Abstract
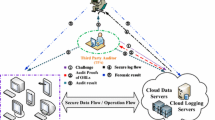
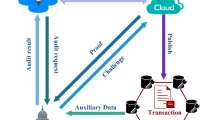
In this paper, we focus on auditing for users’ operation behaviors, which is significant for the avoidance of potential crimes in the cloud and equitable accountability determination in the forensic. We first present a public model for operation behaviors in cloud storage, in which a trusted third party is introduced to verify the integrity of operation behavior logs to enhance the credibility of forensic results as well as alleviate the burden of the forensic investigator. Further, we design a block-based logging approach to support selective verification and a hash-chain-based structure for each log block to ensure the forward security and append-only properties for log entries. Moreover, to achieve the tamper resistance of log blocks and non-repudiation of auditing proofs, we employ Merkle hash tree (MHT) to record the hash values of the aggregation authentication block tags sequentially and publish the root of MHT to the public once a block has been appended. Meanwhile, using the authentication property of MHT, our scheme can provide log-less verification with privacy preservation. We formally prove the security of the proposed scheme and evaluate its performance on entry appending and verification by concrete experiments and comparisons with the state-of-the-art schemes. The results demonstrate that the proposed scheme can effectively achieve secure auditing for log files of operation behaviors in cloud storage and outperforms the previous ones in computation complexity and communication overhead.










Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Abdalla M, Reyzin L (2000) A new forward-secure digital signature scheme. In: Proceedings of cryptology ASIACRYPT 2000. Springer, Berlin, pp 116–129
Accorsi R (2009) Safe-keeping digital evidence with secure logging protocols: State of the art and challenges. In: Proceedings of the 5th IEEE international conference on IT security incident management and IT forensic, pp 94–110
Ateniese G, Burns R, Curtmola R, Herring J, Kissner L, Peterson Z, Song D (2007) Provable data possession at untrusted stores. In: Proceedings of the 14th ACM conference on Computer and communications security, pp 598–609
Bellare M, Miner SK (1999) A forward-secure digital signature scheme. In: Proceedings of cryptology—CRYPTO’99. Springer, Berlin, pp 431–448
Bellare M, Yee B (1997) Forward integrity for secure audit logs. Computer Science and Engineering Department Technical Report
Birk D, Wegener C (2011) Technical issues of forensic investigations in cloud computing environments. In: Proceedings of the 6th IEEE international workshop on systematic approaches to digital forensic engineering, pp 1–10
Chen L (2013) Using algebraic signatures to check data possession in cloud storage. Future Gener Comput Syst 29:1709–1715
Chen YR (2015) The growing pains of cloud storage. IEEE Internet Comput 19(1):4–7
Chen CM, Chen CY, Chao HC (2015) Proof of ownership in deduplicated cloud storage with mobile device efficiency. IEEE Netw 29(2):51–55
Corey V, Peterman C, Shearin S, Greenberg MS, Bokkele JV (2012) Network forensics analysis. IEEE Internet Comput 6(6):60–66
Crosby SA, Wallach DS (2009) Efficient data structures for tamper-evident logging. In: Proceedings of the USENIX security symposium, pp 317–334
Dewan H, Hansdah RC (2011) A survey of cloud storage facilities. In: Proceedings of the 7th IEEE world congress on services, pp 224–231
Dixon PD (2005) An overview of computer forensics. IEEE Potentials 24(5):7–10
Erway CC, Küpçü A, Papamanthou C, Tamassia R (2009) Dynamic provable data possession. In: Proceedings of the 16th ACM conference on computer and communications security, pp 213–222
Halevi S, Harnik D, Pinkas B, Peleg AS (2011) Proofs of ownership in remote storage systems. In: Proceedings of the 18th ACM conference on computer and communications security, pp 491–500
Holt JE (2006) Logcrypt: forward security and public verification for secure audit logs. In: Proceedings of the 4th Australasian workshops on grid computing and E-research, pp 203–211
Juels A, Kaliski BS (2007) PoRs: proofs of retrievability for large files. In: Proceedings of the 14th ACM conference on computer and communications security, pp 584–597
Lan Z, Varadharajan V, Hitchens M (2015) Trust enhanced cryptographic role-based access control for secure cloud data storage. IEEE Trans Inf Forensics Secur 10(11):2381–2395
Li X, Li J, Huang F (2016) A secure cloud storage system supporting privacy-preserving fuzzy deduplication. Soft Comput 20(4):1437–1448
Liu J, Huang K, Rong H, Wang H, Xian M (2015) Privacy-preserving public auditing for regenerating-code-based cloud storage. IEEE Trans Inf Forensics Secur 10(7):1513–1528
Ma D, Tsudik G (2009) A new approach to secure logging. ACM Trans Storage 5(1):1–21
Martini B, Choo KKR (2012) An integrated conceptual digital forensic framework for cloud computing. Digit Investig 9(2):71–80
Mao J, Zhang Y, Li P, Li T, Wu Q, Liu J (2015) A position-aware Merkle tree for dynamic cloud data integrity verification. Soft Comput. doi:10.1007/s00500-015-1918-8
Merkle RC (1989) A certified digital signature. In: Proceedings of the 9th annual international cryptology conference, pp 218–238
Mell P, Grance T (2009) The NIST definition of cloud computing. National Institute of Standards and Technology Technique Report
Pritzker P, Gallagher PD (2014) SHA-3 standard: permutation-based hash and extendable-output functions. National Institute of Standards and Technology, pp 1–35
Ren K, Wang C, Wang Q (2012) Security challenges for the public cloud. IEEE Internet Comput 16(1):69–73
Rogaway P, Shrimpton T (2004) Cryptographic hash-function basics: definitions, implications, and separations for preimage resistance, second-preimage resistance, and collision resistance. In: Proceedings of the 11th international workshop on fast software encryption, pp 371–388
Ryoo J, Rizvi S, Aiken W, Kissell J (2014) Cloud security auditing: challenges and emerging approaches. IEEE Secur Priv 12(6):68–74
Schneier B, Kelsey J (1999) Secure audit logs to support computer forensics. ACM Trans Inf Syst Secur 2(2):159–176
Shacham H, Waters B (2008) Compact proofs of retrievability. In: Advances in cryptology, ASIACRYPT’08. Springer, Berlin, pp 90–107
Shi E, Stefanov E, Papamanthou C (2013) Practical dynamic proofs of retrievability. In: Proceedings of the 2013 ACM SIGSAC conference on computer and communications security, pp 325–336, 2013
Sookhak M, Gani A, Talebain H, Akhunzada A, Khan S, Buyya R, Zomaya A (2015) Remote data auditing in cloud computing environments: a survey, taxonomy, and open issues. ACM Comput Surv 47(4):65
Sookhak M, Talebain H, Ahmed E, Gani A, Khan MK (2014) A review on remote data auditing in single cloud server: taxonomy and open issues. J Netw Comput Appl 43(5):121–141
Stathopoulos V, Kotzanikolaou P, Magkos E (2006) A framework for secure and verifiable logging in public communication networks. In: Proceedings of 1st international workshop on critical information infrastructures security, pp 273–284
Stinson DR (2006) Some observations on the theory of cryptographic hash functions. Des Codes Cryptogr 38(2):259–277
Szydlo M (2004) Merkle tree traversal in log space and time. In: Proceedings of the 14th international conference on the theory and applications of cryptographic techniques, pp 541–554
Thorpe S, Grandison T, Campbell A, Williams J, Burrell K, Ray I (2013) Towards a forensic-based service oriented architecture framework for auditing of cloud logs. In: Proceedings of the 9th IEEE world congress on services, pp 75–83
Tian H, Chen Y, Chang CC, Jiang H, Huang Y, Chen YH, Liu J (2015) Dynamic-hash- table based public auditing for secure cloud storage. IEEE Trans Serv Comput. doi:10.1109/TSC.2015.2512589
Wang X, Yin Y L, Yu H (2005) Finding collisions in the full SHA-1. In: Proceedings of Cryptology—CRYPTO 2005. Springer, Berlin, pp 17-36
Wang C, Ren K, Lou W, Li J (2010a) Toward publicly auditable secure cloud data storage services. IEEE Netw 24(4):9–24
Wang G, Liu Q, Wu J (2010b) A hierarchical attribute-based encryption for fine-grained access control in cloud storage services. In: Proceedings of the 17th ACM conference on computer and communications security, pp 735–737
Wang Q, Wang C, Ren K, Lou W, Li J (2011) Enabling public auditability and data dynamics for storage security in cloud computing. IEEE Trans Parallel Distrib Syst 22(5):847–859
Wang C, Chow SM, Wang Q, Ren K, Lou W (2013) Privacy-preserving public auditing for secure cloud storage. IEEE Trans Comput 62(2):362–375
Wang B, Li B, Li H (2015) Panda: public auditing for shared data with efficient user revocation in the cloud. IEEE Trans Serv Comput 8(1):92–106
Xu J, Chang E C (2012) Towards efficient proofs of retrievability. In: Proceedings of the 7th ACM symposium on information, computer and communications security, pp 79–80
Yang K, Jia X (2012) Data storage auditing service in cloud computing: challenges, methods and opportunities. World Wide Web 15(4):409–428
Yang K, Jia X (2013) An efficient and secure dynamic auditing protocol for data storage in cloud computing. IEEE Trans Parallel Distrib Syst 24(9):1717–1726
Yang K, Jia X, Ren K, Zhang B, Xie R (2013) DAC-MACS: effective data access control for multi-authority cloud storage systems. IEEE Trans Inf Forensics Secur 8(11):1790–1801
Yavuz AA, Ning P, Reiter MK (2012) Efficient, compromise resilient and append-only cryptographic schemes for secure audit logging. In: Proceedings of the 16th international conference on financial cryptography and data security, pp 148–163
Yuan J, Yu S (2013) Proofs of retrievability with public verifiability and constant communication cost in cloud. In: Proceedings of the 1st ACM international workshop on security in cloud computing, pp 19–26
Yu Y, Zhang Y, Ni J, Au MH, Chen L, Liu H (2015) Remote data possession checking with enhanced security for cloud storage. Future Gener Comput Syst 52:77–85
Zawoad S, Dutta AK, Hasan R (2013) SecLaaS: secure logging-as-a-service for cloud forensics. In: Proceedings of the 8th ACM SIGSAC symposium on information, computer and communications security, pp 219–230
Zawoad S, Dutta AK, Hasan R (2016) Towards building forensics enabled cloud through secure logging-as-a-service. IEEE Trans Dependable Secure Comput 13(2):148–162
Zawoad S, Hasan R, Skjellum A (2015) OCF: an open cloud forensics model for reliable digital forensics. In: Proceedings of the 8th IEEE international conference on cloud computing, pp 437–444
Zheng Q, Xu S (2012) Secure and efficient proof of storage with deduplication. In: Proceedings of 2nd ACM conference on data and application security and privacy, pp 1–12
Acknowledgments
This work was supported in part by Natural Science Foundation of China under Grant Nos. U1405254, U1536115 and 61302094, Program of China Scholarships Council under Grant No. 201507540001, Natural Science Foundation of Fujian Province of China under Grant No. 2014J01238, Program for New Century Excellent Talents in Fujian Province University under Grant No. MJK2016-23, Program for Outstanding Young Teachers in Higher Education Institutions of Fujian Province of China under Grant No. MJK2015-54, Education and Science Research Program for Young and Middle-aged Teachers of Fujian Province of China under Grant No. JA13012, Promotion Program for Young and Middle-aged Teacher in Science & Technology Research of Huaqiao University under Grant No. ZQN-PY115, and Program for Science & Technology Innovation Teams and Leading Talents of Huaqiao University under Grant No. 2014KJTD13.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Communicated by V. Loia.
Rights and permissions
About this article
Cite this article
Tian, H., Chen, Z., Chang, CC. et al. Enabling public auditability for operation behaviors in cloud storage. Soft Comput 21, 2175–2187 (2017). https://doi.org/10.1007/s00500-016-2311-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-016-2311-y