Abstract
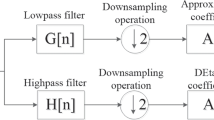
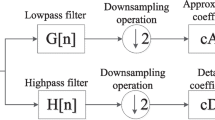
We present a new method for watermarking which is based on redundant wavelet transform (RDWT) and independent component analysis (ICA) for authenticity protection of multimedia products. RDWT gives an over complete presentation of the input sequences and functions as a better approximation to the wavelet transform, and therefore, is well-suitable for watermarking. An advantage of using a large logo is the ability to carry redundant information about copyright, increasing the robustness. By exploiting RDWT, we can embed a large binary logo watermark, which has the same size as the host image. The watermark is detected by a new intelligent ICA-based detector, with which we can directly extract the watermark in spatial domain without transformation steps. Our findings are that RDWT-based watermarking out-performs against image compression, and produces less image distortion than conventional DWT. The robustness of the proposed method is demonstrated and tested under various attacks
Similar content being viewed by others
References
Hien TD, Nakao Z, Chen Y-W (2004) A robust logo multiresolution watermarking based on independent component analysis extraction. In: Lecture notes in computer science, vol 2939. Springer, Berlin Heidelberg New York, pp 408–422
Hien TD, Chen Y-W, Nakao Z (2004) Digital watermarking based on principal component analysis. Int J Comput Intell Appl 4(2), World Scientific Publishing
Hua L, Fowler JE (2002) A performance analysis of spread-spectrum watermarking based on redundant transforms. In: Proceedings of the IEEE international conference on multimedia and expo. Lausanne, Switzerland, vol. 2. pp 553–556
Barni M, Bartolini F, Cappellini V, Lippi A, Piva A. DWT-based technique for spatio-frequency masking of digital signatures. In: Proceedings of SPIE, vol. 3657. Security and Watermarking of Multimedia Contents.
Shensa MJ (1992) The discrete wavelet transform: wedding the ‘Atrous and mallat algorithms. IEEE Trans Signal Process 40(10):2464–2482
Goyal VK, Vetterli M, Thao NT (1998) Quantized overcomplete expansions in IRn: analysis, synthesis, and algorithms. IEEE Trans Inf Theory 44(1):16–31
Xu Y, Weaver JB, Healy DM, Jr, Lu J (1994) Wavelet transform domain filters: a spatially selective noise filtration technique. IEEE Trans Image Proc 3(6):747–758
Barni M, Bartolini F, Piva A (2001) Improved wavelet-based watermarking through pixel-wise masking. IEEE Trans Image Process 10(5):783–791
Hyvärinen A, Oja E (2000) Independent component analysis: algorithms and applications. Neural Netw 13(4):411–430
Voloshynovski S, Herrigel A, Pun NB and T (2000) A stochastic approach tocontent adaptive digital image watermarking. In: Lecture notes in computer science, vol. 1768, pp 212–236
Noel S, Szu H (2000) Multimedia authenticity with independent-component watermarks. In: 14th annual international symposium on aerospace/defense sensing, simulation, and controls, Orlando, Florida
Szu H, Noel S, Yim S-B, Willey J, Landa J (2003) Multimedia authenticity protection with independent component watermarking and digital bacteria vaccination. Neural Netw 16(5–6):907–914
Fei C, Kundur D, Kwong R (2004) Analysis and design of watermarking algorithms for improved resistance to compression. IEEE Trans Image Process 13(2):126-144
Kundur D, Hatzinakos D (2004) Towards robust logo watermarking using multiresolution image fusion. IEEE Trans Multimedia 6(2):185-198
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hien, T.D., Nakao, Z. & Chen, YW. Robust RDWT-ICA based information hiding. Soft Comput 10, 1135–1144 (2006). https://doi.org/10.1007/s00500-005-0036-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-005-0036-4