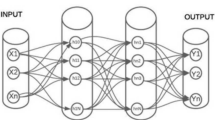
Abstract
Network intrusion detection systems (NIDSs) are pattern recognition problems that classify network traffic patterns as either ‘normal’ or ‘abnormal’. Precisely, the main aim of intrusion detection is to identify unauthorized use, misuse, and abuse of computers by detecting malicious network activities such as port scans, denial of service or other attempts to crack computer network environments. Even though the incorporation of conventional Soft Computing techniques in NIDSs has yielded to good solutions, the strong dynamism characterizing network intrusion patterns tend to invalidate the usability of existing framework. To tackle this issue, our proposal performs an adaptive supervised learning on a collection of time series that characterizes the network behavior to create a so-called timed automata-based fuzzy controller (TAFC), i.e. an evolvable fuzzy controller whose dynamic features allow to design an advanced network intrusion detection system able to directly deal with computer network dynamism and support networks’ administrators to prevent eventual damages coming from unauthorized network intrusion. As will be shown in experiments, where our approach has been compared with a conventional Mamdani fuzzy controller, the proposed system reduces the detection error and, as consequence, improves the computer network robustness.






Similar content being viewed by others
References
Acampora G, Loia V (2005) Fuzzy control interoperability and scalability for adaptive domotic framework. IEEE Trans Ind Inf 1(2):97–111
Acampora G, Loia V (2008) An open integrated environment for transparent fuzzy agents design. Open Source Development, Communities and Quality, IFIP International Federation for Information Processing, vol 275/2008. Springer, Boston, pp 1571–5736
Alur R (1994) A theory of timed automata. Theor Comput Sci 126:183–235
Anderson JP (1980) Computer security threat monitoring and surveillance. Technical report, James P Anderson Co., Fort Washington, Pennsylvania
Anderson D, Frivold T, Valdes A (1995) Next-generation intrusion-detection expert system (NIDES). Technical report, Computer Science Laboratory, SRI International, Menlo Park
Bace RG (2000) Intrusion detection. Macmillan Technical Publishing, Indianapolis
Barbara D, Couto J, Jajodia S, Popyack L, Wu N (2001) ADAM: detecting intrusions by data mining. In: Proceedings of the 2001 IEEE, workshop on information assurance and security, United States Military Academy, West Point
Biswanath M, Todd LH, Karl NL (1994) Network intrusion detection. IEEE Netw 8(3):26–41
Bolzoni D, Etalle S (2008) Approaches in anomaly-based network intrusion Detection systems. In: Intrusion detection systems. Advances in Information Security, vol 38. Springer, London, pp 1–15
Botha M, Solms R (2003) Utilising fuzzy logic and trend analysis for effective intrusion detection. Comput Secur 22:423–434
Bulatovic D, Velasevic D (1999) A distributed intrusion detection system based on bayesian alarm networks. Lect Notes Comput Sci 1740:219–228
Byuhghae-Cha KP, Jaiyttyun S (2005) Neural networks techniques for host anomaly intrusion detection using fixed pattern transformation. In: ICCSA 2005, LNCS, vol 3481, pp 254–263
Chandola V, Banerjee A, Kumar V (2009) Anomaly detection: a survey. ACM Comput Surv 41(3)
Debar H, Dacier M, Wespi A (1999) Towards a taxonomy of intrusion-detection systems. Comput Netw 31(8):805–822
Dickerson JE, Dickerson JA (2000) Fuzzy network profiling for intrusion detection. In: Proceedings of NAFIPS 19th international conference of the North American fuzzy information processing society, Atlanta, pp 301–306
Dickerson JE, Juslin J, Koukousoula O, Dickerson JA (2001) Fuzzy intrusion detection. In: IFSA world congress and 20th NAFIPS international conference, vol 9. No 3, pp 1506–1510
Gupta MM, Tsukamoto Y (1980) Fuzzy logic controllers—a perspective. In: Proceedings of the joint automatic control Conference, San Francisco, pp FA10-C
Hong TP, Lee CY (1996) Induction of fuzzy rules and membership functions from training examples. Fuzzy Sets Syst 84:33–47
Hu PZ, Heywood MI (2003) Predicting intrusions with local linear model. In: Proceedings of the international joint conference on neural networks, vol 3, pp 1780–1785
Javitz HS, Valdes A, Denning DE, Neumann PG, (1986) Analytical techniques development for a statistical intrusion-detection system (SIDS) based on accounting records. Technical report, SRI International, Menlo Park
Kayacik HG, Zincir-Heywood AN, Heywood MI (2003) On the capability of an som based intrusion detection system. In: Proceedings of the international joint conference on neural networks, vol 3, pp 1808–1813
Lee CC (1990) Fuzzy logic in control system: fuzzy logic controller—Part I and Part II. IEEE Trans SMC 20:404–435
Lee W, Salvatore J. Stolfo, Mok KW (1998) Mining audit data to build intrusion detection models. In: Proceedings of the fourth international conference on knowledge discovery and data mining (KDD 98), New York
Lee W, Stolfo SJ (1998) Data mining approaches for intrusion detection. In: Proceedings of the 7th USENIX Security Symposium, San Antonio
Lei JZ, Ghorbani A (2004) Network intrusion detection using an improved competitive learning neural network. In: Proceedings of the second annual conference on communication networks and services research (CNSR04), pp 190–197
Lippmann R, Fried D, Graf I, Haines J, Kendall K, McClung D, Weber D, Webster S, Wyschogrod D, Cunningham R, Zissman M (1998) Evaluating intrusion detection systems: 1998 DARPA off-line intrusion detection evaluation. In: Proceedings of IEEE symposium on security and privacy, Oakland
Mamdani EH (1974) Applications of fuzzy algorithms for simple dynamic plants. Proc IEE 121:1585–1588
Mohajerani M, Moeini A, Kianie M (2003) NFIDS: a neuro-fuzzy intrusion detection system. In: Proceedings of the 10th IEEE international conference on electronics, circuits and systems, pp 348–351
Mukkamala S , Sung AH, Abraham A (2003) Intrusion detection using ensemble of soft computing paradigms. In: The third international conference on intelligent systems design and applications, intelligent systems design and applications, advances in soft computing. Springer, Germany, pp 239–248
Mukkamala S, Sung AH, Abraham A (2004) Modeling intrusion detection systems using linear genetic programming approach. In: The 17th international conference on industrial & engineering applications of artificial intelligence and expert systems, innovations in applied artificial intelligence. In: Robert O.,Chunsheng Y., Moonis A., editors. Lecture Notes in Computer Science, vol 3029. Springer, Germany, pp 633–642
Mukherjee B, Herberlein LT, Levitt KN (1994) Network intrusion detection. IEEE Netw 8
Peddabachigari S, Abraham A, Grosan C, Thomas J (2007) Modeling intrusion detection system using hybrid intelligent systems. J Netw Comput Appl 30:114–132
Scarfone K, Mell P (2007) Guide to intrusion detection and prevention systems (IDPS), National Institute of Standards and Technology Special Publication 800-94, 127
Shah K, Dave N, Chavan S, Mukherjee S, Abraham A, Sanyal S (2004) Adaptive neuro-fuzzy intrusion detection system. In: IEEE international conference on information technology: coding and computing (ITCC04), vol 1. IEEE Computer Society, USA, pp 70–74
Smaha SE (1988) Haystack: an intrusion detection system. In: Fourth aerospace computer security applications conference, Tracor Applied Science Inc., Austin, pp 37–44
Takagi T, Sugeno M (1985) Fuzzy identification of systems and its applications to modeling and control. IEEE Trans Syst Man Cybern 15(1):116–132
Vokorokos L, Balaz A, Chovanec M (2006) Intrusion detection system using self organizing map. Acta Electrotechnica et Informatica 6(1):6
Wang WD, Bridges S (2000) Genetic algorithm optimization of membership functions for mining fuzzy association rules. In: Proceedings of the 7th international conference on fuzzy theory & technology, Atlantic City, pp 131–134
Wang Y, Chen H, Liu W (1996) A parallel algorithm for constructing a labeled tree. IEEE Trans Parallel and Distrib Syst 8:1236–1240
Wang K, Stolfo SJ (2004) Anomalous payload-based network intrusion detection. In: Jonsson E, Valdes A, Almgren M (eds) RAID 04: Proceedings of the 7th symposium on recent advances in intrusion detection. LNCS, vol 3224. Springer, Berlin, pp 203–222
Zadeh LA (1965) Fuzzy sets. Inf Control 8:338–353
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Acampora, G. Exploiting timed automata based fuzzy controllers for designing adaptive intrusion detection systems. Soft Comput 16, 1183–1196 (2012). https://doi.org/10.1007/s00500-011-0791-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-011-0791-3