Abstract
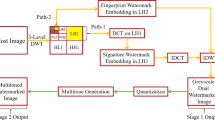
The classical fingerprint recognition system can be compromised at the database and the sensor. Therefore, to beef up security of the fingerprint recognition system, reversible watermarking is proposed to protect these two points. Reversible watermarks thwart manipulations, \({viz}\)., copy and replay attacks and ensure that native fingerprint recognition accuracy remains unaffected. Fingerprint-dependent watermark \(W_1\) authenticates the database and shields it against the copy attack. The second watermark \(W_2\) verifies fingerprint captured by the sensor and foil replay attack. \(W_2\) is derived from the higher order moments of the fingerprint. Divergence in the computed and extracted watermarks indicates loss of authenticity. The experimental results validate proposed hypothesis.










Similar content being viewed by others
References
Acharya, T., Tsai, P.S.: JPEG2000 Standard for Image Compression: Concepts, Algorithms and VLSI Architectures. Wiley, New York (2005)
Baldisserra, D., Franco, A., Maio, D., Maltoni, D.: Fake fingerprint detection by odor analysis. In: Advances in Biometrics, pp. 265–272. Springer, Berlin (2005)
Bartlow, N., Kalka, N., Cukic, B., Ross, A.: Protecting iris images through asymmetric digital watermarking. In: 2007 IEEE Workshop on Automatic Identification Advanced Technologies, pp. 192–197. IEEE, New York (2007)
Bezdek, J.C., Pal, S.K.: Fuzzy Models for Pattern Recognition, vol. 267. IEEE press, New York (1992)
Celik, M.U., Sharma, G., Tekalp, A.M., Saber, E.: Reversible data hiding. In: Proceedings of 2002 International Conference on Image Processing, vol. 2, pp. II-157–II-160. IEEE, New York (2002)
Chen, H., Reid, E., Sinai, J., Silke, A., Ganor, B.: Terrorism Informatics: Knowledge Management and Data Mining for Homeland Security, vol. 18. Springer, Berlin (2008)
E-governance standards: Standards for e-governance applications. http://egovstandards.gov.in/standardsandFramework/biometric-standards/fingerprint_image_data_standard_ver1.0.pdf/view (2008)
El Bakrawy, L.M., Ghali, N.I., Hassanien, A.E., Peters, J.F.: Strict authentication of multimodal biometric images using near sets. In: Soft Computing in Industrial Applications, pp. 249–258. Springer, Berlin (2011)
Fatindez-Zanuy, M.: On the vulnerability of biometric security systems. IEEE Aerosp. Electron. Syst. Mag. 3–8 (2004)
Fingerprint database: Fvc 2000. http://bias.csr.unibo.it/fvc2000/databases.asp (2000)
Fingerprint database: Fvc 2002. http://bias.csr.unibo.it/fvc2002/databases.asp (2002)
Fingerprint database: Fvc 2004. http://bias.csr.unibo.it/fvc2004/databases.asp (2004)
Fingerprint verification competition: Fvc 2006. http://bias.csr.unibo.it/fvc2006/ (2006)
Gonzalez, R.C., Woods, R.E., Eddins, S.L.: Digital Image Processing Using MATLAB. Pearson Education, India (2004)
Gupta, A.K., Raval, M.S.: A robust and secure watermarking scheme based on singular values replacement. Sadhana 37(4), 425–440 (2012)
Homelend Security: Ntas guide. http://www.dhs.gov/xlibrary/assets/ntas/ntas-public-guide.pdf (2011)
Huber, R., Stögner, H., Uhl, A.: Semi-fragile watermarking in biometric systems: template self-embedding. In: Computer Analysis of Images and Patterns, pp. 34–41. Springer, Berlin (2011)
Hwang, J., Kim, J., Choi, J.: A reversible watermarking based on histogram shifting. In: Digital Watermarking, pp. 348–361. Springer, Berlin (2006)
Jain, A.K., Feng, J.: Latent fingerprint matching. IEEE Trans Pattern Anal Mach Intell 33(1), 88–100 (2011)
Jain, A.K., Kumar, A.: Biometrics of next generation: an overview. In: Second Generation Biometrics (2010)
Jain, A.K., Prabhakar, S., Pankanti, S.: A filterbank-based representation for classification and matching of fingerprints. In: International Joint Conference on Neural Networks 1999, IJCNN’99, vol. 5, pp. 3284–3285. IEEE, New York (1999)
Joshi, M., Joshi, V.B., Raval, M.S.: Multilevel semi-fragile watermarking technique for improving biometric fingerprint system security. In: Intelligent Interactive Technologies and Multimedia, pp. 272–283. Springer, Berlin (2013)
Khan, M.K., Zhang, J., Tian, L.: Protecting biometric data for personal identification. In: Advances in Biometric Person Authentication, pp. 629–638. Springer, Berlin (2005)
Komninos, N., Dimitriou, T.: Protecting biometric templates with image watermarking techniques. In: Advances in Biometrics, pp. 114–123. Springer, Berlin (2007)
Kutter, M., Voloshynovskiy, S.V., Herrigel, A.: Watermark copy attack. In: Electronic Imaging, pp. 371–380. International Society for Optics and Photonics (2000)
Li, C., Wang, Y., Ma, B., Zhang, Z.: Multi-block dependency based fragile watermarking scheme for fingerprint images protection. Multimed. Tools Appl. 64(3), 757–776 (2013)
Lin, C.Y., Chang, S.F.: A robust image authentication method distinguishing jpeg compression from malicious manipulation. IEEE Trans Circuits Syst. Video Technol. 11(2), 153–168 (2001)
Liu, R., Tan, T.: An svd-based watermarking scheme for protecting rightful ownership. IEEE Trans. Multimed. 4(1), 121–128 (2002)
Ma, B., Wang, Y., Li, C., Zhang, Z., Huang, D.: Secure multimodal biometric authentication with wavelet quantization based fingerprint watermarking. Multimed. Tools Appl. 1–30 (2013)
MI5 Security Service: Threat levels. https://www.mi5.gov.uk/home/the-threats/terrorism/threat-levels.html (2014)
NSTC, Committee on Technology, Committee on Homeland and National Security, Subcommittee on Biometrics: Fingerprint recognition. http://www.biometrics.gov/documents/fingerprintrec.pdf (2006)
Prabhakar, S.: Fingerprint classification and matching using a filterbank. PhD thesis, Michigan State University (2001)
Ratha, N.K., Bolle, R.M.: Effect of controlled image acquisition of fingerprint matching. In: International Conference on Pattern Recognition, vol. 2, pp. 1659–1659. IEEE Computer Society (1998)
Raval, M.S.: A secure steganographic technique for blind steganalysis resistance. In: Seventh International Conference on Advances in Pattern Recognition 2009, ICAPR’09, pp. 25–28. IEEE, New York (2009)
Sangalli, A.: The importance of being fuzzy: and other insights from the border between math and computers. Princeton University Press, New Jersey (1998)
Sheikh, H.R., Bovik, A.C.: Image information and visual quality. IEEE Trans. Image Process. 15(2), 430–444 (2006)
Vatsa, M., Singh, R., Noore, A., Houck, M.M., Morris, K.: Robust biometric image watermarking for fingerprint and face template protection. IEICE Electron. Express 3(2), 23–28 (2006)
Wang, D.S., Li, J.P., Wen, X.Y.: Biometric image integrity authentication based on SVD and fragile watermarking. In: Congress on Image and Signal Processing 2008, CISP’08, vol. 5, pp. 679–682. IEEE, New York (2008)
Watson, C., Wilson, C.: Effect of image size and compression on one-to-one fingerprint matching. US Department of Commerce, National Institute of Standards and Technology (2005)
Whitelam, C., Osia, N., Bourlai, T.: Securing multimodal biometric data through watermarking and steganography. In: 2013 IEEE International Conference on Technologies for Homeland Security (HST), pp. 61–66. IEEE, New York (2013)
Xiong, Z., Ramchandran, K., Orchard, M.T., Zhang, Y.Q.: A comparative study of DCT-and wavelet-based image coding. IEEE Trans. Circuits Syst. Video Technol. 9(5), 692–695 (1999)
Zheng, D., Liu, Y., Zhao, J., Saddik, A.E.: A survey of RST invariant image watermarking algorithms. ACM Comput. Surv. (CSUR) 39(2), 5 (2007)
Zhou, B., Chen, J.: A geometric distortion resilient image watermarking algorithm based on SVD. J. Image Graph. 4, 022 (2004)
Acknowledgments
The authors would like to thank the Board of Research in Nuclear Science (BRNS), Department of Atomic Energy, Government of India for providing a grant to carry out this research work.
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by T. Haenselmann.
Rights and permissions
About this article
Cite this article
Joshi, V.B., Raval, M.S., Gupta, D. et al. A multiple reversible watermarking technique for fingerprint authentication. Multimedia Systems 22, 367–378 (2016). https://doi.org/10.1007/s00530-015-0465-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00530-015-0465-6