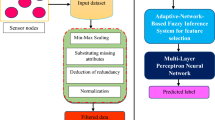
Abstract
The intrusion detection systems (IDSs) developed based on classification algorithms for securing wireless sensor networks (WSNs) are unable to attain the required detection accuracy. To handle the security issue in WSN, an intelligent IDS is proposed in this work by using a convolution neural network (CNN)-based deep learning approach along with a fuzzy inference model. The proposed IDS keeps track of the network and system activities by using the proposed fuzzy CNN along with spatial and temporal constraints to detect malicious nodes. Moreover, this algorithm has been modelled mathematically by using Feynman Path Integral and Schrodinger equation for handling the spatial and temporal constraints with fuzzy rules. From the experiments conducted in this work, it is proved that the proposed IDS increases the security, detection accuracy and packet delivery ratio, but decreases the delay and false positive rate in WSNs when compared with the existing IDSs.











Similar content being viewed by others
Data availability
The datasets generated during and/or analysed during the current study are available from the corresponding author on reasonable request.
References
Selvi M, Santhosh Kumar SVN, Ganapathy S, Ayyanar A, Khanna Nehemiah H, Kannan A (2021) An energy efficient clustered gravitational and fuzzy based routing algorithm in WSNs. Wirel Pers Commun 116:61–90
Nancy P, Muthurajkumar S, Ganapathy S, Santhosh Kumar SVN, Selvi M, Arputharaj K (2020) Intrusion detection using dynamic feature selection and fuzzy temporal decision tree classification for wireless sensor networks. IET Commun 14(5):888–895
Alqahtani M, Gumaei A, Mathkour H, Ben Ismail MM (2019) A genetic-based extreme gradient boosting model for detecting intrusions in wireless sensor networks. Sensors 19(20):4383
Kaur S, Singh M (2020) Hybrid intrusion detection and signature generation using Deep Recurrent Neural Networks. Neural Comput Appl 32(12):7859–7877
Zhou Y, Cheng G, Jiang S, Dai M (2020) Building an efficient intrusion detection system based on feature selection and ensemble classifier. Comput Netw 174:107247
Mighan SN, Kahani M (2021) A novel scalable intrusion detection system based on deep learning. Int J InfSecur 20:387–403
Riyaz B, Ganapathy S (2020) A deep learning approach for effective intrusion detection in wireless networks using CNN. Soft Comput 24(22):17265–17278
Zheng S (2021) network intrusion detection model based on convolutional neural network. In: proceedings of the IEEE conference on advanced information technology, electronic and automation control conference (IAEAC), pp 634–637. https://doi.org/10.1109/IAEAC50856.2021.9390930
Subramani S, Selvi M (2023) Multi-objective PSO based feature selection for intrusion detection in IoT based wireless sensor networks. Optik 273:170419
Maheshwari P, Sharma AK, Verma K (2021) Energy efficient cluster based routing protocol for WSN using butterfly optimization algorithm and ant colony optimization. Ad Hoc Netw 110:102317. https://doi.org/10.1016/j.adhoc.2020.102317
Batra PK, Kant K (2016) LEACH-MAC: a new cluster head selection algorithm for wireless sensor networks. Wirel Netw 22(1):49–60. https://doi.org/10.1007/s11276-015-0951-y
Pal R, Yadav S, Aarti KR (2020) EEWC: energy-efficient weighted clustering method based on genetic algorithm for HWSNs. Complex Intell Syst 6(2):391–400. https://doi.org/10.1007/s40747-020-00137-4
Bhushan S, Pal R, Antoshchuk SG (2018) Energy efficient clustering protocol for heterogeneous wireless sensor network: a hybrid approach using GA and K-means. In: proceedings of the IEEE conference on data stream min process DSMP, pp 381–385. https://doi.org/10.1109/DSMP.2018.8478538
Singh A, Sharma S, Singh J (2021) Nature-inspired algorithms for wireless sensor networks: a comprehensive survey. Comput Sci Rev 39:100342
Cao Y, Zhao Y, Dai, F (2019) Node localization in wireless sensor networks based on quantum annealing algorithm and edge computing. In: proceedings of the IEEE conference on Internet of Things (iThings) and IEEE green computing and communications (greencom) and ieee cyber, physical and social computing (cpscom) and ieee smart data (SmartData), pp 564–568). https://doi.org/10.1109/iThings/GreenCom/CPSCom/SmartData.2019.00112
Selvi M, Thangaramya K, Sannasi G, Kulothungan K, Khannah Nehemiah H, Kannan A (2019) An energy aware trust based secure routing algorithm for effective communication in wireless sensor networks. Wirel Pers Commun 105:1475–1490
Ashwini B A, Manivannan S S (2020) Supervised machine learning classification algorithmic approach for finding anomaly type of intrusion detection in wireless sensor network. Opt. Mem. Neural Netw Inf Opt 29(3), 244–256. https://doi.org/10.3103/S1060992X20030029
Bhushan B (2022) Intrusion detection system (IDS) for security enhancement in wireless sensing applications. Proc Innov Electron Commun Eng (ICIECE) 355:39–49
Madhu S, Prasad RK, Ramotra P, Edla DR, Lipare A (2022) A location-less energy efficient algorithm for load balanced clustering in wireless sensor networks. Wirel Pers Commun 122(2):1967–1985
Zhao C, Wu Q, Lin D, Zhang Z, Zhang Y, Kong L, Guan YL (2022) An energy-balanced unequal clustering approach for circular wireless sensor networks. Ad Hoc Netw 132:102872
Muthurajkumar S, Ganapathy S, Vijayalakshmi M, Kannan A (2015) Secured temporal log management techniques for cloud. In: proceedings of the IEEE conference on Procedia Comput Sci 46, 589–595.
Rajasoundaran S, Santhosh Kumar SVN, Selvi M, Ganapathy S, Rakesh R, Kannan A (2021) Machine learning based volatile block chain construction for secure routing in decentralized military sensor networks. Wirel Netw 27(7):4513–4534
Senthilnayaki B, Venkatalakshmi K, Kannan A (2019) Intrusion detection system using fuzzy rough set feature selection and modified KNN classifier. Int Arab J Inf Technol 16(4):746–753
Yin C, Zhu Y, Fei J, He X (2017) A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access 5:21954–21961
Hosseini S (2020) A new machine learning method consisting of GA-LR and ANN for attack detection. Wirel Networks 26(6):4149–4162
Sahoo BM, Pandey HM, Amgoth T (2021) GAPSO-H: a hybrid approach towards optimizing the cluster based routing in wireless sensor network. Swarm Evol Comput 60:100772
Santhosh Kumar SVN, Selvi M, Kannan A (2023) A comprehensive survey on machine learning-based intrusion detection systems for secure communication in internet of things. Comput Intell Neurosci 2023:1–24
Singh A, Amutha J, Nagar J, Sharma S, Lee CC (2022) AutoML-ID: automated machine learning model for intrusion detection using wireless sensor network. Sci Rep 12(1):1–14
Subbiah S, Anbananthen KSM, Thangaraj S, Kannan S, Chelliah D (2022) Intrusion detection technique in wireless sensor network using grid search random forest with Boruta feature selection algorithm. J Commun Netw 24(2):264–273
Ren J, Guo J, Qian W, Yuan H, Hao X, Jingjing H (2019) Building an effective intrusion detection system by using hybrid data optimization based on machine learning algorithms. Secur Commun Networks 2019:1–11
Bhola J, Soni S, Cheema GK (2020) Genetic algorithm based optimized leach protocol for energy efficient wireless sensor networks. J Ambient Intell Humaniz Comput 11(3):1281–1288
Gauthama Raman MR, Somu N, Kirthivasan K, Liscano R, Shankar Sriram VS (2017) An efficient intrusion detection system based on hypergraph—genetic algorithm for parameter optimization and feature selection in support vector machine. Knowledge-Based Syst 134:1–12
Dash L, Pattanayak BK, Mishra SK, Sahoo KS, Jhanjhi NZ, Baz M, Masud M (2022) A Data aggregation approach exploiting spatial and temporal correlation among sensor data in wireless sensor networks. Electronics 11(7):989
Hosseini S, Zade BMH (2020) New hybrid method for attack detection using combination of evolutionary algorithms, SVM, and ANN. Comput Netw 173:107168
Zhao X, Huang G, Mousoli R (2020) A multi-threading solution to multimedia traffic in NIDS based on hybrid genetic algorithm. Int J Netw Secur 22(3):427–436
Hsu CM, Azhari MZ, Hsieh HY, Prakosa SW, Leu JS (2020) Robust network intrusion detection scheme using long-short term memory based convolutional neural networks. Mob Networks Appl 20:1137–1144
Prithi S (2021) Sumathi S (2021) Automata based hybrid PSO–GWO algorithm for secured energy efficient optimal routing in wireless sensor network. Wirel Pers Commun 117(2):545–559
Thangaramya K, Kulothungan K, Indira Gandhi S, Selvi M, Santhosh Kumar SVN, K. Arputharaj K, (2020) Intelligent fuzzy rule-based approach with outlier detection for secured routing in WSN. Soft Comput 24(21):16483–16497
Selvi M, Velvizhy P, Ganapathy S, Nehemiah HK, Kannan A (2019) A rule based delay constrained energy efficient routing technique for wireless sensor networks. Cluster Comput 22(s5):10839–10848
Santhosh Kumar SVN, Selvi M, Gayathri A, Ruby D, Kannan A (2019) Energy efficient rule based intelligent routing using fitness functions in wireless sensor networks. Int J Innov Technol Explor Eng 8(12):5414–5420
Thangaramya K, Kulothungan K, Logambigai R, Selvi M, Ganapathy S, Kannan A (2019) Energy aware cluster and neuro-fuzzy based routing algorithm for wireless sensor networks in IoT. Comput Netw 151:211–223
Rajesh Kanna P, Santhi P (2021) Unified deep learning approach for efficient intrusion detection system using integrated spatial-temporal features. Knowledge-Based Syst 226:107132
Wang X, Yin S, Li H, Wang J, Teng L (2020) A network intrusion detection method based on deep multi-scale convolutional neural network. Int J Wirel Inf 27(4):503–517
Haider W, Hu J, Slay J, Turnbull BP, Xie Y (2017) Generating realistic intrusion detection system dataset based on fuzzy qualitative modeling. J Netw Comput Appl 87:185–192
Moraboena S, Ketepalli G, Ragam P (2020) A deep learning approach to network intrusion detection using deep autoencoder. Rev d’Intelligence Artif 34(4):457–463
Tavallaee M, Bagheri E, Lu W, Ghorbani AA (2009) A detailed analysis of the KDD CUP 99 data set. In: proceedings of the IEEE symposium on computational intelligence for security and defense applications, pp 1–6. https://doi.org/10.1109/CISDA.2009.5356528
Wang Z (2018) Deep learning-based intrusion detection with adversaries. IEEE Access 6:38367–38384
Behera S, Pradhan A, Dash R (2018) Deep neural network architecture for anomaly based intrusion detection system. In: proceedings of the IEEE international conference on signal processing and integrated networks (SPIN), pp 270–274. https://doi.org/10.1109/SPIN.2018.8474162
Mishra P, Varadharajan V, Tupakula U, Pilli ES (2019) A detailed investigation and analysis of using machine learning techniques for intrusion detection. IEEE Commun Surv Tutorials 21(1):686–728
Yin M, Li X, Zhang Y, Wang S (2019) On the mathematical understanding of ResNet with Feynman path integral. arXiv preprint arXiv:1904.07568
Zhang B, Zou G, Qin D, Ni Q, Li MH, M, (2022) RCL-Learning: ResNet and convolutional long short-term memory-based spatiotemporal air pollutant concentration prediction model. Expert Syst Appl 207:118017
Ricardo K (2020) Schrödinger’s original struggles with a complex wave function. Am J Phys 88(6):433–438
Schrödinger E (1926) An undulatory theory of the mechanics of atoms and molecules. Phys Rev 28(6):1049
Feynman R (1948) Space-time approach to non-relativistic quantum mechanics. Rev Mod Phys 20(2):367–387
Wang Y, Li Z (2021) Inverse problem of nonlinear Schrodinger equation as learning of convolutional neural network. CoRR abs/2107.08593
Subramani S, Selvi M (2023) Intrusion detection system using RBPSO and fuzzy neuro-genetic classification algorithms in wireless sensor networks. Int J Inf Secur 20(3–4):439–461
Selvi M, Logambigai R, Ganapathy S, Sai Ramesh L, Khanna Nehemiah H, Arputharaj K (2016) Fuzzy temporal approach for energy efficient routing in WSN. In: Proceedings of the international conference on informatics and analytics, ACM, pp 1–5. https://doi.org/10.1145/2980258.2982109
Heinzelman WB, Chandrakasan AP, Balakrishnan H (2002) An application-specific protocol architecture for wireless microsensor networks. IEEE Trans Wirel Commun 1(4):660–670
Logambigai R, Kannan A (2016) Fuzzy logic based unequal clustering for wireless sensor networks. Wirel Netw 22:945–957
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
There is no conflict of interest for the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Subramani, S., Selvi, M. Intelligent IDS in wireless sensor networks using deep fuzzy convolutional neural network. Neural Comput & Applic 35, 15201–15220 (2023). https://doi.org/10.1007/s00521-023-08511-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-023-08511-2