Abstract
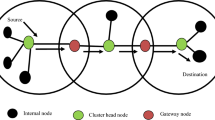
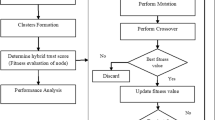
The Internet of Things (IoT) defines the network of physical objects, commonly used to interconnect and communicate with other devices through the internet. Security is highly essential in IoT based communication owing to the massive heterogeneity of devices involved in the network. The interlinked systems in IoT, requires the trusted model for assuring security, authenticity, authorization and confidentiality of interconnected things, irrespective of the functionalities. Considering the challenges in the provision of security in the IoT network, this paper proposes a new chaotic bumble bees mating optimization (CBBMO) algorithm for secure data transmission with trust sensing model, called CBBMOR-TSM model. The BBMO is stimulated by the mating nature of a swarm of bumble bees. To improve the convergence rate of the BBMO technique, the CBBMO model is defined by the integration of chaotic concept into the classical BBMO technique. The aim of the proposed model is to design a trust sensing model and perform secure routing using the CBMO algorithm. The proposed model initially designs a trust sensing model by incorporating indirect and direct trusts that are utilized to determine the trust values of the IoT nodes and thereby the malicious node can be identified. In addition, the secure routing process is invoked using the CMBO algorithm by using the trust sensing model to determine an optimal and secure path for data transmission. To examine the superior performance of the presented method, an extensive set of experiments are performed and the results are investigated in terms of different measures. The CBBMOR-TSM model has attained a higher average PDR of 0.931 and lower average PLR of 0.069 whereas the TRM_IOT, OSEAP_IOT and MCTAR-IOT methods have achieved a maximum PLR of 0.219, 0.161 and 0.110 respectively.








Similar content being viewed by others
References
Shin, D., Sharma, V., Kim, J., Kwon, S., You, I.: Secure and efficient protocol for route optimization in PMIPv6-based smart home IoT networks. IEEE Access 5, 11100–11117 (2017)
Abualigah, L., Diabat, A., Elaziz, M.A.: Intelligent workflow scheduling for Big Data applications in IoT cloud computing environments. Clust. Comput. 24, 2957–2976 (2021). https://doi.org/10.1007/s10586-021-03291-7
Vivekanand, V., Thushara, V.T.: Ultra resource constrained adaptive multipath routing for meteorological sensor networks. In: 2016 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), pp. 1–6. IEEE (2016)
Paulraj, D.: An automated exploring and learning model for data prediction using balanced CA-SVM. J. Ambient Intell. Hum. Comput. (2020). https://doi.org/10.1007/s12652-020-01937-9
Mohammadi, V., Rahmani, A.M., Darwesh, A.M., Sahafi, A.: Trust-based recommendation systems in Internet of Things: a systematic literature review. HCIS 9(1), 1–61 (2019)
Kobayashi, G., Quilici-Gonzalez, M.E., Broens, M.C., Quilici-Gonzalez, J.A.: The ethical impact of the Internet of Things in social relationships: technological mediation and mutual trust. IEEE Consum. Electron. Mag. 5(3), 85–89 (2016)
Anand, J.G.: Trust based optimal routing in MANET's. In: 2011 International Conference on Emerging Trends in Electrical and Computer Technology (pp. 1150–1156). IEEE (2011)
Divyabharathi, S.: Large scale optimization to minimize network traffic using MapReduce in big data applications. In: International Conference on Computation of Power, Energy Information and Communication (ICCPEIC), pp. 193–199. https://doi.org/10.1109/ICCPEIC.2016.7557196 (2016)
Kamalraj, R., Neelakandan, S., Ranjith Kumar, M., Chandra Sekhar Rao, V., Anand R., Singh, H.: Interpretable filter based convolutional neural network for glucose prediction and classification using. Measurement 183, 184 (2021)
Yiğit, B., Gür, G., Alagöz, F., Tellenbach, B.: Cost-aware securing of IoT systems using attack graphs. Ad Hoc Netw. 86, 23–35 (2019)
Berlin, M.A., Tripathi, S., et al.: IoT-based traffic prediction and traffic signal control system for smart city. Soft. Comput. (2021). https://doi.org/10.1007/s00500-021-05896-x
Almobaideen, W., Krayshan, R., Allan, M., Saadeh, M.: Internet of Things: geographical routing based on healthcare centers vicinity for mobile smart tourism destination. Technol. Forecast. Soc. Chang. 123, 342–350 (2017)
Shende, D.K. and Sonavane, S.S., 2020. CrowWhale-ETR CrowWhale optimization algorithm for energy and trust aware multicast routing in WSN for IoT applications. Wireless Networks 1:1–19. Doi: https://doi.org/10.1007/s11276-020-02299-y(0123456789(
Malchi, S.K., Kallam, S., Al-Turjman, F., Patan, R.: A trust-based fuzzy neural network for smart data fusion in internet of things. Comput. Electr. Eng. 89, 106901 (2021)
Seyfollahi, A., Ghaffari, A.: Reliable data dissemination for the Internet of Things using Harris hawks optimization. Peer-to-Peer Netw. Appl. 13(6), 1886–1902 (2020)
Wang, Y., Zhang, M., Shu, W.: An emerging intelligent optimization algorithm based on trust sensing model for wireless sensor networks. EURASIP J. Wirel. Commun. Netw. 2018(1), 1–10 (2018)
Gali, S., Nidumolu, V.: Multi-context trust aware routing for internet of things. Int. J. Intell. Eng. Syst. 12(1), 189–200 (2018)
Mabodi, K., Yusefi, M., Zandiyan, S., Irankhah, L., Fotohi, R.: Multi-level trust-based intelligence schema for securing of internet of things (IoT) against security threats using cryptographic authentication. J. Supercomput. 76, 7081–7106 (2020)
Mo, W., Wang, T., Zhang, S., Zhang, J.: An active and verifiable trust evaluation approach for edge computing. J. Cloud Comput. 9(1), 1–19 (2020)
Djedjig, N., Tandjaoui, D., Medjek, F., Romdhani, I.: Trust-aware and cooperative routing protocol for IoT security. J. Inf. Secur. Appl. 52, 102467 (2020)
Tandon, A., Srivastava, P.: Trust-based enhanced secure routing against rank and sybil attacks in IoT. In: 2019 Twelfth International Conference on Contemporary Computing (IC3), pp. 1–7. IEEE (2019).
Stavrinides, G.L., Karatza, H.D.: Orchestrating real-time IoT workflows in a fog computing environment utilizing partial computations with end-to-end error propagation. Clust. Comput. 24, 3629–3650 (2021). https://doi.org/10.1007/s10586-021-03327-y
Ghamry, W.K., Shukry, S.: Spectrum access in cognitive IoT using reinforcement learning. Clust. Comput. 24, 2909–2925 (2021). https://doi.org/10.1007/s10586-021-03306-3
Etemadi, M., Ghobaei-Arani, M., Shahidinejad, A.: A cost-efficient auto-scaling mechanism for IoT applications in fog computing environment: a deep learning-based approach. Clust. Comput. 24, 3277–3292 (2021)
Denko, M.K., Sun, T., Woungang, I.: Trust management in ubiquitous computing: a Bayesian approach. Comput. Commun. 34(3), 398–406 (2011)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Gali, S., Nidumolu, V. An intelligent trust sensing scheme with metaheuristic based secure routing protocol for Internet of Things. Cluster Comput 25, 1779–1789 (2022). https://doi.org/10.1007/s10586-021-03473-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-021-03473-3