Abstract
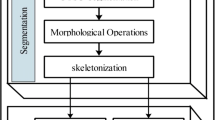
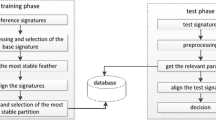
This paper describes a method for stroke-based online signature verification using null component analysis (NCA) and principal component analysis (PCA). After the segmentation and flexible matching of the signature, we extract stable segments from each reference signature in order that the segment sequences have the same length. The reference set of feature vectors are transformed and separated into null components (NCs) and principal components (PCs) by K-L transform. Online signature verification is a special two-category classification problem and there is not a single available forgery set in an actual system. Therefore, it is different from the typical application of PCA in pattern recognition that both NCA and PCA are used to respectively analyze stable and unstable components of genuine reference set. Experiments on a data set containing a total 1,410 signatures of 94 signers show that the NCA/PCA-based online signature verification method can achieve better results. The best result yields an equal error rate of 1.9%.










Similar content being viewed by others
References
Leclerc F, Plamondon R (1994) Automatic signature verification: the state of the art—1989–1993. Int J Pattern Recognit Artif Intell 8(3):643–660
Nalwa VS (1997) Automatic online signature verification. Proc IEEE 85(2):215–239
Jain AK, Griess FD, Connell SD (2002) Online signature verification. J Pattern Recognit 35(2):2963–2972
Zhang K, Pratikakis I, Cornelis J, Nyssen E (2000) Using landmarks to establish a point-to-point correspondence between signatures. J Pattern Anal Appl 3(1):69–75
Brault J, Plamondon R (1993) Segmenting handwritten signatures at their perceptually important points. IEEE Trans Pattern Anal Mach Intell 15(9):953–957
Yue KW, Wijesoma WS (2000) Improved segmentation and segment association for online signature verification. IEEE Inter Conf Syst Man Cybern 4:2752–2756
Wirtz B (1995) Stroke-based time warping for signature verification. In: Proceedings of the 3rd international conference on document analysis and recognition, vol 1, pp 179–182
Wirtz B (1997) Average prototypes for stroke-based signature verification. In: Proceedings of the 4th interernational conference on document analysis and recognition, vol 1, pp 268–272
Rhee TH, Cho SJ, Kim JH (2001) On-line signature verification using model-guided segmentation and discriminative feature selection for skilled forgeries. In: Proceedings of 6th international conference on document analysis and recognition, pp 645–649
Qu T, Saddik AE, Adler A (2004) A Stroke based algorithm for dynamic signature verification. In: Proceedings of international conference on electrical and computer engineering, vol 1, pp 461–464
Qu T, Saddik AE, Adler A (2003) Dynamic signature verification system using stroked based features. In: Proceedings of 2003 international conference on haptic, audio and visual environments and their applications, vol 1, pp 83–88
Lee J, Yoon H, Soh J, Chun B, Chung Y (2004) Using geometric extrema for segment-to-segment characteristics comparison in online signature verification. J Pattern Recognit 37:93–103
Lee W, Mokankishnan N, Paulik M (1998) Improved segmentation through dynamic time warping for signature verification using a neural network classifer. In: Image proceedings on 1998 international conference, vol 2, pp 929–933
Sirovich L, Kirby M (1987) Low-dimensional procedure for characterization of human faces. J Opt Soc Am 4:519–524
Kirby M, Sirovich L (1990) Application of the KL procedure for the characterization of human faces. IEEE Trans Pattern Anal Mach Intell 12:103–108
Turk M, Pentland A (1991) Eigenfaces for recognition. J Cognit Neurosci 3:71–86
Lu G, Zhang D, Wang K (2003) Palmprint recognition using eigenpalms features. Pattern Recognit Lett 24:1463–1467
Wu X, Zhang D, Wang K (2003) Fisherpalms based palmprint recognition. Pattern Recognit Lett 24:2829–2838
Huber R, Ramoser H, Mayer K, Penz H, Rubik M (2005) Classification of coins using an eigenspace approach. Pattern Recognit Lett 26:61–75
Acknowledgements
This work is supported by Sci-Tech. Project of Harbin, China (2003AA1CG055-10).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Li, B., Zhang, D. & Wang, K. Online signature verification based on null component analysis and principal component analysis. Pattern Anal Applic 8, 345–356 (2006). https://doi.org/10.1007/s10044-005-0016-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10044-005-0016-4