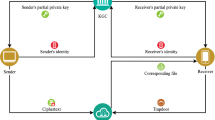
Abstract
To ensure the confidentiality of medical data, the medical information is usually encrypted before outsourcing to a third party for processing. Encryption technology can ensure the privacy of data, but it limits the search for data. The problem is usually solved using public key encryption with keyword search (PEKS). Recently, a few certificateless PEKS (CPEKS) schemes have been proposed. However, they rely on the high-consuming bilinear pairing, and some of them are vulnerable to inside keyword guessing attacks (IKGA). To solve these problems, we propose a lightweight CPEKS scheme for the Medical Internet of things (IoMT), which does not contain bilinear pairing. The scheme is proved to be secure in the random oracle model. The analysis results show that it has better comprehensive performance than the existing schemes according to the security property, the computation cost, and the communication cost.
This work is supported by the Fundamental Research Funds for the Central Universities of Southwest Minzu University (No: ZYN2022077), the Fund of Guangxi Key Laboratory of Cryptography and Information Security (No: GCIS202121), the Foreign Experts Program of Ministry of Science and Technology of China (No: DL2022186001L), and the Sichuan Science and Technology Program (No: 2021ZYD0021).
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Srinadh, V., Srinivasa Rao, M., Ranjan Sahoo, M., Rameshchandra, K.: An analytical study on security and future research of internet of things. Materials Today: Proceedings (2021). https://www.sciencedirect.com/science/article/pii/S2214785320400586
Zhang, T., Liu, M., Yuan, T., Al-Nabhan, N.: Emotion-aware and intelligent internet of medical things toward emotion recognition during covid-19 pandemic. IEEE Internet Things J. 8(21), 16 002–16 013 (2021)
Daoud, M.K., Otair, M.: The role of artificial intelligence and the internet of things in the development of medical radiology (an experimental study on magnetic resonance imaging). In: Proceeding 2020 International Conference on Intelligent Computing and Human-Computer Interaction (ICHCI), Sanya, China, 2020, pp. 17–20 (2020)
Liu, X., Yang, X., Luo, Y., Zhang, Q.: Verifiable multi-keyword search encryption scheme with anonymous key generation for medical internet of things. IEEE Internet Things J. (2021). https://ieeexplore.ieee.org/document/9344688
Ghubaish, A., Salman, T., Zolanvari, M., Unal, D., Al-Ali, A., Jain, R.: Recent advances in the internet-of-medical-things (IOMT) systems security. IEEE Internet Things J. 8(11), 8707–8718 (2021)
Song, D.X., Wagner, D., Perrig, A.: Practical techniques for searches on encrypted data. In: Proceeding: IEEE Symposium on Security and Privacy. Berkeley, CA, USA 2000, pp. 44–55 (2000)
Ryu, E.-K., Takagi, T.: Efficient conjunctive keyword-searchable encryption. In: Proceeding 21st International Conference on Advanced Information Networking and Applications Workshops, Niagara Falls, ON, Canada, 2007, pp. 409–414 (2007)
Zhang, Q.: An overview and analysis of hybrid encryption: The combination of symmetric encryption and asymmetric encryption. In: Proceeding 2021 2nd International Conference on Computing and Data Science (CDS), Stanford, CA, USA, 2021, pp. 616–622 (2021)
Boneh, D., Crescenzo, G. Di., Ostrovsky, R., Persiano, G.: Public key encryption with keyword search. In: Proceeding International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2004, pp. 506–522 (2004)
Chen, Y.C., Horng, G.: Timestamped conjunctive keyword-searchable public key encryption. In: Proceeding 2009 Fourth International Conference on Innovative Computing, Information and Control, Kaohsiung, Taiwan, 2009, pp. 729–732 (2009)
Ohtaki, Y.: Partial disclosure of searchable encrypted data with support for Boolean queries. In: Proceeding 2008 Third International Conference on Availability, Reliability and Security, Barcelona, Spain, 2008, pp. 1083–1090 (2008)
Miao, Y., Tong, Q., Deng, R., Choo, K.-K., R., Liu, X., Li, H.: Verifiable searchable encryption framework against insider keyword-guessing attack in cloud storage. IEEE Trans. Cloud Comput. (2020). https://ieeexplore.ieee.org/document/9075374
Lu, Y., Li, J.: Lightweight public key authenticated encryption with keyword search against adaptively-chosen-targets adversaries for mobile devices. IEEE Trans. Mob. Comput. (2021). https://ieeexplore.ieee.org/document/9423618
Baek, J., Safavi-Naini, R., Susilo, W.: Public key encryption with keyword search revisited. In: Proceeding International Conference on Computational Science and Its Applications (2008)
Yau, W.-C., Heng, S.-H., Goi, B.-M.: Off-line keyword guessing attacks on recent public key encryption with keyword search schemes. In: Proceeding International Conference on Autonomic and Trusted Computing, Oslo, Norway, 2008, pp. 100–105 (2008)
Byun, J.W., Rhee, H.S., Park, H.-A., Lee, D.H.: Off-line keyword guessing attacks on recent keyword search schemes over encrypted data. In: Proceeding Workshop on Secure Data Management, Seoul, Korea, pp. 75–83 (2006)
Hu, C.Y., Liu, P.T.: A secure searchable public key encryption scheme with a designated tester against keyword guessing attacks and its extension. In: Proceeding International Conference on Computer Science, Environment, Ecoinformatics, and Education, Wuhan, China, 2011, pp. 131–136 (2011)
Yau, W.-C., Phan, C.-W., Heng, S.-H., Goi, B.-M.: Keyword guessing attacks on secure searchable public key encryption schemes with a designated tester. Int. J. Comput. Math. 90, 2581–2587 (2013)
Chen, Y.-C.: Speks: secure server-designation public key encryption with keyword search against keyword guessing attacks. Comput. J. 58(4), 922–933 (2015)
Xu, P., Jin, H., Wu, Q., Wang, W.: Public-key encryption with fuzzy keyword search: a provably secure scheme under keyword guessing attack. IEEE Trans. Comput. 62(11), 2266–2277 (2013)
Ma, S., Huang, Q., Zhang, M., Yang, B.: Efficient public key encryption with equality test supporting flexible authorization. IEEE Trans. Inf. Forensics Secur. 10(3), 458–470 (2015)
Huang, Q., Li, H.: An efficient public-key searchable encryption scheme secure against inside keyword guessing attacks. Inf. Sci. 403–404, 1–14 (2017)
Chen, R., Mu, Y., Yang, G., Guo, F., Wang, X.: Dual-server public-key encryption with keyword search for secure cloud storage. IEEE Trans. Inf. Forensics Secur. 11(4), 789–798 (2016)
Lu, Y., Li, J., Zhang, Y.: Secure channel free certificate-based searchable encryption withstanding outside and inside keyword guessing attacks. IEEE Trans. Serv. Comput. 14(6), 2041–2054 (2021)
Liu, Z.-Y., Tseng, Y.-F., Tso, R., Chen, Y.-C., Mambo, M.: Identity-certifying authority-aided identity-based searchable encryption framework in cloud systems. IEEE Syst. J. 16, 1–12 (2021)
Al-Riyami S.-S., Paterson, K.-G.: Certificateless public key cryptography. In: Proceeding International Conference on the Theory and Application of Cryptology and Information Security, Taipei, China, 2003, pp. 452–473 (2003)
Peng, Y., Cui, J., Peng, C., Ying, Z.: Certificateless public key encryption with keyword search. China Commun. 11(11), 100–113 (2014)
Ma, M., He, D., Kumar, N., Choo, K.-K.R., Chen, J.: Certificateless searchable public key encryption scheme for industrial internet of things. IEEE Trans. Ind. Inform. 14(2), 759–767 (2018)
Zhang, Y., Liu, X., Lang, X., Zhang, Y., Wang, C.: Vclpkes: verifiable certificateless public key searchable encryption scheme for industrial internet of things. IEEE Access 8, 20 849–20 861 (2020)
He, D., Ma, M., Zeadally, S., Kumar, N., Liang, K.: Certificateless public key authenticated encryption with keyword search for industrial internet of things. IEEE Trans. Industr. Inf. 14(8), 3618–3627 (2018)
Lu, Y., Li, J., Zhang, Y.: Privacy-preserving and pairing-free multirecipient certificateless encryption with keyword search for cloud-assisted IIoT. IEEE Internet Things J. 7(4), 2553–2562 (2020)
Lu, Y., Li, J., Wang, F.: Pairing-free certificate-based searchable encryption supporting privacy-preserving keyword search function for IIoTs. IEEE Trans. Industr. Inf. 17(4), 2696–2706 (2021)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Liu, X., Sun, Y., Dong, H. (2022). A Lightweight Certificateless Searchable Public Key Encryption Scheme for Medical Internet of Things. In: Ahene, E., Li, F. (eds) Frontiers in Cyber Security. FCS 2022. Communications in Computer and Information Science, vol 1726. Springer, Singapore. https://doi.org/10.1007/978-981-19-8445-7_5
Download citation
DOI: https://doi.org/10.1007/978-981-19-8445-7_5
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-19-8444-0
Online ISBN: 978-981-19-8445-7
eBook Packages: Computer ScienceComputer Science (R0)