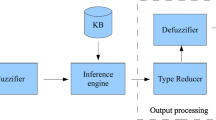
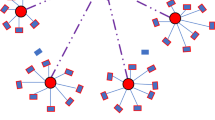
Abstract
Security is a major issue that is being constantly addressed in infrastructure less networks. An ad hoc network like MANET faces several issues that can jeopardize the transmissions in the network. A MANET can be made manageable by clustering it and appointing a cluster head. The cluster head communicates with the other cluster heads through base station. The cluster head routes all traffic from its members with the help of the base station, both within and outside the cluster. Several schemes have been suggested to find and eliminate malicious nodes that may hinder transmission. However, when the cluster member or the cluster head turns malicious, it may damage the transmission by tampering with the data and the routing policies. Though the security schemes target the nodes, they do not have specific techniques to handle a situation where the cluster member and cluster head turn malicious. Because of the constraints prevalent in the election of the cluster head and the selection of the cluster member, an intruder can penetrate and be elected as the cluster head or a member. Our proposed approach tries to counteract this situation by using a two-phase approach. The first phase uses fuzzy rules to form clusters and the second phase uses an efficient three-tier filtering methodology to identify the reliable nodes within the network. For the clustering process, a modified fuzzy C-means clustering algorithm (MFCM) is used to form the clusters. The three-tier filtering methodology decides the authenticity of the nodes by using an efficient filtering process. Our proposed technique can assure a better performance and enhanced throughput when compared to the existing techniques of EAACK.



















Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Acampora G et al (2010) Interoperable and adaptive fuzzy services for ambient intelligence applications. ACM Trans Auton Adapt Syst (TAAS) 5(2):8
Attar A et al (2012) A survey of security challenges in cognitive radio networks: solutions and future research directions. Proc IEEE 100(12):3172–3186
Balakrishna R, Reddy MM, Rao UR, Ramachanndra GA (2009) Detection of routing minbehavior in MANET using 2ACK. In: IEEE international advance computing conference (IACC 2009), Patiala, pp 6–7
Camara D, Loureiro AAF (2000) A novel routing algorithm for ad hoc networks. In: 33rd Hawaii international conference on system sciences—IEEE
Chinmay NK, Abani Kumar GK, Parida K, Das S (2011) Detection of routing misbehavior in MANET with 2ACK scheme. Int J Adv Comput Sci Appl 2(1)
Deng W, Zhao H, Liu J, Yan X, Li Y, Yin L, Ding C (2015) An improved CACO algorithm based on adaptive method and multi-variant strategies. Soft Comput 19(3):701–713
Dvir A, Vasilakos AV (2011) Backpressure-based routing protocol for DTNs ACM SIGCOM. Comput Commun Rev 41(4):405–406
Fadlullah ZM et al (2010) DTRAB: combating against attacks on encrypted protocols through traffic-feature analysis. IEEE/ACM Trans Netw 18(4):1234–1247
Gu B, Sheng VS (2016) A robust regularization path algorithm for \(\nu \)-support vector classification. IEEE Trans Neural Netw Learn Syst. doi:10.1109/TNNLS.2016.2527796
Gu B, Sheng VS, Tay KY, Romano W, Li S (2015a) Incremental support vector learning for ordinal regression. IEEE Trans Neural Netw Learn Syst 26(7):1403–1416
Gu B, Sheng VS, Wang Z, Ho D, Osman S, Li S (2015b) Incremental learning for \(\nu \)-support vector regression. Neural Netw 67:140–150
Gu B, Sun X, Sheng VS (2016) Structural minimax probability machine. IEEE Trans Neural Netw Learn Syst. doi:10.1109/TNNLS.2016.2544779
Jiang T et al (2012) QoE-driven channel allocation schemes for multimedia transmission of priority-based secondary users over cognitive radio networks. IEEE J Sel Areas Commun 30(7):1215–1224
Jing Q, Vasilakos AV, Wan J, Jingwei L, Qiu D (2014) Security of the internet of things: perspectives and challenges. Wirel Netw 20(8):2481–2501
Li P et al (2012) Code pipe: an opportunistic feeding and routing protocol for reliable multicast with pipelined network coding. In: INFOCOM, pp 100–108
Li P, Guo S, Shui Y, Vasilakos AV (2014) Reliable multicast with pipelined network coding using opportunistic feeding and routing. IEEE Trans Parallel Distrib Syst 25(12):3264–3273
Liu B et al (2014) Toward incentivizing anti-spoofing deployment. IEEE Trans Inf Forensics Secur 9(3):436–450
Liu J et al (2016a) Leveraging software-defined networking for security policy enforcement. Inf Sci 327:288–299
Liu Q, Cai W, Shen J, Zhangjie F, Liu X, Linge N (2016b) A speculative approach to spatial-temporal efficiency with multi-objective optimization in a heterogeneous cloud environment. Secur Commun Netw 9(17):4002–4012. doi:10.1002/sec.1582
Manikandan P, Selvarajan S (2015) Multi-objective clustering based on hybrid optimization algorithm (MO-CS-PSO) and its application to health data. J Med Imaging Health Inf 5(6):1133–1144
Manvia SS, Bhajantrib LB, Vaggac VK (2010) Routing misbehavior detection in MANETs using 2ACK. J Telecommun Inf Technol 4:105–111
Meng T, Wu F, Yang Z, Chenm G, Vasilakos A (2015) Spatial reusability-aware routing in multi-hop wireless networks. IEEE TMC. doi:10.1109/TC.2015.2417543
Ramakrishnan B (2010) Analytical study of cluster and sans cluster vehicular adhoc network. IJCEIT 25(1):1–11. ISSN 0974-2034 2010/9
Sathiamoorthy J, Ramakrishnan B (2015) Energy and delay efficient dynamic cluster formation using hybrid AGA with FACO in EAACK. Wireless Netw 1–15
Sathiamoorthy J, Ramakrishnan B (2016a) Energy and delay efficient dynamic cluster formation using improved ant colony optimization algorithm in EAACK MANETs. Wireless Pers Commun 1–122
Sathiamoorthy J, Ramakrishnan B (2016b) CEAACK—a reduced acknowledgment for better data transmission for MANETs. Int J Comput Netw Inf Secur 2:64—71
Sathiamoorthy J, Ramakrishnan B, Usha M (2015) A reliable and secure data transmission in CEAACK MANETs using distinct dynamic key with classified digital signature cryptographic algorithm. In: IEEE international conference on computing and communications technologies (ICCCT) (2015)
Shakshuki EM, Kang N, Sheltami TR (2013) EAACK—a secure intrusion-detection system for MANETs. IEEE Trans Ind Electron 60(3):1089–1098
Tian Q, Chen S (2017) Cross-Heterogeneous-database age estimation through correlation representation learning. Neurocomputing 238:286–295
Vasilakos AV et al (2015) Information centric network: research challenges and opportunities. J Netw Comput Appl 52:1–10
Wen X, Shao L, Xue Y, Fang W (2015) A rapid learning algorithm for vehicle classification. Inf Sci 295(1):395–406
Wu J, Dai F (2004) A generic distributed broadcast scheme in ad hoc wireless networks. IEEE Trans Comput 53(10):1343–1354
Xia Z, Wang X, Sun X, Wang B (2014) Steganalysis of least significant bit matching using multi-order differences. Secur Commun Netw 7(8):1283–1291
Xia Z, Wang X, Sun X, Liu Q, Xiong N (2016) Steganalysis of LSB matching using differences between non adjacent pixels. Multimed Tools Appl 75(4):1947–1962
Xue Y, Jiang J, Zhao B, Ma T (2017) A self-adaptive artificial bee colony algorithm based on global best for global optimization. Soft Comput. doi:10.1007/s00500-017-2547-1
Yan Z et al (2014) A survey on trust management for internet of things. J Netw Comput Appl 42:120–134
Yang J, Watada J (2012) Fuzzy clustering analysis of data mining: application to an accident mining system. Int J Innov Comput Inf Control ICIC Int 8(8):5715–5724. ISSN 1349-4198
Yang H et al (2014) Provably secure three-party authenticated key agreement protocol using smart cards. Comput Netw 58:29–38
Yang M et al (2015a) Software-defined and virtualized future mobile and wireless networks: a survey. MONET 20(1):4–18
Yang M, Li Y et al (2015b) Software-defined and virtualized future mobile and wireless networks: a survey ACM/Springer. Mob Netw Appl 20(1):4–18
Yao Y, Cao Q, Vasilakos AV (2013) EDAL: an energy-efficient, delay-aware, and lifetime-balancing data collection protocol for wireless sensor networks. In: MASS pp 182–190
Yao G et al (2015) Passive IP trace back: disclosing the locations of IP spoofers from path backscatter. IEEE Trans Inf Forensics Secur 10(3):471–484
Yen Y-S et al (2011) Flooding-limited and multi-constrained QoS multicast routing based on the genetic algorithm for MANETs. Math Comput Model 53(11–12):2238–2250
Youssef M et al (2014) Routing metrics of cognitive radio networks: a survey. IEEE Commun Surv Tutor 16(1):92–109
Yuan C, Xia Z, Sun X (2017) Coverless image steganography based on SIFT and BOF. J Internet Technol 18(2):209–216
Zeng Y et al (2013) Directional routing and scheduling for green vehicular delay tolerant networks. Wirel Netw 19(2):161–173
Zhang Y, Yan F, Vasilakos AV (2015) Interference-based topology control algorithm for delay-constrained mobile Ad hoc networks. IEEE Trans Mob Comput 14(4):742–754
Zhangjie F, Xinle W, Guan C, Sun X, Ren K (2016) Toward efficient multi-keyword fuzzy search over encrypted outsourced data with accuracy improvement. IEEE Trans Inf Forensics Secur 11(12):2706–2716. doi:10.1109/TIFS.2016.2596138
Zheng Y, Jeon B, Danhua X, Wu QMJ, Zhang H (2015) Image segmentation by generalized hierarchical fuzzy C-means algorithm. J Intell Fuzzy Syst 28(2):961–973
Zhou L, Xiong N, Shu L, Vasilakos AV, Yeo SS (2010) Context-aware middleware for multimedia services in heterogeneous networks. IEEE Intell Syst 25(2):40–47
Zhou J et al (2015a) Secure and privacy preserving protocol for cloud-based vehicular DTNs. IEEE Trans Inf Forensics Secur 10(6):1299–1314
Zhou J et al (2015b) 4S: a secure and privacy-preserving key management scheme for cloud-assisted wireless body area network in m-healthcare social networks. Inf Sci 314:255–276
Zhou Z, Wang Y, Wu QMJ, Yang C-N, Sun X (2017) Effective and efficient global context verification for image copy detection. IEEE Trans Inf Forensics Secur 12(1):48–63. doi:10.1109/TIFS.2016.2601065
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that there is no conflict of interest.
Additional information
Communicated by V. Loia.
Rights and permissions
About this article
Cite this article
Sathiamoorthy, J., Ramakrishnan, B. A competent three-tier fuzzy cluster algorithm for enhanced data transmission in cluster EAACK MANETs. Soft Comput 22, 6545–6565 (2018). https://doi.org/10.1007/s00500-017-2704-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-017-2704-6