Abstract
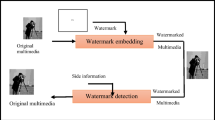
Nowadays, there is a huge requirement of multimedia data security with an advent use of internet that is being more important to save the data confidentiality and save from various attacks. This paper represents the improvement of LSB (Least Significant Bit) watermarking mechanism by using two host images instead of one image to embed the watermark using some logical operations on the bits of the images. It provides better security and on the other and it preserves the originality of the host image. To compare the image quality we used some image quality parameters like PSNR, MSE, NAE, AD, MD, NCC, and SC.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
M. Moniruzzaman, M. A. K. Hawlader, M. F. Hossain.: Wavelet based watermarking approach of hiding patient information in medical image for medical image authentication: 17th International Conference on Computer and Information Technology (ICCIT), 2014 DOI:10.1109/ICCITechn.2014.7073133.
Qing Liu, Jun Ying.: Grayscale image digital watermarking technology based on wavelet analysis. In: IEEE Symposium on Electrical & Electronics Engineering (EEESYM), DOI:10.1109/EEESym.2012.6258734 (2012).
Agung, B. W. R., Adiwijaya, F.P. Permana,.: Medical image watermarking with tamper detection and recovery using reversible watermarking with LSB modification and run length encoding (RLE) compression. In: IEEE International Conference on Communication, Networks and Satellite (ComNetSat), pp: 167–171, DOI:10.1109/ComNetSat.2012.6380799 (2012).
Tao Chen, Hongtao Lu,.: Robust spatial LSB watermarking of color images against JPEG compression. In: IEEE Fifth International Conference on Advanced Computational Intelligence (ICACI), pp. 872–875, DOI:10.1109/ICACI.2012.6463294 (2012).
S. Dadkhah, A.A. Manaf, S. Sadeghi.: Efficient Two Level Image Tamper Detection Using Three LSBWatermarking. In: Fourth International Conference on Computational Intelligence and Communication Networks (CICN), pp: 719–723, DOI:10.1109/CICN.2012.108 (2012).
Hu Lingna, Jiang Lingge.: Blind Detection of LSB Watermarking at Low Embedding Rate in GrayscaleImages. In: Second International Conference on Communications and Networking in China, CHINACOM pp: 413–416, DOI:10.1109/CHINACOM.2007.4469415 (2007).
El Kerek B, El Baba H, El Hassan M.: A New Technique to Multiplex Stereo Images- LSB Watermarking and Hamming Code. In: 1st International Conference on Artificial Intelligence, Modelling and Simulation (AIMS), pp: 267–271, DOI:10.1109/AIMS.2013.49 (2013).
Umaamaheshvari, A., Thanushkodi, K.: Robust image watermarking based on block based error correction code. In: International Conference on Current Trends in Engineering and Technology (ICCTET) 2013.
Bandyopadhyay, P., Das S., Paul S., Chaudhuri A., Banerjee M.: A Dynamic Watermarking Scheme for Color Image Authentication. In: International Conference on Advances in Recent Technologies in Communication and Computing, ARTCom pp: 314–318, DOI:10.1109/ARTCom.2009.94 (2009).
Bandyopadhyay P., Das S., Chaudhuri A., Banerjee M.: A new invisible color image watermarking framework through alpha channel. In: International Conference on Advances in Engineering, Science and Management (ICAESM), pp: 302–308 (2012).
Anwar M.J., Ishtiaq M., Iqbal M.A., Jaffar, M.A.: Block-based digital image watermarking using Genetic Algorithm. In: 6th International Conference on Emerging Technologies (ICET), pp: 204–209, DOI:10.1109/ICET.2010.5638488 (2010).
Liu Pei-pei, Zhu Zhong-liang, Hong-Xia Wang, Yan Tian-yun.: A Novel Image Fragile Watermarking Algorithm Based on Chaotic MapImage and Signal Processing. In: CISP Congress on Image and Signal Processing, CISP’08, Volume: 5 pp: 631–634, DOI:10.1109/CISP.2008.636 (2008).
Subudhi Asit Kumar, Kabi Krishna, Subudhi Abhilipsa, Patra Himanshu, Panda Jyoti Bikash.: An enhanced technique for color image water marking using HAAR transform. In: International Conference on Electrical, Electronics, Signals, Communication and Optimization (EESCO), pp: 1–5, DOI:10.1109/EESCO.2015.7253844 (2015).
A Novel Full-Reference Image Quality Index for Color Images,” Proc. of the (Springer) International Conference on Information Systems Design and Intelligent Applications (INDIA 2012), pp. 245–253 (2012).
Lai B, Chang L (2006) Adaptive data hiding for images based on haar discrete wavelet transform. In: Lecture Notes in Computer Science, Springer-verlag Berlin Heidelberg, vol 4319, pp 1085–1093.
El Safy RO, Zayed HH, El Dessouki A.: An adaptive steganography technique based on integer wavelet transform. In: International Conference on networking and media convergence. Pp-111–117 (2009).
Mei Jiansheng1, Li Sukang1 and Tan Xiaomei2.: A Digital Watermarking Algorithm Based On DCT and DWT. In: International Symposium on Web Information Systems and Applications, pp. 104–107, ISBN 978-952-5726-00-8 (2009).
K.Chaitanya1,Dr E. Srinivasa Reddy2,Dr K. Gangadhara Rao3.: Digital Color Image Watermarking In RGB Planes Using DWT-DCT-SVD Coefficients. In: International Journal of Computer Science and Information Technologies, ISSN: 0975-9646 (2014).
Chin-Chen Chang a,*, Tung-Shou Chen b,1, Lou-Zo Chung a.: A stenographic method based upon JPEG and quantization table modification. In: Elsevier Information Sciences 141 123–138 (2002).
Guochuan Shi1, Guanyu Chen1,Binhao Shi2, Jiangwei Li1 and Kai Shu1.: Research and Implementation of an Integrity Video Watermarking Authentication Algorithm. In: International Journal of Security and Its Applications Vol.8, No.4 pp. 239–246, (2014).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Kumar, N., Jaishree (2017). Digital Watermarking Using Enhanced LSB Technique. In: Satapathy, S., Bhateja, V., Udgata, S., Pattnaik, P. (eds) Proceedings of the 5th International Conference on Frontiers in Intelligent Computing: Theory and Applications . Advances in Intelligent Systems and Computing, vol 515. Springer, Singapore. https://doi.org/10.1007/978-981-10-3153-3_37
Download citation
DOI: https://doi.org/10.1007/978-981-10-3153-3_37
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-10-3152-6
Online ISBN: 978-981-10-3153-3
eBook Packages: EngineeringEngineering (R0)