Abstract
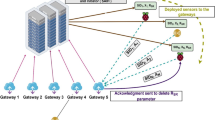
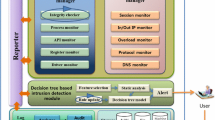
Many government branches report that internal networks are managed safely by separating them from the outside, but there is often a vulnerability that allows malicious codes to attack an internal network. Recently, the Ministry of National Defense of Korea announced that the internal network operated by the Korean military was attacked though hacking. It is difficult to detect cyber-attacks in real time within an internal network, which can be connected to an Internet of Everything (IoE). In this paper, we propose a fast attack detection system for the internal network that can be used by the government or public organizations. This system generates a tree to which the attack level is applied, notifies the user when the level is reached, and can block the system before an attack. Using this system, it is possible to protect the data and physical aspects by preventing the destruction of a system with large amounts of data, including important confidential or intellectual property. The proposed method offers a proper methodology for designing a malware protection system by categorizing the problem into a tree structure.









Similar content being viewed by others
References
Lee, Y.H., Yoo, S.J.: The construction of logical, physical network separation by virtualization. Korea Converg. Secur. Assoc. 14(2), 25–33 (2014)
Lee, M.G.: A study for national cyber security and defense. Korea Contents Soc. 11(4), 18–22 (2013)
Chen, Y., Nyemba, S., Zhang, W., Malin, B.: Specializing network analysis to detect anomalous insider actions. Secur. Inform. 1, 5 (2012)
Zuech, R., Khoshgoftaar, T.M., Walt, R.: Intrusion detection and big heterogeneous data: a survey. J. Big Data 2, 3 (2015)
Yan, J., Govindarasu, M., Chen-Ching, L.I., Ming, N.I., Vaidya, U.: Risk assessment framework for power control systems with PMU-based intrusion response system. J. Mod. Power Syst. Clean Energy 3(3), 321–331 (2015)
Kar, J., Mishra, M.R.: Mitigating threats and security metrics in cloud computing. J. Inf. Process. Syst. 12(2), 226–233 (2016)
StiaWan, D., Idris, M., Abdullah, A.H.: Penetration testing and network auditing: Linux. J. Inf. Process. Syst. 11(1), 104–115 (2015)
Dick, S.: Designing the new Intranet, Ph.D. dissertation, Göteborg University. http://hdl.handle.net/2077/911 (2002)
Alharbi, T., Durando, D., Pakzad, F., Portmann, M.: Securing ARP in software defined networks. In: IEEE 41st Conference on Local Computer Networks (LCN), pp. 523–526 (2016)
Elham, S., Arastouie, N.: Backdoor detection system using artificial neural network and genetic algorithm. In: 2011 International Conference on Computational and Information Sciences (ICCIS), pp. 817–820 (2011)
Schneier, B.: Attack trees. Dr. Dobb’s J. 24(12), 21–29 (1999)
Mark, M., Cassandra, M.T., Cynthia, K.V., John, M., Mark, H., Scott, M., Jason, F.: Cyber threat metrics. Sandia National Laboratories (2012)
Joo, J.W., Moon, S.Y., Singh, S.: S-Detector: an enhanced security model for detecting Smishing attack for mobile computing. Telecommun. Syst. 66(1), 29–38 (2017)
Choi, J., Choi, C., Ko, B., Kim, P.: A method of DDoS attack detection using HTTP packet pattern and rule engine in cloud computing environment. Soft. Comput. 18(9), 1697–1703 (2014)
Betts, M., Stirland, J., Olajide, F., Jones, K., Janicke, H.: Developing a state of the art methodology & toolkit for ICS SCADA forensics. Int. J. Ind. Control Syst. Secur. (IJICSS) 1(2), 44–56 (2016)
Acknowledgements
This work was supported by Defense Acquisition Program Administration and Agency for Defense Development under the contract (UD160066BD).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Kim, D., Kim, YH., Shin, D. et al. Fast attack detection system using log analysis and attack tree generation. Cluster Comput 22 (Suppl 1), 1827–1835 (2019). https://doi.org/10.1007/s10586-018-2269-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-018-2269-x