Abstract
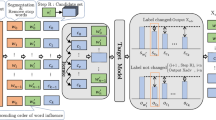
In modern multimedia systems, adversarial text attack is a vital way to expose the vulnerability of deep neural networks and improve their robustness. However, existing methods have some limitations. For example, character-level insertion attacks cause misspelling errors and word-level attacks tend to make limited lexical variations. Although sentence-level attacks can greatly enrich the variety of sentences, they are less effective towards fooling victim models and sometimes lead to the wrong representation. In this paper, we propose the Parentheses Insertion Sentence-level Text Adversarial Attack (PI) algorithm that crafts adversarial texts by filling frequently used parentheses. Specifically, we collect a parentheses set (\(P_{set}\)) at the beginning where all the parentheses are meaningless to ensure the semantics of the sentence remain unchanged after the insertion. Then we utilize the beam search strategy to merge the selected parentheses in the appropriate text positions to improve the attack success rate (ASR). To evaluate the effectiveness of PI method, we conduct extensive experiments by attacking several popular models. Experimental results show that PI enhances the ASR performance compared to word-level and sentence-level baselines while preserving high semantic similarity and incurring minimal perturbation costs. Additionally, PI helps enhance the robustness of modern NLP models by adversarial training.








Similar content being viewed by others
Data availability
Sequence data that support the findings of this study have been deposited in the Github with the primary accession code git@github.com:lucky-fairy-girl/PI.git
Change history
26 February 2025
A Correction to this paper has been published: https://doi.org/10.1007/s00530-025-01723-7
Notes
TED Talks dataset can be found here: https://www.kaggle.com/datasets/ahmadfatani/ted-talks-dataset.
References
Miller, D.J., Xiang, Z., Kesidis, G.: Adversarial learning targeting deep neural network classification: A comprehensive review of defenses against attacks. Proceedings of the IEEE 108(3), 402–433 (2020)
Liu, F., Chen, H., Cheng, Z., Liu, A., Nie, L., Kankanhalli, M.: Disentangled multimodal representation learning for recommendation. IEEE Transactions on Multimedia 25, 7149–7159 (2023). https://doi.org/10.1109/TMM.2022.3217449
Iyyer, M., Wieting, J., Gimpel, K., Zettlemoyer, L.: Adversarial example generation with syntactically controlled paraphrase networks. In: Proceedings of the 2018 Conference of the North American Chapter of the Association for Computational Linguistics: Human Language Technologies, Volume 1 (Long Papers), pp. 1875–1885. Association for Computational Linguistics, New Orleans, Louisiana (2018). https://doi.org/10.18653/v1/N18-1170 . https://aclanthology.org/N18-1170
Han, W., Zhang, L., Jiang, Y., Tu, K.: Adversarial attack and defense of structured prediction models. In: Proceedings of the 2020 Conference on Empirical Methods in Natural Language Processing (EMNLP), pp. 2327–2338. Association for Computational Linguistics, Online (2020). https://doi.org/10.18653/v1/2020.emnlp-main.182 . https://aclanthology.org/2020.emnlp-main.182
Jia, R., Liang, P.: Adversarial examples for evaluating reading comprehension systems. In: Proceedings of the 2017 Conference on Empirical Methods in Natural Language Processing, pp. 2021–2031. Association for Computational Linguistics, Copenhagen, Denmark (2017). https://doi.org/10.18653/v1/D17-1215 . https://aclanthology.org/D17-1215
Xing, X., Jin, Z., Jin, D., Wang, B., Zhang, Q., Huang, X.: Tasty burgers, soggy fries: Probing aspect robustness in aspect-based sentiment analysis. In: Proceedings of the 2020 Conference on Empirical Methods in Natural Language Processing (EMNLP), pp. 3594–3605. Association for Computational Linguistics, Online (2020). https://doi.org/10.18653/v1/2020.emnlp-main.292 .https://aclanthology.org/2020.emnlp-main.292
Wang, T., Wang, X., Qin, Y., Packer, B., Li, K., Chen, J., Beutel, A., Chi, E.: CAT-gen: Improving robustness in NLP models via controlled adversarial text generation. In: Proceedings of the 2020 Conference on Empirical Methods in Natural Language Processing (EMNLP), pp. 5141–5146. Association for Computational Linguistics, Online (2020)
Zhao, Z., Dua, D., Singh, S.: Generating natural adversarial examples. arXiv preprint arXiv:1710.11342 (2017)
Ribeiro, M.T., Singh, S., Guestrin, C.: Semantically equivalent adversarial rules for debugging NLP models. In: Proceedings of the 56th Annual Meeting of the Association for Computational Linguistics (Volume 1: Long Papers), pp. 856–865. Association for Computational Linguistics, Melbourne, Australia (2018). https://doi.org/10.18653/v1/P18-1079 . https://aclanthology.org/P18-1079
Shao, Z., Wu, Z., Huang, M.: Advexpander: Generating natural language adversarial examples by expanding text. IEEE/ACM Transactions on Audio, Speech, and Language Processing 30, 1184–1196 (2022). https://doi.org/10.1109/TASLP.2021.3129339
Ribeiro, M.T., Singh, S., Guestrin, C.: Semantically equivalent adversarial rules for debugging nlp models. In: Proceedings of the 56th Annual Meeting of the Association for Computational Linguistics (volume 1: Long Papers), pp. 856–865 (2018)
Huang, K.-H., Chang, K.-W.: Generating syntactically controlled paraphrases without using annotated parallel pairs. In: Proceedings of the 16th Conference of the European Chapter of the Association for Computational Linguistics: Main Volume, pp. 1022–1033. Association for Computational Linguistics, Online (2021). https://doi.org/10.18653/v1/2021.eacl-main.88 . https://aclanthology.org/2021.eacl-main.88
Cer, D., Yang, Y., Kong, S.-y., Hua, N., Limtiaco, N., John, R.S., Constant, N., Guajardo-Cespedes, M., Yuan, S., Tar, C., et al.: Universal sentence encoder. arXiv preprint arXiv:1803.11175 (2018)
Gao, J., Lanchantin, J., Soffa, M.L., Qi, Y.: Black-box generation of adversarial text sequences to evade deep learning classifiers. In: 2018 IEEE Security and Privacy Workshops (SPW), pp. 50–56 (2018). IEEE
Ebrahimi, J., Lowd, D., Dou, D.: On adversarial examples for character-level neural machine translation. In: Proceedings of the 27th International Conference on Computational Linguistics, pp. 653–663. Association for Computational Linguistics, Santa Fe, New Mexico, USA (2018). https://aclanthology.org/C18-1055
Ebrahimi, J., Rao, A., Lowd, D., Dou, D.: HotFlip: White-box adversarial examples for text classification. In: Proceedings of the 56th Annual Meeting of the Association for Computational Linguistics (Volume 2: Short Papers), pp. 31–36. Association for Computational Linguistics, Melbourne, Australia (2018). https://doi.org/10.18653/v1/P18-2006 . https://aclanthology.org/P18-2006
Eger, S., Benz, Y.: From hero to zéroe: A benchmark of low-level adversarial attacks. In: Proceedings of the 1st Conference of the Asia-Pacific Chapter of the Association for Computational Linguistics and the 10th International Joint Conference on Natural Language Processing, pp. 786–803. Association for Computational Linguistics, Suzhou, China (2020). https://aclanthology.org/2020.aacl-main.79
Liu, A., Yu, H., Hu, X., Li, S., Lin, L., Ma, F., Yang, Y., Wen, L.: Character-level white-box adversarial attacks against transformers via attachable subwords substitution. In: Proceedings of the 2022 Conference on Empirical Methods in Natural Language Processing, pp. 7664–7676. Association for Computational Linguistics, Abu Dhabi, United Arab Emirates (2022)
Jin, D., Jin, Z., Zhou, J.T., Szolovits, P.: Is bert really robust? a strong baseline for natural language attack on text classification and entailment. Proceedings of the AAAI Conference on Artificial Intelligence 34, 8018–8025 (2020)
Li, D., Zhang, Y., Peng, H., Chen, L., Brockett, C., Sun, M.-T., Dolan, B.: Contextualized perturbation for textual adversarial attack. In: Proceedings of the 2021 Conference of the North American Chapter of the Association for Computational Linguistics: Human Language Technologies, pp. 5053–5069. Association for Computational Linguistics, Online (2021). https://doi.org/10.18653/v1/2021.naacl-main.400 . https://aclanthology.org/2021.naacl-main.400
Garg, S., Ramakrishnan, G.: BAE: BERT-based adversarial examples for text classification. In: Proceedings of the 2020 Conference on Empirical Methods in Natural Language Processing (EMNLP), pp. 6174–6181. Association for Computational Linguistics, Online (2020). https://doi.org/10.18653/v1/2020.emnlp-main.498 . https://aclanthology.org/2020.emnlp-main.498
Chen, Q., Sun, J., Palade, V.: A word-level adversarial attack method based on sememes and an improved quantum-behaved particle swarm optimization. IEEE Transactions on Neural Networks and Learning Systems 1–12,(2023). https://doi.org/10.1109/TNNLS.2023.3283308
Yang, X., Qi, Y., Chen, H., Liu, B., Liu, W.: Generation-based parallel particle swarm optimization for adversarial text attacks. Information Sciences 644, 119237 (2023)
Zhou, Y., Jiang, J.-Y., Chang, K.-W., Wang, W.: Learning to discriminate perturbations for blocking adversarial attacks in text classification. In: Proceedings of the 2019 Conference on Empirical Methods in Natural Language Processing and the 9th International Joint Conference on Natural Language Processing (EMNLP-IJCNLP), pp. 4904–4913. Association for Computational Linguistics, Hong Kong, China (2019). https://doi.org/10.18653/v1/D19-1496 . https://aclanthology.org/D19-1496
Zou, A., Wang, Z., Kolter, J.Z., Fredrikson, M.: Universal and transferable adversarial attacks on aligned language models. arXiv preprint arXiv:2307.15043 (2023)
Chang, G., Gao, H., Yao, Z., Xiong, H.: Textguise: Adaptive adversarial example attacks on text classification model. Neurocomputing 529, 190–203 (2023)
Wang, J., Hu, X., Hou, W., Chen, H., Zheng, R., Wang, Y., Yang, L., Huang, H., Ye, W., Geng, X., et al.: On the robustness of chatgpt: An adversarial and out-of-distribution perspective. arXiv preprint arXiv:2302.12095 (2023)
Socher, R., Perelygin, A., Wu, J., Chuang, J., Manning, C.D., Ng, A.Y., Potts, C.: Recursive deep models for semantic compositionality over a sentiment treebank. In: Proceedings of the 2013 Conference on Empirical Methods in Natural Language Processing, pp. 1631–1642 (2013)
Chen, Z., Zhang, H., Zhang, X., Zhao, L.: Quora question pairs (2018)
Liang, A.: Rotten tomatoes: Sentiment classification in movie reviews. CS 229, 15 (2006)
Maas, A., Daly, R.E., Pham, P.T., Huang, D., Ng, A.Y., Potts, C.: Learning word vectors for sentiment analysis. In: Proceedings of the 49th Annual Meeting of the Association for Computational Linguistics: Human Language Technologies, pp. 142–150 (2011)
Zhang, T., Kishore, V., Wu, F., Weinberger, K.Q., Artzi, Y.: Bertscore: Evaluating text generation with bert. arXiv preprint arXiv:1904.09675 (2019)
Miller, G.A.: Wordnet: a lexical database for english. Communications of the ACM 38(11), 39–41 (1995)
Chen, Y., Eger, S.: Menli: Robust evaluation metrics from natural language inference. Transactions of the Association for Computational Linguistics 11, 804–825 (2023)
Acknowledgements
This work was supported by the Shandong Natural Science Foundation(Grant No.ZR2023MF008), the Shandong Natural Science Foundation (Grant No.ZR2023QF051), Outstanding Youth Science Foundation Project of Shandong Province (Overseas) (Grant No.2023HWYQ-070), the Qingdao Natural Science Foundation (Grant No.23-2-1-161-zyyd-jch), Independent Innovation Research Project (Grant No.22CX06059A), Young Talent of Lifting engineering for Science and Technology in Shandong, China (Grant No. SDAST2024QTA040).
Author information
Authors and Affiliations
Contributions
A.L. and X.Y. wrote the main manuscript text. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no competing interests.
Additional information
Communicated by Junyu Gao.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
The original article has been corrected to update acknowledgment section.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Li, A., Yang, X., Liu, B. et al. Parentheses insertion based sentence-level text adversarial attack. Multimedia Systems 31, 101 (2025). https://doi.org/10.1007/s00530-025-01678-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s00530-025-01678-9