Abstract
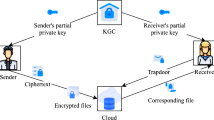
The inherent security threat of public key encryption with keyword search (PEKS) is the inside guessing attack since the ciphertext of keyword is generated publicly. Sever-aided schemes and keyword search with authenticated encryption schemes are proposed to resist inside keyword guessing attack in PEKS. Unfortunately, these solutions have limitations due to the security and privacy. To overcome these weakness, we propose an encrypted keyword search with fine-grained access control. The access policy of our scheme is semi-hidden in order to prevent the behavior of online keyword guessing attacks. At the same time, our scheme achieves offline keyword guessing attacks resistant by the private generation of ciphertext (without using the private key). Security proofs and experiment results show that our solution is feasible in terms of security and performance.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Song, D.X., Wagner, D., Perrig, A.: Practical techniques for searches on encrypted data. In: Proceeding 2000 IEEE Symposium on Security and Privacy. S&P 2000, pp. 44–55. IEEE (2000)
Boneh, D., Crescenzo, G.D., Ostrovsky, R., Persiano, G.: Public key encryption with keyword search. In: Cachin, C., Camenisch, J.L. (eds.) International Conference on the Theory and Applications of Cryptographic Techniques, pp. 506–522. Springer, Heidelberg (2004)
Sahai, Amit, Waters, Brent: Fuzzy identity-based encryption. In: Cramer, Ronald (ed.) EUROCRYPT 2005. LNCS, vol. 3494, pp. 457–473. Springer, Heidelberg (2005). https://doi.org/10.1007/11426639_27
Miao, Y., et al.: Privacy-preserving attribute-based keyword search in shared multi-owner setting. IEEE Trans. Dependable Secure Comput. 18(3), 1080–1094 (2021)
Miao, Y., Deng, R.H., Liu, X., Choo, K.-K.R., Wu, H., Li, H.: Multi-authority attribute-based keyword search over encrypted cloud data. IEEE Trans. Dependable Secure Comput. 18(4), 1667–1680 (2021)
Sun, J., Xiong, H., Nie, X., Zhang, Y., Wu, P.: On the security of privacy-preserving attribute-based keyword search in shared multi-owner setting. IEEE Trans. Dependable Secure Comput. 18(5), 2518–2519 (2021)
Niu, S., Song, M., Fang, L., Yu, F., Han, S., Wang, C.: Keyword search over encrypted cloud data based on blockchain in smart medical applications. Comput. Commun. 192, 33–47 (2022)
Liu, Z., Liu, Y., Fan, Y.: Searchable attribute-based signcryption scheme for electronic personal health record. IEEE Access 6, 76 381–76 394 (2018)
Li, H., Jing, T.: A lightweight fine-grained searchable encryption scheme in fog-based healthcare IoT networks. Wireless Commun. Mob. Comput. 2019, 15 (2019)
Zhang, K., Jiang, Z., Ning, J., Huang, X.: Subversion-resistant and consistent attribute-based keyword search for secure cloud storage. IEEE Trans. Inf. Forensics Secur. 17, 1771–1784 (2022)
Yu, J., Liu, S., Xu, M., Guo, H., Zhong, F., Cheng, W.: An efficient revocable and searchable MA-ABE scheme with blockchain assistance for C-IoT. IEEE Internet Things J. 10(3), 2754–2766 (2023)
Huang, Q., Yan, G., Wei, Q.: Attribute-based expressive and ranked keyword search over encrypted documents in cloud computing. IEEE Trans. Serv. Comput. 16(2), 957–968 (2023)
Chen, R., Mu, Y., Yang, G., Guo, F., Wang, X.: Dual-server public-key encryption with keyword search for secure cloud storage. IEEE Trans. Inf. Forensics Secur. 11(4), 789–798 (2015)
Huang, Q., Li, H.: An efficient public-key searchable encryption scheme secure against inside keyword guessing attacks. Inf. Sci. 403, 1–14 (2017)
Chaudhari, P., Das, M.L.: Privacy preserving searchable encryption with fine-grained access control. IEEE Trans. Cloud Comput. 9(2), 753–762 (2021)
Yang, Y., et al.: Dual traceable distributed attribute-based searchable encryption and ownership transfer. IEEE Trans. Cloud Comput. 11(1), 247–262 (2023)
Niu, S., Hu, Y., Su, Y., Yan, S., Zhou, S.: Attribute-based searchable encrypted scheme with edge computing for industrial Internet of Things. J. Syst. Architect. 139, 102889 (2023)
Chaudhari, P.: KeySea: keyword-based search with receiver anonymity in attribute-based searchable encryption. IEEE Trans. Serv. Comput. 15(2), 1036–1044 (2022)
Liu, X., Yang, X., Luo, Y., Zhang, Q.: Verifiable multikeyword search encryption scheme with anonymous key generation for medical internet of things. IEEE Internet of Things J. 9(22), 22 315–22 326 (2022)
Miao, Y., Deng, R.H., Choo, K.-K.R., Liu, X., Ning, J., Li, H.: Optimized verifiable fine-grained keyword search in dynamic multi-owner settings. IEEE Trans. Dependable Secure Comput. 18(4), 1804–1820 (2021)
Miao, Y., Ma, J., Liu, X., Li, X., Jiang, Q., Zhang, J.: Attribute-based keyword search over hierarchical data in cloud computing. IEEE Trans. Serv. Comput. 13(6), 985–998 (2020)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Feng, Y., Zeng, S., Xiao, J., Cheng, S., Zhang, F. (2024). Fine-Grained Searchable Encryption Scheme Against Keyword Brute-Force Attacks. In: Vaidya, J., Gabbouj, M., Li, J. (eds) Artificial Intelligence Security and Privacy. AIS&P 2023. Lecture Notes in Computer Science, vol 14509. Springer, Singapore. https://doi.org/10.1007/978-981-99-9785-5_1
Download citation
DOI: https://doi.org/10.1007/978-981-99-9785-5_1
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-99-9784-8
Online ISBN: 978-981-99-9785-5
eBook Packages: Computer ScienceComputer Science (R0)