Abstract
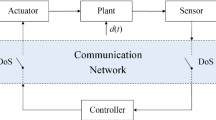
This paper mainly studies the secure control problem of cyber-physical systems with positive constraint and denial-of-service (DoS) attack. The energy of DoS attack considered in this paper is assumed to be limited. According to the different lengths of DoS attack duration, a switched positive system model composed of several positive subsystems is constructed. By virtue of the persistent dwell time and multiple copositive Lyapunov functions methods, the stabilization criterion is derived. Furthermore, the secure controller is designed and the corresponding algorithm is developed for solution. At last, a numerical example is provide to illustrate the potential of the proposed method.





Similar content being viewed by others
Availability of data and materials
The datasets used or analyzed during the current study are available from the corresponding author on reasonable request.
References
S. Amin, A. Cárdenas, S. Sastry, Safe and secure networked control systems under denial-of-service attacks, in Proceedings of the 12th International Conference on Hybrid Systems: Computation and Control (2009), pp. 31–45
L. An, G. Yang, Byzantine-resilient distributed state estimation: a min-switching approach. Automatica 129, 109664 (2021)
L. An, G. Yang, Distributed secure state estimation for cyber-physical systems under sensor attacks. Automatica 107, 526–538 (2019)
A. Cetinkaya, H. Ishii, T. Hayakawa, Analysis of stochastic switched systems with application to networked control under jamming attacks. IEEE Trans. Automat. Control 64(5), 2013–2028 (2019)
R. Cao, J. Wu, C. Long, et al., Stability analysis for networked control systems under denial-of-service attacks, in Proceedings of the 54th IEEE Conference on Decision and Control (2015), pp. 7476–7481
J. Farwell, R. Rohozinski, Stuxnet and the future of cyber war. Survival 53(1), 23–40 (2011)
H. Fawzi, P. Tabuada, S. Diggavi, Secure estimation and control for cyber-physical systems under adversarial attacks. IEEE Trans. Automat. control 59(6), 1454–1467 (2014)
S. Gill, I. Kockar, G. Ault, Dynamic optimal power flow for active distribution networks. IEEE Trans. Power Syst. 29(1), 121–131 (2013)
A. Gupta, C. Langbort, T. Basar, Optimal vontrol in the presence of an interlligent jammer with limited actions, in Proceedings of the 49th IEEE Conference on Decision and Control (2010), pp. 1096-1101
J. Hespanha, Uniform stability of switched linear systems: extensions of Lasalle’s invariance principle. IEEE Trans. Automat. Control 49(4), 470–482 (2004)
Y. Han, J. Lian, X. Huang, Event-triggered \(H_\infty \) control of networked switched systems subject to denial-of-service attacks. Nonlinear Anal. Hybrid Sys. 38, 100930 (2020)
S. Hu, D. Yue, X. Xie et al., Resilient event-triggered controller synthesis of networked control systems under periodic DoS jamming attacks. IEEE Trans. Cybern. 49(12), 1–11 (2019)
E. Iasiello, Cyber attack: a dull tool to shape foreign policy, in The 5th International Conference on Cyber Conflict (2013), pp. 1–18
L. Liu, X. Cao, Z. Fu et al., Finite-time control of uncertain fractional-order positive impulsive switched systems with mode-dependent average dwell time. Circuits Syst. Signal Process 37, 3739–3755 (2018)
S. Lai, B. Chen, T. Li, et al., Packet-based state feedback control under DoS attacks in cyber-physical systems. IEEE Trans. Circuits Syst. II: Exp. Br. 66(8), 1421–1425 (2019)
Y. Li, L. Shi, P. Cheng et al., Jamming attacks on remote state estimation in cyber-physical systems: a game-theoretic approach. IEEE Trans. Automat. Control 60(10), 2831–2836 (2015)
J. Liang, B. Wu, Y. Wang et al., Input-output finite-time stability of fractional-order positive switched systems. Circuits Syst. Signal Process 38, 1619–1638 (2019)
X. Li, D. Ye, Observer-based defense control for networked Takagi–Sugeno fuzzy systems against asynchronous DoS attacks. J. Frankl. Inst. (2021). https://doi.org/10.1016/j.jfranklin.2021.06.003
A. Lu, G. Yang, Input-to-state stabilizing control for cyber-physical systems with multiple transmission channels under denial of service. IEEE Trans. Automat. Control 63(6), 1813–1820 (2018)
J. Liu, Y. Yang, H. Li et al., Stabilisation for switched positive systems under extended asynchronous switching. IET Control Theory Appl. 13(16), 2702–2709 (2019)
J. Liu, Y. Yang, H. Li et al., Event-triggered output-feedback control for networked switched positive systems with asynchronous switching. Int. J. Control, Automat. Syst. 19(9), 3101–3110 (2021)
J. Liu, K. Yin, D. Yang, Stability analysis of switched positive systems with an impulse interval. Circuits Syst. Signal Process 40, 1005–1020 (2021)
L. Liu, J. Zhang, Y. Shao et al., Event-triggered control of positive switched systems based on linear programming. IET Control. Theory Appl. 14(1), 145–155 (2020)
L. Li, H. Zhang, Y. Xia et al., Security estimation under denial-of-service attack with energy constraint. Neurocomputing 292, 111–120 (2018)
I. Markovsky, Linear algebra with applications. Upper Saddle River NJ 13(2–3), 149–171 (2009)
R. Mitchell, R. Chen, Behavior rule specification-based intrusion detection for safety critical medical cyber physical systems. IEEE Trans. Depend. Secure. Comput. 12(1), 16–30 (2014)
X. Ma, J. Huang, L. Chen, Finite-time interval observers’ design for switched systems. Circuits Syst. Signal Process 38(11), 5304–5322 (2019)
A. Meng, H. Lam, Y. Yu et al., Static output feedback stabilization of positive polynomial fuzzy systems. IEEE Trans. Fuzzy Syst. 26(3), 1600–1612 (2018)
H. Sun, C. Peng, T. Yang et al., Resilient control of networked control systems with stochastic denial of service attacks. Neurocomputing 270, 170–177 (2017)
H. Sun, C. Peng, W. Zhang et al., Security-based resilient event-triggered control of networked control systems under denial of service attacks. J. Frankl. Inst. 356(17), 10277–10295 (2019)
Y. Sun, G. Yang, Event-triggered resilient control for cyber-physical systems under asynchronous DoS attacks. Inf. Sci. 465, 340–352 (2018)
S. Xiao, Y. Zhang, B. Zhang, \(l_1\)-Gain filter design of discrete-time positive neural networks with mixed delays. Neural Netw. 122(3), 152–162 (2018)
Y. Zhang, L. Wang, W. Sun et al., Distributed intrusion detection system in a multi-layer network architecture of smart grids. IEEE Trans. Smart Grid 2(4), 796–808 (2011)
Y. Zhu, W. Zheng, Observer-based control for cyber-physical systems with periodic DoS attacks via a cyclic switching strategy. IEEE Trans. Automat. Control 65(8), 3714–3721 (2019)
Acknowledgements
The work is supported by National Natural Science Foundation of China under Grants 62103129, Innovative Capability Improvement Program of Hebei Province under 1896160H.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Liu, J., Kang, L. Secure Control for Cyber-Physical Systems with Positive Constraint Under DoS Attack. Circuits Syst Signal Process 41, 2947–2962 (2022). https://doi.org/10.1007/s00034-021-01910-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00034-021-01910-7