Abstract
Imagine that we have a highly competing virus that is spreading over a (e.g., social) network where users have different sensitivity/interest against it. A virus may be anything that has a “spreading” behavior such as a rumor, a social media trend or even an infectious disease. Is it possible to predict the outcome in such a viral phenomenon and compute the number of users that will eventually get infected? We answer this question by providing qualitative and quantitative thresholds that describe the behavior of the virus in a given network. Our main contribution is that for the first time, the case of a heterogeneous (with respect to the nodes) network is analytically tackled. We model the different sensitivity to the virus by dividing the nodes of the network into different groups. Each group has a particular profile describing its behavior toward the virus. Conditions are provided based on certain network characteristics that govern the extent of the infection. These conditions are experimentally verified by extensive experiments.












Similar content being viewed by others
Change history
18 December 2018
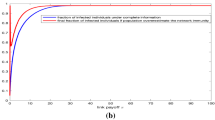
In the original publication, part figures were incorrectly positioned in Figure 2. The correct figure is given below.
Notes
This is a preliminary version of the current paper.
These are time-dependent variables but for brevity we do not write them as such (\(I_{{\mathcal {A}}}(t)\)).
References
Anderson R, May RM (1992) Infectious diseases of humans. Oxford University Press, Oxford
Aral S, Walker D (2012) Identifying influential and susceptible members of social networks. Science 337(6092):337–41
Bailey N (1975) The mathematical theory of infectious diseases and its applications. Griffin, London
Beutel A, Prakash BA, Rosenfeld R, Faloutsos C (2012) Interacting viruses in networks: Can both survive? In: Proceedings of the 18th ACM SIGKDD international conference on knowledge discovery and data mining, KDD ’12. ACM, New York, pp 426–434
Boost. Boost c++ graph library. http://www.boost.org/doc/. Accessed 4 Apr 2016
Chazelle B (2010) Analytical tools for natural algorithms. In: Innovations in computer science: ICS 2010, Tsinghua University, Beijing, China, January 5–7, 2010. Proceedings, pp 32–41. Tsinghua University Press
Ganesh AJ, Massoulié L, Towsley DF (2005) The effect of network topology on the spread of epidemics. In: INFOCOM 2005. 24th annual joint conference of the IEEE computer and communications societies, 13–17 March 2005, Miami, FL, USA, pp 1455–1466
Gould H, Tobochnik J (2010) Statistical and thermal physics: with computer applications. Princeton University Press, Princeton
Hethcote HW (2000) The mathematics of infectious diseases. SIAM Rev 42(4):599–653
Hirsch MW, Smale S (1974) Differential equations, dynamical systems and linear algebra. Academic Press, Cambridge
Kephart JO, White SR (1993) Measuring and modeling computer virus prevalence. In: 1993 IEEE computer society symposium on research in security and privacy, Oakland, CA, USA, May 24–26, 1993, pp 2–15
KONECT (May, 2016a) Dblp co-authorship network dataset. http://konect.uni-koblenz.de/networks/com-dblp. Accessed 4 May 2016
KONECT (May, 2016b) Skitter network dataset. http://konect.uni-koblenz.de/networks/as-skitter. Accessed 4 May 2016
Leskovec J, Kleinberg J, Faloutsos C (2007) Graph evolution: Densification and shrinking diameters. ACM Trans. Knowl. Discov. Data 1(1):2
Leskovec J, Lang KJ, Dasgupta A, Mahoney MW (2009) Community structure in large networks: natural cluster sizes and the absence of large well-defined clusters. Internet Math 6(1):29–123
Lum K, Swarup S, Eubank S, Hawdon J (2014) The contagious nature of imprisonment: an agent-based model to explain racial disparities in incarceration rates. J R Soc Interface 11(98):20140409
McKendrick AG (2011) Applications of mathematics to medical problems. Proc Edinb Math Soc 14:98–130
Pastor-Satorras R, Vespignani A (2001) Epidemic spreading in scale-free networks. Phys Rev Lett 86:3200–3203
Prakash BA, Beutel A, Rosenfeld R, Faloutsos C (2012) Winner takes all: competing viruses or ideas on fair-play networks. In: Proceedings of the 21st international conference on world wide web, WWW ’12. ACM, New York, pp 1037–1046
Prakash BA, Chakrabarti D, Faloutsos M, Valler N, Faloutsos C (2011) Threshold conditions for arbitrary cascade models on arbitrary networks. In: Proceedings of the 2011 IEEE 11th international conference on data mining, ICDM ’11. IEEE Computer Society, Washington, pp 537–546
Rapti A, Sioutas S, Tsichlas K, Tzimas G (2015) Virus propagation in multiple profile networks. In: Proceedings of the 21th ACM SIGKDD international conference on knowledge discovery and data mining, Sydney, NSW, Australia, August 10–13, 2015, pp 975–984
Wei X, Valler N, Prakash BA, Neamtiu I, Faloutsos M, Faloutsos C (2013) Competing memes propagation on networks: a case study of composite networks. IEEE J Sel Areas Commun 6(31):1049–1060
Yang J, Leskovec J (2012) Defining and evaluating network communities based on ground-truth. In: ACM SIGKDD workshop on mining data semantics. ACM, p 3
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
The original version of this article was revised: In the original publication, table row alignment was incorrectly formatted for all the tables.
Rights and permissions
About this article
Cite this article
Rapti, A., Tsichlas, K., Sioutas, S. et al. Virus propagation: threshold conditions for multiple profile networks. Knowl Inf Syst 60, 807–836 (2019). https://doi.org/10.1007/s10115-018-1274-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10115-018-1274-y