Abstract
This paper reviews Generative Adversarial Networks (GANs) in detail by discussing the strength of the GAN when compared to other generative models, how GANs works and some of the notable problems with training, tuning and evaluating GANs. The paper also briefly reviews notable GAN architectures like the Deep Convolutional Generative Adversarial Network (DCGAN), and Wasserstein GAN, with the aim of showing how design specifications in these architectures help solve some of the problems with the basic GAN model. All this is done with a view of discussing the application of GANs in cybersecurity studies. Here, the paper reviews notable cybersecurity studies where the GAN plays a key role in the design of a security system or adversarial system. In general, from the review, one can observe two major approaches these cybersecurity studies follow. In the first approach, the GAN is used to improve generalization to unforeseen adversarial attacks, by generating novel samples that resembles adversarial data which can then serve as training data for other machine learning models. In the second approach, the GAN is trained on data that contains authorized features with the goal of generating realistic adversarial data that can thus fool a security system. These two approaches currently guide the scope of modern cybersecurity studies with generative adversarial networks.


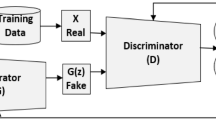
Source: Goodfellow (2016)


Source: Huang et al. (2018s)

Source: Hu and Tan (2017)
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Abadi M, Andersen DG (2016) Learning to protect communications with adversarial neural cryptography. arXiv preprint arXiv:1610.06918
Anderson HS, Woodbridge J, Filar B (2016) DeepDGA: adversarially-tuned domain generation and detection. In: Proceedings of the 2016 ACM workshop on artificial intelligence and security. ACM, pp 13–21
Apruzzese G, Colajanni M, Ferretti L, Guido A, Marchetti M (2018) On the effectiveness of machine and deep learning for cyber security. In: 2018 10th international conference on cyber conflict (CyCon). IEEE
Arjovsky M, Chintala S, Bottou L (2017) Wasserstein gan. arXiv preprint arXiv:1701.07875
Bengio Y, Thibodeau-Laufer E, Alain G, Yosinski J (2014) Deep generative stochastic networks trainable by backprop. In: ICML’2014
Biggio B, Roli F (2018) Wild patterns: ten years after the rise of adversarial machine learning. Pattern Recogn 84:317–331
Bontrager P, Togelius J, Memon N (2017) Deepmasterprint: generating fingerprints for presentation attacks. https://arxiv.org/abs/1705.07386
Chen X, Duan Y, Houthooft R, Schulman J, Sutskever I, Abbeel P (2016) Infogan: interpretable representation learning by information maximizing generative adversarial nets. In: Advances in neural information processing systems, pp 2172–2180
Denton EL, Chintala S, Fergus R (2015) Deep generative image models using a laplacian pyramid of adversarial networks. In: Advances in neural information processing systems, pp 1486–1494
Dziugaite GK, Roy DM, Ghahramani Z (2015) Training generative neural networks via maximum mean discrepancy optimization. arXiv preprint arXiv:1505.03906
Elsayed GF, Shankar S, Cheung B, Papernot N, Kurakin A, Goodfellow I, Sohl-Dickstein J (2018). Adversarial examples that fool both human and computer vision. arXiv preprint arXiv:1802.08195
Frey BJ, Hinton GE, Dayan P (1996) Does the wake-sleep algorithm produce good density estimators? In: Advances in neural information processing systems, pp 661–667
Goodfellow I (2016) NIPS 2016 tutorial: generative adversarial networks. arXiv preprint arXiv:1701.00160
Goodfellow I, Pouget-Abadie J, Mirza M, Xu B, Warde-Farley D, Ozair S, Courville A, Bengio Y (2014) Generative adversarial nets. In: Advances in neural information processing systems, pp 2672–2680
Goodfellow IJ, Shlens J, Szegedy C (2014) Explaining and harnessing adversarial examples. arXiv preprint arXiv:1412.6572
Goodfellow I, Bengio Y, Courville A, Bengio Y (2016) Deep learning, vol 1. MIT press, Cambridge
Grosse K, Papernot N, Manoharan P, Backes M, McDaniel P (2017) Adversarial examples for malware detection. In: European symposium on research in computer security. Springer, Cham, pp 62–79
Gulrajani I, Ahmed F, Arjovsky M, Dumoulin V, Courville AC, (2017) Improved training of wasserstein gans. In: Advances in neural information processing systems, pp 5767–5777
Hayes J, Melis L, Danezis G, De Cristofaro E (2019) LOGAN: membership inference attacks against generative models. Proceedings on Privacy Enhancing Technologies 2019(1):133–152
Higgins I, Matthey L, Pal A, Burgess C, Glorot X, Botvinick M, Mohamed S, Lerchner A (2016) beta-vae: learning basic visual concepts with a constrained variational framework
Hinton GE, Sejnowski TJ (1986) Learning and relearning in Boltzmann machines. Parallel distributed processing: Explorations in the microstructure of cognition 1:282–317
Hitaj B, Gasti P, Ateniese G, Perez-Cruz F (2017) Passgan: a deep learning approach for password guessing. arXiv preprint arXiv:1709.00440
Hu W, Tan Y (2017) Generating adversarial malware examples for black-box attacks based on GAN. arXiv preprint arXiv:1702.05983
Huang C, Kairouz P, Chen X, Sankar L, Rajagopal R (2018) Generative adversarial privacy. arXiv preprint arXiv:1807.05306
Hyvärinen A, Pajunen P (1999) Nonlinear independent component analysis: existence and uniqueness results. Neural Netw 12(3):429–439
Ioffe S, Szegedy C (2015) Batch normalization: accelerating deep network training by reducing internal covariate shift
Isola P, Zhu JY, Zhou T, Efros AA (2017) Image-to-image translation with conditional adversarial networks (2016). arXiv preprint arXiv:1611.07004
Kim JY, Bu SJ, Cho SB (2018) Zero-day malware detection using transferred generative adversarial networks based on deep autoencoders. Information Sci 460:83–102
Kingma DP, Ba J (2014) Adam: a method for stochastic optimization. arXiv preprint arXiv:1412.6980
Kingma DP, Salimans T, Welling M (2016) Improving variational inference with inverse autoregressive flow. In: NIPS
Kos J, Fischer I, Song D (2018) Adversarial examples for generative models. In: 2018 IEEE security and privacy workshops (SPW). IEEE, pp 36–42
Kurakin A, Goodfellow I, Bengio S (2016) Adversarial examples in the physical world. arXiv preprint arXiv:1607.02533
Ledig C, Theis L, Huszar F, Caballero J, Aitken AP, Tejani A, Totz J, Wang Z, Shi W (2016) Photo-realistic single image super-resolution using a generative adversarial network. In: CoRR, abs/1609.04802
Li H, Lin Z, Shen X, Brandt J, Hua G (2015) A convolutional neural network cascade for face detection. In: Proceedings of the IEEE conference on computer vision and pattern recognition, pp 5325–5334
Lin Z, Shi Y, Xue Z (2018) IDSGAN: generative adversarial networks for attack generation against intrusion detection. arXiv preprint arXiv:1809.02077
Lotter W, Kreiman G, Cox D (2016) Deep predictive coding networks for video prediction and unsupervised learning. arXiv preprint arXiv:1605.08104
Malhotra Y (2018) Machine intelligence: AI, machine learning, deep learning & generative adversarial networks: model risk management in operationalizing machine learning for algorithm deployment
Oord AVD, Kalchbrenner N, Kavukcuoglu K (2016) Pixel recurrent neural networks. arXiv preprint arXiv:1601.06759
Radford A, Metz L and Chintala S (2015) Unsupervised representation learning with deep convolutional generative adversarial networks. arXiv preprint arXiv:1511.06434
Rezende DJ, Mohamed S, Wierstra D (2014) Stochastic backpropagation and approximate inference in deep generative models. In: ICML’2014. Preprint: arXiv:1401.4082
Salimans T, Goodfellow I, Zaremba W, Cheung V, Radford A, Chen X (2016) Improved techniques for training gans. In: Advances in neural information processing systems, pp 2226–2234
Shi H, Dong J, Wang W, Qian Y, Zhang X (2017) Ssgan: secure steganography based on generative adversarial networks. In: Pacific Rim conference on multimedia. Springer, Cham, pp 534–544
Springenberg JT, Dosovitskiy A, Brox T, Riedmiller M (2015) Striving for simplicity: the all convolutional net. In: ICLR
Szegedy C, Zaremba W, Sutskever I, Bruna J, Erhan D, Goodfellow I, Fergus R (2013) Intriguing properties of neural networks. arXiv preprint arXiv:1312.6199
Tang W, Tan S, Li B, Huang J (2017) Automatic steganographic distortion learning using a generative adversarial network. IEEE Signal Process Lett 24(10):1547–1551
Theis L, Oord AVD, Bethge M (2015) A note on the evaluation of generative models. arXiv preprint arXiv:1511.01844
Van Den Oord A, Dieleman S, Zen H, Simonyan K, Vinyals O, Graves A, Kalchbrenner N, Senior A, Kavukcuoglu K (2016) Wavenet: a generative model for raw audio. CoRR abs/1609.03499
Yin C, Zhu Y, Liu S, Fei J, Zhang H (2018) An enhancing framework for botnet detection using generative adversarial networks. In: 2018 international conference on artificial intelligence and big data (ICAIBD). IEEE
Zeiler MD, Fergus R (2014) Visualizing and understanding convolutional networks. In: European conference on computer vision. Springer, Cham, pp 818–833
Zeiler MD, Krishnan D, Taylor GW, Fergus R (2010) Deconvolutional networks
Zhu J-Y, Krähenbühl P, Shechtman E, Efros AA (2016) Generative visual manipulation on the natural image manifold. In: European conference on computer vision. Springer, pp 597–613
Zügner D, Akbarnejad A, Günnemann S (2018) Adversarial attacks on neural networks for graph data. In: Proceedings of the 24th ACM SIGKDD international conference on knowledge discovery & data mining. ACM, pp 2847–2856
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations
Rights and permissions
About this article
Cite this article
Yinka-Banjo, C., Ugot, OA. A review of generative adversarial networks and its application in cybersecurity. Artif Intell Rev 53, 1721–1736 (2020). https://doi.org/10.1007/s10462-019-09717-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10462-019-09717-4