Abstract
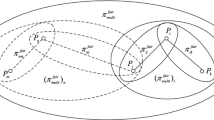
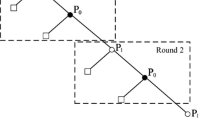
Secure multi-party computing (SMPC) is often used to solve security problems in cloud computing. Rational SMPC is a kind of SMPC in the presence of rational parties, who wish to maximize their utilities. Previous works about rational SMPC only studied the security properties under complete information scenario, where parties’ types are common knowledge. However, parties in practical applications have private types, which is unknown to others. This scenario is called incomplete information. In this paper, rational parties are allowed to have private types, which affect their utilities. Previously, rational parties obtain expected utilities due to unknown private types under incomplete information scenario. However, rational parties prefer to obtain pure utilities in actual life. To solve this contradiction, we use fuzzy theory to confirm the private type of his opponent; then they execute the protocol as if they know the private types just like the execution under complete information scenario. Consequently, they obtain pure utilities other than expected utility. In addition, our protocol can reduce round complexity than previous ones. Consequently, it will improve the security level and efficiency of cloud computing.




Similar content being viewed by others
References
Abraham I, Dolev D, Gonen R, Halpern J (2006) Distributed computing meets game theory: robust mechanisms for rational secret sharing and multiparty computation. In: Proceedings of the 25th annual ACM symposium on Principles of distributed computing, ACM, pp 53–62
Asharov G, Canetti R, Hazay C (2011) Towards a game theoretic view of secure computation. In: Advances in Cryptology–EUROCRYPT 2011, Springer, pp 426–445
Cai Y, Leung H (2008) A formal model of fuzzy ontology with property hierarchy and object membership. In: Conceptual Modeling-ER 2008, Springer, pp 69–82
Castiglione A, Cattaneo G, Cembalo M, Petrillo UF (2013) Experimentations with source camera identification and online social networks. J Ambient Intell Humaniz Comput 4(2):265–274
Castiglione A, Pizzolante R, De Santis A, Carpentieri B, Castiglione A, Palmieri F (2015) Cloud-based adaptive compression and secure management services for 3d healthcare data. Future Gener Comput Sys 43:120–134
Chen X, Wu Q, Zhang F, Tian H, Wei B, Lee B, Lee H, Kim K (2011) New receipt-free voting scheme using double-trapdoor commitment. Inf Sci 181(8):1493–1502
Chen X, Li J, Ma J, Tang Q, Lou W (2012a) New algorithms for secure outsourcing of modular exponentiations. In: Computer Security–ESORICS 2012, Springer, pp 541–556
Chen X, Li J, Susilo W (2012b) Efficient fair conditional payments for outsourcing computations. Inf Forens Secur IEEE Trans 7(6):1687–1694
Doctor F, Iqbal R, Naguib RNG (2014) A fuzzy ambient intelligent agents approach for monitoring disease progression of dementia patients. J Ambient Intell Humaniz Comput 5(1):147–158
Esposito C, Ficco M, Palmieri F, Castiglione A (2015) Smart cloud storage service selection based on fuzzy logic theory of evidence and game theory. IEEE Trans Comput. doi:10.1109/TC.2015.2389952
Fatos X, Wang J, Chen X, Liu JK, Li J, Krause P (2014) An efficient phr service system supporting fuzzy keyword search and fine-grained access control. Soft Comput 18(9):1795–1802
Garay J, Katz J, Maurer U, Tackmann B, Zikas V (2013) Rational protocol design: cryptography against incentive-driven adversaries. In: Foundations of Computer Science (FOCS), 2013 IEEE 54th Annual Symposium on, IEEE, pp 648–657
Groce A, Katz J (2012) Fair computation with rational players. In: EUROCRYPT 2012, pages 81–98. Springer
Halpern J, Pass R (2010) Game theory with costly computation: formulation and application to protocol security. In: ICS 2010, Tsinghua University Press, pp 120–142
Halpern J, Teague V (2004) Rational secret sharing and multiparty computation: extended abstract. In: STOC ’04: Proceedings of the thirty-sixth annual ACM symposium on Theory of computing, New York, ACM, pp 623–632
Javanmardi S, Shojafar M, Shariatmadari S, Ahrabi SS (2015) Fr trust: a fuzzy reputation-based model for trust management in semantic p2p grids. Int J Grid Util Comput 6(1):57–66
Li J, Wang Q, Wang C, Cao N, Ren K, Lou W (2010) Fuzzy keyword search over encrypted data in cloud computing. In: INFOCOM, 2010 Proceedings IEEE, pp 1–5
Li J, Huang X, Li J, Chen X, Xiang Y (2014) Securely outsourcing attribute-based encryption with checkability. Parallel Distrib Sys IEEE Trans 25(8):2201–2210
Lysyanskaya A, Triandopoulos N (2006) Rationality and adversarial behavior in multi-party computation. In: Dwork C (ed) CRYPTO 2006. Springer, Heidelberg, pp 180–197
De Mantaras RL, Godo L, Plaza E, Sierra C (2015) A survey of contributions to fuzzy logic and its applications to artificial intelligence at the iiia. In: Enric Trillas: A Passion for Fuzzy Sets, Springer, pp 67–78
Osborne MJ, Rubinstein A (2004) A course in game theory. MIT Press, Cambridge
Stavrakoudis DG, Theocharis JB, Zalidis GC (2011) A multistage genetic fuzzy classifier for land cover classification from satellite imagery. Soft Comput 15(12):2355–2374
Straccia U (2005) Towards a fuzzy description logic for the semantic web (preliminary report). In: The Semantic Web: Research and Applications, Springer, pp 167–181
Vaccaro A, Zobaa AF (2011) Cooperative fuzzy controllers for autonomous voltage regulation in smart grids. J Ambient Intell Humaniz Comput 2(1):1–10
Vychodil V, Kuhr T (2015) Fuzzy logic programming reduced to reasoning with attribute implications. Fuzzy Sets and Systems 262:1–20
Wang Y, Liu Z, Xu Q (2014) New rational parties relying on reputation. Secur Commun Netw 7(7):1128–1137
Wang Y, Wong DS, Zhao C, Xu Q (2015a) Fair two-party computation with rational parties holding private types. Secu Commun Netw 8(2):284–297
Wang Y, Wong DS, Zhao C, Xu Q (2015b) Fair two-party computation with rational parties holding private types. Secur Commun Netw 8(2):284–297
Wang Y, Zhao C, Xu Q, Zheng Z, Chen Z, Liu Z (2015c) Fair secure computation with reputation assumptions in the mobile social networks. Mobile Information Systems 2015
Xu B, Peng Z, Xiao F, Gates AM, Yu J (2014) Dynamic deployment of virtual machines in cloud computing using multi-objective optimization. Soft Comput, pp 1–9
Yao AC (1982) Protocols for secure computation. In: 23rd Annual Symposium on Foundations of Computer Science (FOCS), IEEE pp 160–164
Yao AC (1986) How to generate and exchange secrets. In: 27th Annual Symposium on Foundations of Computer Science (FOCS), IEEE, pp 162–167
Yeung CA, Leung H. (2006) Ontology with likeliness and typicality of objects in concepts. In: Conceptual Modeling-ER 2006, Springer, pp 98–111
Zimmermann HJ (2001) Fuzzy set theory-and its applications. Springer Science & Business Media
Acknowledgments
This work is partially supported by National Natural Science Foundation of China (No. 61170161, 61202475), Guangzhou Zhujiang Science and Technology Future Fellow Fund (No. 2012J2200094), Distinguished Young Scholars Fund of Department of Education, Guangdong Province(No. Yq2013126), Outstanding Young Scientists Foundation Grant of Shandong Province (No. BS2014DX016), Nature Science Foundation of Shandong Pro- vince (No. ZR2012FQ029), Ph.D. Programs Foundation of Ludong University (No. LY2014033, LY2015033), Fujian Provincial Key Laboratory of Network Security and Cryptology Research Fund (Fujian Normal University) (No. 15004).
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by A. Di Nola.
Rights and permissions
About this article
Cite this article
Wang, Y., Li, T., Chen, L. et al. Rational computing protocol based on fuzzy theory. Soft Comput 20, 429–438 (2016). https://doi.org/10.1007/s00500-015-1773-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-015-1773-7