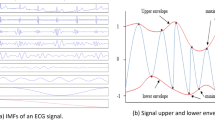
Abstract
With the advent of various security attacks, biometric authentication methods are gaining momentum in the security literature. Electrocardiogram or ECG signals are one of the essential biometric features generated by the human heart’s electrical activities. Many authentication schemes apply these signals due to their uniqueness, resistance to fabrication attacks, and support for continuous authentication. This survey article focuses on the ECG-based authentication approaches and provides the required background knowledge about the ECG signals and authentication methods. Then, it presents a taxonomy of the ECG-based authentication approaches first based on the authentication factors and then according to the applied algorithms for conducting authentication. It then describes their key contributions, applied algorithms, and possible drawbacks. Furthermore, their employed evaluation factors, ECG datasets, and simulators are illuminated and compared. Finally, the concluding remarks and future studies directions in this context are provided.






















Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Abdeldayem SS, Bourlai T (2018) ECG-based human authentication using high-level spectro-temporal signal features. In: 2018 IEEE international conference on big data (big data), pp 4984–4993
Abhishek AM, Suma H (2014) Comparison of biosignal electrocardiography (ECG), fingerprint and iris as biometrics authentication tool. In: 2014 IEEE conference on biomedical engineering and sciences (IECBES), pp 303–308
Abo-Zahhad M, Ahmed SM, Abbas SN (2014) Biometric authentication based on PCG and ECG signals: present status and future directions. SIViP 8:739–751
Abo-Zahhad M, Ahmed SM, Abbas SN (2016) A new multi-level approach to EEG based human authentication using eye blinking. Pattern Recogn Lett 82:216–225
Alizadeh M, Abolfazli S, Zamani M, Baharun S, Sakurai K (2016) Authentication in mobile cloud computing: a survey. J Netw Comput Appl 61:59–80
Arteaga-Falconi JS, Al Osman H, El Saddik A (2016) ECG authentication for mobile devices. IEEE Trans Instrum Meas 65:591–600
Arteaga-Falconi JS, Al Osman H, El Saddik A (2018) ECG and fingerprint bimodal authentication. Sustain Cities Soc 40:274–283
Ba-Hammam A, Alhulwah S, Altamimi M, Alshebeili S (2017) Authentication using ECG signals. In: 2017 international conference on electrical and computing technologies and applications (ICECTA), pp 1–4
Banerjee SP, Woodard DL (2012) Biometric authentication and identification using keystroke dynamics: a survey. J Pattern Recognit Res 7:116–139
Barra S, Casanova A, Fraschini M, Nappi M (2015) Eeg/ecg signal fusion aimed at biometric recognition. In: International conference on image analysis and processing, 2015, pp 35–42
Belgacem N, Fournier R, Nait-Ali A, Bereksi-Reguig F (2015) A novel biometric authentication approach using ECG and EMG signals. J Med Eng Technol 39:226–238
Berkaya SK, Uysal AK, Gunal ES, Ergin S, Gunal S, Gulmezoglu MB (2018) A survey on ECG analysis. Biomed Signal Process Control 43:216–235
Bhatt S, Santhanam T (2013) Keystroke dynamics for biometric authentication—a survey. In: 2013 international conference on pattern recognition, informatics and mobile engineering, pp 17–23
Bhutra G, Rasheed A, Mahapatra R (2018) Privacy-preserving ECG based active authentication (PPEA2) for IoT devices. In: 2018 IEEE 37th international performance computing and communications conference (IPCCC), pp 1–7
Butt MM, Akram U, Khan SA (2015) Denoising practices for electrocardiographic (ECG) signals: a survey. In: 2015 international conference on computer, communications, and control technology (I4CT), pp 264–268
Cai H, Venkatasubramanian KK (2016) Fusion of electrocardiogram and arterial blood pressure signals for authentication in wearable medical systems. In: IEEE conference on computer and network systems CNS workshop, 2016, pp 1–5
Camara C, Peris-Lopez P, Tapiador JE (2015) Human identification using compressed ECG signals. J Med Syst 39:148
Camara C, Peris-Lopez P, Gonzalez-Manzano L, Tapiador J (2018) Real-time electrocardiogram streams for continuous authentication. Appl Soft Comput 68:784–794
Chamatidis I, Katsika A, Spathoulas G (2017) Using deep learning neural networks for ECG based authentication. In: 2017 international Carnahan conference on security technology (ICCST), pp 1–6
Chatterjee S, Changawala N (2010) Fragmented QRS complex: a novel marker of cardiovascular disease. Clin Cardiol 33:68–71
Chaudhry SA, Mahmood K, Naqvi H, Khan MK (2015) An improved and secure biometric authentication scheme for telecare medicine information systems based on elliptic curve cryptography. J Med Syst 39:175
Chen Y, Chen W (2017) Finger ECG-based authentication for healthcare data security using artificial neural network. In: 2017 IEEE 19th international conference on e-health networking, applications and services (Healthcom), pp 1–6
Chen Y, Chen W (2018) Finger ECG based two-phase authentication using 1D convolutional neural networks. In: 2018 40th annual international conference of the IEEE engineering in medicine and biology society (EMBC), pp 336–339
Choudhary T, Manikandan MS (2015) A novel unified framework for noise-robust ECG-based biometric authentication. In: 2015 2nd international conference on signal processing and integrated networks (SPIN), pp 186–191
Chu Y, Shen H, Huang K (2019) ECG authentication method based on parallel multi-scale one-dimensional residual network with center and margin loss. IEEE Access 7:51598–51607
Chun SY (2016) Small scale single pulse ECG-based authentication using GLRT that considers T wave shift and adaptive template update with prior information. In: 23rd international conference on pattern recognition (ICPR), 2016, pp 3043–3048
Chun SY (2016) Single pulse ECG-based small scale user authentication using guided filtering. In: 2016 international conference on biometrics (ICB), pp 1–7
Chun SY, Kang J-H, Kim H, Lee C, Oakley I, Kim S-P (2016) ECG based user authentication for wearable devices using short time Fourier transform. In: 2016 39th international conference on telecommunications and signal processing (TSP), pp 656–659
Cirrincione G, Randazzo V, Pasero E (2020) A neural based comparative analysis for feature extraction from ECG signals. In: Esposito A, Faundez-Zanuy M, Morabito F, Pasero E (eds) Neural approaches to dynamics of signal exchanges. Smart innovation, systems and technologies, vol 151. Springer, Singapore, pp 247–256
Coutinho DP, Fred AL, Figueiredo MA (2011) ECG-based continuous authentication system using adaptive string matching. In: Biosignals, 2011, pp 354–359
Dey N, Mukhopadhyay S, Das A, Chaudhuri SS (2012) Analysis of P-QRS-T components modified by blind watermarking technique within the electrocardiogram signal for authentication in wireless telecardiology using DWT. Int J Image Graph Signal Process 4:33
Dey M, Dey N, Mahata SK, Chakraborty S, Acharjee S, Das A (2014) Electrocardiogram feature based inter-human biometric authentication system. In: 2014 international conference on electronic systems, signal processing and computing technologies (ICESC), pp 300–304
Dhanush M, Jain A, Moulyashree S, Melkot A, Manjula A (2016) ECG based authentication using autocorrelation and artificial neural networks. In: International conference on computing, analytics and security trends (CAST), 2016, pp 238–243
Diker A, Avci E, Tanyildizi E, Gedikpinar M (2020) A novel ECG signal classification method using DEA-ELM. Med Hypotheses 136:109515
Dinakarrao SMP, Jantsch A, Shafique M (2019) Computer-aided arrhythmia diagnosis with bio-signal processing: a survey of trends and techniques. ACM Comput Surv (CSUR) 52:23
do Vale Madeiro JP, Marques JAL, Han T, Pedrosa RC (2020) Evaluation of mathematical models for QRS feature extraction and QRS morphology classification in ECG signals. Measurement 156:107580
Eastwood SC, Shmerko VP, Yanushkevich SN, Drahansky M, Gorodnichy DO (2015) Biometric-enabled authentication machines: a survey of open-set real-world applications. IEEE Trans Hum Mach Syst 46:231–242
Farash MS, Chaudhry SA, Heydari M, Sajad Sadough SM, Kumari S, Khan MK (2017) A lightweight anonymous authentication scheme for consumer roaming in ubiquitous networks with provable security. Int J Commun Syst 30:e3019
Ferrag MA, Maglaras LA, Janicke H, Jiang J, Shu L (2017) Authentication protocols for internet of things: a comprehensive survey. Secur Commun Netw. https://doi.org/10.1155/2017/6562953
Ferrag MA, Maglaras L, Argyriou A, Kosmanos D, Janicke H (2018) Security for 4G and 5G cellular networks: a survey of existing authentication and privacy-preserving schemes. J Netw Comput Appl 101:55–82
Gia TN, Jiang M, Rahmani A-M, Westerlund T, Liljeberg P, Tenhunen H (2015) Fog computing in healthcare internet of things: a case study on ecg feature extraction. In: 2015 IEEE international conference on computer and information technology; ubiquitous computing and communications; dependable, autonomic and secure computing; pervasive intelligence and computing, pp 356–363
Grover K, Lim A (2015) A survey of broadcast authentication schemes for wireless networks. Ad Hoc Netw 24:288–316
Hammad M, Wang K (2019) Parallel score fusion of ECG and fingerprint for human authentication based on convolution neural network. Comput Secur 81:107–122
Hammad M, Luo G, Wang K (2019a) Cancelable biometric authentication system based on ECG. Multimed Tools Appl 78:1857–1887
Hammad M, Liu Y, Wang K (2019b) Multimodal biometric authentication systems using convolution neural network based on different level fusion of ECG and fingerprint. IEEE Access 7:26527–26542
He D, Zeadally S, Kumar N, Wu W (2016) Efficient and anonymous mobile user authentication protocol using self-certified public key cryptography for multi-server architectures. IEEE Trans Inf Forensics Secur 11:2052–2064
Hegde C, Prabhu HR, Sagar D, Shenoy PD, Venugopal K, Patnaik LM (2010) Human authentication based on ECG waves using radon transform. In: Fang WC, Arnett M, Slezak H (eds) Security technology, disaster recovery and business continuity. Springer, New York, pp 197–206
Hegde C, Prabhu HR, Sagar D, Shenoy PD, Venugopal K, Patnaik LM (2011) Statistical analysis for human authentication using ECG waves. In: International conference on information intelligence, systems, technology and management, pp 287–298
Heidbüchel H, La Gerche A (2012) The right heart in athletes. Herzschrittmachertherapie Elektrophysiologie 23:82–86
Hejazi M, Al-Haddad SAR, Singh YP, Hashim SJ, Aziz AFA (2016) ECG biometric authentication based on non-fiducial approach using kernel methods. Digit Signal Proc 52:72–86
Hsiao C-C, Wang S-W, Lin R, Lee R-G (2016) Multiple biometric authentication for personal identity using wearable device. In: 2016 IEEE international conference on systems, man, and cybernetics (SMC), pp 000673–000678
Huang P, Li B, Guo L, Jin Z, Chen Y (2016) A robust and reusable ecg-based authentication and data encryption scheme for ehealth systems. In: 2016 IEEE global communications conference (GLOBECOM), pp 1–6
John B, Jörg S, Koppal S, Jain E (2020) The security-utility trade-off for iris authentication and eye animation for social virtual avatars. IEEE Trans Visual Comput Graphics 26:1880–1890
Jung W-H, Lee S-G (2017) ECG identification based on non-fiducial feature extraction using window removal method. Appl Sci 7:1205
Kang D, Woo J, Kuo CJ, Slomka PJ, Dey D, Germano G (2012) Heart chambers and whole heart segmentation techniques. J Electron Imaging 21:010901
Kang SJ, Lee SY, Cho HI, Park H (2016) Ecg authentication system design based on signal analysis in mobile and wearable devices. IEEE Signal Process Lett 23:805–808
Karegar FP, Fallah A, Rashidi S (2017a) ECG based human authentication with using generalized Hurst exponent. In: 2017 Iranian conference on electrical engineering (ICEE), pp 34–38
Karegar FP, Fallah A, Rashidi S (2017b) Using recurrence quantification analysis and generalized hurst exponents of ECG for human authentication. In: 2nd conference on swarm intelligence and evolutionary computation (CSIEC), 2017, pp 66–71
Karimian N, Wortman PA, Tehranipoor F (2016) Evolving authentication design considerations for the internet of biometric things (IoBT). In: Proceedings of the eleventh IEEE/ACM/IFIP international conference on hardware/software codesign and system synthesis, 2016, p 10
Karimian N, Tehranipoor M, Forte D (2017) Non-fiducial ppg-based authentication for healthcare application. In: 2017 IEEE EMBS international conference on biomedical & health informatics (BHI), pp 429–432
Kataria AN, Adhyaru DM, Sharma AK, Zaveri TH (2013) A survey of automated biometric authentication techniques. In: 2013 Nirma university international conference on engineering (NUiCONE), pp 1–6
Kaul A, Arora A, Chauhan S (2012) ECG based human authentication using synthetic ECG template. In: 2012 IEEE international conference on signal processing, computing and control (ISPCC), pp 1–4
Keshishzadeh S, Rashidi S (2014) A system of biometric authentication based on ECG signal segmentation. In: 2014 22nd Iranian conference on electrical engineering (ICEE), pp 1873–1877
Khalil I, Sufi F (2008) Legendre polynomials based biometric authentication using QRS complex of ECG. In: International conference on intelligent sensors, sensor networks and information processing, 2008. ISSNIP 2008, pp 297–302
Khattri V, Nayak SK, Singh DK (2020) Development of integrated distance authentication and fingerprint authorization mechanism to reduce fraudulent online transaction. In: Basha M et al (eds) Intelligent communication, control and devices. Springer, Singapore, pp 73–83
Kilinc HH, Yanik T (2013) A survey of SIP authentication and key agreement schemes. IEEE Commun Surv Tutor 16:1005–1023
Kim HJ, Lim JS (2018) Study on a biometric authentication model based on ECG using a fuzzy neural network. In: IOP conference series: materials science and engineering, p 012030
Kumar U, Gambhir S (2020) KDFBA: key distribution through fingerprint based authentication using mobile agent. Multimed Tools Appl 79:13891–13918
Kurogi T, Yamaba H, Aburada K, Katayama T, Park M, Okazaki N (2018) A study on a user identification method using dynamic time warping to realize an authentication system by s-EMG. In: International conference on emerging internetworking, data & web technologies, pp 889–900
Labati RD, Sassi R, Scotti F (2013) ECG biometric recognition: permanence analysis of QRS signals for 24 hours continuous authentication. In: 2013 IEEE international workshop on information forensics and security (WIFS), pp 31–36
Li X, Niu J, Kumari S, Wu F, Sangaiah AK, Choo K-KR (2018) A three-factor anonymous authentication scheme for wireless sensor networks in internet of things environments. J Netw Comput Appl 103:194–204
Liao X, Qin Z, Ding L (2017) Data embedding in digital images using critical functions. Sig Process Image Commun 58:146–156
Liao X, Yu Y, Li B, Li Z, Qin Z (2019) A new payload partition strategy in color image steganography. In: IEEE transactions on circuits and systems for video technology
Louis W, Komeili M, Hatzinakos D (2016) Continuous authentication using one-dimensional multi-resolution local binary patterns (1DMRLBP) in ECG biometrics. IEEE Trans Inf Forensics Secur 11:2818–2832
Luz EJDS, Schwartz WR, Cámara-Chávez G, Menotti D (2016) ECG-based heartbeat classification for arrhythmia detection: a survey. Comput Methods Programs Biomed 127:144–164
Mahfouz A, Mahmoud TM, Eldin AS (2017) A survey on behavioral biometric authentication on smartphones. J Inf Secur Appl 37:28–37
Manvi SS, Tangade S (2017) A survey on authentication schemes in VANETs for secured communication. Veh Commun 9:19–30
Masdari M, Ahmadzadeh S (2016) Comprehensive analysis of the authentication methods in wireless body area networks. Secur Commun Netw 9:4777–4803
Masdari M, Ahmadzadeh S (2017) A survey and taxonomy of the authentication schemes in telecare medicine information systems. J Netw Comput Appl 87:1–19
Masdari M, Naghiloo F (2017) Fuzzy logic-based sink selection and load balancing in multi-sink wireless sensor networks. Wireless Pers Commun 97:2713–2739
Masdari M, Bazarchi SM, Bidaki M (2013) Analysis of secure LEACH-based clustering protocols in wireless sensor networks. J Netw Comput Appl 36:1243–1260
Masdari M, Ahmadzadeh S, Bidaki M (2017) Key management in wireless body area network: challenges and issues. J Netw Comput Appl 91:36–51
Molina GG, Bruekers F, Presura C, Damstra M, Van Der Veen M (2007) Morphological synthesis of ECG signals for person authentication. In: Signal processing conference, 2007 15th European, pp 738–742
Mu Z, Hu J, Min J (2016) EEG-based person authentication using a fuzzy entropy-related approach with two electrodes. Entropy 18:432
Muhammad M, Safdar GA (2018) Survey on existing authentication issues for cellular-assisted V2X communication. Veh Commun 12:50–65
Mukherjee A, Dey G, Dey M, Dey N (2015) Web-based intelligent EEG signal authentication and tamper detection system for secure telemonitoring. In: Hassanien A, Azar A (eds) Brain-computer interfaces. Springer, Cham
Nguyen B, Nguyen D, Ma W, Tran D (2017) Investigating the possibility of applying EEG lossy compression to EEG-based user authentication. In: 2017 international joint conference on neural networks (IJCNN), pp 79–85
Page A, Kulkarni A, Mohsenin T (2015) Utilizing deep neural nets for an embedded ECG-based biometric authentication system. In: 2015 IEEE biomedical circuits and systems conference (BioCAS), pp 1–4
Pal S, Mitra M (2011) ECG based biometric authentication-a novel data modelling approach. In: 2011 international conference on image information processing (ICIIP), pp 1–4
Peris-Lopez P, González-Manzano L, Camara C, de Fuentes JM (2018) Effect of attacker characterization in ECG-based continuous authentication mechanisms for Internet of Things. Future Gener Comput Syst 81:67–77
Peter S, Pratap Reddy B, Momtaz F, Givargis T (2016) Design of secure ECG-based biometric authentication in body area sensor networks. Sensors 16:570
Piper A (2013) How to write a systematic literature review: a guide for medical students. Natl AMR Fostering Med Res 1–8
Prakasha K, Muniyal B (2016) Electrocardiogram-Kerberos authentication scheme for secure services. In International conference on inventive computation technologies (ICICT), 2016, pp 1–4
Rehman A, Saqib NA, Danial SM, Ahmed SH (2017) ECG based authentication for remote patient monitoring in IoT by wavelets and template matching. In: 2017 8th IEEE international conference on software engineering and service science (ICSESS), pp 91–94
Rehman A, Saqib NA, Danial SM, Ahmed SH (2017) ECG based authentication for remote patient monitoring in IoT by wavelets and template matching
Rezgui D, Lachiri Z (2016) ECG biometric recognition using SVM-based approach. IEEJ Trans Electr Electron Eng 11:S94–S100
Safie S (2019) ECG slope features for biometric authentication. In: 2018 IEEE 5th international conference on smart instrumentation, measurement and application (ICSIMA), pp 1–5
Safie SI, Soraghan JJ, Petropoulakis L (2011a) Pulse active ratio (PAR): a new feature extraction technique for ECG biometric authentication. In: 2011 IEEE international conference on signal and image processing applications (ICSIPA), pp 16–21
Safie SI, Soraghan JJ, Petropoulakis L (2011b) Electrocardiogram (ECG) biometric authentication using pulse active ratio (PAR). IEEE Trans Inf Forensics Secur 6:1315–1322
Safie SI, Soraghan JJ, Petropoulakis L (2011c) Pulse active bit (PAB) feature extractor for ECG biometric authentication. In: 2011 18th international conference on systems, signals and image processing (IWSSIP), pp 1–4
Safie SI, Soraghan JJ, Petropoulakis L (2011d) ECG biometric authentication using pulse active width (PAW). In: 2011 IEEE workshop on biometric measurements and systems for security and medical applications (BIOMS), pp 1–6
Safie SI, Soraghan JJ, Petropoulakis L (2011e) ECG based biometric for doubly secure authentication. In: 2011 19th European signal processing conference, pp 2274–2278
Safie S, Haris N, Zainal A, Soraghan J, Petropoulakis L (2013) Pulse active harmonic (PAH) features for ECG biometric authentication. In: 2013 1st international conference on artificial intelligence, modelling and simulation (AIMS), pp 255–260
Safie S, Yusof M, Kadir K, Nasir H, Petropoulakis L (2014) Multiple pulse K-nearest neighbors authentication for malay ECG based class attendance system. In: 2014 4th international conference on engineering technology and technopreneuship (ICE2T), pp 156–160
Safie SI, Nurfazira H, Azavitra Z, Soraghan JJ, Petropoulakis L (2014) Pulse active transform (PAT): a non-invertible transformation with application to ECG biometric authentication. In: 2014 IEEE region 10 symposium, pp 667–671
Sahoo SS, Mohanty S (2018) A lightweight biometric-based authentication scheme for telecare medicine information systems using ECC. In: 2018 9th international conference on computing, communication and networking technologies (ICCCNT), pp 1–6
Sangaiah AK, Arumugam M, Bian G-B (2020) An intelligent learning approach for improving ECG signal classification and arrhythmia analysis. Artif Intell Med 103:101788
Santos A, Medeiros I, Resque P, Rosário D, Nogueira M, Santos A, Cerqueira E, Chowdhury KR (2018) ECG-based user authentication and identification method on VANETs. In: Proceedings of the 10th Latin America networking conference, 2018, pp 119–122
Sarkar A, Abbott AL, Doerzaph Z (2015) ECG biometric authentication using a dynamical model. In: 2015 IEEE 7th international conference on biometrics theory, applications and systems (BTAS), pp 1–6
Simplicio MA Jr, De Oliveira BT, Margi CB, Barreto PS, Carvalho TC, Näslund M (2013) Survey and comparison of message authentication solutions on wireless sensor networks. Ad Hoc Netw 11:1221–1236
Singh YN, Singh SK, Gupta P (2012) Fusion of electrocardiogram with unobtrusive biometrics: an efficient individual authentication system. Pattern Recogn Lett 33:1932–1941
Singh K, Singhvi A, Pathangay V (2015) Dry contact fingertip ECG-based authentication system using time, frequency domain features and support vector machine. In: Engineering in medicine and biology society (EMBC), 2015 37th annual international conference of the IEEE, pp 526–529
Smith-Creasey M, Rajarajan M (2019) A novel word-independent gesture-typing continuous authentication scheme for mobile devices. Comput Secur 83:140–150
Soraghan J, Petropoulakis L, Haris N, Safie S, Zainal A (2015) Comparison of pulse active (PA) modulation signal for electrocardiogram (ECG) authentication
Šprager S, Trobec R, Jurič MB (2017) Feasibility of biometric authentication using wearable ECG body sensor based on higher-order statistics. In: 2017 40th international convention on information and communication technology, electronics and microelectronics (MIPRO), pp 264–269
Sriram JC, Shin M, Choudhury T, Kotz D (2009) Activity-aware ECG-based patient authentication for remote health monitoring. In: Proceedings of the 2009 international conference on multimodal interfaces, pp 297–304
Sufi F, Khalil I, Hu J (2010a) ECG-based authentication. In: Stavroulakis P, Stamp M (eds) Handbook of information and communication security. Springer, Berlin, pp 309–331
Sufi F, Khalil I, Habib I (2010b) Polynomial distance measurement for ECG based biometric authentication. Secur Commun Netw 3:303–319
Sung D, Kim J, Koh M, Park K (2017) ECG authentication in post-exercise situation. In: Engineering in medicine and biology society (EMBC), 2017 39th annual international conference of the IEEE, pp 446–449
Teh PS, Zhang N, Teoh ABJ, Chen K (2016) A survey on touch dynamics authentication in mobile devices. Comput Secur 59:210–235
Vyas R, Kanumuri T, Sheoran G, Dubey P (2020) Smartphone based iris recognition through optimized textural representation. Multimed Tools Appl 79:14127–14146
Wu Q, Zeng Y, Zhang C, Tong L, Yan B (2018) An EEG-based person authentication system with open-set capability combining eye blinking signals. Sensors 18:335
Xu X, Liu H (2020) ECG heartbeat classification using convolutional neural networks. IEEE Access 8:8614–8619
Sanjana G. Human authentication based on ECG imaging
Zaghouani EK, Benzina A, Attia R (2017) ECG based authentication for e-healthcare systems: towards a secured ECG features transmission. In: 2017 13th international wireless communications and mobile computing conference (IWCMC), pp 1777–1783
Zebboudj S, Cherifi F, Mohammedi M, Omar M (2017) Secure and efficient ECG-based authentication scheme for medical body area sensor networks. Smart Health 3:75–84
Zeng Y, Wu Q, Yang K, Tong L, Yan B, Shu J, Yao D (2019) EEG-based identity authentication framework using face rapid serial visual presentation with optimized channels. Sensors 19:6
Zhang Y, Wu J (2016) Practical human authentication method based on piecewise corrected electrocardiogram. In: 7th IEEE international conference on software engineering and service science (ICSESS), 2016, pp 300–303
Zhang Z, Wang H, Vasilakos AV, Fang H (2012) ECG-cryptography and authentication in body area networks. IEEE Trans Inf Technol Biomed 16:1070–1078
Zhang Y, Gravina R, Lu H, Villari M, Fortino G (2018) PEA: parallel electrocardiogram-based authentication for smart healthcare systems. J Netw Comput Appl 117:10–16
Zhang J, Tian J, Cao Y, Yang Y, Xu X (2020) Deep time–frequency representation and progressive decision fusion for ECG classification. Knowl Based Syst 190:105402
Zhao Z, Zhang Y, Deng Y, Zhang X (2018) ECG authentication system design incorporating a convolutional neural network and generalized S-transformation. Comput Biol Med 102:168–179
Zheng G, Fang G, Shankaran R, Orgun MA, Zhou J, Qiao L, Saleem K (2016) Multiple ECG fiducial points-based random binary sequence generation for securing wireless body area networks. IEEE J Biomed Health Inf 21:655–663
Author information
Authors and Affiliations
Corresponding authors
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Hosseinzadeh, M., Vo, B., Ghafour, M.Y. et al. Electrocardiogram signals-based user authentication systems using soft computing techniques. Artif Intell Rev 54, 667–709 (2021). https://doi.org/10.1007/s10462-020-09863-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10462-020-09863-0