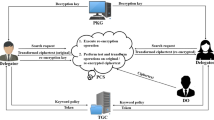
Abstract
Prior to outsourcing sensitive data, users need to encrypt the data and outsource the ciphertexts to cloud servers. Therefore, efficient search techniques on encrypted data are required. Attribute-based keyword search (ABKS) is a public key encryption with keyword search scheme where a legal user can authorize a proxy to test whether a ciphertext includes some exact keywords without exposing the content of sensitive data to the proxy. However, the main obstacle to implementing existing ABKS schemes is that the computation cost is very heavy, namely linear with the number of required attributes. In this paper, we propose a new ABKS scheme with following features: (1) It supports AND and NOT gates; (2) the size of the searchable ciphertexts is constant; (3) the size of the trapdoors generated by legal users for the proxy is constant; (4) to encrypt a message, the computation cost is constant; and (5) the computation cost of the test algorithm is constant. To the best of our knowledge, it is the first ABKS which has constant-size ciphertext and supports AND and NOT gates.





Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Notes
Notably, in this paper, we mainly consider how to encrypt keywords. To encrypt the files, standard public key encryption schemes can be adopted, such as AES encryption, RSA encryption, etc.
References
Armbrust M, Fox A, Griffith R, Joseph AD, Katz R, Konwinski A, Lee G, Patterson D, Rabkin A, Stoica I, Zaharia M (2010) A view of cloud computing. Commun ACM 53(4):50–58
Baek J, Safiavi-Naini R, Susilo W (2008) Public key encryption with keyword search revisited. In: Proceedings of ICCSA 2008, volume 5072 of lecture notes in computer science. Springer, pp 1249–1259
Bethencourt J, Sahai A, Waters B (2007) Ciphertext-policy attribute-based encryption. In: Proceedings of IEEE S & P 2007. IEEE, pp 321–334
Boneh D, Franklin MK (2003) Identity-based encryption from the weil pairing. SIAM J Comput 32(3):586–615
Boneh D, Boyen X, Goh EJ (2005) Hierarshical identity based encryption with constant size ciphertetx. In: Proceedings of Enrocrypt 2005, volume 3494 of lecture notes in computer science. Springer, pp 440–456
Boneh D, Di Crescenzo G, Ostrovsky R, Persiano G (2004) Public key encryption with key word search. In: Proceedings of EUROCRYPT 2004, volume 3027 of lecture notes in computer science. Spinger, pp 506–522
Byun JW, Rhee HS, Park HA, Lee DH (2006) Off-line keyword guessing attacks on recent keyword search schemes over encrypted data. In: Proceedings of VLDB SDM 2006, volume 4165 of lecture notes in computer science. Springer, pp 75–83
Chen C, Zhang Z, Feng D (2011) Efficient ciphertext policy attribute-based encryption with constant-size ciphertext and constant computation-cost. In: Proceedings of ProvSec 2011, volume 6980 of lecture notes in computer science. Springer, pp 84–101
Cheung L, Newport C (2007) Provably secure ciphertext policy abe. In: Proceedings CCS 2007. ACM, pp 456–465
Curtmola R, Garay JA, Kamara S, Ostrovsky R (2006) Searchable symmetric encryption: improved definitions and efficient constructions. In: Proceedings of CCS 2006. ACM
Delerablée C, Paillier P, Pointcheval D (2007) Fully collusion secure dynamic broadcast encryption with constant-size ciphertexts or decryption keys. In: Proceedings of Pairing 2007, volume 4575 of lecture notes in computer science. Springer, pp 39–59
Emura K, Miyaji A, Nomura A, Omote K, Soshi M (2009) A ciphertext-policy attribute-based encryption scheme with constant ciphertext length. In: Proceedings of ISPEC 2009, volume 5451 of lecture notes in computer science. Springer, pp 13–23
Fu Z, Ren K, Shu J, Sun X, Huang F (2016) Enabling personalized search over encrypted outsourced data with efficiency improvement. IEEE Trans Parallel Distrib Syst 27(9):2546–2559
Fu Z, Sun X, Liu Q, Zhou L, Shu J (2015) Achieving efficient cloud search services: multi-keyword ranked search over encrypted cloud data supporting parallel computing. IEICE Trans Commun E98–B(1):190–200
Fu Z, Wu X, Guan C, Sun K, Ren K (2016) Towards efficient multi-keyword fuzzy search over encrypted outsourced data with accuracy improvement. IEEE Trans Inf Forensics Secur. doi:10.1109/TIFS.2016.2596138
Goh EJ (2003) Secure indexes. IACR Cryptology ePrint Archive. http://eprint.iacr.org/2003/216
Golle P, Staddon J, Waters B (2004) Secure conjunctive keyword search over encrypted data. In: Proceedings of ACNS 2004, volume 3089 of lecture notes in computer science. Springer, pp. 31–45
Goyal V, Pandey O, Sahai A, Waters B (2006) Attribute based encryption for fine-grained access control of encrypted data. In: Proceedings of CCS 2006. ACM, pp 89–98
Han J, Susio W, Mu Y, Yan J (2012) Attribute-based oblivious access control. Comput J 55(10):1202–1205
Han F, Qin J, Zhao H, Hu J (2014) A general transformation from KP-ABE to searchable encryption. Future Gener Comput Syst 30:107–115
Han J, Susilo W, Mu Y, Zhou J, Au MHA (2015) Improving privacy and security in decentralized ciphertext-policy attribute-based encryption. IEEE Trans Inf Forensics Secur 10(3):665–678
Herranz J, Laguillaumie F, Ràfols C (2010) Constant size ciphertexts in threshold attribute-based encryption. In: Proceedings of PKC - 2010, volume 6056 of lecture notes in computer science. Springer, pp 19–34
Jeong IR, Kwon JO, Hong D, Lee DH (2009) Constructing PEKS schemes secure against keyword guessing attacks is possible ? Comput Commun 32(2):394–396
Kong Y, Zhang M, Ye D (2016) A belief propagation-based method for task allocation in open and dynamic cloud environments. Knowl Based Syst 115:123–132
Kurosawa K, Ohtaki Y (2012) Uc-secure searchable symmetric encryption. In: Proceedings of FC 2012, volume 7397 of lecture notes in computer science . Springer, pp 285–298
Li H, Liu D, Jia K, Lin X (2015) Achieving authorized and ranked multi-keyword search over encrypted cloud data. In: Proceedings of ICC 2015. IEEE, pp 7450–7455
Li J, Lin X, Zhang Y, Han J (2016) Ksf-oabe: Outsourced attribute-based encryption with keyword search function for cloud storage. IEEE Trans Serv Comput. doi:10.1109/TSC.2016.2542813
Li J, Li X, Wang L, He D, Ahmed H, Niu X (2017) Fuzzy encryption in cloud computation: efficient verifiable outsourced attribute-based encryption. Soft Comput. doi:10.1007/s00500-017-2482-1
Liang K, Susilo W (2015) Searchable attribute-based mechanism with efficient data sharing for secure cloud storage. IEEE Trans Inf Forensics Secur 10(9):1981–1992
Liu Q, Cai W, Shen J, Fu Z, Liu X, Linge N (2016) A speculative approach to spatial-temporal efficiency with multi-objective optimization in a heterogeneous cloud environment. Secur Commun Netw 9(17):4002–4012
Lynn B (2006) The pairing-based cryptography library. https://crypto.stanford.edu/pbc/
Ma S, Lai J, Deng RH, Ding X (2016) Adaptable key-policy attribute-based encryption with time interval. Soft Comput. doi:10.1007/s00500-016-2177-z
Park DJ, Kim K, Lee PJ (2004) Public key encryption with conjunctive field keyword search. In: Proceedings of WISA 2004, volume 3325 of lecture notes in computer science. Springer, pp 73–86
Rhee HS, Susilo W, Kim HJ (2009) Secure searchable public key encryption scheme against keyword guessing attacks. IEICE Electron Express 6(5):237–243
Sahai A, Waters B (2005) Fuzzy identity-based encryption. In: Proceedings of EUROCRYPT - 2005, volume 3494 of lecture notes in computer science. Springer, pp 457–473
Song DX, Wagner D, Perrig A (2000) Practical techniques for searches on encrypted data. In: Proceedings of IEEE - S&P 2000. IEEE, pp 44–55
Sun W, Yu S, Lou W, Hou YT, Li H (2014) Protecting your right: attribute-based keyword search with fine-grained owner-enforced search authorization in the cloud. In: Proceedings of INFOCOM 2014. IEEE, pp 226–234
Wang H, He D, Shen J, Zheng Z, Zhao C, Zhao M (2016) Verifiable outsourced ciphertext-policy attribute-based encryption in cloud computing. Soft Comput. doi:10.1007/s00500-016-2271-2
Waters B (2011) Ciphertext-policy attribute-based encryption: an expressive, efficient, and provably secure realization. In: Proceedings of PKC - 2011, volume 6571 of lecture notes in computer science. Springer, pp 53–70
Xia Z, Wang X, Sun X, Wang Q (2016) A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data. IEEE Trans Parallel Distrib Syst 27(2):340–352
Xu J, Wen Q, Li W, He D (2016) Succinct multi-authority attribute-based access control for circuits with authenticated outsourcing. Soft Comput. doi:10.1007/s00500-016-2244-5
Yang Y, Han J, Susilo W, Yuen TH, Li J (2016) Abks-csc: attribute-based keyword search with constant size ciphertexts. Secur Commun Netw 9(18):5003–5015
Zheng Q, Xu S, Ateniese G (2014) VABKS: verifiable attribute-based keyword search over outsourced encrypted data. In: Proceedings of INFOCOM 2014. IEEE, pp 522–530
Zhong H, Zhu W, Xu Y, Cui J (2016) Multi-authority attribute-based encryption access control scheme with policy hidden for cloud storage. Soft Comput. doi:10.1007/s00500-016-2330-8
Zhou Z, Huang D (2010) On efficient ciphertext-policy attribute based encryption and broadcast encryption. In: Proceedings of CCS 2010. ACM, pp 753–755
Acknowledgements
We would like to thank Dr Yu Chen for his valuable suggestions. This paper was partially supported by the National Natural Science Foundation of China (Grant Nos. 61300213, 61672207, 61672295), Six Talents Peak Project of Jiangsu Province (Grant No. 2015-DZXX-020) and Jiangsu Provincial Natural Science Foundation (BK20161511).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that there is no conflict of interest regarding the publication of this paper (declaration attached).
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Informed consent
Informed consent was obtained from all individual participants included in the study.
Additional information
Communicated by V. Loia.
Rights and permissions
About this article
Cite this article
Han, J., Yang, Y., Liu, J.K. et al. Expressive attribute-based keyword search with constant-size ciphertext. Soft Comput 22, 5163–5177 (2018). https://doi.org/10.1007/s00500-017-2701-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-017-2701-9