Abstract
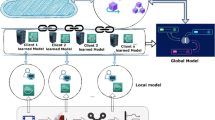
In the field of medical image content protection and security sharing, the introduction of blockchain technology has a problem in that the secret key may be lost and cannot be recovered. Therefore, this paper proposes an authenticable medical image-sharing scheme based on an embedded small shadow QR code and a blockchain framework. First, a small shadow image is obtained by employing a secret image-sharing method based on the Chinese remainder theorem. Then, the shadow image is embedded into a QR code with error correction. This not only ensures the security and integrity of the shadow image transmission in the public channel but also avoids the problem where the secret key is lost and cannot be recovered. Compared with some existing excellent schemes, our scheme adopts a hash bit stream for authentication purposes and employs smart contracts to authenticate and restore secret images, thus reducing the local load. In addition, experiments validate that the recovered secret medical image is lossless and that the cover QR code is more robust and secure. This method is suitable for medical image content protection and security sharing.







Similar content being viewed by others
References
Mcbee, M.P., Wilcox, C.: Blockchain technology: principles and applications in medical imaging. J. Digit. Imaging 33(2), 726–734 (2020)
Langer, S.G., Tellis, W., Canr, C., Daly, M., Erickson, B.: The RSNA image sharing network. J. Digit. Imaging 28(1), 53–61 (2015)
Patel, V.: A framework for secure and decentralized sharing of medical imaging data via blockchain consensus. Health Inform. J. 25(4), 1398–1411 (2018)
Niu, S., Liu, W., Chen, L., Wang, C., Du, X.: Electronic medical record data sharing scheme based on searchable encryption via consortium blockchain. J. Commun. 41(08), 204–214 (2020)
Xu, S.M., Ning, J.T., Li, Y.J., et al.: A secure EMR sharing system with tamper resistance and expressive access control. IEEE Trans. Dependable Secur. Comput. 11(15), 1 (2021)
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612–613 (1979)
Blakley, G. R.: Safeguarding cryptographic keys. In: International Workshop on Managing Requirements Knowledge. IEEE Computer Society, pp. 313–313 (1979)
Thien, C.-C., Lin, J.C.: Secret image sharing. Comput. Graph. 26(5), 765–770 (2002)
Yan, X., Li, J., Pan, Z., Zhong, X., Yang, G.: Multiparty verification in image secret sharing. Inf. Sci. 562(12), 475–490 (2021)
Ateniese, G., Blundo, C., Santis, A.D., Stinson, D.R.: Extended capabilities for visual cryptography. Theor. Comput. Sci. 250(1–2), 143–161 (2001)
Sukumar, A., Subramaniyaswamy, V., Ravi, L., Vijayakumar, V., Indragandhi, V.: Robust image steganography approach based on RIWT-Laplacian pyramid and histogram shifting using deep learning. Multimedia Syst. 27, 651–666 (2021). https://doi.org/10.1007/s00530-020-00665-6
Lu, J., Zhang, W., Deng, Z., Zhang, S., Chang, Y., Liu, X.: Research on information steganography based on network data stream. Neural Comput. Appl. 33(3), 851–866 (2021)
Wu, X., Yang, C.: Invertible secret image sharing with steganography and authentication for AMBTC compressed images. Signal Process. Image Commun. 78(11), 437–447 (2019)
Xiong, L., Zhong, X., Yang, C., Han, X.: Transform domain-based invertible and lossless secret image sharing with authentication. IEEE Trans. Inf. Forensics Secur. 16, 2912–2925 (2021)
Chen, J., Liu, K., Yan, X., Liu, L., Xuan, Z., Tan, L.: Chinese remainder theorem-based secret image sharing with small-sized shadow images. Symmetry 10(8), 340 (2018)
Lu, Y., Sun, Y., Chen, J.R., Zhang, W., Yan, X.: Meaningful secret image sharing scheme with high visual quality based on natural steganography. Mathematics 8(9), 1452 (2020)
Chou, G., Wang, R.: The nested QR code. IEEE Signal Process. Lett. 27, 1230–1234 (2020). https://doi.org/10.1109/LSP.2020.3006375
Yan, X., Lu, Y.: Applying QR code to secure medical management. In: 2018 9th International Conference on Information Technology in Medicine and Education (ITME). IEEE Computer Society, pp. 53–56 (2018). https://doi.org/10.1109/ITME.2018.00023
Jiang, Y., Lu, Y., Yan, X., Liu, L.: Extended secret image sharing with lossless recovery based on Chinese remainder theorem and quick response code. In: IEEE 3rd international conference on image, vision and computing (ICIVC), pp. 678–683 (2018). https://doi.org/10.1109/ITME.2018.00023
Huang, P., Chang, C., Li, Y., Liu, Y.: Enhanced (\(n\), \(n\))-threshold QR code secret sharing scheme based on error correction mechanism. J. Inf. Secur. Appl. 58(11), 102719 (2021)
Xiong, L., Zhong, X., Liu, W., Xiong, N.: QR-3S: a high payload QR code secret sharing system for industrial internet of things in 6G networks. IEEE Trans. Ind. Inform. 17(10), 7213–7222 (2021)
Huang, P., Chang, C., Li, Y.: Efficient access control system based on aesthetic QR code. Pers. Ubiquitous Comput. 22(1), 81–91 (2018)
Li, T., Messer, K.D.: To scan or not to scan: the question of consumer behavior and QR codes on food packages. J. Agric. Resour. Econ. 44(2), 311 (2019)
Ramalingam, N.D., Tran, H.N., Gangopadhyay, A.: As simple as taking a picture-how use of QR codes improved evaluation response rates, documentation, and timeliness. J. Gen. Intern. Med. 35(8), 1615–1616 (2020)
Lin, S., Hu, M., Lee, C.H.: Efficient QR code beautification with high quality visual content. IEEE Trans. Multimedia 17(9), 1515–1524 (2015)
Xu, B., Huang, D., Mi, B.: Research on the application of mobile payment security system based on the internet of things. Concurr. Comput. Pract. Exp. (2020). https://doi.org/10.1002/cpe.5779
Liu, A., Du, X., Wang, N.: Research progress of blockchain technology and its application in information security. J. Softw. 29(7), 2092–2115 (2018)
Pp, A., Lei, P.A., Xi, Z.B., Aj, B.: SolGuard: preventing external call issues in smart contract-based multi-agent robotic systems. Inf. Sci. 579(1), 150–166 (2021)
Zhang, E., Li, M., Du, J., Yiu, S., Jin, G.: Fair hierarchical secret sharing scheme based on smart contract. Inf. Sci. 546(6), 166–176 (2021)
Tan, L., Lu, Y., Yan, X., Liu, L., Zhou, X.: XOR-ed visual secret sharing scheme with robust and meaningful shadows based on QR codes. Multimedia Tools Appl. 79(9), 5719–5741 (2020)
Lin, P.Y.: Distributed secret sharing approach with cheater prevention based on QR code. IEEE Trans. Ind. Inform. 12(1), 384–392 (2016)
Chow, Y.-W., Susilo, W., Yang, G., Phillips, J.G., Pranata, I., Barmawi, A.M.: Exploiting the error correction mechanism in QR codes for secret sharing. In: Australasian Conference on Information Security and Privacy (ACISP), pp. 409–425 (2016). https://doi.org/10.1007/978-3-319-40253-6-25
Patel, R., Lad, K., Patel, M.: Study and investigation of video steganography over uncompressed and compressed domain: a comprehensive review. Multimedia Syst. 27, 985–1024 (2021). https://doi.org/10.1007/s00530-021-00763-z
Yan, X., Liu, L., Li, L.: Robust secret image sharing scheme against noise in shadow images. ACM Trans. Multimedia Comput. Commun. Appl. 17(24), 1–22 (2021)
Wu, X., Yang, C., Zhuang, Y., Hsu, S.C.: Improving recovered image quality in secret image sharing by simple modular arithmetic. Signal Process. Image Commun. 66, 42–49 (2018). https://doi.org/10.1016/j.image.2018.05.001
Wu, X., Yang, C., Yang, Y.: A hybrid scheme for enhancing recovered image quality in polynomial based secret image sharing by modify-and-recalculate strategy. J. Inf. Secur. Appl. 51(11), 102452 (2020)
Yan, X., Lu, Y., Yang, C.: A common method of share authentication in image secret sharing. IEEE Trans. Circuits Syst. Video Technol. 31(7), 2896–2908 (2021)
Yan, X., Lu, Y., Liu, L., Lin, T., Xian Song, H.: Reversible image secret sharing. IEEE Trans. Inf. Forensics Secur. 15, 3848–3858 (2020). https://doi.org/10.1109/TIFS.2020.3001735
Acknowledgements
This work was supported by the Training Program for Academic and Technical Leaders of Jiangxi Province (Grant no. 20204BCJL23036), the Natural Science Foundation of China (Grant nos. 61961022, 62201233, 61906079), and Postdoctoral Research Project of Jiangxi Province (Grant no. 2020KY14).
Author information
Authors and Affiliations
Contributions
WW: writing-original draft; YJ: data curation; formal analysis; YF: project administration; YZ: methodology, software; BQ: writing-review and editing.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Wen, W., Jian, Y., Fang, Y. et al. Authenticable medical image-sharing scheme based on embedded small shadow QR code and blockchain framework. Multimedia Systems 29, 831–845 (2023). https://doi.org/10.1007/s00530-022-00999-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00530-022-00999-3