Abstract
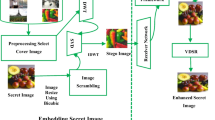
Nowadays, highly sensitive medical images are vulnerable to data threats and privacy attacks. They must be kept secure while transmitting them across insecure channels precisely for this purpose. The robust image steganography is focused on this work by exploiting Redundant Integer Wavelet Transform (RIWT), Laplacian Pyramid, Arnold scrambling and Histogram shifting algorithm to facilitate secure communication of secret images in the context. Stego images thus generated are subjected to a deep learning approach to assess if it can be classified as a cover or not. If not, the HS parameter is modified to generate stego images in such a way to classify it as a cover image. Thus it is difficult to suspect the existence of a secret image by the Human Visual System (HVS). The efficiency of our method is analyzed by comparing it with related methods present in the literature. Average NCC values between the original secret image and the extracted secret image are 0.8917 which is higher than the schemes in the literature. Average PSNR values of the stego image are 36.375 even when the embedding rate is increased to 4 bits per pixel. The analysis was done on security and robustness also reveals better results. From the experimental analysis, it is proved that the proposed method is superior to the related methods of the literature.













Similar content being viewed by others
References
Kishor, S. N., GN Kodanda Ramaiah, and S. A. K. Jilani (2016). A review on steganography through multimedia. 2016 International Conference on Research Advances in Integrated Navigation Systems (RAINS). IEEE.
Jero, S. Edward, Palaniappan Ramu, and S. Ramakrishnan(2014). Discrete wavelet transform and singular value decomposition based ECG steganography for secured patient information transmission. Journal of medical systems 38.10 132.
Wang, W., Si, M., Pang, Y., Ran, P., Wang, H., Jiang, X., Liu, Y., Wu, J., Wu, W., Chilamkurti, N., Jeon, G.: An encryption algorithm based on combined chaos in body area networks. Comput. Electr. Eng. 65, 282–291 (2018)
Muhammad, K., et al.: Image steganography using uncorrelated color space and its application for security of visual contents in online social networks. Future Gener. Comput. Syst. 86, 951–960 (2018)
Cheddad, A., et al.: Digital image steganography: survey and analysis of current methods. Signal Process. 90(3), 727–752 (2010)
Sreekutty, M. S., Baiju, P.S.: Security enhancement in image steganography for medical integrity verification system. In: 2017 International Conference on Circuit, Power and Computing Technologies (ICCPCT). IEEE (2017)
Altaay, A. A. Jabbar, S. B. S., Mazdak Z.: An introduction to image steganography techniques. In: 2012 International Conference on Advanced Computer Science Applications and Technologies (ACSAT). IEEE (2012)
Shaik, A., Thanikaiselvan, V., Amitharajan, R.: Data security through data hiding in images: a review. J. Artif. Intell. 10(1), 1–21 (2017)
Arunkumar, S., Subramaniyaswamy, S., et al.: RIWT and QR factorization based hybrid robust image steganography using block selection algorithm for IoT devices. J. Intell. Fuzzy Syst. 36(5), 4265–4276 (2019)
Arunkumar, S., Subramaniyaswamy, S., et al.: SVD-based robust image steganographic scheme using RIWT and DCT for secure transmission of medical images. Measurement 139, 426–437 (2019)
Zhang, Yi, et al.: On the fault-tolerant performance for a class of robust image steganography. Signal Process. 146, 99–111 (2018)
Arunkumar, S., Subramaniyaswamy, S., et al.: Meta-data based secret image sharing application for different sized biomedical images. Biomed. Res. 29, S394–S398 (2018)
Bandyopadhyay, D., et al.: A novel secure image steganography method based on chaos theory in spatial domain. Int. J. Secur. Priv. Trust Manag. IJSPTM 3(1), 11–22 (2014)
Rabie, T., Baziyad, M.: Visual fidelity without sacrificing capacity: an adaptive Laplacian pyramid approach to information hiding. J. Electron. Imaging 26(6), 063001 (2017)
Subhedar, M.S., Mankar, V.H.: Current status and key issues in image steganography: a survey. Comput. Sci. Rev. 13, 95–113 (2014)
Peng, F., Li, X., Yang, B.: Adaptive reversible data hiding scheme based on integer transform. Signal Process. 92(1), 54–62 (2012)
Qin, C., Chang, C.C., Huang, Y.H., Liao, L.T.: An inpainting-assisted reversible steganographic scheme using a histogram shifting mechanism. IEEE Trans. Circuits Syst. Video Technol. 23(7), 1109–1118 (2012)
Rabie, T., Baziyad, M., Kamel, I.: Enhanced high capacity image steganography using discrete wavelet transform and the Laplacian pyramid. Multimed. Tools Appl. 77(18), 23673–23698 (2018)
Ni, Z., Shi, Y. Q., Ansari, N., Su, W.: Reversible data hiding. In: IEEE Transactions on Circuits and Systems for Video Technology, pp. 354–362 (2006)
Hussain, S., Keung, J., Akhunzada, A., Ahmad, A., Khan, A.A., Cuomo, S., Piccialli, F., Jeon, G.: Implications of deep learning for the automation of design patterns organization. J. Parallel Distrib. Comput. 117, 256–266 (2018)
Jan, B., Farman, H., Khan, M., Ul Islam, I., Ali, S., Ahmad, A., Jeon, G.: Deep learning in big data analytics: a comparative study. Comput. Electr. Eng. 75, 275–287 (2019)
Baby, D., Thomas, J., Augustine, G., George, E., Michael, N.R.: A novel DWT based image securing method using steganography. Proc. Comput. Sci. 46, 612–618 (2015)
Kini, N.G., Kini, V.G.: A secured steganography algorithm for hiding an image in an image. Integrated Intelligent Computing, Communication and Security, pp. 539–546. Springer, Singapore (2019)
Wang, J., Wu, J., Wu, Z., Anisetti, M., Jeon, G.: Bayesian method application for color demosaicking. SPIE Opt. Eng. 57(5), 053102 (2018)
Wu, W., Yang, X., Pang, Y., Peng, J., Jeon, G.: A multifocus image fusion method by using hidden Markov model. Opt. Commun. 287, 63–72 (2013)
Reddy, H.M., Raja, K.B.: High capacity and security steganography using discrete wavelet transform. Int. J. Comput. Sci. Secur. IJCSS 3(6), 462 (2009)
Nag, A., Biswas, S., Sarkar, D., Sarkar, P.P.: A novel technique for image steganography based on DWT and Huffman encoding. Int. J. Comput. Sci. Secur. IJCSS 4(6), 497–610 (2011)
Latef, A.A.: Color image steganography based on discrete wavelet and discrete cosine transforms. Ibn Al-Haitham J. Pure Appl. Sci. 24(3), 296–302 (2011)
Dey, N., Roy, A.B., & Dey, S.: A novel approach of color image hiding using RGB color planes and DWT. arXiv preprint arXiv:1208.0803 (2012)
Jeon, G., Park, S.J., Fang, Y., Anisetti, M., Bellandi, V., Damiani, E., Jeong, J.: Specification of efficient block matching scheme for motion estimation in video compression. SPIE Opt. Eng. 48(12), 127005 (2009)
Shejul, A.A., Kulkarni, U.L.: A secure skin tone based steganography using wavelet transform. Int. J. Comput. Theory Eng. 3(1), 16 (2011)
Kaur, G., Kochhar, A.: Transform domain analysis of image steganography. Int. J. Sci. Emerg. Technol. Latest Trends 6(1), 29–37 (2013)
Singh, A.K., Dave, M., Mohan, A.: Hybrid technique for robust and imperceptible dual watermarking using error correcting codes for application in telemedicine. IJESDF 6(4), 285–305 (2014)
Nagpal, S., Bhushan, S., Mahajan, M.: An enhanced digital image watermarking scheme for medical images using neural network, DWT and RSA. Int. J. Mod. Educ. Comput. Sci. 8(4), 46 (2016)
Thakkar, F.N., Srivastava, V.K.: A blind medical image watermarking: DWT-SVD based robust and secure approach for telemedicine applications. Multimed. Tools Appl. 76(3), 3669–3697 (2017)
Kalita, M., Tuithung, T., Majumder, S.: A new steganography method using integer wavelet transform and least significant bit substitution. Comput. J. 62, 1639–1655 (2019)
Rathore, M.M., Paul, A., Ahmad, A., Anisetti, M., Jeon, G.: Hadoop-based intelligent care system (HICS): analytical approach for big data in IoT. ACM Trans. Internet Technol. 18(1), 1–24 (2017)
Burt, P., Adelson, E.: The Laplacian pyramid as a compact image code. IEEE Trans. Commun. 31(4), 532–540 (1983)
Swain, G., Lenka, S.K.: A hybrid approach to steganography embedding at darkest and brightest pixels. In: 2010 International Conference on Communication and Computational Intelligence (INCOCCI), pp. 529–534. IEEE (2010)
Makbol, N.M., Khoo, B.E.: Robust blind image watermarking scheme based on redundant discrete wavelet transform and singular value decomposition. AEU Int. J. Electron. Commun. 67(2), 102–112 (2013)
Zhang, Z., Wu, L., Gao, S., Sun, H., Yan, Y.: Robust reversible watermarking algorithm based on RIWT and compressed sensing. Arab. J. Sci. Eng. 43(2), 979–992 (2018)
Ye, J., Ni, J., Yi, Y.: Deep learning hierarchical representations for image steganalysis. IEEE Trans. Inf. Forensics Secur. TIFS 12(11), 2545–2557 (2017)
Zhang, Y., Zhang, W., Chen, K., Liu, J., Liu, Y., Yu, N.: Adversarial examples against deep neural network based steganalysis. In: Proceedings of the 6th ACM workshop on information hiding and multimedia security, IH&MMSec'2018, pp. 67–72, Innsbruck, Austria (2018)
Goljan, M., Fridrich, J., Cogranne, R.: Rich model for steganalysis of color images. In: 2014 IEEE International Workshop on Information Forensics and Security (WIFS), pp. 185–190. IEEE (2014)
Ye, J., Ni, J., Yi, Y.: Deep learning hierarchical representations for image steganalysis. IEEE Trans. Inf. Forensics Secur. 12(11), 2545–2557 (2017)
Chen, J., Kang, X., Liu, Y., Wang, Z.J.: Median filtering forensics based on convolutional neural networks. IEEE Signal Process. Lett. 22(11), 1849–1853 (2015)
Lin, C.C., Shiu, P.F.: High capacity data hiding scheme for DCT-based images. J. Inf. Hiding Multimed. Signal Process. 1(3), 220–240 (2010)
Li, F., Mao, Q., Chang, C.C.: Reversible data hiding scheme based on the Haar discrete wavelet transform and interleaving prediction method. Multimed. Tools Appl. 77(5), 5149–5168 (2018)
Shaik, A., Thanikaiselvan, V.: A new image-based hybrid reversible data hiding model using IHWT and RP-PEHM for secured data communication. Circuits Syst. Signal Process. 37(11), 4907–4928 (2018)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sukumar, A., Subramaniyaswamy, V., Ravi, L. et al. Robust image steganography approach based on RIWT-Laplacian pyramid and histogram shifting using deep learning. Multimedia Systems 27, 651–666 (2021). https://doi.org/10.1007/s00530-020-00665-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00530-020-00665-6