Abstract
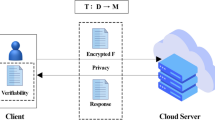
In this paper, we explore the verification problem of outsourcing constrained nonlinear programming (NLP) when it is required to be solved by particle swarm optimization (PSO) algorithm, i.e., making sure that the cloud runs PSO algorithm faithfully and returns an acceptable solution. An efficient verification scheme without any cryptographic tool is proposed. The proposed scheme involves approximate KKT conditions with the \(\varepsilon \)-KKT point in verifying the optimality of the result returned by PSO algorithm. Extensive experiments on PSO benchmarks and NLP test problems demonstrate that our proposed scheme is effective and efficient at verifying the cloud’s honesty.


Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Abdullah MN, Bakar AHA, Rahim NA, Jamian JJ, Aman MM (2012) Economic dispatch with valve point effect using iteration particle swarm optimization. In: Proceedings of International Universities Power Engineering Conference (UPEC), pp 1–6, London, UK
Andreani R, Haeser G, Martínez JM (2011) On sequential optimality conditions for smooth constrained optimization. Optimization 60(5):627–641
Angeline PJ (1998) Evolutionary optimization versus particle swarm optimization: philosophy and performance differences. In: Proceedings of international conference on evolutionary programming (EP), pp 601–610, London, UK
Ardagna CA, Asal R, Damiani E, Quang Hieu V (2015) From security to assurance in the cloud: a survey. ACM Comput Surv 48(1):2
Arora S, Safra S (1998) Probabilistic checking of proofs: a new characterization of np. J ACM 45(1):70–122
Atallah MJ, Frikken KB (2010) Securely outsourcing linear algebra computations. In: Proceedings of ACM symposium on information, computer and communications security (ASIACCS), pp 48–59, New York, NY, USA
Chen F, Xiang T, Yang Y, Wang C, Zhang S (2015) Secure cloud storage hits distributed string equality checking: more efficient, conceptually simpler, and provably secure. In: Proceedings of IEEE international conference on computer communications (INFOCOM), pp 2389–2397, Hong Kong, China
Chen F, Xiang T, Yang Y, Chow SSM (2016) Secure cloud storage meets with secure network coding. IEEE Trans Comput 65(6):1936–1948
Corazza M, Fasano G, Gusso R (2013) Particle swarm optimization with non-smooth penalty reformulation, for a complex portfolio selection problem. Appl Math Comput 224:611–624
Cormode G, Mitzenmacher M, Thaler J (2012) Practical verified computation with streaming interactive proofs. In: Proceedings of innovations in theoretical computer science conference (ITCS), pp 90–112, New York, NY, USA
Du W, Jia J, Mangal M, Murugesan M (2004) Uncheatable grid computing. In: Proceedings of international conference on distributed computing systems (ICDCS), pp 4–11
Dutta J, Deb K, Tulshyan R, Arora R (2013) Approximate KKT points and a proximity measure for termination. J Glob Optim 56(4):1463–1499
Eberhart RC, Kennedy J (1995) A new optimizer using particle swarm theory. In: Proceedings of international symposium on micro machine and human science (MHS’95), pp 39–43, Nagoya, Japan
Eberhart RC, Shi Y (1998) Comparison between genetic algorithms and particle swarm optimization. In: Proceedings of international conference on evolutionary programming (EP), pp 611–616, London, UK
Ganesan T, Vasant P, Elamvazuthy I (2012) A hybrid PSO approach for solving non-convex optimization problems. Arch Control Sci 22(1):87–105
Gennaro R, Gentry C, Parno B (2010) Non-interactive verifiable computing: outsourcing computation to untrusted workers. In: Proceedings of annual conference on advances in cryptology (CRYPTO), pp 465–482, Santa Barbara, CA, USA
Gennaro R, Gentry C, Parno B, Raykova M (2013) Quadratic span programs and succinct NIZKs without PCPs. In: Proceedings of international conference on the theory and applications of cryptographic techniques (EUROCRYPT), pp 626–645, Athens, Greece
Goldwasser S, Kalai YT, Rothblum GN (2015) Delegating computation: interactive proofs for muggles. J ACM 62(4):27
Golle P, Mironov I (2001) Uncheatable distributed computations. In: Proceedings of Cryptographers Track at the RSA Conference (CT-RSA), pp 425–440, San Francisco, CA, USA
Kennedy J, Eberhart RC (1995) Particle swarm optimization. In: Proceedings of IEEE international conference on neural networks, pp 1942–1948, Perth, Australia
Liang JJ, Runarsson TP, Mezura-Montes E, Clerc M, Suganthan PN, Coello Coello CA, Deb K (2006) Problem definitions and evaluation criteria for the CEC 2006 special session on constrained real-parameter optimization. Technical report
Luenberger DG, Ye Y (2008) Linear and nonlinear programming, 3rd edn. Springer, Berlin
Manoharan PS, Kannan PS, Baskar S, Iruthayarajan MW (2008) Penalty parameter-less constraint handling scheme based evolutionary algorithm solutions to economic dispatch. IET Gener Transm Distrib 2(4):478–490
Micali S (2000) Computationally sound proofs. SIAM J Comput 30(4):1253–1298
Niu D, Wei Y (2013) A novel social-environmental-economic dispatch model for thermal/wind power generation and application. Int J Innov Comput Inf Control 9(7):3005–3014
Ogiela MR, Ogiela U (2008) Linguistic approach to cryptographic data sharing. In: Proceedings of IEEE international conference on future generation communication and networking (FGCN’08), vol 1, pp 377–380, Hainan Island, China
Ogiela MR, Ogiela U, Ogiela L (2012) Secure information sharing using personal biometric characteristics. In: Proceedings of international mega-conference on future generation information technology (FGIT), pp 369–373, Kangwondo, Korea
Omran M, Engelbrecht AP, Salman A (2005) Particle swarm optimization method for image clustering. Int J Pattern Recognit Artif Intell 19(3):297–321
Parno B, Raykova M, Vaikuntanathan V (2012) How to delegate and verify in public: verifiable computation from attribute-based encryption. In: Proceedings of theory of cryptography conference (TCC), pp 422–439, Taormina, Sicily, Italy
Parno B, Howell J, Gentry C, Raykova M (2013) Pinocchio: nearly practical verifiable computation. In: Proceedings of IEEE symposium on security and privacy (S&P), pp 238–252, Berkeley, CA, USA
Parsopoulos KE, Vrahatis MN (2002) Particle swarm optimization method for constrained optimization problems. Intell Technol Theory Appl New Trends Intell Technol 76(1):214–220
Setty S, McPherson R, Blumberg AJ, Walfish M (2012) Making argument systems for outsourced computation practical (sometimes). In: Proceedings of network and distributed system security symposium (NDSS), San Diego, CA, USA
Setty STV (2014) Toward practical argument systems for verifiable computation. Ph.D. thesis, University of Texas
Shi Y, Eberhart R (1998) A modified particle swarm optimizer. In: Proceedings of IEEE international conference on evolutionary computation (CEC), pp 69–73, Anchorage, USA
Szajda D, Lawson B, Owen J (2003) Hardening functions for large scale distributed computations. In: Proceedings of IEEE symposium on security and privacy (S&P), pp 216–224
Takabi H, Joshi JBD, Ahn G-J (2010) Security and privacy challenges in cloud computing environments. IEEE Secur Priv 8(6):24–31
Tulshyan R, Arora R, Deb K, Dutta J (2010) Investigating EA solutions for approximate KKT conditions in smooth problems. In: Proceedings of annual conference on genetic and evolutionary computation, pp 689–696, New York, NY, USA
Walfish M, Blumberg AJ (2015) Verifying computations without reexecuting them. Commun ACM 58(2):74–84
Wang C, Ren K, Wang J (2011) Secure and practical outsourcing of linear programming in cloud computing. In: Proceedings of IEEE international conference on computer communications (INFOCOM), pp 820–828, Shanghai, China
Xiang T, Zhang W, Chen F (2014) A verifiable PSO algorithm in cloud computing. In: Proceedings of IEEE congress on evolutionary computation (CEC), pp 190–193, Beijing, China
Xiao Z, Xiao Y (2013) Security and privacy in cloud computing. IEEE Commun Surv Tutor 15(2):843–859
Zhen X, Wang C, Ren K, Wang L, Zhang B (2014) Proof-carrying cloud computation: the case of convex optimization. IEEE Trans Inf Forensics Secur 9(11):1790–1803
Zhou L, Li C (2015) Outsourcing large-scale quadratic programming to a public cloud. IEEE Access 3:2581–2589
Acknowledgements
This work was supported by the National Natural Science Foundation of China (No. 61672118) and the Fundamental Research Funds for the Central Universities (No. 106112016CDJZR185513).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Communicated by V. Loia.
Rights and permissions
About this article
Cite this article
Xiang, T., Zhang, W., Zhong, S. et al. Verifiable outsourcing of constrained nonlinear programming by particle swarm optimization in cloud. Soft Comput 22, 3343–3355 (2018). https://doi.org/10.1007/s00500-017-2569-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-017-2569-8