Abstract
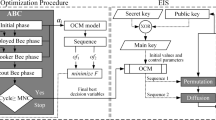
In this study, a novel 2D fully chaotic map (FULLMAP) derived through a multi-objective optimization strategy with artificial bee colony (ABC) algorithm is introduced for image encryption procedures (IMEPs). First, a model for FULLMAP with eighth decision variables was empirically constituted, and then, the variables were optimally determined using ABC for minimizing a quadruple-objective function composed of Lyapunov exponent (LE), entropy, 0–1 test and correlation coefficient. FULLMAP manifests superior performance in diverse measurements such as bifurcation, 3D phase space, LE, 0–1 test, permutation entropy (PE) and sample entropy (SE). The encryption performance of FULLMAP through an IMEP was verified with respect to various cryptanalyses compared with many reported studies, as well. The main advantage of FULLMAP rather than the optimization-based IMEP studies reported elsewhere is that it need not any optimization in the encryption procedures, and hence, it is faster than the reported procedures. On the other hand, those studies use ciphertext images through IMEPs in every cycle of the optimization. For this reason, they might have long processing time. As a result, the proposed IMEP with FULLMAP demonstrates better cryptanalyses for the most of the compared results.
















Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Xuejing K, Zihui G (2020) A new color image encryption scheme based on DNA encoding and spatiotemporal chaotic system. Signal Process Image Commun 80:1–11. https://doi.org/10.1016/j.image.2019.115670
Alawida M, Samsudin A, Sen TJ, Alkhawaldeh RS (2019) A new hybrid digital chaotic system with applications in image encryption. Signal Process 160:45–58. https://doi.org/10.1016/j.sigpro.2019.02.016
Bao L, Yi S, Zhou Y (2017) Combination of Sharing Matrix and Image Encryption for Lossless (k, n)-Secret Image Sharing. IEEE Trans Image Process 26:5618–5631. https://doi.org/10.1109/TIP.2017.2738561
Zhang F, Kodituwakku HADE, Hines JW, Coble J (2019) Multilayer Data-Driven Cyber-Attack Detection System for Industrial Control Systems Based on Network, System, and Process Data. IEEE Trans Ind Informatics 15:4362–4369. https://doi.org/10.1109/TII.2019.2891261
Chen J, Chen L, Zhou Y (2020) Cryptanalysis of a DNA-based image encryption scheme. Inf Sci (Ny) 520:130–141. https://doi.org/10.1016/j.ins.2020.02.024
Liu Y, Qin Z, Liao X, Wu J (2020) Cryptanalysis and enhancement of an image encryption scheme based on a 1-D coupled Sine map. Nonlinear Dyn 100:2917–2931. https://doi.org/10.1007/s11071-020-05654-y
Hua Z, Zhu Z, Yi S et al (2021) Cross-plane colour image encryption using a two-dimensional logistic tent modular map. Inf Sci (Ny) 546:1063–1083. https://doi.org/10.1016/j.ins.2020.09.032
Talhaoui MZ, Wang X (2020) A new fractional one dimensional chaotic map and its application in high-speed image encryption. Inf Sci (Ny). https://doi.org/10.1016/j.ins.2020.10.048
Wen W, Wei K, Zhang Y et al (2020) Colour light field image encryption based on DNA sequences and chaotic systems. Nonlinear Dyn 99:1587–1600. https://doi.org/10.1007/s11071-019-05378-8
Zheng P, Huang J (2018) Efficient Encrypted Images Filtering and Transform Coding with Walsh-Hadamard Transform and Parallelization. IEEE Trans Image Process 27:2541–2556. https://doi.org/10.1109/TIP.2018.2802199
Ćalasan M, Abdel Aleem SHE, Bulatović M et al (2021) Design of controllers for automatic frequency control of different interconnection structures composing of hybrid generator units using the chaotic optimization approach. Int J Electr Power Energy Syst 129:106879. https://doi.org/10.1016/j.ijepes.2021.106879
Pierezan J, dos Santos CL, Cocco Mariani V et al (2021) Chaotic coyote algorithm applied to truss optimization problems. Comput Struct 242:106353. https://doi.org/10.1016/j.compstruc.2020.106353
Yousri D, Allam D, Eteiba MB (2019) Chaotic whale optimizer variants for parameters estimation of the chaotic behavior in Permanent Magnet Synchronous Motor. Appl Soft Comput J 74:479–503. https://doi.org/10.1016/j.asoc.2018.10.032
Coelho LDS, Mariani VC, Guerra FA et al (2014) Multiobjective optimization of transformer design using a chaotic evolutionary approach. IEEE Trans Magn 50:669–672. https://doi.org/10.1109/TMAG.2013.2285704
Okamoto T, Hirata H (2013) Global optimization using a multipoint type quasi-chaotic optimization method. Appl Soft Comput J 13:1247–1264. https://doi.org/10.1016/j.asoc.2012.10.025
dos Coelho L, S, Mariani VC, (2009) A novel chaotic particle swarm optimization approach using Hénon map and implicit filtering local search for economic load dispatch. Chaos, Solitons Fractals 39:510–518. https://doi.org/10.1016/j.chaos.2007.01.093
Chai X, Gan Z, Yuan K et al (2019) A novel image encryption scheme based on DNA sequence operations and chaotic systems. Neural Comput Appl 31:219–237. https://doi.org/10.1007/s00521-017-2993-9
Wang X, Li Y (2021) Chaotic image encryption algorithm based on hybrid multi-objective particle swarm optimization and DNA sequence. Opt Lasers Eng 137:106393. https://doi.org/10.1016/j.optlaseng.2020.106393
Ahmad M, Alam MZ, Umayya Z et al (2018) An image encryption approach using particle swarm optimization and chaotic map. Int J Inf Technol 10:247–255. https://doi.org/10.1007/s41870-018-0099-y
Kaur M, Kumar V, Li L (2019) Color image encryption approach based on memetic differential evolution. Neural Comput Appl 31:7975–7987. https://doi.org/10.1007/s00521-018-3642-7
Dua M, Wesanekar A, Gupta V et al (2020) Differential evolution optimization of intertwining logistic map-DNA based image encryption technique. J Ambient Intell Humaniz Comput 11:3771–3786. https://doi.org/10.1007/s12652-019-01580-z
Saravanan S, Sivabalakrishnan M (2021) A hybrid chaotic map with coefficient improved whale optimization-based parameter tuning for enhanced image encryption. Soft Comput 48:1–24. https://doi.org/10.1007/s00500-020-05528-w
Wang H, Xiao D, Chen X, Huang H (2018) Cryptanalysis and enhancements of image encryption using combination of the 1D chaotic map. Signal Process 144:444–452. https://doi.org/10.1016/j.sigpro.2017.11.005
Mansouri A, Wang X (2020) A novel one-dimensional sine powered chaotic map and its application in a new image encryption scheme. Inf Sci (Ny) 520:46–62. https://doi.org/10.1016/j.ins.2020.02.008
Wu J, Liao X, Yang B (2018) Image encryption using 2D Hénon-Sine map and DNA approach. Signal Process 153:11–23. https://doi.org/10.1016/j.sigpro.2018.06.008
Chen C, Sun K, He S (2020) An improved image encryption algorithm with finite computing precision. Signal Process 168:1–10. https://doi.org/10.1016/j.sigpro.2019.107340
Su Y, Tang C, Chen X et al (2017) Cascaded Fresnel holographic image encryption scheme based on a constrained optimization algorithm and Henon map. Opt Lasers Eng 88:20–27. https://doi.org/10.1016/j.optlaseng.2016.07.012
Farah MAB, Guesmi R, Kachouri A, Samet M (2020) A novel chaos based optical image encryption using fractional Fourier transform and DNA sequence operation. Opt Laser Technol 121:105777. https://doi.org/10.1016/j.optlastec.2019.105777
Kaur M, Singh D, Uppal RS (2020) Parallel strength Pareto evolutionary algorithm-II based image encryption. IET Image Process 14:1015–1026. https://doi.org/10.1049/iet-ipr.2019.0587
Asgari-Chenaghlu M, Feizi-Derakhshi MR, Nikzad-Khasmakhi N et al (2021) Cy: Chaotic yolo for user intended image encryption and sharing in social media. Inf Sci (Ny) 542:212–227. https://doi.org/10.1016/j.ins.2020.07.007
Enayatifar R, Guimarães FG, Siarry P (2019) Index-based permutation-diffusion in multiple-image encryption using DNA sequence. Opt Lasers Eng 115:131–140. https://doi.org/10.1016/j.optlaseng.2018.11.017
Chai X, Bi J, Gan Z et al (2020) Color image compression and encryption scheme based on compressive sensing and double random encryption strategy. Signal Process 176:107684. https://doi.org/10.1016/j.sigpro.2020.107684
Suri S, Vijay R (2020) A Pareto-optimal evolutionary approach of image encryption using coupled map lattice and DNA. Neural Comput Appl 32:11859–11873. https://doi.org/10.1007/s00521-019-04668-x
Kaur M, Singh D (2020) Multiobjective evolutionary optimization techniques based hyperchaotic map and their applications in image encryption. Multidimens Syst Signal Process 32:281–301. https://doi.org/10.1007/s11045-020-00739-8
Yang Y, Wang L, Duan S, Luo L (2021) Dynamical analysis and image encryption application of a novel memristive hyperchaotic system. Opt Laser Technol 133:106553. https://doi.org/10.1016/j.optlastec.2020.106553
Hanis S, Amutha R (2019) A fast double-keyed authenticated image encryption scheme using an improved chaotic map and a butterfly-like structure. Nonlinear Dyn 95:421–432. https://doi.org/10.1007/s11071-018-4573-7
Asgari-Chenaghlu M, Balafar MA, Feizi-Derakhshi MR (2019) A novel image encryption algorithm based on polynomial combination of chaotic maps and dynamic function generation. Signal Process 157:1–13. https://doi.org/10.1016/j.sigpro.2018.11.010
Lan R, He J, Wang S et al (2018) Integrated chaotic systems for image encryption. Signal Process 147:133–145. https://doi.org/10.1016/j.sigpro.2018.01.026
Chai X, Fu X, Gan Z et al (2019) A color image cryptosystem based on dynamic DNA encryption and chaos. Signal Process 155:44–62. https://doi.org/10.1016/j.sigpro.2018.09.029
Hua Z, Zhou Y, Huang H (2019) Cosine-transform-based chaotic system for image encryption. Inf Sci (Ny) 480:403–419. https://doi.org/10.1016/j.ins.2018.12.048
Sreelaja NK, Vijayalakshmi Pai GA (2012) Stream cipher for binary image encryption using Ant Colony Optimization based key generation. Appl Soft Comput J 12:2879–2895. https://doi.org/10.1016/j.asoc.2012.04.002
Carbas S, Toktas A, Ustun D (2021) Nature-Inspired Metaheuristic Algorithms for Engineering Optimization Applications. Springer Singapore
Li G, Liu L, Feng X (2019) Accelerating GPU Computing at Runtime with Binary Optimization. In: CGO 2019 - Proceedings of the 2019 IEEE/ACM International Symposium on Code Generation and Optimization. Institute of Electrical and Electronics Engineers Inc., pp 276–277
Premkumar M, Jangir P, Sowmya R (2021) MOGBO: A new Multiobjective Gradient-Based Optimizer for real-world structural optimization problems. Knowledge-Based Syst 218:106856. https://doi.org/10.1016/j.knosys.2021.106856
Moreno SR, Pierezan J, dos Coelho L, S, Mariani VC, (2021) Multi-objective lightning search algorithm applied to wind farm layout optimization. Energy 216:119214. https://doi.org/10.1016/j.energy.2020.119214
Vasconcelos Segundo EH, de, Mariani VC, Coelho L dos S, (2019) Metaheuristic inspired on owls behavior applied to heat exchangers design. Therm Sci Eng Prog 14:100431. https://doi.org/10.1016/j.tsep.2019.100431
Rubio-Largo Á, Vega-Rodríguez MA, González-Álvarez DL (2016) Hybrid multiobjective artificial bee colony for multiple sequence alignment. Appl Soft Comput J 41:157–168. https://doi.org/10.1016/j.asoc.2015.12.034
Zhou X, Liu Y, Li B, Sun G (2015) Multiobjective biogeography based optimization algorithm with decomposition for community detection in dynamic networks. Phys A Stat Mech its Appl 436:430–442. https://doi.org/10.1016/j.physa.2015.05.069
Sajasi S, Eftekhari Moghadam AM (2015) An adaptive image steganographic scheme based on Noise Visibility Function and an optimal chaotic based encryption method. Appl Soft Comput J 30:375–389. https://doi.org/10.1016/j.asoc.2015.01.032
Alkebsi K, Du W (2020) A Fast Multi-Objective Particle Swarm Optimization Algorithm Based on a New Archive Updating Mechanism. IEEE Access 8:124734–124754. https://doi.org/10.1109/ACCESS.2020.3007846
Demertzis K, Iliadis L (2017) Adaptive elitist differential evolution extreme learning machines on big data: Intelligent recognition of invasive species. In: Advances in Intelligent Systems and Computing. Springer Verlag, pp 333–345
Arora S, Singh S (2016) Butterfly algorithm with Lèvy Flights for global optimization. In: Proceedings of 2015 International Conference on Signal Processing, Computing and Control, ISPCC 2015. Institute of Electrical and Electronics Engineers Inc., pp 220–224
Karaboga D, Basturk B (2007) A powerful and efficient algorithm for numerical function optimization: artificial bee colony (ABC) algorithm. J Glob Optim 39:459–471. https://doi.org/10.1007/s10898-007-9149-x
Toktas A, Ustun D (2020) Triple-Objective Optimization Scheme Using Butterfly-Integrated ABC Algorithm for Design of Multilayer RAM. IEEE Trans Antennas Propag 68:5603–5612. https://doi.org/10.1109/TAP.2020.2981728
Toktas A, Ustun D, Tekbas M (2020) Global optimisation scheme based on triple-objective ABC algorithm for designing fully optimised multi-layer radar absorbing material. IET Microwaves, Antennas Propag 14:800–811. https://doi.org/10.1049/iet-map.2019.0868
Toktas A, Ustun D, Erdogan N (2020) Pioneer Pareto artificial bee colony algorithm for three-dimensional objective space optimization of composite-based layered radar absorber. Appl Soft Comput 96:1–12. https://doi.org/10.1016/j.asoc.2020.106696
Akdagli A, Toktas A (2010) A novel expression in calculating resonant frequency of H-shaped compact microstrip antennas obtained by using artificial bee colony algorithm. J Electromagn Waves Appl 24:2049–2061. https://doi.org/10.1163/156939310793675989
Toktas A (2021) Multi-objective design of multilayer microwave dielectric filters using artificial bee colony algorithm. In: Carbas S, Toktas A, Ustun D (eds) Nature-Inspired Metaheuristic Algorithms for Engineering Optimization Applications. Springer Singapore
May RM (1976) Simple mathematical models with very complicated dynamics. Nature 261:459–467. https://doi.org/10.1038/261459a0
Gottwald GA, Melbourne I (2016) The 0–1 test for chaos: A review. In: Lecture Notes in Physics. Springer Verlag, pp 221–247
Richman JS, Moorman JR (2000) Physiological time-series analysis using approximate and sample entropy. Am J Physiol - Hear Circ Physiol 278:2039–2049. https://doi.org/10.1152/ajpheart.2000.278.6.h2039
Bandt C, Pompe B (2002) Permutation Entropy: A Natural Complexity Measure for Time Series. Phys Rev Lett 88:4. https://doi.org/10.1103/PhysRevLett.88.174102
Yang F, Mou J, Liu J et al (2020) Characteristic analysis of the fractional-order hyperchaotic complex system and its image encryption application. Signal Process 169:1–16. https://doi.org/10.1016/j.sigpro.2019.107373
Wu Y, Zhang L, Qian T et al (2021) Content-adaptive image encryption with partial unwinding decomposition. Signal Process 181:107911. https://doi.org/10.1016/j.sigpro.2020.107911
Luo Y, Lin J, Liu J et al (2019) A robust image encryption algorithm based on Chua’s circuit and compressive sensing. Signal Process 161:227–247. https://doi.org/10.1016/j.sigpro.2019.03.022
Chai X, Zheng X, Gan Z et al (2018) An image encryption algorithm based on chaotic system and compressive sensing. Signal Process 148:124–144. https://doi.org/10.1016/j.sigpro.2018.02.007
Wang X, Gao S (2020) Image encryption algorithm based on the matrix semi-tensor product with a compound secret key produced by a Boolean network. Inf Sci (Ny) 539:195–214. https://doi.org/10.1016/j.ins.2020.06.030
Alvarez G, Li S (2006) Some basic cryptographic requirements for chaos-based cryptosystems. Int J Bifurc Chaos 16:2129–2151. https://doi.org/10.1142/S0218127406015970
Zhang X, Zhao Z, Wang J (2014) Chaotic image encryption based on circular substitution box and key stream buffer. Signal Process Image Commun 29:902–913. https://doi.org/10.1016/j.image.2014.06.012
Asuni N, Giachetti A (2014) TESTIMAGES: a large-scale archive for testing visual devices and basic image processing algorithms. In: Giachetti A (ed) STAG: Smart Tools & Apps for Graphics (2014). The Eurographics Association
Wu Y, Noonan JP, Agaian S (2011) NPCR and UACI Randomness Tests for Image Encryption. Cyber Journals Multidiscip Journals Sci Technol J Sel Areas Telecommun 31–38
Enginoğlu S, Erkan U, Memiş S (2019) Pixel similarity-based adaptive Riesz mean filter for salt-and-pepper noise removal. Multimed Tools Appl. https://doi.org/10.1007/s11042-019-08110-1
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Toktas, A., Erkan, U. 2D fully chaotic map for image encryption constructed through a quadruple-objective optimization via artificial bee colony algorithm. Neural Comput & Applic 34, 4295–4319 (2022). https://doi.org/10.1007/s00521-021-06552-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-021-06552-z