Abstract
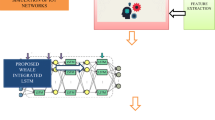
The impacts of Distributed-Denial-of-Service (DDoS) are doubtlessly major and continue to grow along with the growth of Internet-of-Things (IoT) devices. So many solutions have been contributed to detecting and mitigating this attack, specifically in IoT devices, yet the threat still exists and is bigger than ever. Denial of service attacks are often carried out by flooding a targeted computer or resource with phony requests in an attempt to overwhelm systems and prevent a few or all genuine requests from being completed; this is known as botnet attacks. There have been so many attempts to solve such puzzle-like middle-box and Artificial Intelligence (AI) solutions through machine learning (ML). The new botnets are so complex where for example, the Mirai botnet can mutate on a daily basis. This paper proposes a deep learning (DL) approach that consists of three DL algorithms, namely, recurrent neural network (RNN), convolutional neural network (CNN), and Long short-term memory (LSTM)-RNN to counter DDoS attacks targeting IoT networks. These algorithms are tested by implementing a real-world N-BaIoT dataset that has been collected by infecting nine IoT devices with two of the most dangerous DDoS botnets (Mirai and Bashlite). Subsequently, the three algorithms are compared in terms of accuracy, precision, recall, and f-measure. The results show that the RNN has achieved the highest accuracy of 89.75% among the three algorithms, followed by the LSTM-RNN and the CNN.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Abhishta, A., van Rijswijk-Deij, R., Nieuwenhuis, L.J.: Measuring the impact of a successful DDoS attack on the customer behaviour of managed DNS service providers. ACM SIGCOMM Comput. Commun. Rev. 48(5), 70–76 (2019)
Mirkovic, J., Reiher, P.: A taxonomy of DDoS attack and DDoS defense mechanisms. ACM SIGCOMM Comput. Commun. Rev. 34(2), 39–53 (2004)
Doshi, R., Apthorpe, N., Feamster, N.: Machine learning DDoS detection for consumer internet of things devices. In: 2018 IEEE Security and Privacy Workshops (SPW), pp. 29–35. IEEE (2018)
Meidan, Y., et al.: N-BaIoT—network-based detection of IoT botnet attacks using deep autoencoders. IEEE Pervasive Comput. 17(3), 12–22 (2018)
Khalaf, B.A., et al.: An adaptive protection of flooding attacks model for complex network environments. Secur. Commun. Netw. 2021, 1–17 (2021)
Maseer, Z.K., Yusof, R., Bahaman, N., Mostafa, S.A., Foozy, C.F.M.: Benchmarking of machine learning for anomaly based intrusion detection systems in the CICIDS2017 dataset. IEEE Access 9, 22351–22370 (2021)
Azizan, A.H., et al.: A machine learning approach for improving the performance of network intrusion detection systems. Ann. Emerging Technol. Comput. (AETiC) 5(5), (2021)
Zulhilmi, A., Mostafa, S.A., Khalaf, B.A., Mustapha, A., Tenah, S.S.: A comparison of three machine learning algorithms in the classification of network intrusion. In: Anbar, M., Abdullah, N., Manickam, S. (eds.) ACeS 2020. CCIS, vol. 1347, pp. 313–324. Springer, Singapore (2021). https://doi.org/10.1007/978-981-33-6835-4_21
Khalaf, B.A., Mostafa, S.A., Mustapha, A., Mohammed, M.A., Abduallah, W.M.: Comprehensive review of artificial intelligence and statistical approaches in distributed denial of service attack and defense methods. IEEE Access 7, 51691–51713 (2019)
Al-Othman, Z., Alkasassbeh, M., Baddar, S.A.-H.: A state-of-the-art review on IoT botnet attack detection. arXiv preprint arXiv:2010.13852 (2020)
Ahmed, M.E., Kim, H.: DDoS attack mitigation in internet of things using software defined networking. In: Proceedings of 3rd IEEE International Conference on Big Data Computing Service and Applications, BigDataService, pp. 271–276 (2017)
Metz, R.: Finding insecurity in the internet of things. Technol. Rev 119(2), 76–77 (2016)
Suo, H., Wan, J., Zou, C., Liu, J.: Security in the internet of things: a review. In: Proceedings of 2012 International Conference on Computer Science and Electronics Engineering, ICCSEE 2012, vol. 3, pp. 648–651 (2012)
Doshi, R., Apthorpe, N., Feamster, N.: Machine learning DDoS detection for consumer internet of things devices. In: Proceedings 2018 IEEE Symposium on Security and Privacy Workshops, SPW, pp. 29–35 (2018)
Kolias, C., Kambourakis, G., Stavrou, A., Voas, J.: DDoS in the IoT: Mirai and other botnets. Computer 50(7), 80–84 (2017)
Jia, Y., Zhong, F., Alrawais, A., Gong, B., Cheng, X.: Flowguard: an intelligent edge defense mechanism against IoT DDoS attacks. IEEE Internet Things J. 7(10), 9552–9562 (2020)
Soe, Y.N., Feng, Y., Santosa, P.I., Hartanto, R., Sakurai, K.: Machine learning-based IoT-botnet attack detection with sequential architecture. Sensors 20(16), 4372 (2020)
Parra, G.D.L.T., Rad, P., Choo, K.K.R., Beebe, N.: Detecting Internet of Things attacks using distributed deep learning. J. Netw. Comput. Appl. 163, 102662 (2020)
Ab Aziz, M.F., Mostafa, S.A., Foozy, C.F.M., Mohammed, M.A., Elhoseny, M., Abualkishik, A.: Integrating elman recurrent neural network with particle swarm optimization algorithms for an improved hybrid training of multidisciplinary datasets. Expert Syst. Appl. 183, 115441 (2021)
Kashinath, S.A., et al.: Review of data fusion methods for real-time and multi-sensor traffic flow analysis. IEEE Access 9, 51258–51276 (2021)
Wu, J.: Introduction to convolutional neural networks. Natl. Key Lab Novel Softw. Technol. 5(23), 495 (2017)
Maseer, Z.K., Yusof, R., Mostafa, S.A., Bahaman, N., Musa, O., Al-rimy, B.A.S.: DeepIoT.IDS: hybrid deep learning for enhancing IoT network intrusion detection. CMC-Comput. Mater. Continua 69(3), 3945–3966 (2021)
Acknowledgment
This paper is supported by the Center of Intelligent and Autonomous Systems (CIAS), Faculty of Computer Science and Information Technology, Universiti Tun Hussein Onn Malaysia (UTHM).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Hezam, A.A., Mostafa, S.A., Ramli, A.A., Mahdin, H., Khalaf, B.A. (2021). Deep Learning Approach for Detecting Botnet Attacks in IoT Environment of Multiple and Heterogeneous Sensors. In: Abdullah, N., Manickam, S., Anbar, M. (eds) Advances in Cyber Security. ACeS 2021. Communications in Computer and Information Science, vol 1487. Springer, Singapore. https://doi.org/10.1007/978-981-16-8059-5_19
Download citation
DOI: https://doi.org/10.1007/978-981-16-8059-5_19
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-16-8058-8
Online ISBN: 978-981-16-8059-5
eBook Packages: Computer ScienceComputer Science (R0)