Abstract
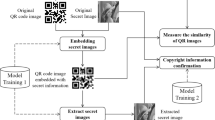
Traceability via quick response (QR) codes is regarded as a clever way to learn specifics about a product’s history, from its creation to its transit and preservation before reaching consumers. The QR code can, however, be easily copied and faked. Therefore, we suggest a novel strategy to prevent tampering with this code. The method is divided into two primary phases: concealing a security element in the QR code and determining how similar the QR code on the goods is to the real ones. For the first problem, error-correcting coding is used to encode and decode the secret feature in order to manage faults in noisy communication channels. A deep neural network is used to both conceal and extract the information encoded in a QR code, and the suggested network creates watermarked QR code images with good quality and noise tolerance. The network has the ability to be resilient to actual distortions brought on by the printing and photographing processes. In order to measure the similarity of QR codes, we create neural networks based on the Siamese network design. To assess whether a QR code is real or fraudulent, the hidden characteristic extracted from the acquired QR code and the outcome of QR code similarity estimation are merged. With an average accuracy of 98%, the proposed technique performs competitively and has been used in practice for QR code authentication.













Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Data availability
The datasets analyzed during the current study are available in the Logo-2K+ (https://github.com/msn199959/Logo-2k-plus-Dataset) and MIRFLICKR (https://press.liacs.nl/mirflickr/) repository. Besides, part of the watermarked QR code dataset generated during the research is not publicly available due to privacy but is available from the corresponding author on reasonable request.
References
Malla B, Dugar A (2016) Product authentication using QR codes: a mobile application to combat counterfeiting. Wirel Pers Commun 90:381–398
Wan S et al (2019) Multiple security anti-counterfeit applications to QR code payment based on visual secret sharing and QR code. Math Biosci Eng 16:6367–6385
Xie S, Tan H-Z (2021) An anti-counterfeiting architecture for traceability system based on modified two-level quick response codes. Electronics 10(3):320
Tran T, Hong S (2015) Rfid anti-counterfeiting for retailing systems. J Appl Math Phys 03:1–9
Lancaster I (2009) Anti-counterfeiting holograms 117:24–25
https://temchonggiavietnam.com/tem-chong-hang-gia/tem-chong-hang-gia-bo-cong-an/
Yiu NCK (2021) Decentralizing supply chain anti-counterfeiting systems using blockchain technology. Correction 13(4):1
Yiu NCK (2016). An nfc-enabled anti-counterfeiting system for wine industry. CoRR abs/1601.06372
http://www.qrcodestickers.org/about-qr-codes/positive-negative-aspects-of-qr-codes.html
Cu VL, Burie JC, Ogier JM (2018) Document images watermarking for security issue using fully convolutional networks, pp 1091–1096
Cu V, Burie J-C, Ogier J-M, Liu C-L (2019) A robust data hiding scheme using generated content for securing genuine documents, pp 787–792
Cu V, Burie J-C, Ogier J-M, Liu C-L (2019) Hiding security feature into text content for securing documents using generated font, pp 1214–1219
Cu V, Nguyen T, Burie J-C, Ogier J-M (2020) A robust watermarking approach for security issue of binary documents using fully convolutional networks. Int J Doc Anal Recognit 23:219–239
Wu P, Yang Y, Li X (2018). Stegnet: mega image steganography capacity with deep convolutional network. 10(6): 54
Zhu J, Kaplan R, Johnson J, Fei-Fei L (2018). Hidden: hiding data with deep networks, pp 682-697
Luo X, Zhan R, Chang H, Yang F, Milanfar P (2020) Distortion agnostic deep watermarking, pp 13545–13554
Wengrowski E, Dana K (2019) Light field messaging with deep photographic steganography, pp 1515–1524
Appalaraju S, Chaoji V (2017) Image similarity using deep cnn and curriculum learning. ArXiv abs/1709.08761
Yuan X, Liu Q, Long J, Hu L, Wang Y (2019) Deep image similarity measurement based on the improved triplet network with spatial pyramid pooling. Information 10:129
Dong X, Shen J (2018) Triplet loss in siamese network for object tracking, pp 459–474
Bohush R, Ablameyko S, Adamovskiy E, Savca D (2020) Image similarity estimation based on ratio and distance calculation between features. Pattern Recognit Image Anal 30:147–159
Alshowaish H, Al-Ohali Y, Al-Nafjan A (2022) Trademark image similarity detection using convolutional neural network. Appl Sci 12:1752
Cu VL, Burie JC, Ogier JM (2018) Stable regions and object fill-based approach for document images watermarking, pp 181–186
Cu VL, Burie JC, Ogier JM (2018) Watermarking for security issue of handwritten documents with fully convolutional networks, pp 303–308
Baluja S (2017) Hiding images in plain sight: deep steganography, pp 2066-2076
Zhang KA, Cuesta-Infante A, Xu L, Veeramachaneni K (2019) Steganogan: high capacity image steganography with gans. CoRR abs/1901.03892
Ahmadi SBB, Zhang G, Rabbani M, Boukela L, Jelodar H (2021) An intelligent and blind dual color image watermarking for authentication and copyright protection. Appl Intell 51:1701–1732
Zhang J et al (2022) Deep model intellectual property protection via deep watermarking. IEEE Trans Pattern Anal Mach Intell 44:4005–4020
Hasinoff SW (2014) Photon, Poisson Noise, pp 608-610
Vinh Loc CuJ-CB, Nguyen Trac, Ogier J-M (2020) A robust watermarking approach for security issue of binary documents using fully convolutional networks. Int J Doc Anal Recognit 23:219–239
Cu VL, Burie JC, Ogier JM, Liu CL (2019) A robust data hiding scheme using generated content for securing genuine documents, pp 787–792
Cu VL, Burie JC, Ogier JM, Liu CL (2019) Hiding security feature into text content for securing documents using generated font, pp 1214–1219
Xiao C, Zhang C, Zheng C (2018) Fontcode: embedding information in text documents using glyph perturbation. ACM Trans Graph 37:1–16
Xiao C, Zhang C, Zheng C (2017) Fontcode: embedding information in text documents using glyph perturbation. Correction 37:1–16
Zhu J, Kaplan R, Johnson J, Fei-Fei L (2018) Hidden: hiding data with deep networks. 11219: 682–697
He K, Zhang X, Ren S, Sun J (2016) Deep residual learning for image recognition, pp 770–778
Schroff F, Kalenichenko D, Philbin J (2015) Facenet: a unified embedding for face recognition and clustering, pp 815–823
https://github.com/msn199959/Logo-2k-plus-Dataset
Huiskes MJ, Lew MS (2008) The mir flickr retrieval evaluation
Bose R, Ray-Chaudhuri D (1960) On a class of error correcting binary group codes. Inf Control 3:68–79
Acknowledgments
This study is funded in part by the Can Tho University, Code: T2022-126.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Loc, C.V., Viet, T.X., Viet, T.H. et al. A real noise resistance for anti-tampering quick response code. Neural Comput & Applic 36, 12791–12807 (2024). https://doi.org/10.1007/s00521-024-10036-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-024-10036-1