Abstract
Quantum money allows a bank to mint quantum money states that can later be verified and cannot be forged. Usually, this requires a quantum communication infrastructure to perform transactions. Gavinsky (CCC 2012) introduced the notion of classically verifiable quantum money, which allows verification through classical communication. In this work, we introduce the notion of classical minting and combine it with classical verification to introduce semi-quantum money. Semi-quantum money is the first type of quantum money to allow transactions with completely classical communication and an entirely classical bank. This work features constructions for both a public memory-dependent semi-quantum money scheme and a private memoryless semi-quantum money scheme. The public construction is based on the works of Zhandry and Coladangelo, and the private construction is based on the notion of noisy trapdoor claw-free functions (NTCF) introduced by Brakerski et al. (FOCS 2018). In terms of technique, our main contribution is a perfect parallel repetition theorem for NTCF.

Similar content being viewed by others
Notes
In our public semi-quantum money construction, the classical verification can only be done with the bank; users still require quantum communication to transfer banknotes without the bank. We leave it as an open question whether public semi-quantum money with entirely classical communication can be made. A recent work of Amos et al. [7] exhibits completely classical communication between users, but in the oracle model.
Here \(\cdot \) denotes multiplication mod 2.
We deviate here slightly from the formal definitions; since the bank does not have a “database,” verification should only use the key. This is handled by using a message authentication code (MAC) and by returning to the user a tag for these values, and then verifying that tag during the verification. For the sake of clarity, we omit this part in the discussion—refer to Algorithm 4 to see how we work around this issue.
In Definition 8, the counterfeiter can ask the bank to run either \(\mathsf {cverify}\) and \(\mathsf {qverify}\) each time—i.e., he is not bound to choosing only one of them for the entire security game.
If there is non-negligible probability that a generated bolt would have the same serial number as one already in D, assuming D contains an amount of serial numbers polynomial in
 , we could construct a bolt forger \(\mathcal {L}\) that would generate
, we could construct a bolt forger \(\mathcal {L}\) that would generate  bolts and with non-negligible probability end up with two bolts with the same serial number that pass \(\mathsf {verify\text {-}bolt}\), winning the bolt forging security game (Definition 40).
bolts and with non-negligible probability end up with two bolts with the same serial number that pass \(\mathsf {verify\text {-}bolt}\), winning the bolt forging security game (Definition 40).We arbitrarily number the runs of \(\$_P.\mathsf {mint}\) according to the order they were initiated.
Suppose
 passes with non-negligible probability a verification of some \((\vert \psi \rangle , s, \sigma )\) on \(\mathsf {qverify}\) or a verification of \(s, \sigma , c\) on \(\mathsf {cverify}\) such that \(s \ne s_j \; \forall j \in [\ell ]\). In that case \(\mathsf {DS}.\mathsf {verify}_{pk_\sigma }(s, \sigma ) = 1\) with non-negligible probability (either on line 2 of \(\mathsf {qverify}\) or on line 4 of \(\mathsf {cverify}\)). We could use
passes with non-negligible probability a verification of some \((\vert \psi \rangle , s, \sigma )\) on \(\mathsf {qverify}\) or a verification of \(s, \sigma , c\) on \(\mathsf {cverify}\) such that \(s \ne s_j \; \forall j \in [\ell ]\). In that case \(\mathsf {DS}.\mathsf {verify}_{pk_\sigma }(s, \sigma ) = 1\) with non-negligible probability (either on line 2 of \(\mathsf {qverify}\) or on line 4 of \(\mathsf {cverify}\)). We could use  to construct a digital signature forger \(\mathcal {F}\) with non-negligible success probability: \(\mathcal {F}\) simulates a bank, but instead of signing with \(sk_\sigma \) and verifying with \(pk_\sigma \) that were generated in \(\mathsf {key\text {-}gen}\) he uses his signing oracle and the real pk. He then runs
to construct a digital signature forger \(\mathcal {F}\) with non-negligible success probability: \(\mathcal {F}\) simulates a bank, but instead of signing with \(sk_\sigma \) and verifying with \(pk_\sigma \) that were generated in \(\mathsf {key\text {-}gen}\) he uses his signing oracle and the real pk. He then runs  against the simulated bank and will be able to present \((s, \sigma )\) which pass \(\mathsf {DS}\) verification with non-negligible probability, while \(s \notin Q\) since \(s \ne s_j \; \forall j \in [\ell ]\).
against the simulated bank and will be able to present \((s, \sigma )\) which pass \(\mathsf {DS}\) verification with non-negligible probability, while \(s \notin Q\) since \(s \ne s_j \; \forall j \in [\ell ]\).In Ref. [15] this notion is defined for any PPT algorithm.
The weakly verifiable puzzle \(\hat{Z}\) constructed from a 1-of-2 puzzle is classical—each attempt to solve the puzzle creates a new quantum state, so even when running a solver for a puzzle multiple times there is indeed no rewinding.
Note that
 is indeed polynomial in
is indeed polynomial in  - since a weak 1-of-2 puzzle holds that \(1-h\) is noticeable (see Definition 12), by using the inequality \(\ln (1-\varepsilon ) \le -\varepsilon \) we get that \(\log (1/h)\) is noticeable.
- since a weak 1-of-2 puzzle holds that \(1-h\) is noticeable (see Definition 12), by using the inequality \(\ln (1-\varepsilon ) \le -\varepsilon \) we get that \(\log (1/h)\) is noticeable.Recall that a weak 1-of-2 puzzle has completeness \(\eta =1\) (see Definition 12).
Otherwise, we could construct a MAC forger \(\mathcal {F}\) with non-negligible success probability. Assume towards a contradiction that with non-negligible probability, \(\mathcal {C}\) passes verification by sending in line 4 \(\overline{o'}^n, t_o'\) such that \(\overline{o'}^n \ne \overline{o}^n\). That means that the MAC verification in line 5 passed. So \(\mathcal {F}\) could simulate a bank, but instead of signing and verifying with k generated in \(\$_\mathcal {Z}.\mathsf {key\text {-}gen}\), \(\mathcal {F}\) uses the signing and verification oracles. \(\mathcal {F}\) runs \(\mathcal {C}\) against the simulated bank, and present \(\overline{o'}^n, \tilde{o'}^n\). With non-negligible probability, MAC verification passes, and since \(\overline{o'}^n \ne \overline{o}^n\), and no other signings are requested (\(\mathsf {mint}\) was run only once), \(\mathcal {F}\) wins
 .
.\(\mathcal {C}\) can, of course, run both verification protocols simultaneously. We number the verifications according to the one that got to line 4 of the protocol first.
\(\mathcal {B}\) can, of course, run several verification protocols simultaneously. We number the verifications according to the order in which they were initiated.
Suppose
 passes with non-negligible probability a verification of \((c, t, \vert \$ \rangle )\) such that \(c \ne c_j \; \forall j \in [\ell ]\). In that case \(MAC.\mathsf {verify}(c, t)=1\) with non-negligible probability. We could use
passes with non-negligible probability a verification of \((c, t, \vert \$ \rangle )\) such that \(c \ne c_j \; \forall j \in [\ell ]\). In that case \(MAC.\mathsf {verify}(c, t)=1\) with non-negligible probability. We could use  to construct a forger \(\mathcal {F}\) with non-negligible success probability: \(\mathcal {F}\) simulates a bank, but instead of signing and verifying with the MAC key generated in \(\hat{\$}.\mathsf {key\text {-}gen}\), he uses the signing and verification oracles. He then runs
to construct a forger \(\mathcal {F}\) with non-negligible success probability: \(\mathcal {F}\) simulates a bank, but instead of signing and verifying with the MAC key generated in \(\hat{\$}.\mathsf {key\text {-}gen}\), he uses the signing and verification oracles. He then runs  against the simulated bank, and will be able to present c, t which pass MAC verification with non-negligible probability, while he did not ask for a tag of c before since \(c \ne c_j \; \forall j \in [\ell ]\).
against the simulated bank, and will be able to present c, t which pass MAC verification with non-negligible probability, while he did not ask for a tag of c before since \(c \ne c_j \; \forall j \in [\ell ]\). can, of course, run several mint protocols simultaneously. We number them according to the order they were initiated.
can, of course, run several mint protocols simultaneously. We number them according to the order they were initiated.Indistinguishability works for messages of the same length. Here, we assume, without loss of generality, that
 always outputs keys of the same length.
always outputs keys of the same length.Assume
 is non-negligible. Assume without loss of generality that \(\Pr [S_2] \le \Pr [S_1]\). In that case, we could construct a distinguisher \(\mathcal {D}\) with non-negligible success probability: \(\mathcal {D}\) will simulate a bank, but instead of encrypting with the ENC key generated in \(\hat{\$}.\mathsf {key\text {-}gen}\), he will use the encryption oracle, and instead of decrypting he will “remember” each encryption he made and thus could match each encryption to the relevant key (any unrecognized encryption would not have passed the real bank verification either, because the encryptions are MAC signed). On the ith mint, he will present a random key and the actual mini-scheme key used in that mint as \(m_0\) and \(m_1\) (the chosen messages whose encryptions he needs to recognize in the CPA game), respectively, and proceed with the encryption he received to finish the game. \(\mathcal {D}\) returns \(b'=1\) (guessing the encryption he received was of the real key) if and only if he wins the counterfeiting game (since he wins with higher probability when he receives encryption of the real key). \(\mathcal {D}\) has a
is non-negligible. Assume without loss of generality that \(\Pr [S_2] \le \Pr [S_1]\). In that case, we could construct a distinguisher \(\mathcal {D}\) with non-negligible success probability: \(\mathcal {D}\) will simulate a bank, but instead of encrypting with the ENC key generated in \(\hat{\$}.\mathsf {key\text {-}gen}\), he will use the encryption oracle, and instead of decrypting he will “remember” each encryption he made and thus could match each encryption to the relevant key (any unrecognized encryption would not have passed the real bank verification either, because the encryptions are MAC signed). On the ith mint, he will present a random key and the actual mini-scheme key used in that mint as \(m_0\) and \(m_1\) (the chosen messages whose encryptions he needs to recognize in the CPA game), respectively, and proceed with the encryption he received to finish the game. \(\mathcal {D}\) returns \(b'=1\) (guessing the encryption he received was of the real key) if and only if he wins the counterfeiting game (since he wins with higher probability when he receives encryption of the real key). \(\mathcal {D}\) has a  probability to win, which is non-negligible, in contradiction to the security of ENC.
probability to win, which is non-negligible, in contradiction to the security of ENC.This discussion is not relevant to the public setting.
Also known as certified randomness.
Here, we use a slightly weaker (and simpler) definition compared to Brakerski et al. Our definition follows from theirs by using Lemma 2 in [13], which relates the Hellinger distance to the trace distance.
Note that although both \(x_0\) and \(x_1\) are referred to to define the set \(H_k\), only one of them, \(x_b\), is explicitly specified in any 4-tuple that lies in \(H_k\).
This can be verified since \(A'\) generated those puzzles along with their verification information and therefore can verify them efficiently. Moreover, A solves \(n-1\) puzzles with non-negligible probability, meaning that \(A'\) can get correct solutions in polynomial time with high probability.
References
S. Aaronson, Quantum copy-protection and quantum money, in Proceedings of the 24th Annual IEEE Conference on Computational Complexity, CCC 2009, Paris, France, 15–18 July 2009 (IEEE Computer Society, 2009), pp. 229–242. arXiv:1110.5353. https://doi.org/10.1109/CCC.2009.42
S. Aaronson, Shadow tomography of quantum states, in I. Diakonikolas, D. Kempe, M. Henzinger, editors, Proceedings of the 50th Annual ACM SIGACT Symposium on Theory of Computing, STOC 2018, Los Angeles, CA, USA, June 25–29, 2018 (ACM, 2018), pp. 325–338. arXiv:1711.01053. https://doi.org/10.1145/3188745.3188802
S. Aaronson, P. Christiano, Quantum money from hidden subspaces. Theory of Comput. 9, 349–401 (2013). arXiv:1203.4740. https://doi.org/10.4086/toc.2013.v009a009
G. Alagic, A.M. Childs, A.B. Grilo, S.-H. Hung, Non-interactive classical verification of quantum computation (2019). arXiv:1911.08101
G. Alagic, C. Majenz, A. Russell, Efficient simulation of random states and random unitaries, in A. Canteaut, Y. Ishai, editors, Advances in Cryptology - EUROCRYPT 2020 - 39th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, May 10–14, 2020, Proceedings, Part III, volume 12107 of Lecture Notes in Computer Science (Springer, 2020), pp. 759–787. https://doi.org/10.1007/978-3-030-45727-3_26. arXiv:1910.05729
R. Amiri, J.M. Arrazola, Quantum money with nearly optimal error tolerance. Phys. Rev. A, 95(6) (2017). https://doi.org/10.1103/physreva.95.062334
R. Amos, M. Georgiou, A. Kiayias, M. Zhandry, One-shot signatures and applications to hybrid quantum/classical authentication, in K. Makarychev, Y. Makarychev, M. Tulsiani, G. Kamath, J. Chuzhoy, editors, Proccedings of the 52nd Annual ACM SIGACT Symposium on Theory of Computing, STOC 2020, Chicago, IL, USA, June 22–26, 2020 (ACM, 2020), pp. 255–268. https://doi.org/10.1145/3357713.3384304
C. Badertscher, A. Cojocaru, L. Colisson, E. Kashefi, D. Leichtle, A. Mantri, P. Wallden, Security limitations of classical-client delegated quantum computing (2020). arXiv:2007.01668
A. Banerjee, C. Peikert, A. Rosen, Pseudorandom functions and lattices, in D. Pointcheval and T. Johansson, editors, Advances in Cryptology - EUROCRYPT 2012 - 31st Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, April 15–19, 2012. Proceedings, volume 7237 of Lecture Notes in Computer Science (Springer, 2012), pp. 719–737. https://doi.org/10.1007/978-3-642-29011-4_42
M. Bellare, R. Impagliazzo, M. Naor, Does parallel repetition lower the error in computationally sound protocols? In 38th Annual Symposium on Foundations of Computer Science, FOCS ’97, Miami Beach, Florida, USA, October 19–22, 1997 (IEEE Computer Society, 1997), pp. 374–383. https://doi.org/10.1109/SFCS.1997.646126
S. Ben-David, O. Sattath, Quantum tokens for digital signatures (2016). arXiv:1609.09047
D. Boneh, M. Zhandry, Quantum-secure message authentication codes, in T. Johansson, P.Q. Nguyen, editors, Advances in Cryptology - EUROCRYPT 2013, 32nd Annual International Conference on the Theory and Applications of Cryptographic Techniques, Athens, Greece, May 26–30, 2013. Proceedings, volume 7881 of Lecture Notes in Computer Science (Springer, 2013), pp. 592–608. https://doi.org/10.1007/978-3-642-38348-9_35
Z. Brakerski, P. Christiano, U. Mahadev, U.V. Vazirani, T. Vidick. A cryptographic test of quantumness and certifiable randomness from a single quantum device, in M. Thorup, editor, 59th IEEE Annual Symposium on Foundations of Computer Science, FOCS 2018, Paris, France, October 7–9, 2018 (IEEE Computer Society, 2018), pp. 320–331. arXiv:1804.00640. https://doi.org/10.1109/FOCS.2018.00038
A. Broadbent, C. Schaffner, Quantum cryptography beyond quantum key distribution. Des. Codes Cryptogr. 78(1), 351–382 (2016). https://doi.org/10.1007/s10623-015-0157-4. arXiv:1510.06120
R. Canetti, S. Halevi, M. Steiner, Hardness amplification of weakly verifiable puzzles, in J. Kilian, editor, Theory of Cryptography, Second Theory of Cryptography Conference, TCC 2005, Cambridge, MA, USA, February 10–12, 2005, Proceedings, volume 3378 of Lecture Notes in Computer Science (Springer, 2005), pp. 17–33. https://doi.org/10.1007/978-3-540-30576-7_2
A. Cojocaru, L. Colisson, E. Kashefi, P. Wallden, Qfactory: Classically-instructed remote secret qubits preparation, in S.D. Galbraith and S. Moriai, editors, Advances in Cryptology - ASIACRYPT 2019 - 25th International Conference on the Theory and Application of Cryptology and Information Security, Kobe, Japan, December 8–12, 2019, Proceedings, Part I, volume 11921 of Lecture Notes in Computer Science (Springer, 2019), pp. 615–645. arXiv:1904.06303. https://doi.org/10.1007/978-3-030-34578-5_22
A. Coladangelo, Smart contracts meet quantum cryptography (2019). arXiv:1902.05214
A. Coladangelo, O. Sattath, A quantum money solution to the blockchain scalability problem. Quantum 4, 297 (2020). https://doi.org/10.22331/q-2020-07-16-297
D. Dieks, Communication by EPR devices. Phys. Lett. A 92(6), 271–272 (1982). https://doi.org/10.1016/0375-9601(82)90084-6
V. Dunjko, E. Kashefi, Blind quantum computing with two almost identical states (2016). arXiv:1604.01586
E. Farhi, D. Gosset, A. Hassidim, A. Lutomirski, P.W. Shor, Quantum money from knots, in S. Goldwasser, editor, Innovations in Theoretical Computer Science 2012, Cambridge, MA, USA, January 8–10, 2012 (ACM, 2012), pp. 276–289. arXiv:1004.5127. https://doi.org/10.1145/2090236.2090260
R.A. Friedman, R. Renner, T. Vidick, Simple and tight device-independent security proofs. SIAM J. Comput. 48(1), 181–225 (2019). arXiv:1607.01797. https://doi.org/10.1137/18M1174726
T. Gagliardoni, A. Hülsing, C. Schaffner, Semantic security and indistinguishability in the quantum world, in M. Robshaw and J. Katz, editors, Advances in Cryptology - CRYPTO 2016 - 36th Annual International Cryptology Conference, Santa Barbara, CA, USA, August 14–18, 2016, Proceedings, Part III, volume 9816 of Lecture Notes in Computer Science (Springer, 2016), pp. 60–89. arXiv:1504.05255. https://doi.org/10.1007/978-3-662-53015-3_3
D. Gavinsky, Quantum money with classical verification, in Proceedings of the 27th Conference on Computational Complexity, CCC 2012, Porto, Portugal, June 26–29, 2012 (IEEE Computer Society, 2012), pp. 42–52. arXiv:1109.0372. https://doi.org/10.1109/CCC.2012.10
M. Georgiou, I. Kerenidis, New constructions for quantum money, in 10th Conference on the Theory of Quantum Computation, Communication and Cryptography, TQC 2015, May 20–22, 2015, Brussels, Belgium (Schloss Dagstuhl - Leibniz-Zentrum fuer Informatik, 2015), pp. 92–110. https://doi.org/10.4230/LIPIcs.TQC.2015.92
A. Gheorghiu, T. Vidick, Computationally-secure and composable remote state preparation (2019). arXiv:1904.06320
O. Goldreich, The Foundations of Cryptography - Volume 1, Basic Techniques (Cambridge University Press, 2001). https://doi.org/10.1017/CBO9780511546891
O. Goldreich, The Foundations of Cryptography - Vol. 2, Basic Applications (Cambridge University Press, 2004)
K. Horodecki, M. Stankiewicz, Semi-device-independent quantum money. New J. Phys. 22(2), 023007 (2020). arXiv:1811.10552. https://doi.org/10.1088/1367-2630/ab6872
Z. Ji, Y. Liu, F. Song, Pseudorandom quantum states, in H. Shacham and A. Boldyreva, editors, Advances in Cryptology - CRYPTO 2018 - 38th Annual International Cryptology Conference, Santa Barbara, CA, USA, August 19–23, 2018, Proceedings, Part III, volume 10993 of Lecture Notes in Computer Science (Springer, 2018), pp. 126–152. arXiv:1711.00385. https://doi.org/10.1007/978-3-319-96878-0_5
J. Katz, Y. Lindell, Introduction to Modern Cryptography, Second Edition (CRC Press, 2014)
A. Lutomirski, An online attack against Wiesner’s quantum money (2010). arXiv:1010.0256
A. Lutomirski, Component mixers and a hardness result for counterfeiting quantum money (2011). arXiv:1107.0321
A. Lutomirski, S. Aaronson, E. Farhi, D. Gosset, J.A. Kelner, A. Hassidim, P.W. Shor, Breaking and making quantum money: Toward a new quantum cryptographic protocol, in A.C. Yao, editor, Innovations in Computer Science - ICS 2010, Tsinghua University, Beijing, China, January 5–7, 2010. Proceedings (Tsinghua University Press, 2010), pp. 20–31. http://conference.iiis.tsinghua.edu.cn/ICS2010/content/papers/2.html. arXiv:0912.3825
U. Mahadev, Classical homomorphic encryption for quantum circuits, in M. Thorup, editor, 59th IEEE Annual Symposium on Foundations of Computer Science, FOCS 2018, Paris, France, October 7–9, 2018 (IEEE Computer Society, 2018), pp. 332–338. arXiv:1708.02130. https://doi.org/10.1109/FOCS.2018.00039
U. Mahadev, Classical verification of quantum computations, in M. Thorup, editor, 59th IEEE Annual Symposium on Foundations of Computer Science, FOCS 2018, Paris, France, October 7–9, 2018 (IEEE Computer Society, 2018), pp. 259–267. arXiv:1804.01082. https://doi.org/10.1109/FOCS.2018.00033
A. Molina, T. Vidick, J. Watrous, Optimal counterfeiting attacks and generalizations for Wiesner’s quantum money, in Theory of Quantum Computation, Communication, and Cryptography (Springer, 2013), pp. 45–64. arXiv:1202.4010
M. Mosca, D. Stebila, Quantum Coins, volume 523 of Contemp. Math. (Amer. Math. Soc., 2010), pp. 35–47. arXiv:0911.1295. https://doi.org/10.1090/conm/523/10311
D. Nagaj, O. Sattath, A. Brodutch, D. Unruh, An adaptive attack on Wiesner’s quantum money. Quantum Inf. Comput., 16(11&12), 1048–1070 (2016). http://www.rintonpress.com/xxqic16/qic-16-1112/1048-1070.pdf, arXiv:1404.1507
M.A. Nielsen, I.L. Chuang, Quantum Computation and Quantum Information: 10th Anniversary Edition, 10th edition (Cambridge University Press, New York, 2011)
J.L. Park, The concept of transition in quantum mechanics. Found. Phys. 1(1), 23–33 (1970). https://doi.org/10.1007/BF00708652
F. Pastawski, N.Y. Yao, L. Jiang, M.D. Lukin, J.I. Cirac, Unforgeable noise-tolerant quantum tokens. Proc. Natl. Acad. Sci. 109(40), 16079–16082 (2012). arXiv:1112.5456. https://doi.org/10.1073/pnas.1203552109
M.C. Pena, R.D. Díaz, J.Faugère, L.H. Encinas, L. Perret, Non-quantum cryptanalysis of the noisy version of Aaronson-Christiano’s quantum money scheme. IET Inf. Secur. 13(4):362–366 (2019). https://doi.org/10.1049/iet-ifs.2018.5307
R. Raz, A parallel repetition theorem. SIAM J. Comput. 27(3), 763–803 (1998). https://doi.org/10.1137/S0097539795280895
R. Raz, A counterexample to strong parallel repetition. SIAM J. Comput. 40(3), 771–777 (2011). https://doi.org/10.1137/090747270
B. Roberts, Toward Secure Quantum Money. PhD thesis, Princeton University (2019). http://people.eecs.berkeley.edu/~bhaskarr/documents/Thesis_RZ19.pdf
V. Shoup, Sequences of games: a tool for taming complexity in security proofs. Cryptology ePrint Archive, Report 2004/332 (2004). https://eprint.iacr.org/2004/332
Y. Tokunaga, T. Okamoto, N. Imoto, Anonymous quantum cash (2003). http://qci.is.s.u-tokyo.ac.jp/qci/eqis03/program/papers/O09-Tokunaga.ps.gz
U.V. Vazirani, T. Vidick, Fully device independent quantum key distribution. Commun. ACM 62(4), 133 (2019). arXiv:1210.1810. https://doi.org/10.1145/3310974
S. Wiesner, Conjugate coding. ACM Sigact News 15(1), 78–88 (1983). https://doi.org/10.1145/1008908.1008920
W.K. Wootters, W.H. Zurek, A single quantum cannot be cloned. Nature 299(5886), 802–803 (1982). https://doi.org/10.1038/299802a0
M. Zhandry, How to construct quantum random functions, in 53rd Annual IEEE Symposium on Foundations of Computer Science, FOCS 2012, New Brunswick, NJ, USA, October 20–23, 2012 (IEEE Computer Society, 2012), pp. 679–687. https://doi.org/10.1109/FOCS.2012.37
M. Zhandry, Quantum lightning never strikes the same state twice, in Y. Ishai, V. Rijmen, editors, Advances in Cryptology - EUROCRYPT 2019 - Germany, May 19–23, 2019, Proceedings, Part III, volume 11478 of Lecture Notes in Computer Science (Springer, 2019), pp. 408–438. arXiv:1711.02276. https://doi.org/10.1007/978-3-030-17659-4_14
Acknowledgements
We wish to thank Zvika Brakerski, Urmila Mahadev, and Thomas Vidick for fruitful discussions. We also wish to thank an anonymous referee for insightful comments. O.S. and R.R. are supported by the Israel Science Foundation (ISF) grant Nos. 682/18 and 2137/19, and by the Cyber Security Research Center at Ben-Gurion University.
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by Serge Fehr.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
A Nomenclature
-
 :
: -
Counterfeiter of a full blown private quantum money scheme (also NTCF adversary in Sect. 4)
- \(B\) :
-
A bank
- \(\mathcal {B}\) :
-
Counterfeiter of a private quantum money mini-scheme
- \(\mathcal {C}\) :
-
Counterfeiter of a private quantum money 2-of-2 mini-scheme (also quantum lightning certificate forger)
- \(\mathcal {D}\) :
-
An encryption distinguisher—i.e., an adversary whose goal is to distinguish between an actual encryption and a random string
- \(\$_C\) :
-
A quantum money scheme with classical minting
- \(\$_P\) :
-
Our public semi-quantum money scheme based on quantum lightning with bolt-to-certificate
- \(\$_\mathcal {Z}\) :
-
Our private semi-quantum money construction based on 1-of-2 puzzles
- \(\mathsf {DS}\) :
-
A digital signature scheme
- ENC:
-
A symmetric encryption scheme
- \(\mathcal {F}\) :
-
A MAC or digital signature forger—i.e., an adversary whose goal is to break the security of a MAC or digital signature scheme
- \(\in _R\) :
-
For a finite set S we denote \(s \in _R S\) to be the process in which s is sampled uniformly from S
- \(\mathcal {L}\) :
-
A quantum lightning adversary, i.e., an adversary whose goal is to pass verification for two bolts with the same serial number
- LWE:
-
Learning with errors
- MAC:
-
Message authentication code
- [n]:
-
We denote \([n] \equiv \{1, \ldots , n\}\)
- NTCF:
-
Noisy Trapdoor Claw-free Function
- \(P\) :
-
A payer in a transaction
- PQ-EU-CMA:
-
Post-quantum existentially unforgeable under an adaptive chosen-message attack
- PQ-IND-CPA:
-
Post-quantum indistinguishable encryptions under a chosen-plaintext attack
- \(\mathsf {QL}\) :
-
A quantum lightning scheme
- \(R\) :
-
A receiver in a transaction
- \(\mathcal {T}\) :
-
A QPT 2-of-2 solver—an adversary that attempts to solve both challenges of a 1-of-2 puzzle
- \(V_2\) :
-
An algorithm that verifies solutions for both challenges of a puzzle
- \( \mathcal Z\) :
-
A 1-of-2 puzzle
- \(\hat{\mathcal Z}\) :
-
A weakly verifiable puzzle
B Preliminaries
This appendix contains mainly the standard definitions of private-key encryption and message authentication codes (MAC) and can be safely skipped by readers already familiar with these notions.
We use the standard definitions for negligible, non-negligible and noticeable functions—see, e.g., [27].
Definition 32
(Private-key encryption system, [31, Definition 3.7]) A private-key encryption scheme consists of three PPT algorithms \(\mathsf {key\text {-}gen}\), \(\mathsf {encrypt}\) and \(\mathsf {decrypt}\) such that:
-
1.
The randomized key-generation algorithm \(\mathsf {key\text {-}gen}\) takes as input
 and outputs a key
and outputs a key  .
. -
2.
The (possibly randomized) encryption algorithm
 takes as input a key k and a plaintext message \(m \in \{0, 1\}^*\), and outputs a ciphertext \(c \leftarrow \mathsf {encrypt}_k(m)\).
takes as input a key k and a plaintext message \(m \in \{0, 1\}^*\), and outputs a ciphertext \(c \leftarrow \mathsf {encrypt}_k(m)\). -
3.
The deterministic decryption algorithm \(\mathsf {decrypt}\) takes as input a key k and a ciphertext c, and outputs a message \(m {:}{=}Dec_k(c)\).
A private-key encryption system is required to have perfect completeness, meaning that for every  , every k output by
, every k output by  , and every \(m \in \{0, 1\}^*\), it holds that
, and every \(m \in \{0, 1\}^*\), it holds that  .
.
Definition 33
(PQ-IND-CPA, adapted from [31, Definition 3.22]) A private-key encryption scheme \(\Pi \) has post-quantum indistinguishable encryptions under a chosen-plaintext attack (PQ-IND-CPA) if for every QPT distinguisher \(\mathcal {D}\) there is a negligible function  such that, for all
such that, for all  :
:

The indistinguishability game  :
:
-
1.
A key k is generated by running
 .
. -
2.
The distinguisher \(\mathcal {D}\) is given input
 and classical oracle access to \(\mathsf {encrypt}_k(\cdot )\), and outputs a pair of messages \(m_0, m_1\) of the same length.
and classical oracle access to \(\mathsf {encrypt}_k(\cdot )\), and outputs a pair of messages \(m_0, m_1\) of the same length. -
3.
A uniform bit \(b \in _R \{0, 1\}\) is chosen, and then a ciphertext \(c \leftarrow \mathsf {encrypt}_k(m_b)\) is computed and given to \(\mathcal {D}\).
-
4.
\(\mathcal {D}\) continues to have oracle access to \(\mathsf {encrypt}_k(\cdot )\) and outputs a bit \(b'\).
-
5.
The output of the game is defined to be 1 if \(b'=b\), and 0 otherwise. In the former case, we say that \(\mathcal {D}\) succeeds.
Definition 34
(Message authentication code [31, Definition 4.1]) A message authentication code (MAC) consists of 3 PPT algorithms  , and \(\mathsf {verify}\) satisfying:
, and \(\mathsf {verify}\) satisfying:
-
1.
\(\mathsf {key\text {-}gen}\) takes as input the security parameter
 and outputs a key k
and outputs a key k -
2.
 takes as input a key k and a message \(m \in \{0,1\}^*\) and outputs a tag
takes as input a key k and a message \(m \in \{0,1\}^*\) and outputs a tag  .
. -
3.
\(\mathsf {verify}\) takes as input a key k, a message m, and a tag t. It outputs a bit \(b {:}{=}\mathsf {verify}_k(m,t)\), with \(b=1\) meaning valid and \(b=0\) meaning invalid.
A MAC is required to have perfect completeness, i.e., for every  , every key
, every key  and every \(m \in \{0,1\}^*\), it holds that
and every \(m \in \{0,1\}^*\), it holds that  .
.
Definition 35
(PQ-EU-CMA MAC, adapted from [31, Definition 4.2]) A message authentication code \(\Pi \) is Post-Quantum Existentially Unforgeable under an adaptive Chosen-Message Attack (PQ-EU-CMA) if for every QPT forger \(\mathcal {F}\), there exists a negligible function  such that:
such that:

The CMA message authentication game  :
:
-
1.
A key k is generated by running
 .
. -
2.
The forger \(\mathcal {F}\) is given input
 , classical oracle access to
, classical oracle access to  and classical oracle access to \(\mathsf {verify}_k(\cdot )\). (Note that the forger cannot query the oracles in superposition.) The forger eventually outputs (m, t). Let \(\mathcal {Q}\) denote the set of all queries that \(\mathcal {F}\) asked its signing oracle.
and classical oracle access to \(\mathsf {verify}_k(\cdot )\). (Note that the forger cannot query the oracles in superposition.) The forger eventually outputs (m, t). Let \(\mathcal {Q}\) denote the set of all queries that \(\mathcal {F}\) asked its signing oracle. -
3.
\(\mathcal {F}\) succeeds if and only if (1) \(\mathsf {verify}_k(m,t) = 1\) and (2) \(m \notin \mathcal {Q}\). In that case, the output of the game is defined to be 1.
Definition 36
(Digital signature scheme [31, Definition 12.1]) A digital signature scheme consists of three PPT algorithms \(\mathsf {key\text {-}gen}\), \(\mathsf {sign}\) and \(\mathsf {verify}\) such that:
-
1.
The key-generation algorithm \(\mathsf {key\text {-}gen}\) takes as input a security parameter
 and outputs a pair of keys (pk, sk). These are called the public key and the private key, respectively. We assume that pk and sk each has length of at least
and outputs a pair of keys (pk, sk). These are called the public key and the private key, respectively. We assume that pk and sk each has length of at least  and that
and that  can be determined from either.
can be determined from either. -
2.
The signing algorithm \(\mathsf {sign}\) takes as input a private key sk and a message m. It outputs a signature \(\sigma \leftarrow \mathsf {sign}_{sk}(m)\).
-
3.
The deterministic verification algorithm \(\mathsf {verify}\) takes as input a public key pk, a message m and a signature \(\sigma \). It outputs a bit \(b \leftarrow \mathsf {verify}_{sk}(m,\sigma )\), with \(b=1\) meaning valid and \(b=0\) meaning invalid.
A digital signature scheme is required to have perfect completeness, meaning that except with negligible probability over (pk, sk) output by  , it holds that \(\mathsf {verify}_{pk}(m, \mathsf {sign}_{sk}(m))=1\) for every legal message m.
, it holds that \(\mathsf {verify}_{pk}(m, \mathsf {sign}_{sk}(m))=1\) for every legal message m.
Definition 37
(PQ-EU-CMA digital signature scheme, adapted from [31, Definition 12.2]) A digital signature scheme \(\Pi \) is Post-Quantum Existentially Unforgeable under an adaptive Chosen Message Attack (PQ-EU-CMA) if for every QPT forger \(\mathcal {F}\), there exists a negligible function  such that:
such that:

The signature experiment  :
:
-
1.
\(\mathsf {key\text {-}gen}\) is run to generate to obtain keys (pk, sk).
-
2.
Forger \(\mathcal {F}\) is given pk and access to a signing oracle \(\mathsf {sign}_{sk}(\cdot )\). The forger than outputs \((m, \sigma )\). Let Q denote the set of all queries that \(\mathcal {F}\) asked its oracle.
-
3.
\(\mathcal {F}\) succeeds iff \(\mathsf {verify}_{pk}(m, \sigma )=1\) and \(m \notin Q\). In this case, the output of the experiment is defined to be 1 (and otherwise 0).
Lemma 38
(Difference Lemma [47, Lemma 1]) Let A, B, F be events defined in some probability distribution, and suppose that \(A \wedge \lnot F \iff B \wedge \lnot F\). Then,  .
.
C Quantum Lightning with Bolt-to-Certificate
The following definitions are taken almost verbatim from [18]. The definitions originate in [53] and [17], but in this work we use the notations of the superseding work [18].
Definition 39
(Quantum Lightning [53]) A quantum lightning scheme consists of a PPT algorithm  (where
(where  is a security parameter) which samples a pair of QPT algorithms \((\mathsf {gen\text {-}bolt}, \mathsf {verify\text {-}bolt})\). \(\mathsf {gen\text {-}bolt}\) outputs a pair of the form
is a security parameter) which samples a pair of QPT algorithms \((\mathsf {gen\text {-}bolt}, \mathsf {verify\text {-}bolt})\). \(\mathsf {gen\text {-}bolt}\) outputs a pair of the form  . We refer to \(\vert \psi \rangle \) as a “bolt” and to s as a “serial number.” \(\mathsf {verify\text {-}bolt}\) takes as input a pair of the same form, and outputs either “accept” (1) or “reject” (0). They satisfy the following:
. We refer to \(\vert \psi \rangle \) as a “bolt” and to s as a “serial number.” \(\mathsf {verify\text {-}bolt}\) takes as input a pair of the same form, and outputs either “accept” (1) or “reject” (0). They satisfy the following:
-

-
For all
 :
: 
Definition 40
(Security [53]) A quantum lightning scheme \(\mathsf {QL}\) is secure if, for all QPT bolt forgers \(\mathcal {L}\):

The bolt forging game  :
:
-
1.
The challenger runs
 and sends \((\mathsf {gen\text {-}bolt}, \mathsf {verify\text {-}bolt})\) to \(\mathcal {L}\).
and sends \((\mathsf {gen\text {-}bolt}, \mathsf {verify\text {-}bolt})\) to \(\mathcal {L}\). -
2.
\(\mathcal {L}\) produces a pair
 .
. -
3.
The challenger runs \(\mathsf {verify\text {-}bolt}(\cdot , s)\) on each half of \(\vert \Psi _{12} \rangle \). The output of the game is 1 if both outcomes are “accept” (and otherwise 0).
Definition 41
(Bolt-to-certificate) For a quantum lightning scheme \(\mathsf {QL}\) to have bolt-to-certificate capability, we change the procedure  slightly, so that it outputs a quadruple
slightly, so that it outputs a quadruple
where \(\mathsf {gen\text {-}certificate}\) is a QPT algorithm that takes as input a quantum money state and a serial number and outputs a classical string of some fixed length  for some polynomially bounded function l, to which we refer as a certificate, and \(\mathsf {verify\text {-}certificate}\) is a PPT algorithm that takes as input a serial number and a certificate, and outputs “accept” (1) or “reject” (0).
for some polynomially bounded function l, to which we refer as a certificate, and \(\mathsf {verify\text {-}certificate}\) is a PPT algorithm that takes as input a serial number and a certificate, and outputs “accept” (1) or “reject” (0).
Let  . We say that a quantum lightning scheme \(\mathsf {QL}\) has bolt-to-certificate capability if:
. We say that a quantum lightning scheme \(\mathsf {QL}\) has bolt-to-certificate capability if:
-

-
For all QPT algorithms \(\mathcal {C}\):

The certificate forging game  :
:
-
1.
The challenger runs

and sends the quadruple to \(\mathcal {C}\).
-
2.
\(\mathcal {C}\) returns
 and \((\vert \psi \rangle , s)\).
and \((\vert \psi \rangle , s)\). -
3.
The challenger runs \(\mathsf {verify\text {-}certificate}(s,c)\) and \(\mathsf {verify\text {-}bolt}(\vert \psi \rangle , s)\), and outputs 1 if they both accept (otherwise outputs 0).
D Trapdoor Claw-Free Families
Most of this section is taken verbatim from Brakerski et al. [13]. Let  be a security parameter, and let \(\mathcal {X}\) and \(\mathcal {Y}\) be finite sets (depending on
be a security parameter, and let \(\mathcal {X}\) and \(\mathcal {Y}\) be finite sets (depending on  ). For our purposes, an ideal family of functions \(\mathcal {F}\) would have the following properties. For each public key k, there are two functions \(\{f_{k,b}:\mathcal {X}\rightarrow \mathcal {Y}\}_{b\in \{0,1\}}\) that are both injective, that have the same range (equivalently, \((b,x)\mapsto f_{k,b}(x)\) is 2-to-1), and that are invertible given a suitable trapdoor \(t_k\) (i.e., \(t_k\) can be used to compute x given b and \(y=f_{k,b}(x)\)). Furthermore, the pair of functions should be claw-free: it must be hard for an attacker to find two pre-images \(x_0,x_1\in \mathcal {X}\) such that \(f_{k,0}(x_0) = f_{k,1}(x_1)\). Finally, the functions should satisfy an adaptive hardcore bit property, which is a stronger form of the claw-free property: assuming for convenience that \(\mathcal {X}= \{0,1\}^w\), we want it to be computationally infeasible to simultaneously generate \((b,x_b)\in \{0,1\}\times \mathcal {X}\) and a nonzero string \(d\in \{0,1\}^w\) such that with a non-negligible advantage over \(\frac{1}{2}\) the equation \(d\cdot (x_0\oplus x_1)=0\) holds, where \(x_{1-b}\) is defined as the unique element such that \(f_{k,1-b}(x_{1-b})=f_{k,b}(x_b)\).
). For our purposes, an ideal family of functions \(\mathcal {F}\) would have the following properties. For each public key k, there are two functions \(\{f_{k,b}:\mathcal {X}\rightarrow \mathcal {Y}\}_{b\in \{0,1\}}\) that are both injective, that have the same range (equivalently, \((b,x)\mapsto f_{k,b}(x)\) is 2-to-1), and that are invertible given a suitable trapdoor \(t_k\) (i.e., \(t_k\) can be used to compute x given b and \(y=f_{k,b}(x)\)). Furthermore, the pair of functions should be claw-free: it must be hard for an attacker to find two pre-images \(x_0,x_1\in \mathcal {X}\) such that \(f_{k,0}(x_0) = f_{k,1}(x_1)\). Finally, the functions should satisfy an adaptive hardcore bit property, which is a stronger form of the claw-free property: assuming for convenience that \(\mathcal {X}= \{0,1\}^w\), we want it to be computationally infeasible to simultaneously generate \((b,x_b)\in \{0,1\}\times \mathcal {X}\) and a nonzero string \(d\in \{0,1\}^w\) such that with a non-negligible advantage over \(\frac{1}{2}\) the equation \(d\cdot (x_0\oplus x_1)=0\) holds, where \(x_{1-b}\) is defined as the unique element such that \(f_{k,1-b}(x_{1-b})=f_{k,b}(x_b)\).
Unfortunately, we (as well as Brakerski et al.) do not know how to construct a function family that exactly satisfies all these requirements under standard cryptographic assumptions. Instead, Brakerski et al. construct a family that satisfies slightly relaxed requirements based on the hardness of the learning with errors (LWE) problem, and we will show that these are still adequate for our purposes. The requirements are relaxed as follows. First, the range of the functions is no longer a set \(\mathcal {Y}\); instead, it is \(\mathcal {D}_{\mathcal {Y}}\), the set of probability densities over \(\mathcal {Y}\). That is, each function returns a density, rather than a point. The trapdoor injective pair property is then described in terms of the support of the output densities: These supports should either be identical for a colliding pair or be disjoint in all other cases.
The consideration of functions that return densities elicits an additional requirement of efficiency: there should exist a quantum polynomial-time procedure that efficiently prepares a superposition over the range of the function, i.e., for any key k and \(b\in \{0,1\}\), the procedure can prepare a state that is close (up to a negligible trace distance) to the state
We modify the adaptive hardcore bit requirement slightly. Since the set \(\mathcal {X}\) may not be a subset of binary strings, we first assume the existence of an injective, efficiently invertible map \(J:\mathcal {X}\rightarrow \{0,1\}^w\). Next, we only require the adaptive hardcore bit property to hold for a subset of all nonzero strings rather than for the set \(\{0,1\}^w\setminus \{0^w\}\). Finally, membership in the appropriate set should be efficiently checkable, given access to the trapdoor.
Definition 42
(NTCF family) Let  be a security parameter. Let \(\mathcal {X}\) and \(\mathcal {Y}\) be finite sets. Let \(\mathcal {K}_{\mathcal {F}}\) be a finite set of keys. A family of functions
be a security parameter. Let \(\mathcal {X}\) and \(\mathcal {Y}\) be finite sets. Let \(\mathcal {K}_{\mathcal {F}}\) be a finite set of keys. A family of functions
is called a noisy trapdoor claw-free (NTCF) family if the following conditions hold:
-
1.
Efficient Function Generation. There exists an efficient probabilistic algorithm \(\mathsf {key\text {-}gen}_{\mathcal {F}}\) which generates a key \(k\in \mathcal {K}_{\mathcal {F}}\) together with a trapdoor \(t_k\):

-
2.
Trapdoor Injective Pair. For all keys \(k\in \mathcal {K}_{\mathcal {F}}\), the following conditions hold.
-
(a)
Trapdoor: For all \(b\in \{0,1\}\) and \(x\ne x' \in \mathcal {X}\), \(\textsc {Supp}(f_{k,b}(x))\cap \textsc {Supp}(f_{k,b}(x')) = \emptyset \). Moreover, there exists an efficient deterministic algorithm \(\text {INV}_{\mathcal {F}}\) such that for all \(b\in \{0,1\}\), \(x\in \mathcal {X}\) and \(y\in \textsc {Supp}(f_{k,b}(x))\), \(\text {INV}_{\mathcal {F}}(t_k,b,y) = x\).
-
(b)
Injective pair: There exists a perfect matching \(\mathcal {R}_k \subseteq \mathcal {X}\times \mathcal {X}\) such that \(f_{k,0}(x_0) = f_{k,1}(x_1)\) if and only if \((x_0,x_1)\in \mathcal {R}_k\).
-
(a)
-
3.
Efficient range superposition.Footnote 24 There exists an efficient procedure SAMP\(_{\mathcal {F}}\) that on input k and \(b\in \{0,1\}\) prepares a state \(\vert \psi ' \rangle \) which has a negligible trace distance to the state
$$\begin{aligned} \vert \psi \rangle = \frac{1}{\sqrt{|\mathcal {X}|}}\sum _{x\in \mathcal {X},y\in \mathcal {Y}}\sqrt{(f_{k,b}(x))(y)}\vert x \rangle \vert y \rangle \;. \end{aligned}$$ -
4.
Adaptive Hardcore Bit. For all keys \(k\in \mathcal {K}_{\mathcal {F}}\), the following conditions hold, for some integer w that is a polynomially bounded function of
 .
. -
(a)
For all \(b\in \{0,1\}\) and \(x\in \mathcal {X}\), there exists a set \(G_{k,b,x}\subseteq \{0,1\}^{w}\) such that \(\Pr _{d\leftarrow _U \{0,1\}^w}[d\notin G_{k,b,x}]\) is negligible, and moreover there exists an efficient algorithm that checks for membership in \(G_{k,b,x}\) given k, b, x and the trapdoor \(t_k\).
-
(b)
There is an efficiently computable injection \(J:\mathcal {X}\rightarrow \{0,1\}^w\), such that \(J\) can be inverted efficiently on its range, and such that the following holds. If
 (8)
(8)Footnote 25 then for any quantum polynomial-time procedure \(\mathcal {A}\) there exists a negligible function \(\mu (\cdot )\) such that
 (9)
(9)
-
(a)
Theorem 43
(Informal) Under the assumption that the learning with errors (LWE) problem with certain parameters is hard for \(\textsf {BQP}\), an NTCF family exists.
The hardness definition of LWE and the exact parameters required for the theorem above are given in [13, Theorem 26].
E The Advantage of Memoryless Money
When discussing any form of quantum money, we must consider the motivation, i.e., the benefits over classical constructions—for example, we could construct a rudimentary private classical money scheme in the following way: Upon minting, the bank would produce a random serial number significantly long for some security parameter  and sign it using a MAC. The bank would maintain a database of all banknotes that have already been spent, and upon verification, after verifying the MAC tag of the banknote, the bank would search for its serial number within the database—if it is not there, the verification succeeds and the serial number is added to the database, and if it is there the bank would know the money was already spent and thus verification will fail (of course, the bank would have to mint a new banknote for the user after a successful verification). Gavinsky [24] discusses a similar notion.
and sign it using a MAC. The bank would maintain a database of all banknotes that have already been spent, and upon verification, after verifying the MAC tag of the banknote, the bank would search for its serial number within the database—if it is not there, the verification succeeds and the serial number is added to the database, and if it is there the bank would know the money was already spent and thus verification will fail (of course, the bank would have to mint a new banknote for the user after a successful verification). Gavinsky [24] discusses a similar notion.
This scheme is counterfeit-resistant according to our security definitions. However, it is memory-dependent (also known as state-based); i.e., the bank has to maintain a database to represent an ongoing state, remembering the banknotes that were spent. On its own, a memory-dependent protocol is not a terrible problem; many services maintain a database. This, however, becomes a liability when considering multiple branches of the same bank: a central database must maintain the shared state and synchronize the access to it (otherwise information would have to propagate between the branches, causing potential security breaches during the propagation time); this has a toll in terms of response time and communication.
Constructing a memory-dependent (classical) private money scheme is trivial—the scheme above is an extremely simple example—so such a construction is not particularly interesting. The case is different, however, in the public setting; constructing even a memory-dependent quantum money scheme that is publicly secure is challenging (and impossible to achieve classically), and thus such a construction is an interesting result.
In semi-quantum money we assumed the users are quantum while the bank branches are classical. It is natural to consider reversing this setting so that the users are classical and only the bank branches are quantum. We note that in any setting where the users are classical, any verification must involve communication between all branches: Consider an adversary which receives one bill from the bank by following the minting protocol. The adversary now has a classical state, which we denote by S. At this point, if the adversary follows the (honest) verification protocol with branch \(B_1\), verification would accept, since his bill was valid. The adversary could now rewind his classical state to S and run the verification with branch \(B_2\). Since the branches are not allowed to communicate, the second branch would also accept. In other words, double-spending becomes trivial in any scheme in which there are multiple, non-communicating quantum bank branches. We emphasize that our private semi-quantum money construction does not require communication between the bank branches.
F Parallel Repetition of Weakly Verifiable Puzzles
As seen in Sect. 4.3, our main tool for proving parallel repetition for 1-of-2 puzzles is the notion of weakly verifiable puzzles introduced by [15]. This section provides a brief informal overview of their parallel repetition proof for weakly verifiable puzzles (Theorem 20).
The goal is to show a reduction from an algorithm A (which in our case may be quantum) that solves n weakly verifiable puzzles in parallel with probability at least  for some non-negligible h to an algorithm \(A'\) solving a single puzzle with probability at least
for some non-negligible h to an algorithm \(A'\) solving a single puzzle with probability at least  . This shows that the best strategy for solving n puzzles has the same probability (up to a negligible difference) of solving each puzzle separately.
. This shows that the best strategy for solving n puzzles has the same probability (up to a negligible difference) of solving each puzzle separately.
Denote the event where A solves the puzzle \(p_i\) correctly by \(S_i\), and denote the event where A solves puzzles \(p_k, \ldots , p_n\) correctly by \(R_k\). We call a puzzle coordinate \(i \in [n]\) good if it holds that  , i.e., if the probability that A solved \(p_i\) correctly conditioned on the probability that A solved \(p_{i+1}, \ldots , p_{n}\) correctly is at least h, where the probability is taken over the randomness of A as well as over the random choices of puzzles \(p_1, \ldots , p_n\). We make the following statistical observation:
, i.e., if the probability that A solved \(p_i\) correctly conditioned on the probability that A solved \(p_{i+1}, \ldots , p_{n}\) correctly is at least h, where the probability is taken over the randomness of A as well as over the random choices of puzzles \(p_1, \ldots , p_n\). We make the following statistical observation:

The last inequality holds because we know the probability of A to solve all n puzzles is at least \(h^n\). Therefore, we conclude that at least one of the following must hold: either \(\underset{p_1,\ldots ,p_n}{\Pr }[S_1|R_2] \ge h\), or \(\underset{p_1,\ldots ,p_n}{\Pr }[R_2] \ge h^{n-1}\). Meaning either 1 is a good coordinate, or the probability that A solves the last \(n-1\) puzzles of its input is at least \(h^{n-1}\).
If 1 is a good coordinate, then \(A'\) solves its original puzzle in the following way: \(A'\) runs A with \((p, p_2, \ldots , p_n)\)—where p is the original challenge puzzle and \(p_2, \ldots , p_n\) are randomly generated by \(A'\)—until puzzles \(p_2, \ldots , p_n\) were solved correctly.Footnote 26 Since 1 is a good coordinate, we know that if A solved puzzles \(p_2, \ldots , p_n\) correctly, the first puzzle is also solved correctly with probability at least h, as needed.
If 1 is not a good coordinate, then we know the probability of A to solve \(n-1\) puzzles is at least \(h^{n-1}\). This provides us with a solver for \(n-1\) puzzles with probability at least  , and the reduction continues by induction. Eventually, \(A'\) will either reach a good coordinate i and solve it with probability at least h as described above, or arrive at a solver that solves a single puzzle—the last puzzle—with probability at least h.
, and the reduction continues by induction. Eventually, \(A'\) will either reach a good coordinate i and solve it with probability at least h as described above, or arrive at a solver that solves a single puzzle—the last puzzle—with probability at least h.
To find out whether i is a good coordinate, A estimates \(\underset{p_1,\ldots ,p_n}{\Pr }[S_i|R_{i+1}]\). This is done by generating n puzzles, and running A multiple times, all the while checking whether puzzles \(p_{i+1}, \ldots , p_n\) were solved correctly, and if so checking whether puzzle \(p_i\) was also solved correctly. Since  , this estimation can be done efficiently with high probability.
, this estimation can be done efficiently with high probability.
The proof itself in [15] is more complex than the outline given here. For example, we cannot know for sure if a coordinate is a good coordinate, since we can only estimate the probabilities within some polynomial bounds—the original proof deals with these issues.
Note that this parallel repetition is “perfect”—i.e., it shows that the best strategy for solving multiple puzzles has the same probability as solving them separately (up to a negligible difference). This would not be the case if we had more than 2 rounds—for 3 rounds the repetition would not be perfect, and for 4 rounds the soundness error does not decrease exponentially at all [10]. We can see that the proof above indeed would not work for more than 2 rounds: In our reduction, when we find a good coordinate i, we run the multiple-puzzle adversary multiple times until the puzzles \(p_{i+1}, \ldots , p_n\) are solved correctly, and then our original puzzle is solved correctly with probability h. But in the case of multiple rounds, the single-puzzle adversary is required to provide the multiple-puzzle adversary with messages from the challenger for all the puzzles, including the original one. The answers of the multiple-puzzles adversary for each puzzle can therefore depend on messages for all the puzzles, but we can run the protocol for the original puzzle with the challenger only once—i.e., we cannot provide the challenger’s answers for the original puzzles more than once. Therefore, we cannot condition on the adversary solving \(p_{i+1}, \ldots , p_n\) correctly, meaning that if we can run the adversary only once our success probability will not be h as needed.
G Transaction Figures
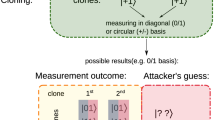
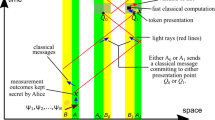
This section contains figures showing transactions can be made with each flavor of quantum money and the kind of communication they require (quantum or classical). Fat arrows \(\Rightarrow \) indicate quantum communication, and thin arrows \(\rightarrow \) indicate classical communication. A two-sided arrow indicates two-sided communication (Figs. 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15).
Private classically verifiable direct transaction for a scheme which allows multiple verifications for the same banknote. Note that after a finite number of verifications the banknote is destroyed and communication with the bank is required, like in Fig. 6
Classically verifiable bank transaction for a scheme which allows multiple verifications for the same banknote. For some such schemes, it could be possible to have a classical verification that ensures the banknote was destroyed, in which case a transaction through the bank could be executed like in Fig. 11
Rights and permissions
About this article
Cite this article
Radian, R., Sattath, O. Semi-quantum Money. J Cryptol 35, 8 (2022). https://doi.org/10.1007/s00145-021-09418-8
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s00145-021-09418-8



 , we could construct a bolt forger
, we could construct a bolt forger  bolts and with non-negligible probability end up with two bolts with the same serial number that pass
bolts and with non-negligible probability end up with two bolts with the same serial number that pass  passes with non-negligible probability a verification of some
passes with non-negligible probability a verification of some  to construct a digital signature forger
to construct a digital signature forger  against the simulated bank and will be able to present
against the simulated bank and will be able to present  is indeed polynomial in
is indeed polynomial in  - since a weak 1-of-2 puzzle holds that
- since a weak 1-of-2 puzzle holds that  .
. passes with non-negligible probability a verification of
passes with non-negligible probability a verification of  to construct a forger
to construct a forger  against the simulated bank, and will be able to present c, t which pass MAC verification with non-negligible probability, while he did not ask for a tag of c before since
against the simulated bank, and will be able to present c, t which pass MAC verification with non-negligible probability, while he did not ask for a tag of c before since  can, of course, run several mint protocols simultaneously. We number them according to the order they were initiated.
can, of course, run several mint protocols simultaneously. We number them according to the order they were initiated. always outputs keys of the same length.
always outputs keys of the same length. is non-negligible. Assume without loss of generality that
is non-negligible. Assume without loss of generality that  probability to win, which is non-negligible, in contradiction to the security of ENC.
probability to win, which is non-negligible, in contradiction to the security of ENC. :
: and outputs a key
and outputs a key  .
. takes as input a key k and a plaintext message
takes as input a key k and a plaintext message  .
. and classical oracle access to
and classical oracle access to  and outputs a key k
and outputs a key k takes as input a key k and a message
takes as input a key k and a message  .
. .
. , classical oracle access to
, classical oracle access to  and classical oracle access to
and classical oracle access to  and outputs a pair of keys (pk, sk). These are called the public key and the private key, respectively. We assume that pk and sk each has length of at least
and outputs a pair of keys (pk, sk). These are called the public key and the private key, respectively. We assume that pk and sk each has length of at least  and that
and that  can be determined from either.
can be determined from either.
 :
: 
 and sends
and sends  .
.


 and
and 
 .
. 














