Abstract
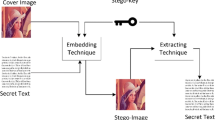
Internet of Things (IoT) networks are considered the great challenging by emerging technologies that try to solve the problems in modern life, while securing the information still vital in different systems in research. A simple, but yet efficient, steganography based on the pixels characteristics of the cover image in the spatial domain is proposed in this paper. The cover image pixels are classified into highly smooth (HS) and Less Smooth (LS) domains to select the extra eligible pixels that occur in the HS region. The proposed classification scheme, named IoTSteg, achieves an embedment process different from other traditional steganography that use the total number of pixels. The performance of the developed new steganography is evaluated using the measures such as the Peak Signal to Noise Ratio (PSNR), Capacity-Distortion Trade-Off (CDTO) and Structural Similarity Index (SSIM). The results are compared with the schemes including the Statistical Features Maintained (SFM_A and SFM_B) and Difference Histogram Shifting (DHS). The secret test using 8000 bits and 4 cover images each size \(512\times 512\) produced a PSNR value of 66.61, CDTO, and SSIM of 0.9998. The competence of the proposed scheme is determined under two embedding rates of 0.1 and 0.2 bit per pixel maintaining the high level of imperceptibility of the cover images. Detail analyses showed that the proposed steganography achieved excellent competence for the embedment procedure with two rates (HS and LS) to maintain the high level of the cover images imperceptibility.







Similar content being viewed by others
References
Kadhim, I.J., Premaratne, P., Vial, P.J., Halloran, B.: Comprehensive survey of image steganography: techniques, evaluations, and trends in future research. Neurocomputing 335, 299–326 (2019)
Shi, Y.-Q., Li, X., Zhang, X., Wu, H.-T., Ma, B.: Reversible data hiding: advances in the past two decades. IEEE Access 4, 3210–3237 (2016)
Tao, J., Li, S., Zhang, X., Wang, Z.: Towards robust image steganography. IEEE Trans. Circuits Syst. Video Technol. 29(2), 594–600 (2018)
Wang, Z., Qian, Z., Zhang, X., Yang, M., Ye, D.: On improving distortion functions for jpeg steganography. IEEE Access 6, 74917–74930 (2018)
Hao, W., Xiang, L., Li, Y., Yang, P., Shen, X.: Reversible natural language watermarking using synonym substitution and arithmetic coding. Comput. Mater. Continua 55, 541 (2018)
Li, F., Wu, K., Zhang, X., Yu, J., Lei, J., Wen, M.: Robust batch steganography in social networks with non-uniform payload and data decomposition. IEEE Access 6, 29912–29925 (2018)
Holub, V., Fridrich, J.: Digital image steganography using universal distortion. In: Proceedings of the First ACM Workshop on Information Hiding and Multimedia Security, 2013, pp. 59–68
Sedighi, V., Cogranne, R., Fridrich, J.: Content-adaptive steganography by minimizing statistical detectability. IEEE Trans. Inf. Foren. Security 11(2), 221–234 (2015)
Cui, Q., Zhou, Z., Fu, Z., Meng, R., Sun, X., Wu, Q.J.: Image steganography based on foreground object generation by generative adversarial networks in mobile edge computing with internet of things. IEEE Access 7, 90815–90824 (2019)
Zhou, Z., Mu, Y., Wu, Q.J.: Coverless image steganography using partial-duplicate image retrieval. Soft Comput. 23(13), 4927–4938 (2019)
Cao, Y., Zhou, Z., Sun, X., Gao, C.: Coverless information hiding based on the molecular structure images of material. Comput. Mater. Continua 54(2), 197–207 (2018)
Yin, J. H. J., Fen, G. M. , Mughal, F., Iranmanesh, V.: Internet of things: Securing data using image steganography. In: 2015 3rd International Conference on Artificial Intelligence, Modelling and Simulation (AIMS), 2015, pp. 310–314
Lin, J.C.W., Srivastava, G., Zhang, Y., Djenouri, Y., Aloqaily, M.: Privacy preserving multi-objective sanitization model in 6g iot environments. IEEE Internet Things J. 1, 1 (2020)
Hamza, R., Yan, Z., Muhammad, K., Bellavista, P., Titouna, F.: A privacy-preserving cryptosystem for iot e-healthcare. Inf. Sci. 527, 493–510 (2019)
Feng, C., Yu, K., Aloqaily, M., Alazab, M., Lv, Z., Mumtaz, S.: Attribute-based encryption with parallel outsourced decryption for edge intelligent iov. IEEE Trans. Vehicular Technol. 69(11), 13784–13795 (2020)
Elhoseny, M., Ramarez-Gonzailez, G., Abu-Elnasr, O.M., Shawkat, S.A., Arunkumar, N., Farouk, A.: Secure medical data transmission model for iot-based healthcare systems. IEEE Access 6, 20596–20608 (2018)
Abuadbba, S., Ibaida, A., Khalil, I.: Iotsign: Protecting privacy and authenticity of iot using discrete cosine based steganography, resreport, arXiv:1911.00604 (2019)
Li, L., Hossain, M.S., El-Latif, A.A.A., Alhamid, M.F.: Distortion less secret image sharing scheme for internet of things system. Clust. Comput. 22, 2293–2307 (2019)
El-Latif, A.A.A., Abd-El-Atty, B., Hossain, M.S., Elmougy, S., Ghoneim, A.: Secure quantum steganography protocol for fog cloud internet of things. IEEE Access 6, 10332–10340 (2018)
Lewis Tseng, A.X.Y., Otoum, S., Aloqaily, M., Jararweh, Y.: Blockchain-based database in an iot environment: challenges, opportunities, and analysis. Clust. Comput. 23, 1 (2020)
Bhattacharyya, S., Hassanien, A., Gupta, D., Khanna, A., Pan, I.: Image steganography using lsb substitution facilitated by shared password. In: International Conference on Innovative Computing and Communications. Lecture Notes in Networks and Systems, vol 55, (2019)
Mansoor, F., Mohsen, R., Yasser, I.: A new method of coding for steganography based on lsb matching revisited, Security and Communication Networks (2021)
Zhenkun, B., Yanqing, G., Xiaolong, L., Yi, Z., Meng, X., Xiangyang, L.: A robust image steganography based on the concatenated error correction encoder and discrete cosine transform coefficients. J. Ambient Intell. Hum. Comput. 11, 1889–1901 (2020)
Pratik, S., B. R.: A secure spatial domain image steganography using genetic algorithm and linear congruential generator. In: International Conference on Intelligent Computing and Applications. Advances in Intelligent Systems and Computing, vol 632. Springer, Singapore, 2018, pp. 119–129
Hassaballah, M., Hameed, M.A., Awad, A.I., Muhammad, K.: A novel image steganography method for industrial internet of things security. IEEE Trans. Ind. Inf. (2021). https://doi.org/10.1109/TII.2021.3053595
Xie, G., Ren, J., Marshall, S., Zhao, H., Li, H.: A new cost function for spatial image steganography based on 2d-ssa and wmf. IEEE Access 9, 30604–30614 (2021)
Das, A., Singh Wahi, J., Anand, M., Rana, Y.: Multi-image steganography using deep neural networks, Technical report eprint arXiv:2101.00350 (2021)
Pattanaik, B., Chitra, P., Lakshmi, H., Thamarai Selvi, G., Nagaraj, V.: Contrasting the performance metrics of discrete transformations on digital image steganography using artificial intelligence. In: Materials Today: Proceedings. https://www.sciencedirect.com/science/article/pii/S2214785320397613
Holub, V., Fridrich, J.:Designing steganographic distortion using directional filters. In: 2012 IEEE International Workshop on Information Forensics and Security (WIFS), IEEE, 2012, pp. 234–239
Pevnỳ, T., Filler, T., Bas, P.: Using high-dimensional image models to perform highly undetectable steganography. In: International Workshop on Information Hiding, Springer, Berlin, 2010, pp. 161–177
Zitnick, C.L., Kang, S.B.: Stereo for image-based rendering using image over-segmentation. Int. J. Comput. Vis. 75(1), 49–65 (2007)
Clausi, D.A.: Comparison and fusion of co-occurrence, gabor and mrf texture features for classification of sar sea-ice imagery. Atmosphere-Ocean 39(3), 183–194 (2001)
Feng, J., Jiao, L., Zhang, X., Yang, D.: Bag-of-visual-words based on clonal selection algorithm for sar image classification. IEEE Geosci. Remote Sens. Lett. 8(4), 691–695 (2011)
Feng, H., Hou, B., Gong, M.: Sar image despeckling based on local homogeneous-region segmentation by using pixel-relativity measurement. IEEE Trans. Geosci. Remote Sens. 49(7), 2724–2737 (2011)
Touzi, R., Lopes, A., Bousquet, P.: A statistical and geometrical edge detector for sar images. IEEE Trans. Geosci. Remote Sens. 26(6), 764–773 (1988)
Li, T., Li, H., Hu, L., Li, H.: A reversible steganography method with statistical features maintained based on the difference value. IEEE Access 8, 12845–12855 (2020)
Acknowledgements
This study was financially supported via a funding grant by Deanship of Scientific Research, University of Jeddah Researchers Supporting Project number [UJ-DSR-DR-21-111], University of Jeddah, Jeddah, Saudi Arabia
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Alarood, A., Ababneh, N., Al-Khasawneh, M. et al. IoTSteg: ensuring privacy and authenticity in internet of things networks using weighted pixels classification based image steganography. Cluster Comput 25, 1607–1618 (2022). https://doi.org/10.1007/s10586-021-03383-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-021-03383-4