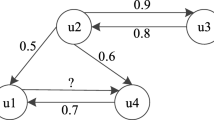
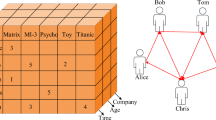
Abstract
User-based collaborative filtering is widely used in recommendation systems, which normally comprises three steps: (1) finding the nearest conceptual neighbors, (2) aggregating the neighbors’ ratings to predict the ratings of unrated items, and (3) generating recommendations based on the prediction. Existing algorithms mainly focus on steps 1 and 3 but neglect subtle treatments of aggregating neighbors’ suggestions in step 2. Based on the discovery of psychology that (i) users’ responses to positive and negative suggestions are different, and (ii) users may respond differently from one another, this paper proposes a Personal Asymmetry Response-based Suggestions Aggregation (PARSA) algorithm, which first uses a linear regression method to learn each user’s response to negative/positive suggestions from neighbors and then uses a gradient descent algorithm for optimizing them. In addition, this paper designs an Identical Asymmetry Response-based Suggestions Aggregation (IARSA) baseline algorithm, which assumes that all the users’ responses to suggestions are identical as references to verify the key contribution of the heuristics employed in our PARSA algorithm that user may responses differently to positive and negative suggestions. Three sets of experiments are designed and implemented over two real-life datasets (i.e., Eachmovie and Netflix) to evaluate the performance of our algorithms. Further, in order to eliminate the influence of different similarity measures, this paper selects three kinds of similarity measures to discover neighbors. Experimental results demonstrate that most people indeed pay more attention to negative suggestions and our algorithms achieve better prediction and recommendation performances than the compared algorithms under various similarity measures.









Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Teng Y, He L (2012, April) Rating prediction algorithm and recommendation based on user behavior in IPTV. In: 2012 2nd International conference on consumer electronics, communications and networks (CECNet). IEEE, pp. 3373–3378
Ye L, Wu C, L Mi (2017) Collaborative filtering recommendation based on trust model with fused similar factor. In: MATEC Web of Conferences. Vol. 139, pp. 00010
Anderson NH (1974) Cognitive algebra: integration theory applied to social attribution. In: Advances in experimental social psychology, vol 7. Academic, Amsterdam, pp 1–101
Frodi AM, Lamb ME, Leavitt LA, Donovan WL (1978) Fathers’ and mothers’ responses to infant smiles and cries. Infant Behav Dev 1:187–198
Fiske ST (1980) Attention and weight in person perception: the impact of negative and extreme behavior. J Pers Soc Psychol 38(6):889–906
Hamilton DL, Zanna MP (1972) Differential weighting of favorable and unfavorable attributes in impressions of personality. J Res Pers 6:2–3
Pratto F, John OP (1991) Automatic vigilance: the attention-grabbing power of negative social information. J Pers Soc Psychol 61(3):380–391
Lu J, Wu D, Mao M, Wang W, Zhang G (2015) Recommender system application developments: a survey. Decis Support Syst 74:12–32
Bobadilla J, Ortega F, Hernando A, Gutiérrez A (2013) Recommender systems survey. Knowl-Based Syst 46:109–132
Shi Y, Larson M, Hanjalic A (2009, October) Exploiting user similarity based on rated-item pools for improved user-based collaborative filtering. In: Proceedings of the third ACM conference on recommender systems. ACM, pp. 125–132
Sarwar BM, Karypis G, Konstan JA, Riedl J (2001) Item-based collaborative filtering recommendation algorithms. Proceedings of the 10th international conference on World Wide Web 1:285–295
Li W, Xu H, Ji M, Xu Z, Fang H (2016, October) A hierarchy weighting similarity measure to improve user-based collaborative filtering algorithm. In: 2016 2nd IEEE International conference on computer and communications (ICCC). IEEE, pp. 843–846
Azadjalal MM, Moradi P, Abdollahpouri A, Jalili M (2017) A trust-aware recommendation method based on Pareto dominance and confidence concepts. Knowl-Based Syst 116:130–143
Frolov E, Oseledets I (2016, September) Fifty shades of ratings: how to benefit from a negative feedback in top-N recommendations tasks. In: Proceedings of the 10th ACM conference on recommender systems. ACM, pp. 91–98
Hu Y, Shi W, Li H, Hu X (2017) Mitigating data sparsity using similarity reinforcement-enhanced collaborative filtering. ACM Transactions on Internet Technology (TOIT) 17(3):31
Liu H, Hu Z, Mian A, Tian H, Zhu X (2014) A new user similarity model to improve the accuracy of collaborative filtering. Knowl-Based Syst 56:156–166
Li, Q., Lin, Z., & Fei, Z. (2016). Similarity coefficient of collaborative filtering based on contribution of neighbors. In: 2016 International conference on machine learning and cybernetics (ICMLC), Vol. 1. IEEE, pp. 226–232
Lee WP, Ma CY (2016) Enhancing collaborative recommendation performance by combining user preference and trust-distrust propagation in social networks. Knowl-Based Syst 106:125–134
Mahara T (2016) A new similarity measure based on mean measure of divergence for collaborative filtering in sparse environment. Proc Comput Sci 89:450–456
Srikanth T, Shashi M (2015) A new similarity measure for user-based collaborative filtering in recommender systems. Int J Comput Technol 14:6118–6128
Wu X, Cheng B, Chen J (2015) Collaborative filtering service recommendation based on a novel similarity computation method. IEEE Trans Serv Comput 10(3):352–365
Wang Y, Deng J, Gao J, Zhang P (2017) A hybrid user similarity model for collaborative filtering. Inf Sci 418:102–118
Zang X, Liu T, Qiao S, Gao W, Wang J, Sun X, Zhang B (2016, June) A new weighted similarity method based on neighborhood user contributions for collaborative filtering. In: 2016 IEEE first international conference on data science in cyberspace (DSC). IEEE, pp. 376–381
Zeng W, Shang MS (2010). Effects of negative ratings on personalized recommendation. In: 2010 5th International conference on computer science & education. IEEE, pp. 375–379
Liang LI, Yu-Xin D, Chun-Hui Z, Wei-Jie C (2017) Collaborative filtering recommendation algorithm combined with user trust. J Chn Comput Syst 38(5):951–955
Lu K, Xie L, Li MC (2016) Research on implied-trust aware collaborative filtering recommendation algorithm. J Chn Comput Syst 37(2):241–245
Costa PT Jr, Terracciano A, McCrae RR (2001) Gender differences in personality traits across cultures: robust and surprising findings. J Pers Soc Psychol 81(2):322
Wang X, Ji SJ, Liang YQ, Leung HF, Chiu DK (2019) An unsupervised strategy for defending against multifarious reputation attacks. Appl Intell 49:4189–4210
Wang J, Wen Y, Gou Y, Ye Z, Chen H (2017) Fractional-order gradient descent learning of BP neural networks with Caputo derivative. Neural Netw 89:19–30
Wu W, Zhao J, Zhang C, Meng F, Zhang Z, Zhang Y, Sun Q (2017) Improving performance of tensor-based context-aware recommenders using Bias tensor factorization with context feature auto-encoding. Knowl-Based Syst 128:71–77
Xu XY, Liu JM (2016) Collaborative filtering recommendation algorithm based on multi-level item similarity. Comput Sci 34:262–265
Chao C, Qu S, Du T (2014) Research of collaborative filtering recommendation algorithm for short text. J Comput Commun 2(14):59
Ziegler CN, McNee SM, Konstan JA, Lausen G (2005) Improving recommendation lists through topic diversification. In Proceedings of the 14th international conference on World Wide Web. ACM, pp. 22–32
Ge M, Delgado-Battenfeld C, Jannach D (2010, September) Beyond accuracy: evaluating recommender systems by coverage and serendipity. In: Proceedings of the fourth ACM conference on recommender systems. ACM, pp. 257–260
Yera R, Martinez L (2017) Fuzzy tools in recommender systems: a survey. Int J Computation Intell Syst 10(1):776–803
Chiu DK, Leung HF, Lam KM (2009) On the making of service recommendations: an action theory based on utility, reputation, and risk attitude. Expert Syst Appl 36(2):3293–3301
Ji SJ, Ma HY, Zhang SL, Leung HF, Chiu D, Zhang CJ, Fang XW (2016) A pre-evolutionary advisor list generation strategy for robust defensing reputation attacks. Knowl-Based Syst 103:1–18
Ji S, Ma H, Liang Y, Leung H, Zhang C (2017) A whitelist and blacklist-based co-evolutionary strategy for defensing against multifarious trust attacks. Appl Intell 47(4):1115–1131
Hung PC, Chiu DK, Fung WW, Cheung WK, Wong R, Choi SP, Cheng VS (2007) End-to-end privacy control in service outsourcing of human intensive processes: a multi-layered web service integration approach. Inf Syst Front 9(1):85–101
Chiu DK, Lin DT, Kafeza E, Wang M, Hu H, Hu H, Zhuang Y (2010) Alert based disaster notification and resource allocation. Inf Syst Front 12(1):29–47
Meng S, Chiu DK, Kafeza E, Wenyin L, Li Q (2010) Automated management of assets based on RFID triggered alarm messages. Inf Syst Front 12(5):563–578
Qiu LQ, Jia W, Yu J, Fan X, Gao W(2019) PHG: A Three-Phase Algorithm for Influence Maximization Based on Community Structure, IEEE Access, 7: 62511-62522
Acknowledgements
This paper is supported in part by the Natural Science Foundation of China (no. 71772107, 71,403,151, 61,502,281, 61,433,012, U1435215), Qingdao social science planning project (no. QDSKL1801138), the National key R&D Plan (no. 2018YFC0831002), the key R&D Plan of Shandong Province (no.2018GGX101045), humanity and social science Fund of the Ministry of education (no. 18YJAZH136), the Natural Science Foundation of Shandong Province (Nos. ZR2018BF013, ZR2019MF003, ZR2013FM023), the innovative Research Foundation of Qingdao (grant no. 18–2–2-41-jch), Shandong education quality improvement plan for postgraduate, the leading talent development program of Shandong University of Science and Technology, special funding for Taishan scholar construction project, and SDUST research fund
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
In order to get optimal TMFSF similarity, we use an interpolation method to get the optimal value of f over two datasets, which is assigned a value of 1.0, 1.1, 1.2, 1.3, 1.4, and 1.5, respectively. We employ MAE and RMSE as evaluation criteria in this experiment. The smaller the values of MAE and RMSE, the more accurate the prediction is.
For the Eachmovie dataset, we obtain the MAE and RMSE values as shown in Fig. 10a and b, when f ranges from 1.0 to 1.5. Then we can see that, when f is 1.0, the values of MAE and RMSE achieve their minimums respectively. That means, the optimal value of f is 1.0. Similarly, as shown Fig. 11a and b, we obtain the optimal MAE and RMSE values on the Netflix dataset when f is 1.1. Therefore, we can conclude that the optimal values of f on the two datasets are 1.0 and 1.1, respectively
Rights and permissions
About this article
Cite this article
Ji, S., Yang, W., Guo, S. et al. Asymmetric response aggregation heuristics for rating prediction and recommendation. Appl Intell 50, 1416–1436 (2020). https://doi.org/10.1007/s10489-019-01594-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10489-019-01594-2