Abstract
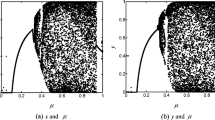
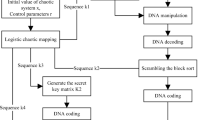
Digital image encryption technology is an important means to effectively protect the secure transmission of images. With the advantage of the sensitivity and pseudo randomness of the chaotic map to the initial condition and the inherent spatial configuration of DNA molecule and the unique information processing ability, an image encryption algorithm based on chaotic system and DNA sequence operations is proposed. First, the Logistic map is employed to generate the index sequence to scramble the pixel positions. Second, the hash value of the plaintext image is computed using the SHA-3 algorithm, which is used as the initial key of the 2D-LSCM chaotic system. Third, dynamic DNA encoding is performed on the image and the XOR operations are carried out with the generated random sequence to achieve pixel scrambling and further enhances the security of the encryption algorithm. Finally, preset DNA encoding rules are selected through DNA sequence operations to further enhance the confusion and diffusion characteristics of the algorithm. The experimental and security analysis results show that the algorithm not only has large key space and strong sensitivity to the key, but also can effectively resist statistical attacks and differential attacks.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Baldi, M., Bianchi, M., Chiaraluce, F., Rosenthal, J., Schipani, D.: Enhanced public key security for the McEliece cryptosystem. J. Cryptol. 29(1), 1–27 (2016)
Mahajan, P., Sachdeva, A.: A study of encryption algorithms AES, DES and RSA for security. Glob. J. Comput. Sci. Technol. 13(15), 15–22 (2013)
Zaki, A.K., Indiramma, M.: A novel redis security extension for NoSQL database using authentication and encryption. In: IEEE International Conference on Electrical, Computer and Communication Technologies, pp. 1–6. IEEE (2015)
Suryadi, M.T., Nurpeti, E., Widya, D.: Performance of chaos-based encryption algorithm for digital image. Telkomnika 12(3), 675–682 (2014)
Niu, Y., Zhang, X., Han, F.: Image encryption algorithm based on hyperchaotic maps and nucleotide sequences database. Comput. Intell. Neurosci. (2017). Article ID 4079793
Cui, G., Liu, Y., Zhang, X., Zhou, Z.: A new image encryption algorithm based on DNA dynamic encoding and hyper-chaotic system. In: He, C., Mo, H., Pan, L., Zhao, Y. (eds.) BIC-TA 2017. CCIS, vol. 791, pp. 286–303. Springer, Singapore (2017). https://doi.org/10.1007/978-981-10-7179-9_22
Zhang, Y.: The image encryption algorithm based on chaos and DNA computing. Multimed. Tools Appl. 77(16), 21589–21615 (2018)
Gehani, A., Labean, T., Reif, J.: DNA-based cryptography. Asp. Mol. Comput. 54(456), 233–249 (2004)
Zhang, X., Zhou, Z., Niu, Y.: An image encryption method based on the feistel network and dynamic DNA encoding. IEEE Photonics J. (2018). https://doi.org/10.1109/JPHOT.2018.2859257
Zhang, X., Han, F., Niu, Y.: Chaotic image encryption algorithm based on bit permutation and dynamic DNA encoding. Comput. Intell. Neurosci. (2017). Article ID 6919675
Zhang, X., Zhou, Z., Jiao, Y., Niu, Y., Wang, Y.: A visual cryptography scheme-based DNA microarrays. Int. J. Perform. Eng. 14(2), 334–340 (2018)
Guo, Y.: A summary of image encryption algorithm based on chaotic sequence. Open Autom. Control Syst. J. 6(1), 1110–1114 (2014)
Yang, C., Hua, M., Jia, S.: Image encryption algorithm based on chaotic mapping and Chinese remainder theorem. Metall. & Min. Ind. 7(4), 206–212 (2015)
Hua, Z., Jin, F., Xu, B., Huang, H.: 2D Logistic-Sine-Coupling map for image encryption. Signal Process. 149, 148–161 (2018)
Kumar, V., Raheja, E.G., Sareen, M.S.: New field of cryptography: DNA cryptography. Int. J. Comput. Technol. 37(6), 24–27 (2013)
Dodis, Y., An, J.H.: Concealment and its applications to authenticated encryption. In: Biham, E. (ed.) EUROCRYPT 2003. LNCS, vol. 2656, pp. 312–329. Springer, Heidelberg (2003). https://doi.org/10.1007/3-540-39200-9_19
Dan, B., Dunworth, C., Lipton, R.J.: Breaking DES using a molecular computer. In: Proceedings of a DIMACS Workshop, 4 April 1995, Princeton University, vol. 27 (1995)
Gehani, A., LaBean, T., Reif, J.: DNA-based cryptography. In: Jonoska, N., Păun, G., Rozenberg, G. (eds.) Aspects of Molecular Computing. LNCS, vol. 2950, pp. 167–188. Springer, Heidelberg (2003). https://doi.org/10.1007/978-3-540-24635-0_12
Zheng, H.Y., Wen-Jie, L.I., Xiao, D.: Novel image blocking encryption algorithm based on spatiotemporal chaos system. J. Comput. Appl. 31(11), 3053–3055 (2011)
Zhang, Q., Liu, L., Wei, X.: Improved algorithm for image encryption based on DNA encoding and multi-chaotic maps. AEUE-Int. J. Electron. Commun. 68(3), 186–192 (2014)
Liu, Y., Zhao, G., Wei, G., Zhang, J.: An improved DNA coding image encryption algorithm Combining entropy and chaos. In: International Symposium on Computers and Informatics, pp. 880–887. Atlantis Press (2015)
Shi, F., Zhang, H., Zhang, X.: Image encryption algorithm based on chaotic map and DNA coding. Comput. Eng. Appl. 54(5), 91–95 (2018)
Hua, Z., Zhou, Y., Pun, C.M., Chen, C.L.P.: 2D sine logistic modulation map for image encryption. Inf. Sci. Int. J. 297, 80–94 (2015)
Zenk, J., Tuntivate, C., Schulman, R.: Kinetics and thermodynamics of Watson-Crick base pairing driven DNA Origami dimerization. J. Am. Chem. Soc. 138(10), 3346–3354 (2016)
Al Shaikhli, I., Alahmad, M., Munthir, K.: Hash function of finalist SHA-3: analysis study. Int. J. Adv. Comput. Sci. Inf. Technol. 2(2), 1–12 (2014)
Acknowledgments
The work for this paper was supported by the National Natural Science Foundation of China (Grant nos. 61602424, 61472371, 61572446, and 61472372), Plan for Scientific Innovation Talent of Henan Province (Grant no. 174100510009), Program for Science and Technology Innovation Talents in Universities of Henan Province (Grant no. 15HASTIT019), and Key Scientific Research Projects of Henan High Educational Institution (18A510020).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2018 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Zhang, X., Zhou, Z., Niu, Y., Wang, Y., Wang, L. (2018). An Image Encryption Algorithm Based on Chaotic System Using DNA Sequence Operations. In: Qiao, J., et al. Bio-inspired Computing: Theories and Applications. BIC-TA 2018. Communications in Computer and Information Science, vol 952. Springer, Singapore. https://doi.org/10.1007/978-981-13-2829-9_20
Download citation
DOI: https://doi.org/10.1007/978-981-13-2829-9_20
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-13-2828-2
Online ISBN: 978-981-13-2829-9
eBook Packages: Computer ScienceComputer Science (R0)