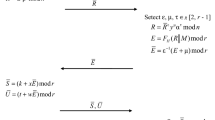
Abstract
Bilinear pairings have been used to design protocols such as identity-based encryption, one-round three-party key agreement, and aggregate signatures. Several authors have proposed many secret sharing schemes using elliptic curves and bilinear pairings. In 2004, Lee introduced bilinear self-pairing. Blind signature schemes have been the most significant obligation since the beginning of electronic money. In this article, we propose a blind signature scheme based on elliptic curves and a slightly modified Lee’s self-pairing. We provide an explicit example for the illustration purpose. We also show that the signature scheme avoids well-known attacks by M. Tian, Y. Zhu, and Z. Chen related to the blind signature scheme proposed by K. Chakraborty and J. Mehta. The security aspects of the proposed blind signature scheme have been discussed in this article.
The Author was supported in part by the Council of Scientific and Industrial Research, India, under award letter 09/414(1146)/2017-EMR-I.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Binu VP, Sreekumar A (2015) Threshold multi secret sharing using elliptic curve and pairing. Int J Inf Process 9(4):100–112
Blake I, Seroussi G, Smart N (1999) Elliptic curves in cryptography. Cambridge University Press
Chakraborty K, Mehta J (2012) A stamped blind signature scheme based on elliptic curve discrete logarithm problem. Int J Netw Sec 14(6):316–319
Chaum D (1983) Blind signatures for untraceable payments. In: Advances in cryptology - crypto ’82, vol 10. Springer, pp 199–203
Enge A (1999) Elliptic curves and their applications to cryptography: an introduction. Kluwer Academic Publishers
Goldwasser S, Micali S, Rivest R (1988) A digital signature scheme secure against adaptative chosen-message attacks. SIAM J Comput 17(2):281–308 April
Lee H-S (2004) A self-pairing map and its applications to cryptography. Appl Math Comput 151:671–678
Liu D, Huang D, Luo P, Dai Y (2008) New schemes for sharing points on an elliptic curve. Comput Math Appl 56:1556–1561
Menezes A (2005) An introduction to pairing-based cryptography, Lecture Notes. http://www.math.uwaterloo.ca/~ajmeneze/publications/pairings.pdf
Mohamed M (2011) A stamped hidden-signature scheme utilizing the elliptic curve discrete logarithm problem,. Int J Netw Secur 13(1):49–57
Nikolay Moldovyan A (2011) Blind signature protocols from digital signature standards,. Int J Netw Secur 13(1):22–30
Pointcheval D, Stern J (1996) Provably secure blind signature schemes. In: Asiacrypt ’96. LNCS 1163. Springer, Berlin, pp 252–265
Preneel B (1999) The state of cryptographic hash functions, Lecture notes in computer science, vol 1561, pp 158–182. (Lectures on Data Security)
Silverman JH (1986) The Arithmetic of elliptic curves. Graduate texts in mathematics. Springer, New York, p. 106
Tian M, Zhu Y, Chen Z (2014) Two simple attacks on a blind signature scheme. Int J Netw Secur 16(6):498–500
Zhao ZM (2008) ID-based weak blind signature from bilinear pairings. Int J Netw Secur 7(2):265–268
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Chintamani, M., Sa, L. (2022). A Blind Signature Scheme Based on Bilinear Pairings. In: Giri, D., Raymond Choo, KK., Ponnusamy, S., Meng, W., Akleylek, S., Prasad Maity, S. (eds) Proceedings of the Seventh International Conference on Mathematics and Computing . Advances in Intelligent Systems and Computing, vol 1412. Springer, Singapore. https://doi.org/10.1007/978-981-16-6890-6_1
Download citation
DOI: https://doi.org/10.1007/978-981-16-6890-6_1
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-16-6889-0
Online ISBN: 978-981-16-6890-6
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)