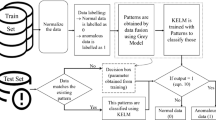
Abstract
Advances in digital electronics, wireless communications, and electro-mechanical systems technology have revolutionized the society and economy across the globe by enabling the development of low-cost, low-power, and multi-functional sensor nodes, from which the sensor networks are realized by leveraging the features of sensing, data processing, and communication present in these nodes. Though the energy of the wireless sensor network (WSN) nodes is limited, the detection of existing intrusion detection systems in WSN is weakly accurate further. To reduce the energy consumption of nodes in WSNs during detection processing, we propose a hierarchical intrusion detection model that clusters the nodes in a WSN according to their functions. Even more, to improve the detection accuracy of abnormal behavior of the WSN intrusion detection system and reduce the false alarm rate, it is considered in this research the usage of the classification algorithm of kernel extreme learning machine, following to Mercer Property to synthesize multi-kernel functions. We realize the optimal linear combination by testing and applying the multi-kernel function and build a multi-kernel extreme learning machine to WSN intrusion detection systems. Simulation results show that the system not only guarantees a high detection accuracy but also dramatically reduces the detection time, being well suited for resource-constrained WSNs.








Similar content being viewed by others
References
Bao F, Chen R, Chang MJ et al (2012) Hierarchical trust management for wireless sensor networks and its applications to trust-based routing and intrusion detection. IEEE Trans Netw Serv Manag 9(2):169–183
Borkar GM, Patil LH, Dalgade D et al (2019) A novel clustering approach and adaptive SVM classifier for intrusion detection in WSN: a data mining concept. Sustain Comput Inform Syst 23:120–135
Butun I, Morgera SD, Sankar R (2014) A survey of intrusion detection systems in wireless sensor networks. IEEE Commun Surv Tutor 16(1):266–282
Cao LL, Huang WB, Sun FC (2014) Optimization-based extreme learning machine with multi-kernel learning approach for classification. IEEE Comput Soc 14:3564–3569
Cheng C, Tay WP, Huang GB (2012) Extreme learning machines for intrusion detection. In: the 2012 international joint conference on neural networks (IJCNN). IEEE, pp 1–8
Dai JJ, Tao Y, Yang FY (2018) A novel intrusion detection system based on IABRBFSVM for wireless sensor networks. Procedia Comput Sci 131:1113–1121
Girolami M (2002) Mercer kernel-based clustering in feature space. IEEE Trans Neural Netw 13(3):780–784
Han Z, Zhang W, Chen Z (2010) A Markov-based intrusion detection scheme for wireless sensor networks. Comput Eng Sci 9:009
Huang GB, Chen L (2007) Convex incremental extreme learning machine. Neurocomputing 70(16):3056–3062
Huang GB, Zhu QY, Siew CK (2006) Extreme learning machine: theory and applications. Neurocomputing 70(16):489–501
Huang G, Huang GB, Song S et al (2015) Trends in extreme learning machines: a machines: a review. Neural Netw 61:32–48
Huang SH, Chen WZ, Li J (2017) Network intrusion detection based on extreme learning machine and principal component analysis. J Jilin Univ (Inf Sci Ed) 35(5):576–583
Liang W, Li K-C et al (2019a) An industrial network intrusion detection algorithm based on multi-feature data clustering optimization model. IEEE Trans Ind Inform. https://doi.org/10.1109/TII.2019.2946791
Liang W, Tang M, Long J, Peng X, Xu J, Li K-C (2019b) A secure fabric blockchain-based data transmission technique for industrial internet-of-things. IEEE Trans Ind Inform 15(6):3582–3592
Maleh Y, Ezzati A, Qasmaoui Y et al (2015) A global hybrid intrusion detection system for wireless sensor networks. Procedia Comput Sci 52:1047–1052
Rani TP, Jayakumar C (2017) Unique identity and localization based replica node detection in hierarchical wireless sensor networks. Comput Electr Eng 64:148–162
Shone N, Ngoc TN, Phai VD et al (2018) A deep learning approach to network intrusion detection. IEEE Trans Emerg Top Comput Intell 2(1):41–50
Silva AAPD, Martins MH, Rocha BP et al (2005) Decentralized intrusion detection in wireless sensor networks. In: Proceedings of the 1st ACM international workshop on quality of service & security in wireless and mobile networks, pp 16–23
Tang J, Deng C, Huang GB (2016) Extreme learning machine for multilayer perceptron. IEEE Trans Neural Netw Learn Syst 27(4):809–821
Wang CR, Xu RF, Lee SJ et al (2018) Network intrusion detection using equality constrained-optimization-based extreme learning machines. Knowl Based Syst 147:68–80
Yin C, Zhu Y, Fei J et al (2017) A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access 5(2):21954–21961
Zhang Z (2014) Efficient computer intrusion detection method based on artificial bee colony optimized kernel extreme learning machine. Indones J Electr Eng Comput Sci 12(3):1954–1959
Zhang YT, Ma C, Li ZN et al (2014) Online modeling of kernel extreme learning machine based on fast leave-one-out cross-validation. Shanghai Jiaotong Univ (Sci) 48:641–646
Acknowledgements
Authors of this manuscript are grateful to the valuable comments provided by external reviewers and international experts for the improvement of technical and organization sections.
Funding
This work is supported by the National Natural Science Foundation of China (Nos. 61672338 and 61873160).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All the authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Communicated by V. Loia.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhang, W., Han, D., Li, KC. et al. Wireless sensor network intrusion detection system based on MK-ELM. Soft Comput 24, 12361–12374 (2020). https://doi.org/10.1007/s00500-020-04678-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-020-04678-1