Abstract
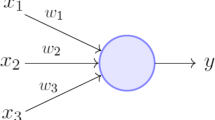
Telemedicine is one of the safest methods to provide healthcare facilities to the remote patients with the help of digitization. In this paper, state-of-the-art session key has been proposed based on the priority oriented neural machines followed by its validation. State-of-the-art technique can be mentioned as newer scientific method. Soft computing has been extensively used and modified here under the ANN domain. Telemedicine facilitates secure data communication between the patients and the doctors regarding their treatments. The best fitted hidden neuron can contribute only in the formation of the neural output. Minimum correlation was taken into consideration under this study. Hebbian learning rule was applied on both the patient’s neural machine and the doctor’s neural machine. Lesser iterations were needed in the patient’s machine and the doctor’s machine for the synchronization. Thus, the key generation time has been shortened here which were 4.011 ms, 4.324 ms, 5.338 ms, 5.691 ms, and 6.105 ms for 56 bits, 128 bits, 256 bits, 512 bits, and 1024 bits of state-of-the-art session keys, respectively. Statistically, different key sizes of the state-of-the-art session keys were tested and accepted. Derived value-based function had yielded successful outcomes too. Partial validations with different mathematical hardness had been imposed here too. Thus, the proposed technique is suitable for the session key generation and authentication in the telemedicine in order to preserve the patients’ data privacy. This proposed method has been highly protective against numerous data attacks inside the public networks. Partial transmission of the state-of-the-art session key disables the intruders to decode the same bit patterns of the proposed set of keys.



Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Data availability
Data sharing not applicable to this article as no datasets were generated or analyzed during the current study.
References
Maatuk AM, Elberkawi EK, Aljawarneh S et al (2021) The COVID-19 pandemic and E-learning: challenges and opportunities from the perspective of students and instructors. J Comput High Educ. https://doi.org/10.1007/s12528-021-09274-2
Almaiah MA, Al-Khasawneh A, Althunibat A (2020) Exploring the critical challenges and factors influencing the Elearning system usage during COVID-19 pandemic. Educ Inf Technol 25:5261–5280. https://doi.org/10.1007/s10639-020-10219-y
Mislovaty R, Perchenok Y, Kanter I, Kinzel W (2002) Secure key-exchange protocol with an absence of injective functions. Phys Rev E 66:066102
Song S, Miller KD, Abbott LF (2000) Competitive Hebbian learning through spike-timing-dependent synaptic plasticity. Nat Neurosci 3:919–926
Jeong S, Park C, Hong D, Seo C, Jho N (2021) Neural cryptography based on generalized tree parity machine for real-life systems. Secur Commun Netw. https://doi.org/10.1155/2021/6680782
Hellman M (1978) An overview of public key cryptography. IEEE Commun Soc Mag 16(6):24–32
Rivest RL, Shamir A, Adleman L (1978) A method for obtaining digital signatures and public-key cryptosystems. Commun ACM 21(2):120–126
Anoop MS (2008) Security needs in embedded systems. IACR Cryptology ePrint Archive 198
Choi Y et al (2014) Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 14(6):10081–10106
Carlson A (1990) Anti-Hebbian learning in a non-linear neural network. Biol Cybern 64:171–176
Yang XS (2010) Nature-inspired Metaheuristic Algorithms Luniver Press.
Francke JA, Groden P, Ferrer C et al (2022) Remote enrollment into a telehealth-delivering patient portal: Barriers faced in an urban population during the COVID-19 pandemic. Health Technol 12:227–238. https://doi.org/10.1007/s12553-021-00614-x
Alonso SG, Marques G, Barrachina I et al (2021) Telemedicine and e-Health research solutions in literature for combatting COVID-19: a systematic review. Health Technol 11:257–266. https://doi.org/10.1007/s12553-021-00529-7
Ghosh A, Gupta R, Misra A (2020) Telemedicine for diabetes care in India during COVID19 pandemic and national lockdown period: Guidelines for physicians. Diabetes Metab Syndr: Clin Res Rev 14:273–276. https://doi.org/10.1016/j.dsx.2020.04.001
Abo-Zahhad M, Ahmed SM, Elnahas O (2014) A wireless emergency telemedicine system for patients monitoring and diagnosis. Int J Telemed App. https://doi.org/10.1155/2014/380787
Hatcher-Martin JM, Adams JL, Anderson ER et al (2020) Telemedicine in Neurology. Neurology 94(1):30–38
Norman S (2006) The use of telemedicine in psychiatry. J Psychiatr Mental Health Nursing 13(6):771–777
Tresenriter M, Holdaway J, Killeen J et al (2021) The implementation of an emergency medicine telehealth system during a pandemic. J Emergency Med 60(4):548–553
Bokolo A (2021) Exploring the adoption of telemedicine and virtual software for care of outpatients during and after COVID-19 pandemic. Ir J Med Sci 190:1–10. https://doi.org/10.1007/s11845-020-02299-z
Yang L, Brown-Johnson CG, Miller-Kuhlmann R et al (2020) Accelerated launch of video visits in ambulatory neurology during COVID-19. Neurology 95(7):305–311
Chauhan V, Galwankar S, Arquilla B et al (2020) Novel coronavirus (COVID-19): leveraging telemedicine to optimize care while minimizing exposures and viral transmission. J Emerg Trauma Shock 13(1):20
Jnr Bokolo A (2020) Use of telemedicine and virtual care for remote treatment in response to COVID-19 pandemic. J Med Syst 44:132
Dey J, Mukherjee S (2021) Wireless COVID-19 telehealth: leukocytes encryption guided by amino acid matrix. Wireless Pers Commun 120:1769–1789. https://doi.org/10.1007/s11277-021-08534-9
Sarkar A, Dey J, Chatterjee M, Bhowmik A, Karforma S (2019) Neural soft computing based secured transmission of intraoral gingivitis image in E-health. Indonesian J Electr Eng Comput Sci 14(1):178–184
Rahman S, Amit S, Kafy A (2022) Impact of COVID-19 and telehealth on mental health in Bangladesh: a propensity score matching approach. Spat Inf Res. https://doi.org/10.1007/s41324-022-00434-9
Dash S, Aarthy R, Mohan V (2021) Telemedicine during COVID-19 in India—a new policy and its challenges. J Public Health Pol 42:501–509. https://doi.org/10.1057/s41271-021-00287-w
Lei X, Liao X, Chen F, Huang T (2013) Two-layer tree-connected feed-forward neural network model for neural cryptography. Phys Rev E 87(3):032811
Allam AM, Abbas HM, El-Kharashi MW (2013) Authenticated key exchange protocol using neural cryptography with secret boundaries. In: The 2013 International Joint Conference on Neural Networks (IJCNN) Aug 4 (pp. 1-8). IEEE.
Dey L, Chakraborty S, Mukhopadhyay A (2020) Machine learning techniques for sequence-based prediction of viral–host interactions between SARS-CoV-2 and human proteins. Biomed J 43(5):438–450
Jeong S, Park C, Hong D, Seo C, Jho N (2021) Neural cryptography based on generalized tree parity machine for real-life systems. Secur Commun Netw. https://doi.org/10.1155/2021/6680782
Mislovaty R, Perchenok Y, Kanter I, Kinzel W (2002) Secure key-exchange protocol with an absence of injective functions. Phys Rev E 66(6):066102
Rosen-Zvi M, Klein E, Kanter I, Kinzel W (2002) Mutual learning in a tree parity machine and its application to cryptography. Phys Rev E 66(6):066135
Dolecki M, Kozera R (2015) The Impact of the TPM Weights Distribution on Network Synchronization Time. Computer Information Systems and Industrial Management, pp.451–460.
Ruttor A, Kinzel W, Kanter I (2007) Dynamics of neural cryptography. Phys Rev E 75(5):056104
Volkmer M, Wallner S (2005) Tree parity machine rekeying architectures. IEEE Trans Comput 54(4):421–427
Santhanalakshmi S, Sudarshan T, Patra GK Neural synchronization by mutual learning using genetic approach for secure key generation. In: Proceedings of the International Conference on Security in Computer Networks and Distributed Systems, 422–431, Thiruvanathapuram, India, March 2014.
Han YL, Li Y, Li Z, Zhu SS (2020) An improved method to evaluate the synchronization in neural key exchange protocol. Secur Commun Netw. https://doi.org/10.1155/2020/8869688
Jalali MS et al (2020) Why employees (still ) click on phishing links: investigation in hospitals. J Med Internet Res 22(1):e16775
Bassan S (2020) Data privacy considerations for telehealth consumers amind COVID-19. J Law Biosci 7(1).
Kahate A (2006) Cryptography and Network Security, 2003. Tata McGraw-Hill publishing Company Limited, Eighth reprint
Rukhin A, Soto J, Nechvatal J, Smid M, Barker E, Leigh S, Levenson M, Vangel M, Banks D, Heckert A, Dray J, Vo S (2001) A statistical test suite for random and pseudorandom number generators for cryptographic applications. NIST special publication 800–22.
Martínez Padilla J, Meyer-Baese U, Foo S (2018) Security evaluation of Tree Parity Re-keying Machine implementations utilizing side-channel emissions. EURASIP J on Info Secur 2018:3. https://doi.org/10.1186/s13635-018-0073-z
Wu B, Chen J, Wu J, Cardei M (2007) A Survey of Attacks and Countermeasures in Mobile Ad Hoc Networks. In: Xiao, Y., Shen, X.S., Du, DZ. (eds) Wireless Network Security. Signals and Communication Technology. Springer, Boston, MA. https://doi.org/10.1007/978-0-387-33112-6_5.
Hofstede R, Jonker M, Sperotto A et al (2017) Flow-based web application brute-force attack and compromise detection. J Netw Syst Manage 25:735–758. https://doi.org/10.1007/s10922-017-9421-4
Vykopal J (2013) Flow-based brute-force attack detection in large and high-speed networks. Ph.D. thesis, Masaryk University, Brno, Czech Republic.
Rui Z, et al. (2020). PassEye: Sniffing Your Password from HTTP Sessions by Deep Neural Network. In: Cyber Security. CNCERT 2020. Communications in Computer and Information Science, vol 1299. Springer, Singapore. https://doi.org/10.1007/978-981-33-4922-3_1.
Acknowledgements
The author do acknowledges the moral and congenial atmosphere support provided by Maharajadhiraj Uday Chand Women’s College, Burdwan, India -713104.
Funding
Not applicable.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interests
There is no conflict of interests in this manuscript.
Ethics approval and consent to participate
Not applicable.
Consent for publication
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Dey, J. State-of-the-art session key generation on priority-based adaptive neural machine (PANM) in telemedicine. Neural Comput & Applic 35, 9517–9533 (2023). https://doi.org/10.1007/s00521-022-08169-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-022-08169-2