Abstract
Two kinds of automata are presented, for recognising new classes of regular and context-free nominal languages. We compare their expressive power with analogous proposals in the literature, showing that they express novel classes of languages. Although many properties of classical languages hold no longer in the nominal case, we design a slight restriction of our models that preserve some interesting ones. In particular, we prove the emptiness problem decidable and we construct the intersection between (restricted) regular and context-free automata. By examples and walking through their properties we argue the relevance of our models in the context of the verification of resource usage patterns.









Similar content being viewed by others
Notes
Consequently, we have that \(\langle q, [N_{1},\dots ,N_{r}],S\rangle \rightarrow \langle q', [N_{1}',\dots ,N_{r}'],S'\rangle \) iff there exists
 satisfying the conditions \((2-3)\) of Definition 12 and the following holds:
satisfying the conditions \((2-3)\) of Definition 12 and the following holds: - (1m):
-
\( {\left\{ \begin{array}{ll} \sigma = \top \Rightarrow top(S) \text { is defined}\\ \sigma = i \Rightarrow \text {s-top}(N_{i}) \text { is defined} \end{array}\right. }\)
If \(\langle q, [N_{1},\dots ,N_{r}],S\rangle \rightarrow \langle q', [N_{1}',\dots ,N_{r}'],S'\rangle \) because there exists
 satisfying the conditions (1m, 2, 3) then by setting for any \(w'\) the word w such that$$\begin{aligned} {\left\{ \begin{array}{ll} \sigma &{}= \varepsilon \Rightarrow w = w' \\ \sigma &{}= \top \Rightarrow w = aw' \\ \sigma &{}= i \Rightarrow w = aw' \end{array}\right. } \end{aligned}$$
satisfying the conditions (1m, 2, 3) then by setting for any \(w'\) the word w such that$$\begin{aligned} {\left\{ \begin{array}{ll} \sigma &{}= \varepsilon \Rightarrow w = w' \\ \sigma &{}= \top \Rightarrow w = aw' \\ \sigma &{}= i \Rightarrow w = aw' \end{array}\right. } \end{aligned}$$we have that also \(\langle q,w, [N_{1},\dots ,N_{r}],S\rangle \rightarrow \langle q', w',[N_{1}',\dots ,N_{r}'],S'\rangle \). By induction, if \(\langle q, [N_{1},\dots ,N_{r}],S \rangle \rightarrow ^{*} \langle q', [N_{1}',\dots ,N_{r}'],S' \rangle \) then for any word \(w'\) there exists a word w such that \(\langle q,w, [N_{1},\dots ,N_{r}],S \rangle \rightarrow ^{*} \langle q',w', [N_{1}',\dots ,N_{r}'],S' \rangle \).
References
Abadi, M., Needham, R.M.: Prudent engineering practice for cryptographic protocols. IEEE Trans. Softw. Eng. 22(1), 6–15 (1996). doi:10.1109/32.481513
Amarilli, A., Jeanmougin, M.: A proof of the pumping lemma for context-free languages through pushdown automata (2012). arXiv:1207.2819
Bartoletti, M., Costa, G., Degano, P., Martinelli, F., Zunino, R.: Securing Java with local policies. JOT 8(4), 5–32 (2009)
Bartoletti, M., Degano, P., Ferrari, G.L.: Planning and verifying service composition. JCS 17(5), 799–837 (2009)
Bartoletti, M., Degano, P., Ferrari, G.L., Zunino, R.: Semantics-based design for secure web services. IEEE Trans. Softw. Eng. 34(1), 33–49 (2008)
Bartoletti, M., Degano, P., Ferrari, G.L., Zunino, R.: Local policies for resource usage analysis. ACM Trans. Program. Lang. Syst. 31(6), 23 (2009)
Bartoletti, M., Degano, P., Ferrari, G.L., Zunino, R.: Model checking usage policies. Math. Struct. Comput. Sci. 25(3), 710–763 (2015)
Bartoletti, M., Zunino, R.: LocUsT: a tool for checking usage policies. Tech. Rep. TR08-07, University of Pisa (2008)
Belkhir, W., Chevalier, Y., Rusinowitch, M.: Guarded variable automata over infinite alphabets (2013). arXiv:1304.6297
Belkhir, W., Rossi, G., Rusinowitch, M.: A parametrized propositional dynamic logic with application to service synthesis. In: Advances in Modal Logic 10, invited and Contributed Papers from the Tenth Conference on “Advances in Modal Logic, Groningen, The Netherlands, 5–8 August 2014, pp. 34–53 (2014). http://www.aiml.net/volumes/volume10/Belkhir-Rossi-Rusinowitch.pdf
Benedikt, M., Ley, C., Puppis, G.: Automata vs. logics on data words. In: Dawar, A., Veith, H. (eds.) CSL, LNCS, vol. 6247, pp. 110–124. Springer, Berlin (2010)
Bojańczyk, M., Klin, B., Lasota, S.: Automata theory in nominal sets (2011). http://www.mimuw.edu.pl/sl/PAPERS/lics11full.pdf
Bojanczyk, M., Klin, B., Lasota, S.: Automata with group actions. In: LICS, pp. 355–364. IEEE Computer Society, Washington, DC, USA (2011). doi:10.1109/LICS.2011.48
Bollig, B.: An automaton over data words that captures EMSO logic. In: Katoen, J.P. , König, B. (eds.) CONCUR 2011, LNCS, vol. 6901, pp. 171–186. Springer, Berlin (2011)
Bollig, B., Cyriac, A., Gastin, P., Kumar, K.N.: Model checking languages of data words. In: Birkedal, L. (ed.) FOSSACS 2012, LNCS, vol. 7213, pp. 391–405. Springer, Berlin (2012)
Chaki, S., Rajamani, S.K., Rehof, J.: Types as models: model checking message-passing programs. In: Conference Record of POPL 2002: The 29th SIGPLAN-SIGACT Symposium on Principles of Programming Languages, Portland, OR, USA, January 16–18, 2002, pp. 45–57 (2002)
Cheng, E.Y.C., Kaminski, M.: Context-free languages over infinite alphabets. Acta Inf. 35(3), 245–267 (1998)
Ciancia, V., Tuosto, E.: A novel class of automata for languages on infinite alphabets. Tech. rep., CS-09-003, University of Leicester, UK (2009)
Degano, P., Ferrari, G.L., Mezzetti, G.: Nominal automata for resource usage control. In: Moreira, N., Reis, R. (eds.) CIAA 2012, LNCS, vol. 7381, pp. 125–137. Springer, Berlin (2012)
Dierks, T., Rescorla, E.: RFC 5246: The Transport Layer Security (TLS) Protocol Version 1.2 (2008). http://tools.ietf.org/html/rfc5246
Ferris, C., Farrell, J.: What are web services? Commun. ACM 46(6), 31 (2003). doi:10.1145/777313.777335
Gabbay, M., Pitts, A.: A new approach to abstract syntax with variable binding. Form. Asp. Comput. 13(3), 341–363 (2002)
Gershenfeld, N., Krikorian, R., Cohen, D.: The internet of things. Sci. Am. 291(4), 76 (2004)
Gong, Z., Gu, X., Wilkes, J.: PRESS: predictive elastic resource scaling for cloud systems. In: Proceedings of the 6th International Conference on Network and Service Management, CNSM 2010, Niagara Falls, Canada, October 25–29, 2010, pp. 9–16 (2010). doi:10.1109/CNSM.2010.5691343
Gordon, A.D.: Notes on nominal calculi for security and mobility. In: Focardi, R., Gorrieri, R. (eds.) FOSAD 2000, LNCS, vol. 2171, pp. 262–330. Springer, Berlin (2001)
Grigore, R., Distefano, D., Petersen, R.L., Tzevelekos, N.: Runtime verification based on register automata. In: Tools and Algorithms for the Construction and Analysis of Systems—19th International Conference, TACAS 2013, Lecture Notes in Computer Science, vol. 7795, pp. 260–276. Springer, Berlin (2013)
Grumberg, O., Kupferman, O., Sheinvald, S.: Variable automata over infinite alphabets. In: Dediu, A.H., Fernau, H., Martín-Vide, C. (eds.) LATA, LNCS, vol. 6031, pp. 561–572. Springer, Berlin (2010)
Jensen, T.P., Métayer, D.L., Thorn, T.: Verification of control flow based security properties. In: 1999 IEEE Symposium on Security and Privacy, Oakland, California, USA, May 9–12, 1999, pp. 89–103 (1999)
Kaminski, M., Francez, N.: Finite-memory automata. TCS 134(2), 329–363 (1994)
Kaminski, M., Zeitlin, D.: Finite-memory automata with non-deterministic reassignment. Int. J. Found. Comput. Sci. 21(5), 741–760 (2010)
Kurz, A., Suzuki, T., Tuosto, E.: On nominal regular languages with binders. In: Birkedal, L., (ed.) FOSSACS 2012, LNCS, vol. 7213, pp. 255–269. Springer, Berlin (2012)
Kurz, A., Suzuki, T., Tuosto, E.: Nominal regular expressions for languages over infinite alphabets. Extended abstract (2013). arXiv:1310.7093
Manuel, A., Muscholl, A., Puppis, G.: Walking on data words. In: Mogens, N., Branislav, R. (eds.) Computer Science-Theory and Applications, pp. 64–75. Springer, Berlin (2013)
Mezzetti, G.: Nominal context-free behaviour. Ph.D. thesis, University of Pisa (2014)
Minsky, M.L.: Computation: Finite and Infinite Machines. Prentice-Hall, Englewood Cliffs, NJ (1967)
Montanari, U., Pistore, M.: \(\pi \)-calculus, structured coalgebras, and minimal hd-automata. In: Mogens, N., Branislav, R. (eds.) MFCS 2000, LNCS, vol. 1893, pp. 569–578. Springer, Berlin (2000)
Murawski, A.S., Ramsay, S.J., Tzevelekos, N.: Reachability in pushdown register automata. In: Csuhaj-Varjú, E., Dietzfelbinger, M., Ésik, Z. (eds.) Mathematical Foundations of Computer Science 2014 - 39th International Symposium, MFCS 2014, Budapest, Hungary, August 25–29, 2014. Proceedings, Part I, Lecture Notes in Computer Science, vol. 8634, pp. 464–473. Springer, Berlin (2014). doi:10.1007/978-3-662-44522-8_39
Neven, F., Schwentick, T., Vianu, V.: Towards regular languages over infinite alphabets. Math. Found. Comput. Sci. 2001, 560–572 (2001)
Neven, F., Schwentick, T., Vianu, V.: Finite state machines for strings over infinite alphabets. ACM Trans. Comput. Log. (TOCL) 5(3), 403–435 (2004)
Nielson, F., Nielson, H.R., Hankin, C.: Principles of Program Analysis, 1st ed. 1999. corr. 2nd printing, 1999 edn. Springer, Berlin (2005)
Papazoglou, M.P.: Web Services—Principles and Technology. Prentice Hall, Englewood Cliffs (2008). http://vig.pearsoned.com/store/product/1%2C1207%2Cstore-12521_isbn-0321155556%2C00.html
Parys, P.: Higher-order pushdown systems with data. In: Faella, M., Murano, A. (eds.) GandALF, EPTCS, vol. 96, pp. 210–223 (2012)
Perrin, D., Pin, J.: Infinite words: automata, semigroups, logic and games. Pure Appl. Math. 141 (2004)
Pitts, A.M., Stark, I.D.B.: Observable properties of higher order functions that dynamically create local names, or what’s new? In: Andrzej, M.B., Stefan, S. (eds.) MFCS 1993, LNCS, vol. 711, pp. 122–141. Springer, Berlin (1993)
Schneider, F.B.: Enforceable security policies. ACM Trans. Inf. Syst. Secur. (TISSEC) 3(1), 30–50 (2000)
Skalka, C., Smith, S.F., Horn, D.V.: Types and trace effects of higher order programs. J. Funct. Program. 18(2), 179–249 (2008)
Tzevelekos, N.: Fresh-register automata. ACM SIGPLAN Not. 46(1), 295–306 (2011)
Tzevelekos, N., Grigore, R.: History-register automata. In: Pfenning, F. (ed.) Foundations of Software Science and Computation Structures - 16th International Conference, FOSSACS 2013, Held as Part of the European Joint Conferences on Theory and Practice of Software, ETAPS 2013, Rome, Italy, March 16–24, 2013. Proceedings, vol. 7794, pp. 17–33. Springer, Berlin (2013)
Vardi, M.Y., Wolper, P.: An automata-theoretic approach to automatic program verification. In: LICS, pp. 332–344. IEEE Computer Society (1986)
Acknowledgments
We thank Lillo Galletta, Alexander Kurz, Matteo Sammartino and Nikos Tzevelekos for many helpful discussions and the anonymouos referees for their suggestions.
Author information
Authors and Affiliations
Corresponding author
Additional information
This work has been partially supported by the MIUR PRIN project Security Horizons.
Appendix: Usages
Appendix: Usages
To compare the expressive power of \({\text {PDNA}}_{\pm }\) against \({\text {Usages}}\) we need to extend the expressiveness theorems about \({\text {Usages}}\).
Theorem 9
The language \({\varSigma }^{*}\) is not generated by any \({\text {Usages}}\).
Proof
The proof has the following structure: a new transition system for \({\text {Usages}}\) is given, this is provably equivalent to the original one [7]. Then a few lemmata are proved to provide support for the final argument.
In the following we will use the word redex to identify the source of a transition deduced by only applying an (instance of an) axiom.
Lemma 5
If  and \(\mu h. U\) is its redex, then
and \(\mu h. U\) is its redex, then  .
.
Proof
(By induction on the depth of the proof)
There are two exhaustive cases:
-
Base case: \(U_{0} = \mu h. U \) and the thesis follows easily.
-
Inductive case:
 has been proved by
has been proved by 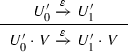
by rule (seq) as last step. By the inductive hypothesis we have that
 and the thesis follows easily.
and the thesis follows easily.
\(\square \)
Lemma 6
If  and k is the least index such that \(\mu h . U\) is the redex of
and k is the least index such that \(\mu h . U\) is the redex of  and rule (rec) is never used in reducing \(U_{i}, i < k\) then \(U_{i} = C_{i}[\mu h. U]\) for some \(C_{i}\) and \(a_{k}=\varepsilon \).
and rule (rec) is never used in reducing \(U_{i}, i < k\) then \(U_{i} = C_{i}[\mu h. U]\) for some \(C_{i}\) and \(a_{k}=\varepsilon \).
Lemma 7
Let  be a computation and let k be the least index such that \(\mu h . U\) is the redex of
be a computation and let k be the least index such that \(\mu h . U\) is the redex of  and rule (rec) is never used in reducing \(U_{i}, i < k\) then \(\exists U_{i}' \equiv U_{i}, i < k\) such that
and rule (rec) is never used in reducing \(U_{i}, i < k\) then \(\exists U_{i}' \equiv U_{i}, i < k\) such that  and (rec) is never used reducing \(U_{i}, 0 \le i \le k\).
and (rec) is never used reducing \(U_{i}, 0 \le i \le k\).
Proof
By Lemma 6
\(U_{i} = C_{i}[\mu h . U], i \le k\), also \(\mu h . U\) is never the redex of \(U_{i}, i < k\), hence also  . By Lemma 5
. By Lemma 5
 . \(\square \)
. \(\square \)
Lemma 8
Let  such that
such that  such that
such that  is deduced using (rec) rule.
is deduced using (rec) rule.
Proof
By repeated application of Lemma 7. \(\square \)
Property 7
(of capture avoiding substitutions) Given \(\mu h . U\), if n occurs in the scope of \(\nu n\), then  contains a term \(\nu n'. U', n' \ne n\) and n does not occur in \(U'\).
contains a term \(\nu n'. U', n' \ne n\) and n does not occur in \(U'\).
Proof
Follows because unfolding a recursion is capture-avoiding and all the bound names are different. \(\square \)
For simplicity , we write \(a_{n}\) for the dynamic resource replacing a name n in U when the rule (new) is applied.
Let U with k occurrences of \(\nu n_{i}\) be such that \(\llbracket U \rrbracket = {\varSigma }^{*}\) and let \(s = a_{n_{1}}a_{n_{2}}\dots a_{n_{k+1}}a_{n_{1}}a_{n_{2}}\dots a_{n_{k+1}}\). By Lemma 8, there exists \(U' \equiv U\) such that  with no transition deduced using rule (rec).
with no transition deduced using rule (rec).
Since \(\nu .n_{k+1}\) does not occur in U, then there exists a subterm of U of the form \(\mu h. {\overline{U}}\), with \(\nu n_{i}. U'', (0 < i \le k)\) in \({\overline{U}}\). Therefore, \(U' = U\{\mu h . {\overline{U}} /h\}\) and the replacing term contains \(\nu n_{k+1}. U''\{n_{k+1}/n_{i}\}, n_{k+1}\ne n_{i}\) for some i because our assumption of keeping bound names apart.
Therefore \(\nu n_{k+1}. U''\{n_{k+1}/n_{i}\}\) occurs in \(U'\) for some \(U''\) (by Lemma 8) and \(n_{i}\) does not occur in \(U''\{n_{k+1}/n_{i}\}\). Also \(n_{k+1}\) must occur at least twice in \(U''\{n_{k+1}/n_{i}\}\) and nowhere else. Since \(U''\{n_{k+1}/n_{i}\}\) can not generate \(a_{n_{i}}\), it can not generate \(a_{n_{k+1}}a_{n_{1}}\dots a_{n_{k}}a_{n_{k+1}}\). \(\square \)
Rights and permissions
About this article
Cite this article
Degano, P., Ferrari, GL. & Mezzetti, G. Regular and context-free nominal traces. Acta Informatica 54, 399–433 (2017). https://doi.org/10.1007/s00236-016-0261-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00236-016-0261-6





 satisfying the conditions
satisfying the conditions  satisfying the conditions (1m, 2, 3) then by setting for any
satisfying the conditions (1m, 2, 3) then by setting for any  has been proved by
has been proved by 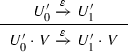
 and the thesis follows easily.
and the thesis follows easily.