Abstract
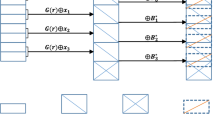
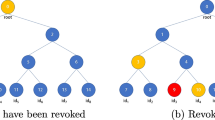
Attribute-based encryption (ABE) is a promising technology to provide fine-grained access control for the encrypted data and hence is widely used in the outsourced storage. However, it can not support the secure deduplication for its encryption feature. In order to handle this problem that users with different access policy to the ciphertext of the same plaintext should retrieve this ciphertext normally, we propose a novel ABE scheme supporting fine-grained authorized secure deduplication. Compared with the related works, we consider the dynamic policy update which adapts to the real-world environment more.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Bellare, M., Keelveedhi, S.: Interactive message-locked encryption and secure deduplication. Cryptology ePrint Archive (2015)
Bellare, M., Keelveedhi, S., Ristenpart, T.: Message-locked encryption and secure deduplication. In: Johansson, T., Nguyen, P.Q. (eds.) EUROCRYPT 2013. LNCS, vol. 7881, pp. 296–312. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-38348-9_18
Bethencourt, J., Sahai, A., Waters, B.: Ciphertext-policy attribute-based encryption. In: 2007 IEEE Symposium on Security and Privacy (SP 2007), pp. 321–334. IEEE (2007)
Boneh, D., Lynn, B., Shacham, H.: The stanford paired encryption library. http://crypto.stanford.edu/pbc/ (2007)
Cheng, S., Zeng, S., Zeng, H., Feng, Y., Xiao, J.: Secure single-server fuzzy deduplication without interactive proof-of-ownership in cloud. Cryptology ePrint Archive, Paper 2023/005 (2023). https://eprint.iacr.org/2023/005. https://eprint.iacr.org/2023/005
Cui, H., Deng, R.H., Li, Y., Wu, G.: Attribute-based storage supporting secure deduplication of encrypted data in cloud. IEEE Trans. Big Data 5(3), 330–342 (2017)
Fugkeaw, S., Sato, H.: Scalable and secure access control policy update for outsourced big data. Futur. Gener. Comput. Syst. 79, 364–373 (2018)
Goyal, V., Pandey, O., Sahai, A., Waters, B.: Attribute-based encryption for fine-grained access control of encrypted data. In: Proceedings of the 13th ACM Conference on Computer and Communications Security, pp. 89–98 (2006)
Joshi, M., Joshi, K., Finin, T.: Attribute based encryption for secure access to cloud based EHR systems. In: 2018 IEEE 11th International Conference on Cloud Computing (CLOUD), pp. 932–935. IEEE (2018)
Lai, J., Deng, R.H., Li, Y.: Expressive CP-ABE with partially hidden access structures. In: Proceedings of the 7th ACM Symposium on Information, Computer and Communications Security, pp. 18–19 (2012)
Lai, J., Deng, R.H., Yang, Y., Weng, J.: Adaptable ciphertext-policy attribute-based encryption. In: Cao, Z., Zhang, F. (eds.) Pairing 2013. LNCS, vol. 8365, pp. 199–214. Springer, Cham (2014). https://doi.org/10.1007/978-3-319-04873-4_12
Liu, J., Asokan, N., Pinkas, B.: Secure deduplication of encrypted data without additional independent servers. In: Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, pp. 874–885 (2015)
Liu, Z., Jiang, Z.L., Wang, X., Yiu, S.M.: Practical attribute-based encryption: outsourcing decryption, attribute revocation and policy updating. J. Netw. Comput. Appl. 108, 112–123 (2018)
Meyer, D.T., Bolosky, W.J.: A study of practical deduplication. ACM Trans. Storage (ToS) 7(4), 1–20 (2012)
Premkamal, P.K., Pasupuleti, S.K., Singh, A.K., Alphonse, P.: Enhanced attribute based access control with secure deduplication for big data storage in cloud. Peer-to-Peer Networking Appl. 14, 102–120 (2021)
Rouselakis, Y., Waters, B.: Efficient statically-secure large-universe multi-authority attribute-based encryption. In: Böhme, R., Okamoto, T. (eds.) FC 2015. LNCS, vol. 8975, pp. 315–332. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-47854-7_19
Sahai, A., Seyalioglu, H., Waters, B.: Dynamic credentials and ciphertext delegation for attribute-based encryption. In: Safavi-Naini, R., Canetti, R. (eds.) CRYPTO 2012. LNCS, vol. 7417, pp. 199–217. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-32009-5_13
Sahai, A., Waters, B.: Fuzzy identity-based encryption. In: Cramer, R. (ed.) EUROCRYPT 2005. LNCS, vol. 3494, pp. 457–473. Springer, Heidelberg (2005). https://doi.org/10.1007/11426639_27
Song, Y., Han, Z., Liu, F., Liu, L.: Attribute-based encryption with hidden policies in the access tree. J. Commun. 36(9), 119–126 (2015)
Yang, K., Jia, X., Ren, K.: Secure and verifiable policy update outsourcing for big data access control in the cloud. IEEE Trans. Parallel Distrib. Syst. 26(12), 3461–3470 (2014)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Xiao, J., Zeng, S., Feng, Y., Cheng, S. (2024). Fine-Grained Authorized Secure Deduplication with Dynamic Policy. In: Vaidya, J., Gabbouj, M., Li, J. (eds) Artificial Intelligence Security and Privacy. AIS&P 2023. Lecture Notes in Computer Science, vol 14509. Springer, Singapore. https://doi.org/10.1007/978-981-99-9785-5_2
Download citation
DOI: https://doi.org/10.1007/978-981-99-9785-5_2
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-99-9784-8
Online ISBN: 978-981-99-9785-5
eBook Packages: Computer ScienceComputer Science (R0)