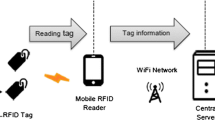
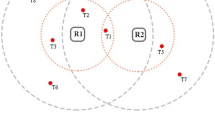
Abstract
With the emergence of wireless RFID technologies, the problem of scheduling transmissions in dynamic RFID systems has been arousing attention. In recent year, it has also instigated researches to propose different heuristic algorithms for scheduling transactions between RFID readers and tags. In this paper, we present a two phase dynamic modulation (TPDM) technique, which consists of regional scheduling and hidden terminal scheduling phases, aims to efficiently perform communications between readers and tags in high density and mobile RFID networks. TPDM is a simple mechanism for coordinating simultaneous transmissions among multiple readers and hidden terminals. A significant improvement of this approach is that TPDM can prevent reader collisions by using a distributed self-scheduling scheme. An advantage of the proposed technique is that TPDM is adaptive in both static and dynamic RFID environments. To evaluate the performance of the proposed technique, we have implemented the TPDM scheme along with the Colorwave and Pulse protocols. The experimental results show that the TPDM scheduling techniques provide superior and stable performance in both static and dynamic circumstance, especially in mobile and high density RFID environments. The TPDM is shown to be effective in terms of throughput, system efficiency, and easy to implement.








Similar content being viewed by others
Notes
RFID readers reside in the same locality can communicate with each other.
All readers are assumed to have the same transmission range of control channel and data channel.
References
Bao L, Garcia-Luna-Aceves JJ (2000) Collision-free topology-dependent channel access scheduling. In: Proceedings of the IEEE 21st century military communications conference (MILCOM), pp 507–511
Birari SM (2005) Mitigating the reader collision problem in RFID networks with mobile readers. In: Proceedings of the 13th IEEE international conference on networks
Carbunar B, Grama A, Octavian Carbunar JV (2006) Redundancy and coverage detection in sensor networks. ACM Transactions on Sensor Networks (TOSN),vol 2, issue 1, February 2006
Cha JR, Kim JH (2006) Dynamic framed slotted ALOHA algorithm using fast tag estimation method for RFID system. In: Proceedings. CCNC’06, Las Vegas, USA, 8–10 January 2006
Chen W-T, Ho T-W, Chen Y-C (2005) An MAC protocol for wireless ad-hoc networks using smart antennas. In: Proceedings of the 11th IEEE international conference on parallel and distributed systems (ICPADS’05), pp 446–452
Diorio C, HAG Co-Chair (2004) Class-1 generation 2 UHF RFID. http://www.autoid.org/sc31/2004/dec/SG3_200411_430_Gen2Update.pdf. Accessed Dec 2004
Engels DW, Sarma SE (2002) The reader collision problem. In: Proceedings of the 2002 IEEE international conference on systems, man and cybernetics
European Telecommunications Standards Institute (2004) ETSI EN 302 208-1 v1.1.1. http://www.RFIDc.com/pdfs_downloads/ETSI%20Standard%202.pdf
Ho J, Engels DW, Sarma SE (2006) HiQ: a hierarchical Q-learning algorithm to solve the reader collision problem. In: Proceedings of the international symposium on applications and the internet workshops (SAINTW’06), pp 88–91
Hsu C-H, Chen Y-M, Kang HJ (2008) Performance-effective and low-complexity redundant reader detection in wireless RFID networks. EURASIP J Wirel Commun Netw 2008, Article ID 604747, 9 pp. doi:10.1155/2008/604747
Hwang L-J, Sheu S-T, Shih Y-Y, Cheng Y-C (2005) Grouping strategy for solving hidden node problem in IEEE 802.15.4 LR-WPAN. In: Proceedings of the 1st international conference on wireless internet, pp 26–32
Jain N, Das SR, Nasipuri A (2001) A multichannel CSMA MAC protocol with receiver-based channel selection for multihop wireless networks. In: Proceedings of the 10th IEEE international conference on computer communications and networks, pp 432–439
Kim J, Kim S, Kim D, Lee W, Kim E (2005) Low-energy localized clustering: an adaptive cluster radius configuration scheme for topology control in wireless sensor networks. In: Proceedings of the IEEE vehicular technology conference (VTC), pp 2546–2550
Konorski J, (2005) Solvability of a Markovian model of an IEEE 802.11 LAN under a backoff attack. In: Proceedings of the 13th IEEE international symposium on modeling, analysis, and simulation of computer and telecommunication systems (MASCOYS’05), pp 491–498
Kuo W-K, Jay Kuo C-C (2003) Enhanced backoff scheme in CSMA/CA for IEEE 802.11. In: Proceedings of the 58th IEEE vehicular technology conference, pp 2809–2813
Sandoval-Reyes S, Soberanes Perez JL (2005) Mobile RFID reader with database wireless synchronization. In: Proceedings of the 2nd IEEE international conference on electrical and electronics engineering, pp 5–8
Sobrinho JL, de Haan R, Brazio JM (2005) Why RTS-CTS is not your ideal wireless LAN multiple access protocol. In: Proceedings of the IEEE wireless communications and networking conference, pp 81–87
Tanaka Y, Sasase I (2007) Interference avoidance algorithms for passive RFID systems using contention-based transmit abortion. IEICE Trans Commun E90-B(11):3170–3180
Waldrop J, Engels DW, Sarma SE (2003) Colorwave: an anticollision algorithm for the reader collision problem. In: Proceedings of the IEEE international conference on communications, pp 1206–1210
Wang X,Kar K (2005) Throughput modeling and fairness issues in CSMA/CA based ad-hoc networks. In: Proceedings of the 24th annual joint conference on IEEE computer and communications societies (INFOCOM 2005), pp 23–34, 002E
You T, Hassanein H, Yeh C-H (2005) PIDC—towards an ideal MAC protocol for multi-hop wireless LANs. In: Proceedings of the IEEE international conference on wireless networks, communications and mobile computing, pp 655–660
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hsu, CH., Chen, SC., Yu, CH. et al. Alleviating reader collision problem in mobile RFID networks. Pers Ubiquit Comput 13, 489–497 (2009). https://doi.org/10.1007/s00779-009-0224-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00779-009-0224-9