Abstract
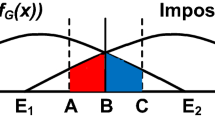
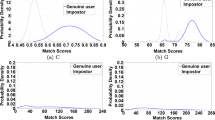
A multistage biometric verification system uses multiple biometrics and/or multiple biometric verifiers to generate a verification decision. The core of a multistage biometric verification system is reject option which allows a stage not to give a genuine/impostor decision when it is not confident enough. This paper studies the effectiveness of symmetric rejection for multistage biometric verification systems. The symmetric rejection method determines the reject region by symmetrically rejecting equal proportion of genuine and impostor scores. The applicability of a multistage biometric verification system depends on how secure and user convenient it is, which is measured by the performance–cost trade-off. This paper analyzes the performance–cost trade-off of symmetric rejection method by conducting extensive experiments. Experiments are performed on two biometric databases: (1) publicly available NIST database and (2) a keystroke database. In addition, the symmetric rejection method is empirically compared with two existing rejection methods: (1) sequential probability ratio test-based method, which uses score-fusion and (2) Marcialis et al.’s method, which does not use score fusion. Results demonstrate strong effect of symmetric rejection method on creating a secure and user convenient multistage biometric verification system.





Similar content being viewed by others
References
Abo-Zahhad M, Ahmed SM, Abbas SN (2016) A new multi-level approach to eeg based human authentication using eye blinking. Pattern Recognit Lett 82:216–225
Akhtar Z, Fumera G, Marcialis G, Roli F (2012) Evaluation of serial and parallel multibiometric systems under spoofing attacks. In: IEEE conference on biometrics: theory, applications and systems (BTAS), pp 283–288
Al-Waisy AS, Qahwaji R, Ipson S, Al-Fahdawi S, Nagem TAM (2018) A multi-biometric iris recognition system based on a deep learning approach. Pattern Anal Appl 21(3):783–802
Allano L, Dorizzi B, Garcia-Salicetti S (2010) Tuning cost and performance in multi-biometric systems: a novel and consistent view of fusion strategies based on the sequential probability ratio test (sprt). Pattern Recognit Lett 31(9):884–890
Baig A, Bouridane A, Kurugollu F, Albesher B (2014) Cascaded multimodal biometric recognition framework. IET Biometr 3(1):16–28
Bartlett PL, Wegkamp MH (2008) Classification with a reject option using a hinge loss. J Mach Learn Res 9:1823–1840
Bharadwaj S, Bhatt HS, Singh R, Vatsa M, Noore A (2015) Qfuse: Online learning framework for adaptive biometric system. Pattern Recognit 48(11):3428–3439
Bhatt H, Bharadwaj S, Vatsa M, Singh R, Ross A, Noore A (2011) A framework for quality-based biometric classifier selection. In: 2011 international joint conference on biometrics (IJCB), pp 1–7
Chow CK (1970) On optimum recognition error and reject tradeoff. IEEE Trans Inf Theory 16(1):41–46
Das RK, Jelil S, Mahadeva Prasanna SR (2017) Development of multi-level speech based person authentication system. J Signal Process Syst 88(3):259–271
Dinca LM, Hancke GP (2017) The fall of one, the rise of many: a survey on multi-biometric fusion methods. IEEE Access 5:6247–6289
Dwivedi R, Dey S (2018) A novel hybrid score level and decision level fusion scheme for cancelable multi-biometric verification. Appl Intell 49(3):1016–1035
Elhoseny M, Essa E, Elkhateb A, Hassanien A, Hamad A (2018) Cascade multimodal biometric system using fingerprint and iris patterns. In: International conference on advanced intelligent systems and informatics, pp 590–599
Fierrez J, Morales A, Vera-Rodriguez R, Camacho D (2018) Multiple classifiers in biometrics. Part 1: fundamentals and review. Inf Fusion 44:57–64
Fierrez J, Morales A, Vera-Rodriguez R, Camacho D (2018) Multiple classifiers in biometrics. Part 2: trends and challenges. Inf Fusion 44:103–112
Fumera G, Roli F, Giacinto G (2000) Reject option with multiple thresholds. Pattern Recognit 33:2099–2101
Gunetti D, Picardi C (2005) Keystroke analysis of free text. ACM Trans Inf Syst Secur 8(3):312–347
Haghighat M, Abdel-Mottaleb M, Alhalabi W (2016) Discriminant correlation analysis: real-time feature level fusion for multimodal biometric recognition. IEEE TIFS 11(9):1984–1996
Hammad M, Wang K (2019) Parallel score fusion of ecg and fingerprint for human authentication based on convolution neural network. Comput Secur 81:107–122
Hezil N, Boukrouche A (2017) Multimodal biometric recognition using human ear and palmprint. IET Biometr 6(5):351–359
Hossain M, Balagani K, Phoha V (2012) New impostor score based rejection methods for continuous keystroke verification with weak templates. In: IEEE conference on biometrics: theory, applications and systems (BTAS)
Hossain M, Balagani K, Phoha V (2013) On controlling genuine reject rate in multi-stage biometric verification. In: CVPRW, pp 194–199
Hossain M, Chen J, Rahman K (2018) On enhancing serial fusion based multi-biometric verification system. Appl Intell 48(12):4824–4833
Hossain MS, Rahman KA (2017) An empirical study on verifier order selection in serial fusion based multi-biometric verification system. In: IEA/AIE, pp 249–258
Huang J, Ling C (2005) Using auc and accuracy in evaluating learning algorithms. IEEE Trans KDE 17(3):299–310
Jomaa RM, Islam MS, Mathkour H (2018) Improved sequential fusion of heart-signal and fingerprint for anti-spoofing. In: Proceedings of IEEE conference on identity, security, and behavior analysis (ISBA), pp 1–7
Kasprowski P, Harezlak K (2018) Fusion of eye movement and mouse dynamics for reliable behavioral biometrics. Pattern Anal Appl 21(1):91–103
Landgrebe TCW, Tax DMJ, Paclík P, Duin RPW (2006) The interaction between classification and reject performance for distance-based reject-option classifiers. Pattern Recogn Lett 27:908–917
Li JQ, Barron AR (1999) Mixture density estimation. Adv Neural Inf Process Syst 12:279–285
Liu W, Wang Z, Liu X, Zeng N, Liu Y, Alsaadi FE (2017) A survey of deep neural network architectures and their applications. Neurocomputing 234:11–26
Lumini A, Nanni L (2017) Overview of the combination of biometric matchers. Inf Fusion 33:71–85
Maity S, Abdel-Mottaleb M, Asfour S (2017) Multimodal biometrics recognition from facial video via deep learning. In: International conference on computer science, information technology and applications, pp 67–75
Marcialis G, Mastinu P, Roli F (2010) Serial fusion of multi-modal biometric systems. In: IEEE Workshop on BIOMS, pp 1 –7
Marcialis GL, Roli F, Didaci L (2009) Personal identity verification by serial fusion of fingerprint and face matchers. Pattern Recognit 42(11):2807–2817
Murakami T, Kaga Y, Takahashi K (2016) On restricting modalities in likelihood-ratio based biometric score fusion. In: ICPR, pp 3036–3042
Murakami T, Ohki T, Takahashi K (2016) Optimal sequential fusion for multibiometric cryptosystems. Inf Fusion 32:93–108
Murakami T, Takahashi K, Matsuura K (2012) Towards optimal countermeasures against wolves and lambs in biometrics. In: IEEE conference on biometrics: theory, applications and systems (BTAS), pp 69 –76
Nandakumar K, Chen Y, Dass SC, Jain A (2008) Likelihood ratio-based biometric score fusion. IEEE Trans Pattern Anal Mach Intell 30:342–347
NIST (2011) Biometric scores set. http://www.nist.gov/itl/iad/ig/biometricscores.cfm. Accessed 15 Oct 2019
Phoha V, Joshi S (2013) Method and system of identifying users based upon free text keystroke (US Patent No. 8489635, Issued July 16, 2013)
Poh N, Bourlai T, Kittler J, Allano L, Alonso-Fernandez F, Ambekar O, Baker J, Dorizzi B, Fatukasi O, Fierrez J, Ganster H, Ortega-Garcia J, Maurer D, Salah AA, Scheidat T, Vielhauer C (2009) Benchmarking quality-dependent and cost-sensitive score-level multimodal biometric fusion algorithms. IEEE TIFS 4(4):849–866
Popescu-Bodorin N, Balas VE, Motoc IM (2011) 8-valent fuzzy logic for iris recognition and biometry. In: International symposium on computational intelligence and intelligent informatics (ISCIII), pp 149–154
Popescu-Bodorin N, Noaica CM, Penariu P (2015) Iris recognition with 4 or 5 fuzzy sets. In: IFSA-EUSFLAT
Raghavendra R, Dorizzi B, Rao A, Kumar GH (2011) Designing efficient fusion schemes for multimodal biometric systems using face and palmprint. Pattern Recognit 44(5):1076–1088
Raja KB, Raghavendra R, Stokkenes M, Busch C (2015) Multi-modal authentication system for smartphones using face, iris and periocular. In: International confernce on biometrics (ICB), pp 143–150
Rakhlin A, Panchenko D, Mukherjee S (2005) Risk bounds for mixture density estimation. ESAIM Probab Stat 9:220–229
Ranjan R, Patel VM, Chellappa R (2019) Hyperface: a deep multi-task learning framework for face detection, landmark localization, pose estimation, and gender recognition. IEEE TPAMI 41(1):121–135
Sabri M, Moin M, Razzazi F (2018) A new framework for match on card and match on host quality based multimodal biometric authentication. J Sign Process Syst 91(2):163–177
Saevanee H, Clarke N, Furnell S, Biscione V (2015) Continuous user authentication using multi-modal biometrics. Comput Secur, pp 234–246
Sajjad M, Khan S, Hussain T, Muhammad K, Sangaiah AK, Castiglione A, Esposito C, Baik SW (2018) CNN-based anti-spoofing two-tier multi-factor authentication system. Pattern Recognit Lett 126:123–131
Santos-Pereira CM, Pires AM (2005) On optimal reject rules and roc curves. Pattern Recognit Lett 26:943–952
Sharma R, Das S, Joshi P (2018) Score-level fusion using generalized extreme value distribution and dsmt, for multi-biometric systems. IET Biometr 7(5):474–481
Soleymani S, Dabouei A, Kazemi H, Dawson J, Nasrabadi N (2018) Multi-level feature abstraction from convolutional neural networks for multimodal biometric identification. In: Proceedings of international conference on pattern recognition (ICPR), pp 3469–3476
Sundararajan K, Woodard DL (2018) Deep learning for biometrics: a survey. ACM Comput Surv 51(3):65:1–65:34
Taigman Y, Yang M, Ranzato M, Wolf L (2014) Deepface: closing the gap to human-level performance in face verification. In: CVPR, pp 1701–1708
Takahashi K, Mimura M, Isobe Y, Seto Y (2004) A secure and user-friendly multimodal biometric system. In: Proceedings of the SPIE, pp 12–19
Talreja V, Valenti CM, Nasrabadi N (2017) Multibiometric secure system based on deep learning. In: Proceedings of Global SIP, pp 1–5
Tortorella F (2000) An optimal reject rule for binary classifiers. In: Proceedings of the Joint IAPR Workshops, pp 611–620
Vatsa M, Singh R, Noore A (2009) Context switching algorithm for selective multibiometric fusion. In: Proceedings of international conference on pattern recognition and machine intelligence, pp 452–457
Vatsa M, Singh R, Noore A, Ross A (2010) On the dynamic selection of biometric fusion algorithms. IEEE Trans Inf Forensics Secur 5(3):470–479
Wald A (1947) Sequential analysis, 1st edn. Wiley, New York
Yadav D, Kohli N, Agarwal A, Vatsa M, Singh R, Noore A (2018) Fusion of handcrafted and deep learning features for large-scale multiple iris presentation attack detection. In: CVPR workshops
Zhang Q, Li H, Sun Z, Tan T (2018) Deep feature fusion for iris and periocular biometrics on mobile devices. IEEE TIFS 13(11):2897–2912
Zhang Q, Yin Y, Zhan DC, Peng J (2014) A novel serial multimodal biometrics framework based on semisupervised learning techniques. IEEE Trans Inf Forensics Secur 9(10):1681–1694
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Hossain, M.S., Balagani, K.S. & Phoha, V.V. Effectiveness of symmetric rejection for a secure and user convenient multistage biometric system. Pattern Anal Applic 24, 49–60 (2021). https://doi.org/10.1007/s10044-020-00899-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10044-020-00899-0