Abstract
Recent efficient constructions of zero-knowledge Succinct Non-interactive Arguments of Knowledge (zk-SNARKs), require a setup phase in which a common-reference string (CRS) with a certain structure is generated. This CRS is sometimes referred to as the public parameters of the system, and is used for constructing and verifying proofs. A drawback of these constructions is that whomever runs the setup phase subsequently possesses trapdoor information enabling them to produce fraudulent pseudoproofs.
Building on a work of Ben-Sasson, Chiesa, Green, Tromer and Virza [BCG+15], we construct a multi-party protocol for generating the CRS of the Pinocchio zk-SNARK [PHGR16], such that as long as at least one participating party is not malicious, no party can later construct fraudulent proofs except with negligible probability. The protocol also provides a strong zero-knowledge guarantee even in the case that all participants are malicious.
This method has been used in practice to generate the required CRS for the Zcash cryptocurrency blockchain.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
Thanks to Eran Tromer for pointing this out, and more generally the connection to subversion zero-knowledge. We note that if one wishes to run the protocol with one player, transcript verification can stay the same, but the player should be altered to take advantage of field rather than group operations when possible for better efficiency.
- 2.
In the actual code a more complex set of elements is used that can be efficiently derived from \(\mathsf {elements}_{i}\), as described in the full version. The reason we use the more complex set is that it potentially provides more security as it contains less information about \(\mathsf {secrets} _i\). However, the proof works as well with this definition of \(\mathsf {e}_{i} \) and it provides a significantly simpler presentation. We explain in the full version the slight modification for protocol and proof for using the more complex element set.
- 3.
The checks below could be simplified if we had also used
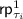 . We do not use it as in the actual code, as explained in the full version, we do not have a
. We do not use it as in the actual code, as explained in the full version, we do not have a  .
. - 4.
A technicality is that in the protocol description in [BCTV14] \(Z(\tau )\cdot g_2\) is appended with index \(m+2\) in \(\mathbf {B_2} \), and \(Z(\tau )\cdot g_1\) is appended in index \(m+3\) in C. However in the actual libsnark code, they are appended in index \(m+1\), and the prover algorithm is slightly modified to take this into account. But for the security proof we assume later on as in [BCTV14] that \(A_{m+1}=C_{m+3} =Z(\tau )\cdot g_1\), \(B_{m+2} = Z(\tau )\cdot g_2\), \(A_{m+2},A_{m+3},B_{m+1},B_{m+3},C_{m+1},C_{m+2}=0\).
References
Abdolmaleki, B., Baghery, K., Lipmaa, H., Zając, M.: A subversion-resistant SNARK. In: Takagi, T., Peyrin, T. (eds.) ASIACRYPT 2017. LNCS, vol. 10626, pp. 3–33. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-70700-6_1
Ben-Sasson, E., Chiesa, A., Green, M., Tromer, E., Virza, M.: Secure sampling of public parameters for succinct zero knowledge proofs. In: 2015 IEEE Symposium on Security and Privacy, SP 2015, San Jose, CA, USA, 17–21 May 2015, pp. 287–304 (2015)
Ben-Sasson, E., Chiesa, A., Tromer, E., Virza, M.: Succinct non-interactive zero knowledge for a von neumann architecture. In: Proceedings of the 23rd USENIX Security Symposium, San Diego, CA, USA, 20–22 Aug 2014, pp. 781–796 (2014)
Bellare, M., Fuchsbauer, G., Scafuro, A.: Nizks with an untrusted CRS: security in the face of parameter subversion. IACR Cryptology ePrint Archive 2016:372 (2016)
Bowe, S., Gabizon, A., Miers, I.: Scalable multi-party computation for zk-SNARK parameters in the random beacon model (2017)
Campanelli, M., Gennaro, R., Goldfeder, S., Nizzardo, L.: Zero-knowledge contingent payments revisited: attacks and payments for services. In: ACM Communications (2017)
Fuchsbauer, G.: Subversion-zero-knowledge SNARKs. In: Abdalla, M., Dahab, R. (eds.) PKC 2018. LNCS, vol. 10769, pp. 315–347. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-76578-5_11
https://github.com/scipr-lab/libsnark, https://github.com/zcash/libsnark
Parno, B., Howell, J., Gentry, C., Raykova, M.: Pinocchio: nearly practical verifiable computation. Commun. ACM 59(2), 103–112 (2016)
Schnorr, C.P.: Efficient identification and signatures for smart cards. In: Brassard, G. (ed.) CRYPTO 1989. LNCS, vol. 435, pp. 239–252. Springer, New York (1990). https://doi.org/10.1007/0-387-34805-0_22
Wilcox, Z.: https://z.cash/blog/the-design-of-the-ceremony.html
Acknowledgements
We thank Eli Ben-Sasson, Alessandro Chiesa, Jens Groth, Daira Hopwood, Hovav Shacham, Eran Tromer, Madars Virza, Nathan Wilcox and Zooko Wilcox for helpful discussions. We thank Daira Hopwood for pointing out some technical inaccuracies. We thank Eran Tromer for bringing to our attention the work of [CGGN17], and the relevance of our protocol to that work, and the connection to subversion zero-knowledge in general. We thank the anonymous reviewers of the 5th Workshop on Bitcoin and Blockchain Research for their comments.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 International Financial Cryptography Association
About this paper
Cite this paper
Bowe, S., Gabizon, A., Green, M.D. (2019). A Multi-party Protocol for Constructing the Public Parameters of the Pinocchio zk-SNARK. In: Zohar, A., et al. Financial Cryptography and Data Security. FC 2018. Lecture Notes in Computer Science(), vol 10958. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-662-58820-8_5
Download citation
DOI: https://doi.org/10.1007/978-3-662-58820-8_5
Published:
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-662-58819-2
Online ISBN: 978-3-662-58820-8
eBook Packages: Computer ScienceComputer Science (R0)





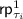 . We do not use it as in the actual code, as explained in the full version, we do not have a
. We do not use it as in the actual code, as explained in the full version, we do not have a  .
.