Abstract
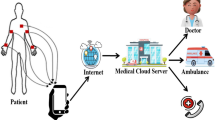
Wireless sensor networks (WSNs) are fast developed and widely used in many applications. One of the most important applications is wireless medical sensor network (WMSN) which makes modern health-care more popular. The doctor can get the patient’s physiological data collected by special sensors deployed on or in the patient’s body in real time with the mobile devices via the wireless communication channel. The collected data are important and should be confidential. So security measures are considered in the process of communication. Recently, He et al. (Multimed Syst, 21(1), 49–60, 2015) proposed a new two-factor authentication scheme for health-care with WMSNs and claimed it to be secure. But we find that it is vulnerable to the off-line guessing attack, the user impersonation attack, and the sensor node capture attack. Moreover, we present an improved scheme to overcome the disadvantages. Through the formal verification with Proverif and the analysis presented by us, our scheme is secure. It is more practical for applications through the comparison between some recent schemes for WMSNs.


Similar content being viewed by others
References
Chen, T.H., Shih, W.K.: A robust mutual authentication protocol for wireless sensor networks. Etri J. 32(5), 704–712 (2010)
Das, M.L.: Two-factor user authentication in wireless sensor networks. Wirel. Commun. IEEE Trans. 8(3), 1086–1090 (2009)
Dolev, D., Yao, A.C.: On the security of public key protocols. Inf. Theory IEEE Trans. 29(2), 198–208 (1983)
He, D., Zeadally, S.: Authentication protocol for an ambient assisted living system. Commun. Mag. IEEE 53(1), 71–77 (2015)
He, D., Kumar, N., Chen, J., Lee, C.C., Chilamkurti, N., Yeo, S.S.: Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimed. Syst. 21(1), 49–60 (2015). doi:10.1007/s00530-013-0346-9
He, D., Kumar, N., Chilamkurti, N.: A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inf. Sci. 321, 236–277 (2015). doi:10.1016/j.ins.2015.02.010
He, D., Zeadally, S., Wu, L.: Certificateless public auditing scheme for cloud-assisted wireless body area networks. IEEE Syst. J. (2015). doi:10.1109/JSYST.2015.2428620
Hsiao, T.C., Liao, Y.T., Huang, J.Y., Chen, T.S., Horng, G.B.: An authentication scheme to healthcare security under wireless sensor networks. J. Med. Syst. 36(6), 3649–3664 (2012). doi:10.1007/s10916-012-9839-x
Hu, F., Jiang, M., Wagner, M., Dong, D.C.: Privacy-preserving telecardiology sensor networks: toward a low-cost portable wireless hardware/software codesign. Inf. Technol. Biomed. IEEE Trans. 11(6), 619–627 (2007)
Huang, H.F., Chang, Y.F., Liu, C.H.: Enhancement of two-factor user authentication in wireless sensor networks. In: Intelligent information hiding and multimedia signal processing (IIH-MSP), sixth International Conference on, IEEE, pp. 27–30 (2010)
Karuppiah, M., Saravanan, R.: A secure remote user mutual authentication scheme using smart cards. J. Inf. Secur. Appl. 19(4), 282–294 (2014)
Karuppiah, M., Saravanan, R.: A secure authentication scheme with user anonymity for roaming service in global mobility networks. Wirel. Pers. Commun. (2015). doi:10.1007/s11277-015-2524-x
Khan, M.K., Alghathbar, K.: Cryptanalysis and security improvements of two-factor user authentication in wireless sensor networks. Sensors 10(3), 2450–2459 (2010)
Khan, M.K., Kumari, S.: An improved user authentication protocol for healthcare services via wireless medical sensor networks. Int. J. Distrib. Sens. Netw. (2014)
Kocher, P., Jaffe, J., Jun, B.: Differential power analysis. In: Advances in Cryptology-CRYPTO99. Springer, pp. 388–397 (1999)
Kumar, P., Lee, S.G., Lee, H.J.: E-sap: Efficient-strong authentication protocol for healthcare applications using wireless medical sensor networks. Sensors 12(2), 1625–1647 (2012)
Kumari, S., Gupta, M.K., Khan, M.K., Li, X.: An improved timestamp-based password authentication scheme: comments, cryptanalysis, and improvement. Secur. Commun. Netw. 7(11), 1921–1932 (2014)
Kumari, S., Khan, M.K., Atiquzzaman, M.: User authentication schemes for wireless sensor networks: a review. Ad Hoc Netw. 27, 159–194 (2015)
Le, X.H., Khalid, M., Sankar, R., Lee, S.: An efficient mutual authentication and access control scheme for wireless sensor networks in healthcare. J. Netw. 6(3), 355–364 (2011)
Li, X., Xiong, Y., Ma, J., Wang, W.: An efficient and security dynamic identity based authentication protocol for multi-server architecture using smart cards. J. Netw. Comput. Appl. 35(2), 763–769 (2012)
Li, X., Ma, J., Wang, W., Xiong, Y., Zhang, J.: A novel smart card and dynamic id based remote user authentication scheme for multi-server environments. Math. Comput. Model. 58(1), 85–95 (2013)
Li, X., Niu, J., Khan, M.K., Liao, J.: An enhanced smart card based remote user password authentication scheme. J. Netw. Comput. Appl. 36(5), 1365–1371 (2013)
Li, X., Niu, J., Kumari, S., Liao, J., Liang, W., Khan, M.K.: A new authentication protocol for healthcare applications using wireless medical sensor networks with user anonymity. Secur. Commun. Netw. (2015)
Mangard, S., Oswald, E., Standaert, F.X.: One for all-call for one: unifying standard differential power analysis attacks. IET Inf. Secur. 5(2), 100–110 (2011)
Messerges, T.S., Dabbish, E.A., Sloan, R.H.: Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 51(5), 541–552 (2002)
Nyang, D., Lee, M.K.: Improvement of das’s two-factor authentication protocol in wireless sensor networks. IACR Cryptol. ePrint Arch. 2009, 631 (2009)
Raja, K.N., Beno, M.M.: On securing wireless sensor network-novel authentication scheme against dos attacks. J. Med. Syst. 38(10), 1–5 (2014). doi:10.1007/s10916-014-0084-3
Wang, D., Wang, P.: On the anonymity of two-factor authentication schemes for wireless sensor networks: attacks, principle and solutions. Comput. Netw. 73, 41–57 (2014)
Wang, D., Wang, P.: Understanding security failures of two-factor authentication schemes for real-time applications in hierarchical wireless sensor networks. Ad Hoc Netw. 20, 1–15 (2014)
Wang, D., He, D., Wang, P., Chu, C.: Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Dependable and Secure Computing (2014). doi:10.1109/TDSC.2014.2355850
Wu, F., Xu, L.: Security analysis and improvement of a privacy authentication scheme for telecare medical information systems. J. Med. Syst. 37(4), 1–9 (2013)
Wu, F., Xu, L., Kumari, S., Li, X.: A novel and provably secure biometrics-based three-factor remote authentication scheme for mobile client-server networks. Comput Elect. Eng. (2015). doi:10.1016/j.compeleceng.2015.02.015
Xu, L., Wu, F.: Cryptanalysis and improvement of a user authentication scheme preserving uniqueness and anonymity for connected health care. J. Med. Syst. 39(2), 1–9 (2015)
Xu, L., Wu, F.: An improved and provable remote user authentication scheme based on elliptic curve cryptosystem with user anonymity. Secur. Commun. Netw. 8(2), 245–260 (2015). doi:10.1002/sec.977
Yoo, S.G., Park, K.Y., Kim, J.: A security-performance-balanced user authentication scheme for wireless sensor networks. Int. J. Distrib. Sens. Netw. (2012)
Acknowledgments
The authors thank the valuable work of the editors and the anonymous reviewers. This research is supported by Fujian Education and Scientific Research Program for Young and Middle-aged Teachers under Grant No. JA14369, the National Natural Science Foundation of China under Grant No. 61300220, and it is also supported by PAPD and CICAEET.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Communicated by L. Zhou.
Rights and permissions
About this article
Cite this article
Wu, F., Xu, L., Kumari, S. et al. An improved and anonymous two-factor authentication protocol for health-care applications with wireless medical sensor networks. Multimedia Systems 23, 195–205 (2017). https://doi.org/10.1007/s00530-015-0476-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00530-015-0476-3