Abstract
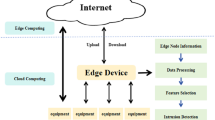
The Internet of Things (IoT) refers to a vast and interconnected network comprising smart objects with comprehensive capabilities. Unfortunately, the vulnerabilities of IoT device awareness layer nodes are vulnerable to network intrusion. Therefore, it is crucial to detect new types of intrusions in the IoT environment. Also, the current IoT intrusion detection models are trained by samples with a balanced distribution. However, the distribution of intercepted network samples is unbalanced in some specific scenarios. In addition, malicious traffic easily interferes with the IoT environment. As a result, detection efficiency and accuracy decrease. In this study, we propose a multi-constraint transfer approach with additional auxiliary domains for IoT intrusion detection under unbalanced samples distribution. First, we construct a high precision and efficiency feature extractor using PointNet ++ as a framework to complete attack feature extraction. We then design a multi-constraint transfer approach with additional auxiliary domains. In addition, we also design a multi-scale and multi-level sample augmented discriminator to complete the final IoT intrusion detection under unbalanced samples distribution. Finally, we validate our approach by using four intrusion datasets from IoT networks, and it demonstrates excellent performance. In the comparison results of all approaches, the detection accuracy of our approach is the highest under four unbalanced sample combinations. Also, the average accuracy is 96.398% on the four datasets. One of the biggest advantages of this approach is its very good convergence, efficiency and detection stability in the presence of noise. In particular, it can be used effectively for intrusion detection in real IoT environments.




















Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Data availability
The data supporting the study’s findings are available from the corresponding author, 1248564936@qq.com, upon reasonable request.
References
Xie X, Li X, Xu L (2023) HaarAE: an unsupervised anomaly detection model for IOT devices based on Haar wavelet transform. Appl Intell. https://doi.org/10.1007/s10489-023-04449-z
Sadiq M, Shi D, Liang J (2022) A robust occlusion-adaptive attention-based deep network for facial landmark detection. Appl Intell 52:9320–9333. https://doi.org/10.1007/s10489-021-02848-8
Polat H, Türkolu M, Polat O (2022) A novel approach for accurate detection of the DDoS attacks in SDN-based SCADA systems based on deep recurrent neural networks. Expert Syst Appl 197:116748. https://doi.org/10.1016/j.eswa.2022.116748
Kumar R, Kumar P, Tripathi R (2022) A distributed intrusion detection system to detect DDoS attacks in blockchain-enabled IoT network. J Parallel Distrib Comput 164:55–68. https://doi.org/10.1016/j.jpdc.2022.01.030
Yungaicela-Naula NM, Vargas-Rosales C, Pérez-Díaz JA, Carrera DF (2022) A flexible SDN-based framework for slow-rate DDoS attack mitigation by using deep reinforcement learning. J Netw Comput Appl 205:103444. https://doi.org/10.1016/j.jnca.2022.103444
Bokhari S, Hamrioui S, Aider M (2022) Cybersecurity strategy under uncertainties for an IoE environment. J Netw Comput Appl 205:103426. https://doi.org/10.1016/j.jnca.2022.103426
Chen C, Fragonara LZ, Tsourdos A (2021) GAPointNet: graph attention based point neural network for exploiting local feature of point cloud. Neurocomputing 438(28):122–132. https://doi.org/10.1016/j.neucom.2021.01.095
Feng M, Zhang L, Lin X, Gilani SZ, Mian A (2020) Point attention network for semantic segmentation of 3D point clouds. Pattern Recogn 107:107446. https://doi.org/10.1016/j.patcog.2020.107446
Al-Haija Q A, Zein-Sabatto S (2020) An efficient deep-learning-based detection and classification system for cyber-attacks in IoT communication networks, multidisciplinary digital publishing institute. 12. https://doi.org/10.3390/electronics9122152
Chen C, Qian S, Fang Q (2020) HAPGN: hierarchical attentive pooling graph network for point cloud segmentation. IEEE Trans Multimed 99:1–1. https://doi.org/10.1109/TMM.2020.3009499
Mushtaq E, Zameer A, Umer M (2022) A two-stage intrusion detection system with auto-encoder and LSTMs. Appl Soft Comput 121. https://doi.org/10.1016/j.asoc.2022.108768
Ap A, Vd B (2022) An intrusion detection approach using ensemble support vector machine based chaos game optimization algorithm in big data platform. Appl Soft Comput. https://doi.org/10.1016/j.asoc.2021.108295
Du H, Zhang Y, Gang K (2021) Online ensemble learning algorithm for imbalanced data stream. Appl Soft Comput 107(1):107378. https://doi.org/10.1016/j.asoc.2021.107378
Niu S, Liu Y, Wang J (2020) A decade survey of transfer learning (2010–2020). IEEE Trans Artif Intell 1(2):151–166. https://doi.org/10.1109/TAI.2021.3054609
Lee JH, Park KH (2019) GAN-based imbalanced data intrusion detection system. Pers Ubiquit Comput 2(1):1–8. https://doi.org/10.1007/s00779-019-01332-y
Lee JH, Park KH (2019) AE-CGAN model based high performance network intrusion detection system. Appl Sci 9(20):4221–4235. https://doi.org/10.3390/app9204221
Arruda VF, Berriel RF, Paixo TM (2022) Cross-domain object detection using unsupervised image translation. Expert Syst Appl 192:116334. https://doi.org/10.1016/j.eswa.2021.116334
Sithungu SP, Ehlers EM (2022) GAAINet: a generative adversarial artificial immune network model for intrusion detection in industrial IoT systems. J Adv Inf Technol 5(13):456–461
Hassan AU, Ahmed H, Choi J (2021) Unpaired font family synthesis using conditional generative adversarial networks. Knowl-Based Syst 229(8):107304. https://doi.org/10.1016/j.knosys.2021.107304
Mirza M, Osindero S (2014) Conditional generative adversarial nets, ar Xiv preprint ar Xiv:1411.1784: 1-7. https://doi.org/10.48550/arXiv.1411.1784
Nagarajan V, Kolter JZ (2017) Gradient descent gan optimization is locally stable. Advances in Neural Information Processing Systems (Neur IPS), California, pp 5585–5595. https://doi.org/10.48550/arXiv.1706.04156
Yang Y, Fu H, Gao S (2022) Intrusion detection: a model based on the improved vision transformer. Trans Emerg Telecommun Technol 33(9). https://doi.org/10.1002/ett.4522
Phan D, Khoa NH, Hiep H (2021) A deep transfer learning approach for flow-based intrusion detection in SDN-enabled network. The 20th international conference on intelligent software methodologies, tools, and techniques (SOMET 2021)
Aldhyani THH (2022) Performance investigation of principal component analysis for intrusion detection system using different support vector machine kernels. Electronics 11. https://doi.org/10.3390/electronics11213571
Gao JL, Chai SC, Zhang BH (2019) Research on network intrusion detection based on incremental extreme learning machine and adaptive principal component analysis. Energies 12(7):1223. https://doi.org/10.3390/en12071223
Dubey GP, Bhujade RK (2021) Optimal feature selection for machine learning based intrusion detection system by exploiting attribute dependence. Mater Today 47(17):6325–6331. https://doi.org/10.1016/j.matpr.2021.04.643
Gaber T, El-Ghamry A, Hassanien AE (2022) Injection attack detection using machine learning for smart IoT applications. Phys Commun 52:101685.1-101685.14. https://doi.org/10.1016/j.phycom.2022.101685
Rajpoot V, Agrawal R (2022) ITSA-KNN: Feature selection model based on improved tree-seed algorithm and K-nearest neighbor for network intrusion detection. Adv Data Inf Sci 1–13. https://doi.org/10.1007/978-981-16-5689-7_1
Zhang XY, Li J, Zhang DJ (2020) Research on feature selection for cyber intrusion detection in industrial Internet of things. Proceedings of the 2020 international conference on cyberspace innovation of advanced technologies. ACM Press, New York, pp 256–262. https://doi.org/10.1145/3444370.3444581
Cheng XX, Li W, Xiao Z (2020) Intrusion detection system based on QBSO-FS. Proceedings of 2020 international conference on artificial intelligence and computer engineering (ICAICE). IEEE Press, Piscataway, pp 372–377
Fu LD, Zhang WB, Tan XB (2021) An algorithm for detection of traffic attribute exceptions based on cluster algorithm in industrial Internet of things. IEEE Access 9(53370):53378. https://doi.org/10.1109/ACCESS.2021.3068756
Azmoodeh A, Dehghantanha A, Choo KKR (2019) Robust malware detection for internet of (Battlefield) things devices using deep eigenspace learning. IEEE Trans Sustain Comput 4(1):88–95. https://doi.org/10.1109/TSUSC.2018.2809665
Haseeb J, Mansoori M, Hirose Y (2022) Autoencoder-based feature construction for IoT attacks clustering. Future Gener Comput Syst 127:487–502. https://doi.org/10.1016/j.future.2021.09.025
Wang N, Wang P, Alipour-Fanid A (2019) Physical-layer security of 5G wireless networks for IoT: challenges and opportunities. IEEE Internet Things J 6(5):8169–8181. https://doi.org/10.1109/JIOT.2019.2927379
Alferaidi A, Yadav K, Alharbi Y (2022) Distributed deep CNN-LSTM model for intrusion detection method in IoT-based vehicles. Math Probl Eng. https://doi.org/10.1155/2022/3424819
Radhakrishnan G, Srinivasan K, Kaneswaran S (2021) A deep-RNN and meta-heuristic feature selection approach for IoT malware detection. Mater Today (7). https://doi.org/10.1016/j.matpr.2021.01.207
Freitas DAP, Kaddoum G, Campelo DR (2021) Intrusion detection for cyber-physical systems using generative adversarial networks in fog environment. IEEE Internet Things J 8(8):6247–6256. https://doi.org/10.1109/JIOT.2020.3024800
Koroniotis N, Moustafa N, Sitnikova E (2020) A new network forensic framework based on deep learning for Internet of things networks: a particle deep framework. Futur Gener Comput Syst 110(91):106. https://doi.org/10.1016/j.future.2020.03.042
Bhuvaneswari A, Selvakumar S (2020) Anomaly detection framework for Internet of things traffic using vector convolutional deep learning approach in fog environment. Futur Gener Comput Syst 113:255–265. https://doi.org/10.1016/j.future.2020.07.020
Saharkhizan M, Azmoodeh A, Dehghantanha A, Choo K-KR, Parizi RM (2020) An ensemble of deep recurrent neural networks for detecting IoT cyber intrusions using network traffic. IEEE Intern Things J 7(9):8852–8859. https://doi.org/10.1109/JIOT.2020.2996425
Liaqat S, Akhunzada A, Shaikh FS (2020) SDN orchestration to combat evolving cyber threats in Internet of medical things (IoMT). Comput Commun 160:697–705. https://doi.org/10.1016/j.comcom.2020.07.006
Debicha I, Bauwens R, Debatty T, Dricot J-M, Kenaza T, Mees W (2023) TAD: Transfer learning-based multi-adversarial detection of evasion attacks against network intrusion detection systems. Futur Gener Comput Syst 138:185–197. https://doi.org/10.1016/j.future.2022.08.011
Saba T, Rehman A, Sadad T (2022) Anomaly-based intrusion detection system for IoT networks through deep learning model. Comput Electr Eng 99:107810. https://doi.org/10.1016/j.compeleceng.2022.107810
Abdel-Basset M, Chang V, Hawash H (2021) Deep-IFS: intrusion detection approach for industrial Internet of things traffic in fog environment. IEEE Trans Industr Inf 17(11):7704–57715. https://doi.org/10.1109/TII.2020.3025755
Chen Y, Lin Q, Ji J (2022) Intrusion detection using multi-objective evolutionary convolutional neural network for Internet of Things in Fog computing. Knowl-Based Syst 23:244. https://doi.org/10.1016/j.knosys.2022.108505
Zhou XK, Liang W, Shimizu S (2020) Siamese neural network based few-shot learning for anomaly detection in industrial cyber- physical systems. IEEE Trans Industr Inf 17(8):5790–5798. https://doi.org/10.1109/TII.2020.3047675
Zhang H, Li Y, Lv Z (2020) A real-time and ubiquitous network intrusion detection based on deep belief network and support vector machine. IEEE/CAA J Autom Sin 7(3):790–799. https://doi.org/10.1109/JAS.2020.1003099
Kan X, Fan Y, Fang Z, Cao L, Li X (2021) A novel IoT network intrusion detection approach based on adaptive particle swarm optimization convolutional neural network. Inf Sci. https://doi.org/10.1016/j.ins.2021.03.060
Tsogbaatar E (2021) DeL-IoT: a deep ensemble learning approach to uncover anomalies in IoT. Internet of Things 14(2):100391. https://doi.org/10.1016/j.iot.2021.100391
Yao Y, Ma J, Ye Y (2022) KfreqGAN: Unsupervised detection of sequence anomaly with adversarial learning and frequency domain information. Knowl-Based Syst 236:1077571–10775713. https://doi.org/10.1016/j.knosys.2021.107757
Douzas G, Bacao F (2018) Effective data generation for imbalanced learning using conditional generative adversarial networks. Expert Syst Appl 91:464–471. https://doi.org/10.1016/j.eswa.2017.09.030
Ngo CP, Winarto AA, Li CKK (2019) Fence GAN: towards better anomaly detection, ar Xiv preprint ar Xiv:1904.01209: 1-13. https://doi.org/10.1109/ICTAI.2019.00028
Zhang H, Yu X, Ren P (2019) Deep adversarial learning in intrusion detection: a data augmentation enhanced framework, ar Xiv Preprint ar Xiv:1901.07949: 1-10. https://doi.org/10.13140/RG.2.2.19731.73762
Szczepański M, Pawlicki M, Kozik R (2023) The application of deep learning imputation and other advanced methods for handling missing values in network intrusion detection. Vietnam J Comput Sci 10(01):1–23. https://doi.org/10.1142/S2196888822500257
Tang Y, Gu L, Wang L (2021) Deep stacking network for intrusion detection. Sensors 22. https://doi.org/10.3390/s22010025
Yang J, Liang G, Li B (2021) A deep-learning- and reinforcement-learning-based system for encrypted network malicious traffic detection. Electron Lett 57(9). https://doi.org/10.1049/ell2.12125
Wang Y, Sun G (2021) Oversampling method for intrusion detection based on clustering and instance hardness. J Comput Appl 41(6):1709–1714. https://doi.org/10.11772/j.issn.1001-9081.2020091378
Folino F, Folino G, Guarascio M, Pisani FS, Pontieri L (2021) On learning effective ensembles of deep neural networks for intrusion detection. Inf Fusion 72(1):48–69. https://doi.org/10.1016/j.inffus.2021.02.007
Singh NB, Singh MM, Sarkar A (2021) A novel wide & deep transfer learning stacked GRU framework for network intrusion detection. J Inf Secur Appl 61. https://doi.org/10.1016/j.jisa.2021.102899
Idrissi I, Azizi M, Moussaoui O (2021) Accelerating the update of a DL-based IDS for IoT using deep transfer learning. Indones J Electric Eng Comput Sci (2). https://doi.org/10.11591/IJEECS.V23.I2.PP1059-1067
Zhu J-Y, Park T, Isola P (2017) Unpaired image-to-image translation using cycle-consistent adversarial networks. Proceedings of the IEEE international conference on computer vision (CVPR), Hawaii, pp 2223–2232. https://doi.org/10.1109/ICCV.2017.244
http://archive.ics.uci.edu/ml/datasets/detection of IoT botnet intrusions N BaIoT. Accessed 9/10/2022
Koroniotis N, Moustafa N, Sitnikova E (2019) Towards the development of realistic botnet dataset in the Internet of things for network forensic analytics: Bot-IoT dataset. Futur Gener Comput Syst 100:779–796. https://doi.org/10.1016/j.future.2019.05.041
Alsaedi A (2020) TON_IoT telemetry dataset: a new generation dataset of IoT and IIoT for data-driven intrusion detection systems. IEEE Access. https://doi.org/10.1109/ACCESS.2020.3022862
Verhnjak O, Hriberšek M, Steinmann P, Ravnik J (2020) A novel two-way coupling model for Euler-Lagrange simulations of multiphase flow. Eng Anal Boundary Elem 119(1):119–132. https://doi.org/10.1016/j.enganabound.2020.07.012
Ansari MS, Cockburn BF, Han J (2020) An improved logarithmic multiplier for energy-efficient neural computing. IEEE Trans Comput 70(4):614–625. https://doi.org/10.1109/TC.2020.2992113
Acknowledgements
This work is funded by the Science and Technology Research and Development Project of China National Railway Group (Grant No. L2021X001, N2018G062, K2018G011). In the end, it is funded by the Natural Science Foundation of Sichuan (Grant No. 2022NSFSC0466).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Liu, R., Ma, W. & Guo, J. A multi-constraint transfer approach with additional auxiliary domains for IoT intrusion detection under unbalanced samples distribution. Appl Intell 54, 1179–1217 (2024). https://doi.org/10.1007/s10489-023-05176-1
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10489-023-05176-1