Abstract
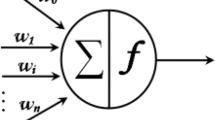
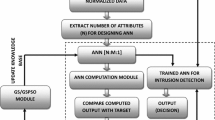
Building an intrusion detection system (IDS) has become an increasingly urgent issue for detecting network security breaches in computer and network systems. However, an effective and flexible IDS is imperative. In this paper, a new natural evolutionary algorithm (EA) called multiverse optimizer (MVO) is investigated and combined with an artificial neural network (ANN) to develop advanced detection approaches for an IDS. Under this context, the combination of ANN and EA produce evolutionary neural network (ENN). ENN makes this combination a new improved system for solving problems encountered by ANNs. The main idea of this work is to use an MVO to train a feed forward multilayer artificial neural network (MVO-ANN) to identify new attacks. This approach is applied to NSL-KDD and the new benchmark dataset called UNSW-NB15. In this manner, the effectiveness of our approach on detecting various forms of attack is demonstrated. Our results using UNSW-NB15 is better than those that were obtained using NSL-KDD. Furthermore, the efficacy of our proposed method is confirmed by performing better when compared to other well-known heuristic-based approaches such as practical swarm optimizer and artificial neural network (PSO-ANN).








Similar content being viewed by others
References
Ahmed M, Mahmood AN, Hu J (2016) A survey of network anomaly detection techniques. J Netw Comput Appl 60(C): 19–31
Ali EE, El-Hameed MA, El-Fergany AA, El-Arini MM (2016) Parameter extraction of photovoltaic generating units using multi-verse optimizer. Sustainable Energy Technol Assess 17:68–76
Bamakan SMH, Amiri B, Mirzabagheri M, Shi Y (2015) A new intrusion detection approach using pso based multiple criteria linear programming. Procedia Comput Sci 55:231–237
Ding S, Li H, Su C, Yu J, Jin F (2013) Evolutionary artificial neural networks: a review. Artif Intell Rev 39(3):251–260
Enache AC, Patriciu VV (2014) Intrusions detection based on support vector machine optimized with swarm intelligence. In: 2014 IEEE 9th IEEE international symposium on applied computational intelligence and informatics (SACI), pp 153–158
Gonzalez F, Gomez J, Kaniganti M, Dasgupta D (2003) An evolutionary approach to generate fuzzy anomaly (attack) signatures. In: IEEE systems man and cybernetics society information assurance workshop, 2003, pp 251–259
Han S-J, Cho S-B (2005) Evolutionary neural networks for anomaly detection based on the behavior of a program. IEEE Trans Syst Man Cybern B Cybern 36(3):559–570
Hofmann A, Sick B (2003) Evolutionary optimization of radial basis function networks for intrusion detection. In: Proceedings of the international joint conference on neural networks, 2003., vol 1, vol 1, pp 415–420
Lee W, Stolfo SJ, Mok KW (2000) Adaptive intrusion detection: A data mining approach. Artif Intell Rev 14(6):533–567
Li J, Zhang G-Y, Gu G-C (2004) The research and implementation of intelligent intrusion detection system based on artificial neural network. In: Proceedings of 2004 International Conference on Machine Learning and Cybernetics (IEEE Cat. No.04EX826), vol 5, pp 3178–3182
Lin W-C, Ke S-W, Tsai C-F (2015) Cann: An intrusion detection system based on combining cluster centers and nearest neighbors. Knowl-Based Syst 78:13–21
Michailidis E, Katsikas SK, Georgopoulos E (2008) Intrusion detection using evolutionary neural networks. In: 2008 Panhellenic Conference on Informatics, pp 8–12
Mirjalili S, Mirjalili SM, Hatamlou A (2016) Multi-verse optimizer: a nature-inspired algorithm for global optimization. Neural Comput Applic 27(2):495–513
Moradi M, Zulkernine M (2004) A neural network based system for intrusion detection and classification of attacks. In: Proceedings of the IEEE international conference on advances in intelligent systems, pp 15–18
Moustafa N, Slay J (2015) Unsw-nb15: a comprehensive data set for network intrusion detection systems (unsw-nb15 network data set). In: 2015 military communications and information systems conference (MilCIS), pp 1–6
Moustafa N, Slay J (2015) The significant features of the unsw-nb15 and the kdd99 data sets for network intrusion detection systems. In: 2015 4th international workshop on building analysis datasets and gathering experience returns for security (BADGERS), pp 25–31. IEEE
Moustafa N, Slay J (2016) The evaluation of network anomaly detection systems: Statistical analysis of the unsw-nb15 data set and the comparison with the kdd99 data set. Inf Secur J A Global Perspect 25(1-3):18–31
NSLKDD (2013) Nsl-kdd dataset, retrieved from http://nsl.cs.unb.ca/NSL-KDD
Rastegari S (2015) Intelligent network intrusion detection using an evolutionary computation approach
Ryan J, Lin M-J, Miikkulainen R (1998) Intrusion detection with neural networks. In: Jordan MI, Kearns MJ, Solla SA (eds) Advances in Neural Information Processing Systems 10, pages 943–949. MIT Press
Sammany M, Sharawi M, El-Beltagy M, Saroit I (2007) Artificial neural networks architecture for intrusion detection systems and classification of attacks. In: The 5th international conference INFO2007, pp 24–26
Shuhui LI (2010) Improved evolutionary neural network algorithm and its applications in intrusion detection. Mod Electron Technique 1:028
Tavallaee M, Bagheri E, Lu W, Ghorbani AA (2009) A detailed analysis of the kdd cup 99 data set. In: Proceedings of the 2nd IEEE international conference on computational intelligence for security and defense applications, CISDA’09, pp 53–58, Piscataway, NJ, USA. IEEE Press
the Cyber Range Lab of the Australian Centre for Cyber Security (ACCS) (2015) Unsw-nb15 dataset, retrieved from http://www.accs.unsw.adfa.edu.au/
Wang L, Yu G, Wang G, Wang D (2001) Method of evolutionary neural network-based intrusion detection. In: 2001 International Conferences on Info-Tech and Info-Net. Proceedings (Cat. No.01EX479), vol 5, pp 13–18
Witten IH, Frank E, Hall MA (2011). In: Witten IH, Frank E, Hall MA (eds) Data Mining: Practical Machine Learning Tools and Techniques (3rd Edition), The Morgan Kaufmann Series in Data Management Systems. Morgan Kaufmann, Boston, third edition
Wu SX, Banzhaf W (2010) The use of computational intelligence in intrusion detection systems: A review. Appl Soft Comput 10(1):1–35
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Benmessahel, I., Xie, K. & Chellal, M. A new evolutionary neural networks based on intrusion detection systems using multiverse optimization. Appl Intell 48, 2315–2327 (2018). https://doi.org/10.1007/s10489-017-1085-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10489-017-1085-y