Wee, H.: Predicate encryption for multi-dimensional range queries from lattices. In: Katz, J. (ed.) PKC 2015. LNCS, vol. 9020, pp. 752–776. Springer, Heidelberg (2015). doi:10.1007/978-3-662-46447-2_34
Goldreich, O.: Foundations of Cryptography: Volume 2, Basic Applications. Cambridge University Press, Cambridge (2009)
Groth, J., Sahai, A.: Efficient non-interactive proof systems for bilinear groups. In: Smart, N. (ed.) EUROCRYPT 2008. LNCS, vol. 4965, pp. 415–432. Springer, Heidelberg (2008). doi:10.1007/978-3-540-78967-3_24
Groth, J., Sahai, A.: Efficient non-interactive proof systems for bilinear groups. SIAM J. Comput. 41(5), 1193–1232 (2012)
Hanser, C., Slamanig, D.: Structure-preserving signatures on equivalence classes and their application to anonymous credentials. In: Sarkar, P., Iwata, T. (eds.) ASIACRYPT 2014. LNCS, vol. 8873, pp. 491–511. Springer, Heidelberg (2014). doi:10.1007/978-3-662-45611-8_26
Izabachène, M., Pointcheval, D., Vergnaud, D.: Mediated traceable anonymous encryption. In: Abdalla, M., Barreto, P.S.L.M. (eds.) LATINCRYPT 2010. LNCS, vol. 6212, pp. 40–60. Springer, Heidelberg (2010). doi:10.1007/978-3-642-14712-8_3
Katz, J., Lindell, Y.: Introduction to Modern Cryptography. CRC Press, Boca Raton (2014)
Kiltz, E., Pan, J., Wee, H.: Structure-preserving signatures from standard assumptions, revisited. In: Gennaro, R., Robshaw, M. (eds.) CRYPTO 2015. LNCS, vol. 9216, pp. 275–295. Springer, Heidelberg (2015). doi:10.1007/978-3-662-48000-7_14
Okamoto, T., Takashima, K.: Adaptively attribute-hiding (hierarchical) inner product encryption. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 591–608. Springer, Heidelberg (2012). doi:10.1007/978-3-642-29011-4_35
Sakai, R.: Cryptosystems based on pairings. In: Symposium on Cryptography and Information Security 2000, SCIS 2000 (2000)
Shi, E., Bethencourt, J., Chan, H.T.-H., Song, D.X., Perrig, A.: Multi-dimensional range query over encrypted data. In: 2007 IEEE Symposium on Security and Privacy (S&P 2007), 20–23 May 2007, Oakland, California, USA, pp. 350–364 (2007)
Shamir, A.: Identity-based cryptosystems and signature schemes. In: Blakley, G.R., Chaum, D. (eds.) CRYPTO 1984. LNCS, vol. 196, pp. 47–53. Springer, Heidelberg (1985). doi:10.1007/3-540-39568-7_5
Sahai, A., Waters, B.: Fuzzy identity-based encryption. In: Cramer, R. (ed.) EUROCRYPT 2005. LNCS, vol. 3494, pp. 457–473. Springer, Heidelberg (2005). doi:10.1007/11426639_27
Acknowledgements
We would like to thank the reviewers of PKC’17 for their diligent proofreading and valuable remarks, helping us to improve the paper.
Fuchsbauer is supported in part by the French ANR ALAMBIC project (ANR-16-CE39-0006). Gay is supported by ERC Project aSCEND (639554).
Kowalczyk is supported in part by the Defense Advanced Research Project Agency (DARPA) and Army Research Office (ARO) under Contract #W911NF-15-C-0236; NSF grants #CNS-1445424, #CNS-1552932, and #CCF-1423306; an NSF Graduate Research Fellowship #DGE-16-44869; and ERC Project aSCEND (639554). Any opinions, findings, and conclusions or recommendations expressed are those of the authors and do not necessarily reflect the views of the Defense Advanced Research Projects Agency, Army Research Office, the National Science Foundation, or the U.S. Government.
Orlandi is supported by the Danish Council for Independent Research (grant id: 6108-00169) and COST Action IC1306.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 International Association for Cryptologic Research
About this paper
Cite this paper
Fuchsbauer, G., Gay, R., Kowalczyk, L., Orlandi, C. (2017). Access Control Encryption for Equality, Comparison, and More. In: Fehr, S. (eds) Public-Key Cryptography – PKC 2017. PKC 2017. Lecture Notes in Computer Science(), vol 10175. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-662-54388-7_4
Download citation
DOI: https://doi.org/10.1007/978-3-662-54388-7_4
Published:
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-662-54387-0
Online ISBN: 978-3-662-54388-7
eBook Packages: Computer ScienceComputer Science (R0)






 . Pick a random PRF key K for a PRF F. Output
. Pick a random PRF key K for a PRF F. Output  and
and 



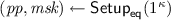 .
.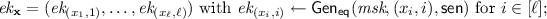

 component-wise.
component-wise.
