Abstract
Risk analysis is traditionally considered a critical activity for the whole software system’s lifecycle. Risks are identified by considering technical aspects (e.g., failures of the system, unavailability of services, etc.) and handled by suitable countermeasures through a refined design. This, however, introduces the problem of reconsidering system requirements. In this paper, we propose a goal-oriented approach for analyzing risks during the requirements analysis phase. Risks are analyzed along with stakeholder interests, and then countermeasures are identified and introduced as part of the system’s requirements. This work extends the Tropos goal modeling formal framework proposing new concepts, qualitative reasoning techniques, and methodological procedures. The approach is based on a conceptual framework composed of three main layers: assets, events, and treatments. We use “loan origination process” case study to illustrate the proposal, and we present and discuss experimental results obtained from the case study.







Similar content being viewed by others
Notes
In ISO 13335, asset is defined as “anything that has value to an organization”. As such, assets may be (1) resources, (2) tasks executed to generate value, and (3) targets/objectives/goals whose fulfillment generates value. This paper concentrates on analyzing assets as goals.
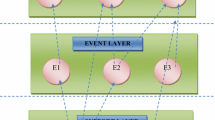
In this paper, we use hexagons only to denote an event treatment/countermeasure.
Related is meant to enumerate all the nodes that can be reachable from a given node in \(\langle{\mathcal N},{\mathcal R},{\mathcal I}\rangle\) through a particular type of relation.
The questionnaire is called requirement collection schema and available at http://fmsweng.science.unitn.it/~sistar/
References
Anton AI (1996) Goal-based requirements analysis. In: Proceedings of the 2nd IEEE international conference on requirements engineering (ICRE’96), IEEE Computer Society Press, Washington, DC, USA, p 136
Asnar Y, Giorgini P (2006) Modelling risk and identifying countermeasures in organizations. In: Proceedings of the 1st international workshop on critical information infrastructures security, Springer-Verlag, Lecture Notes in Computer Science, vol 4347, pp 55–66
Asnar Y, Giorgini P (2008) Analyzing business continuity through a multi-layers modell. In: Proceedings of 6th international conference on business process management
Asnar Y, Bonato R, Bryl V, Campagna L, Dolinar K, Giorgini P, Holtmanns S, Klobucar T, Lanzi P, Latanicki J, Massacci F, Meduri V, Porekar J, Riccucci C, Saidane A, Seguran M, Yautsiukhin A, Zannone N (2006) Security and privacy requirements at organizational level. Project deliverable A1.D2.1, SERENITY consortium, EU-IST-IP 6th framework programme—SERENITY 27587
Asnar Y, Bonato R, Giorgini P, Massacci F, Meduri V, Riccucci C, Saidane A (2007a) Secure and dependable patterns in organizations: an empirical approach. In: Proceedings of the 15th IEEE international requirements engineering conference, IEEE Computer Society Press, Oakland, CA
Asnar Y, Giorgini P, Massacci F, Zannone N (2007b) From trust to dependability through risk analysis. In: Proceedings of the second international conference on availability, reliability and security, IEEE Press, New York
Asnar Y, Moretti R, Sebastianis M, Zannone N (2008) Risk as dependability metrics for the evaluation of business solutions: a model-driven approach. In: Proceedings of the third international conference on availability, reliability and security
Bedford T, Cooke R (2001) Probabilistic risk analysis: foundations and methods. Cambridge University Press, Cambridge
Boehm BW (1991) Software risk management: principles and practices. IEEE Softw 8(1):32–41. doi:10.1109/52.62930
den Braber F, Dimitrakos T, Gran BA, Lund MS, Stølen K, Aagedal JØ (2003) The CORAS methodology: model-based risk assessment using UML and UP. In: UML and the Unified Process, Idea Group Publishing, Hershey, pp 332–357
Bresciani P, Perini A, Giorgini P, Giunchiglia F, Mylopoulos J (2004) Tropos: an agent-oriented software development methodology. J Auton Agent Multi Agent Syst 8(3):203–236. doi:10.1023/B:AGNT.0000018806.20944.ef
Butler S, Fischbeck P (2001) Multi-attribute risk assessment. Tech. Rep. CMU-CS-01-169, Carnegie Mellon University
Butler SA (2002) Security attribute evaluation method: a cost-benefit approach. In: Proceedings of the 24th international conference on software engineering, ACM Press, New York, NY, USA, pp 232–240. doi:10.1145/581339.581370
Carr MJ, Konda SL, Monarch I, Ulrich FC, Walker CF (1993) Taxonomy-based risk identification. Tech. Rep. CMU/SEI-93-TR-6, Software Engineering Institute, Carnegie Mellon University
Chung LK, Nixon BA, Yu E, Mylopoulos J (2000) Non-functional requirements in software engineering. Kluwer Academic Publishers, Dordrecht
Cornford SL, Feather MS, Heron VA, Jenkins JS (2006) Fusing quantitative requirements analysis with model-based systems engineering. In: Proceedings of the 14th IEEE international requirements engineering conference, IEEE Computer Society Press, Los Alamitos, CA, USA, pp 279–284, doi:10.1109/RE.2006.24
Dardenne A, van Lamsweerde A, Fickas S (1993) Goal-directed requirements acquisition. Sci Comput Program 20(1–2):3–50
Feather MS (2004) Towards a unified approach to the representation of, and reasoning with, probabilistic risk information about software and its system interface. In: Proceedings of the 15th IEEE international symposium on software software reliability engineering, IEEE Computer Society Press, Silver Spring, MD, pp 391–402
Giorgini P, Mylopoulos J, Nicchiarelli E, Sebastiani R (2003) Formal reasoning techniques for goal models. J Data Semantics 1(1):1–20
Helmer G, Wong J, Slagell M, Honavar V, Miller L, Lutz R (2002) A software fault tree approach to requirements analysis of an intrusion detection system. Requir Eng J 7(4):207–220
Holton GA (2004) Defining risk. Financ Anal J 60(6):19–25
ISO/IEC (2002) Risk management-vocabulary-guidelines for use in standards. ISO/IEC Guide 73
Jürjens J (2001) Towards secure systems development with UMLsec. In: Proceedings of the 4th international conference on fundamental approaches to software engineering, Springer, New York, pp 187–200
Kletz TA (1997) HAZOP—past and future. Reliab Eng Syst Saf 55(3):263–266
van Lamsweerde A, Letier E (2000) Handling obstacles in goal-oriented requirements engineering. IEEE Trans Softw Eng 26(10):978–1005. doi:10.1109/32.879820
van Lamsweerde A, Brohez S, Landtsheer RD, Janssens D (2003) From system goals to intruder anti-goals: attack generation and resolution for security requirements engineering. In: Proceedings of the 2nd international workshop on requirements for high assurance systems
Linstone H, Turoff M (1975) The delphi method: techniques and applications. Addison-Wesley Pub. Co, Reading, MA
Liu L, Yu ESK, Mylopoulos J (2003) Security and privacy requirements analysis within a social setting. In: Proceedings of the 11th IEEE international requirements engineering conference, pp 151–161
Lodderstedt T, Basin D, Doser J (2002) SecureUML: A UML-based modeling language for model-driven security. In: Proceedings of the 5th international conference on the unified modeling language—the language and its applications, Springer-Verlag, Lecture Notes in Computer Science, vol 2460, pp 426–441
Lutz RR, Woodhouse RM (1997) Requirements analysis using forward and backward search. Ann Softw Eng 3(1):459–475
Mayer N, Rifaut A, Dubois E (2005) Towards a risk-based security requirements engineering framework. In: Proceedings of the 11th international workshop on requirements engineering: foundation for software quality
Mayer N, Dobuis E, Rifaut A (2007) Requirements engineering for improving business/IT alignment in security risk management methods. In: Proceedings of the 3rd international conference interoperability for enterprise software and applications
McDermott J, Fox C (1999) Using abuse case models for security requirements analysis. In: Proceedings of 15th annual computer security applications conference, Phoenix, AZ, USA, pp 55–64. doi:10.1109/CSAC.1999.816013
Pfleeger CP, Pfleeger SL (2006) Security in computing, 4th edn. Prentice-Hall, Englewood, Cliffs, NJ
Roy GG, Woodings TL (2000) A framework for risk analysis in software engineering. In: Proceedings of the seventh Asia-Pacific software engineering conference (APSEC ’00), IEEE Computer Society Press, Washington, DC, USA, p 441
Schneier B (1999) Attack trees: modeling security threats. Dr Dobbï J 12(24):21–29
Sebastiani R, Giorgini P, Mylopoulos J (2004) Simple and minimum-cost satisfiability for goal models. In: Proceedings of the 16th conference on advanced information systems engineering, Springer-Verlag Heidelberg, Lecture Notes in Computer Science, vol 3084, pp 20–33. doi:10.1007/b98058
Shafer G (1976) A mathematical theory of evidence. Princeton University Press, Princeton, NJ
Shull F, Singer J, Sjøberg DIK (2007) Guide to advanced empirical software engineering. Springer, New York
Sindre G, Opdahl AL (2005) Eliciting security requirements with misuse cases. Requir Eng J 10(1):34–44. doi:10.1007/s00766-004-0194-4
Sommerville I (2004) Software engineering, 7th edn. Addison Wesley, Reading, MA
Stamatelatos M, Vesely W, Dugan J, Fragola J, Minarick J, Railsback J (2002) Fault tree handbook with aerospace applications. NASA
US-DoD (1980) Military standard, procedures for performing a failure mode, effects, and critical analysis. MIL-STD-1629A
Yu E (1995) Modelling strategic relationships for process engineering. PhD thesis, University of Toronto, Department of Computer Science
Acknowledgments
This work has been partly supported by the projects EU-SERENITY, EU-MASTER, FIRB-ASTRO, PAT-MOSTRO, PAT-STAMPS, and PRIN-MENSA.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Asnar, Y., Giorgini, P. & Mylopoulos, J. Goal-driven risk assessment in requirements engineering. Requirements Eng 16, 101–116 (2011). https://doi.org/10.1007/s00766-010-0112-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00766-010-0112-x