Abstract
We investigate a method for finding small integer solutions of a univariate modular equation, that was introduced by Coppersmith (Proceedings of Eurocrypt 1996, LNCS, vol 1070, pp 155–165, 1996) and extended by May (New RSA vulnerabilities using lattice reduction methods, Ph.D. thesis, University of Paderborn, 2003). We will refer this method as the Coppersmith technique. This paper provides a way to analyze a general limitations of the lattice construction for the Coppersmith technique. Our analysis upper bounds the possible range of U that is asymptotically equal to the bound given by the original result of Coppersmith and May. This means that they have already given the best lattice construction. In addition, we investigate the optimality for the bivariate equation to solve the small inverse problem, which was inspired by Kunihiro’s (LNCS 7483:55–69, 2012) argument. In particular, we show the optimality for the Boneh–Durfee’s equation (Proceedings of Eurocrypt 1999, LNCS, vol 1592, pp 389–401, 1999) used for RSA cryptoanalysis, To show our results, we establish framework for the technique by following the relation of Howgrave-Graham (Proceedings of cryptography and coding, LNCS, vol 1355, pp 131–142, 1997), and then concretely define the conditions in which the technique succeed and fails. We then provide a way to analyze the range of U that satisfies these conditions. Technically, we show that the original result of Coppersmith achieves the optimal bound for U when constructing a lattice in the standard way. We then provide evidence which indicates that constructing a non-standard lattice is generally difficult.



Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Notes
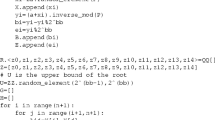
The real root isolation can be performed in polynomial time [9]. Then, rounding the approximate solutions found by using Newton’s method can recover the integer solutions.
References
Aono, Y.: A new lattice construction for partial key exposure attack for RSA. In: Proceedings of PKC 2009, LNCS, vol. 5443, pp. 34–53 (2009). http://www.is.titech.ac.jp/research/research-report/C/C-257.pdf
Aono, Y.: Minkowski sum based lattice construction for multivariate simultaneous Coppersmith’s technique and applications to RSA. In: Proceedings of ACISP 2013, LNCS vol. 7959, pp. 88–103 (2013)
Aono, Y., Agrawal, M., Satoh, T., Watanabe, O.: On the optimality of lattices for the Coppersmith technique. In: Proceedings of ACISP 2012, LNCS, vol. 7372, pp. 376–389 (2012)
Boneh, D., Durfee, G.: Cryptanalysis of RSA with private Key \(d\) Less Than \(N^{0.292}\). In: Proceedings of Eurocrypt 1999, LNCS, vol. 1592, pp. 389–401 (1999)
Blömer, J., May, A.: New partial key exposure attacks on RSA. In: Proceedings of CRTPTO 2003, LNCS, vol. 2729, pp. 27–43 (2003)
Boneh, D.: Finding smooth integers in short intervals using CRT decoding. In: Proceedings of STOC 2000, pp. 265–272 (2000)
Coppersmith, D.: Finding a small root of a univariate modular equation. In: Proceedings of Eurocrypt 1996, LNCS, vol. 1070, pp. 155–165 (1996)
Coppersmith, D.: Finding small solutions to small degree polynomials. In: Proceedings of CaLC 2001, LNCS, vol. 2146, pp. 20–31 (2001)
Collins, G.E., Akritas, A.G.: Polynomial real root isolation using Descartes’ rule of signs. In: Proceedings of the ACM Symposium on Symbolic and Algebraic Computation, pp. 272–275 (1976)
Cohn, H., Heninger, N.: Ideal forms of Coppersmith’s theorem and Guruswami–Sudan list decoding. Proc. ICS 2011, 298–308 (2011)
Chinburg, T., Hemenway, B., Heninger, N., Scherr, Z.: Cryptographic applications of capacity theory: on the optimality of Coppersmith’s method for univariate polynomials. In: Proceedings of Asiacrypt 2016, Part I, LNCS, vol. 10031, pp. 759–788 (2016)
Ernst, M., Jochemsz, E., May, A., Weger, B.: Partial key exposure attacks on RSA up to full size exponents. In: Proceedings of Eurocrypt 2005, LNCS, vol. 3494, pp. 371–386 (2005)
Gama, N., Nguyen, P.Q.: Predicting lattice reduction. In: Proceedings of Eurocrypt 2008, Lecture Notes in Computer Science, vol. 4965, pp. 31–51 (2008)
Gianni, P.: Trager, B.: Square-free algorithms in positive characteristic. In: Applicable Algebra in Engineering, Communication and Computing, vol. 7(1), pp. 1–14 (1996)
Håstad, J.: Solving simultaneous modular equations of low degree. SIAM J. Comput. 17(2), 336–341 (1988)
Howgrave-Graham, N.: Finding small roots of univariate modular equations revisited. Proceedings of Cryptography and Coding, LNCS, vol. 1355, pp. 131–142 (1997)
Howgrave-Graham, N.: Approximate integer common divisors. Proceedings of CaLC 2001, LNCS, vol. 2146, pp. 51–66 (2001)
Jochemsz, E., May, A.: A strategy for finding roots of multivariate polynomials with new applications in attacking RSA variants. In: Proceedings of Asiacrypt 2006, LNCS, vol. 4284, pp. 267–282 (2006)
Kunihiro, N.: On optimal bounds of small inverse problems and approximate GCD problems with higher degree. LNCS 7483, 55–69 (2012)
Konyagin, S.V., Steger, T.: On polynomial congruences. Math. Notes 55(6), 596–600 (1994)
Lenstra, A.K., Lenstra Jr., H.W., Lovász, L.: Factoring polynomials with rational coefficients. Math. Ann. 261, 515–534 (1982)
Milne, J.S.: Étale Cohomology, Princeton Math. Series 33. Princeton University Press (1980)
May, A.: New RSA Vulnerabilities Using Lattice Reduction Methods, Ph.D thesis, University of Paderborn (2003)
Nguyen, P.Q., Vallée, B.: The LLL Algorithm: Survey and Applications. Springer, Berlin (2009)
Okamoto, T., Shiraishi, A.: A fast signature scheme based on quadratic inequalities. In: Proceedings of the Symposium on Security and Privacy, IEEE, pp. 123–132 (1985)
Rogers, C.A.: The number of lattice points in a set. Proc. Lond. Math. Soc. 3(6), 305–320 (1956)
Prudnikov, A.P., Brychkov, Y.A., Marichev, O.I.: Integrals and Series, vol. 1, Elementary Functions. Gordon and Breach, New York (1986)
Rivest, R.L., Shamir, A., Adleman, L.: A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 21(2), 120–128 (1978)
Shoup, V.: OAEP Reconsidered. J. Cryptol. 15(4), 223–249 (2002). http://shoup.net/papers/oaep.pdf
Södergren, A.: On the Poisson distribution of lengths of lattice vectors in a random lattice. Math. Z. 269(3–4), 945–954 (2011)
Schnorr, C.P., Euchner, M.: Lattice basis reduction: improved practical algorithms and solving subset sum problems. Math. Program. 66(1–3), 181–199 (1994)
Vallee, B., Girault, M., Toffin, P.: How to break Okamoto’s cryptosystems by reducing lattices bases. In: Proceedings of Eurocrypt 1988, LNCS, vol. 330, pp. 281–291 (1988)
Acknowledgements
We thank the anonymous referees for their helpful comments.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Aono, Y., Agrawal, M., Satoh, T. et al. On the optimality of lattices for the coppersmith technique. AAECC 29, 169–195 (2018). https://doi.org/10.1007/s00200-017-0336-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00200-017-0336-9