Abstract
Low-rate Denial of Service (LDoS) attacks cause severe destructiveness to network security. Moreover, they are more difficult to detect because they are more hidden and lack distinguishing features. Consequently, packets belonging to legitimate users can be misplaced. The performance of a transport system can be degraded by frequently sending short bursts of packets. An attack program generates its own traffic. Additionally, a diverse array of attack strategies is available. Traditional detection methods cannot effectively extract attack features. This increases the difficulty of detecting LDoS attacks in streams of fluctuating normal traffic. In this study, we establish a method for detecting LDoS attacks. It is constructed using Laplacian eigenmap (LE) and a Wasserstein generative adversarial network (WGAN) with a denoising penalty and sample-augmented discriminator (DPSA-WGAN) based on deep learning. First, an unsupervised deep learning network (LENet) is generated using LE. Moreover, data are preprocessed by dimensionality reduction to extract low-dimensional LDoS attacks features. Subsequently, we build the DPSA-WGAN on top of the WGAN to detect LDoS attacks. Moreover, a denoising penalty term and a sample-augmented discriminator are added to improve the LDoS attacks feature generation. The denoising penalty is employed to improve the performance of the generator. Moreover, the sample-augmented discriminator learns a more accurate classification-decision hyperplane. We test our method on NS2 and test-bed platforms. Using our method, dimensionality reduction and sample generation are demonstrated to be more effective than with other techniques. When background noise traffic is added, the precision rate increases. Moreover, the proposed method shows high efficiency and has an outstanding noise-reduction ability. Furthermore, it is highly robust and can detect LDoS attacks in real time.






















Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Agrawal N, Tapaswi S (2017) Defense schemes for variants of distributed denial-of-service (DDoS) attacks in cloud computing: a survey. Inf Sec J: A Global Perspective 26(2):61–73
Agrawal N, Tapaswi S (2019) Defense mechanisms against DDoS attacks in a cloud computing environment: state-of-the-art and research challenges. IEEE Commun Surv Tutor 21(4):1–27
Matta V, Mauro MD, Longo M (2017) DDoS Attacks With Randomized Traffic Innovation: Botnet Identification Challenges and Strategies. IEEE Trans Inf Forensics Secur 12(99):1844–1859
Lukaseder T, Maile L, Erb B (2018) SDN-assisted network-based mitigation of slow DDoS attacks, Secure Communication, (2) 102–121
Chen H, Meng C, Fu Z (2020) Novel LDoS attack detection by spark-assisted correlation analysis approach in wireless sensor network. IET Inf Secur 6. https://doi.org/10.1049/iet-ifs.2018.5512
Chen Z, Yeo CK, Lee BS (2018) Power Spectrum Entropy based Detection and Mitigation of Low-Rate DoS Attacks. Comput Netw 136(8):80–94
Tang D, Zhang S, Chen J (2021) The detection of low-rate DoS attacks using the SADBSCAN algorithm. Inf Sci 565:229–247. https://doi.org/10.1016/j.ins.2021.02.038
Agrawal N, Tapaswi S (2018) Low Rate Cloud DDoS Attack Defense Method Based on Power Spectral Density Analysis. Inf Process Lett 138:44–50
Yue M, Liu L, Wu Z (2018) Identifying LDoS attack traffic based on wavelet energy spectrum and combined neural network. Int J Commun Syst 31(2):1–16
Sahoo KS, Puthal D, Tiwary M (2018) An early detection of low rate DDoS attack to SDN based data center networks using information distance metrics. Futur Gener Comput Syst 89:685–697
Liu X, Ren J, He H (2021) Low-rate DDoS attacks detection method using data compression and behavior divergence measurement. Comput Secur 100:102107
Agrawal N, Tapaswi S (2020) Detection of low-rate cloud DDoS attacks in frequency domain using fast Hartley transform. Wirel Pers Commun 112(2):1735–1762
Wang W, Ke X, Wang L (2018) A HMM-R approach to detect L-DDoS attack adaptively on SDN controller. Future Internet 10(9):83
Lin SW, Ying KC, Lee CY (2012) An intelligent algorithm with feature selection and decision rules applied to anomaly intrusion detection. Appl Soft Comput 12(10):3285–3290
Ratti R, Singh SR, Nandi S (2020) Towards implementing fast and scalable Network Intrusion Detection System using Entropy based Discretization Technique. 2020 11th International Conference on Computing, Communication and Networking Technologies (ICCCNT)
Jiang F, Sui Y, Zhou L (2015) A relative decision entropy-based feature selection approach. Pattern Recogn 48(7):2151–2163
Feng J, Sui Y (2015) A novel approach for discretization of continuous attributes in rough set theory. Knowl-Based Syst 73(6):324–334
Prabakeran S, Sethukarasi T (2020) Optimal solution for malicious node detection and prevention using hybrid chaotic particle dragonfly swarm algorithm in VANETs. Wirel Netw 26(3):5897–5917
a.Baskar M, Ramkumar J, Karthikeyan C, Anbarasu V, Balaji A, Arulananth T (2021) Low rate DDoS mitigation using real-time multi threshold traffic monitoring system. J Ambient Intell Humaniz Comput:1–9
Kushwah GS, Ranga V (2021) Optimized extreme learning machine for detecting DDoS attacks in cloud computing. Comput Secur 105:102260
Tang D, Tang L, Shi W, Zhan S, Yang Q (2020) Mf-cnn: a new approach for ldos attack detection based on multi-feature fusion and cnn. Mob Netw Appl 7:1–18
Gopi R, Sathiyamoorthi V, Selvakumar S (2021) Enhanced method of ANN based model for detection of DDoS attacks on multimedia internet of things. Multimed Tools Appl 81:1–19
Belkin M, Niyogi P (2014) Laplacian eigenmaps for dimensionality reduction and datarepresentation. Neural Comput 15(6):1373–1396
Wang T, Li W, Rong H (2022) Abnormal traffic detection-based on memory augmented generative adversarial IIoT-assisted network. Wirel Netw 28:2579–2595
Kim JY, Bu SJ, Cho SB (2018) Zero-day malware detection using transferred generative adversarial networks based on deep autoencoders[J]. Inf Sci 460-461:83–102
Arjovsky M, Chintala S, Bottou L (2017) Wasserstein gan, ar Xiv preprint ar Xiv:1701. 07875, 1–32
Zhang X, Wu Z, Chen J, Yue M (2017) An adaptive kpca approach for detecting ldos attack. Int J Commun Syst 30(4):e2993
Wu Z, Pan Q, Yue M, Liu L (2019) Sequence alignment detection of tcp-targeted synchronous low-rate dos attacks. Comput Netw 152:64–77
Tang D, Tang L, Dai R, Chen J, Li X, Rodrigues JJ (2020) Mf-adaboost: Ldos attack detection based on multi-features and improved adaboost. Futur Gener Comput Syst 106:347–359
Tang D, Man J, Tang L, Feng Y, Yang Q (2020) Wedms: an advanced mean shift clustering algorithm for ldos attacks detection. Ad Hoc Netw 102:102145
Liu L, Wang H, Wu Z (2020) The detection method of low-rate DoS attack based on multi-feature fusion. Digital Commun Netw 6:504–513
Liu L, Wang H, Wu Z, Yue M (2020) The detection method of low-rate dos attack based on multi-feature fusion. Digital Commun Netw 6:504–513
Duy PT, Le KT, Khoa NH (2021) DIGFuPAS: Deceive IDS with GAN and Function-Preserving on Adversarial Samples in SDN-enabled networks. Computers & Security 109(1):102367
Cheng J, Luo Y, Tang X, Ou M (Apr. 2019) DoS attack detection method based on LSTM traffic prediction. J Huazhong Univ Sci Technol 47(4):32–36
Tran D, Mac H, Tong V (2017) A LSTM based Framework for Handling Multiclass Imbalance in DGA Botnet Detection. Neurocomputing 275:2401–2413
Zhong Y, Chen W, Wang Z (2019) HELAD: a novel network anomaly detection model based on heterogeneous ensemble learning. Comput Netw 169:107049
Li Q, Wang F, Wang J (2019) LSTM-based SQL injection detection method for intelligent transportation system. IEEE Trans Veh Technol 68(5):4182–4191
Huang W, Peng X, Shi Z, Ma Y (Nov. 2020) Dversarial attack against LSTM-based DDoS intrusion detection system. In: Proc. IEEE 32nd Int.Conf. Tools with Artif. Intell. (ICTAI), Baltimore, MD, USA, pp: 686–693
Binbusayyis A, Vaiyapuri T (2021) Unsupervised deep learning approach for network intrusion detection combining convolutional autoencoder and one-class SVM. Appl Intell 8:7094–7108
Eynard D, Kovnatsky A, Bronstein MM (2015) Multimodal manifold analysis by simultaneous diagonalization of laplacians. IEEE Trans Pattern Anal Mach Intell 37(12):2505–2517
Odena A, Buckman J, Olsson C (2018) Is generator conditioning causally related to Gan performance. International conference on machine learning (ICML), Stockholm, Sweden, pp: 3846–3855
Chen T, Lucic M, Houlsby N (2018) On self modulation for generative adversarial networks, ar Xiv preprint ar Xiv:1810.01365 1–18
Hou M, Chaib-Draa B, Li C (2018) Generative adversarial positive-unlabeled learning. Proceedings of the 27th international joint conference on artificial intelligence (IJCAI), Stockholm, Sweden, 2255–2261
Li H, Zhu J, Wang Q, Zhou T, Qiu H, Li H (2016) LAAEM: a method to enhance LDoS attack. IEEE Commun Lett 20(4):708–711
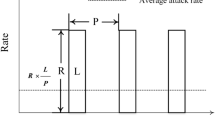
Kuzmanovic A, Knightly EW (2003) Low-rate TCP-targeted denial of service attacks. Proc ACM SIGCOMM 14(4):75–86
Mao X, Li Q, Xie H (2017) Least squares generative adversarial networks. Proceedings of the IEEE international conference on computer vision (CVPR), Hawaii, America, pp: 2794–2802
Xu Z, Fang X, Yang G (2021) Malbert: a novel pre-training method for malware detection. Comput Secur 111:102458. https://doi.org/10.1016/j.cose.2021.102458
Acknowledgments
This research is funded by the National Natural Science Foundation of China, grant number 61703349. Moreover, it is funded by the Science and Technology Research and Development Project, grant number N2018G062, K2018G011. In the end, it is funded by the Science and technology research and development plan of China National Railway Group, grant number L2021X001.
Declaration
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Ma, W., Liu, R. & Guo, J. LDoS attack traffic detection based on feature optimization extraction and DPSA-WGAN. Appl Intell 53, 13924–13955 (2023). https://doi.org/10.1007/s10489-022-04171-2
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10489-022-04171-2