Abstract
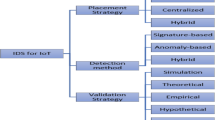
The Internet of Things (IoT) is a paradigm that connects objects to the Internet as a whole and enables them to work together to achieve common objectives, such as innovative home automation. Potential attackers see the scattered and open IoT service structure as an appealing target for cyber-attacks. So, security cannot be dealt with independently. Security must be designed and built-in to every layer of the IoT system. IoT security concerns not only network and data security but also human health and life attacks. Therefore, the development of the loT system to provide security through resistance to attacks is a de facto requirement to make the loT safe and operational. Protecting these things is very important for system security. Plus, it is important to integrate the Intrusion Detection System (IDS) with IoT systems. IDS intends to track and analyze network traffic from different resources and detect malicious activities. It is a significant part of cybersecurity technology. In short, IDS is a process used to detect malicious activities against victims by several methods. Besides, the method of Systematic Literature Review (SLR) is used to classify, review, and incorporate results from all similar research that answers one or more IDS research topics and perform a detailed empirical research analysis on IDS techniques. Furthermore, depending on the detection technique, we classify IDS approaches in IoT as signature-based, anomaly-based, specification-based, and hybrid. Also, for the IDS approaches, the authors give a parametric comparison. The benefits and drawbacks of the chosen mechanisms are then addressed. Eventually, there is an analysis of open problems as well as potential trend directions.
















Similar content being viewed by others
Data availability
The paper contains all of the data.
References
Andoni, M., et al.: Blockchain technology in the energy sector: A systematic review of challenges and opportunities. Renew. Sustain. Energy Rev. 100, 143–174 (2019)
Heidari, A., et al.: Internet of Things offloading: ongoing issues, opportunities, and future challenges. Int. J. Commun Syst 33(14), e4474 (2020)
Rahman, S.A., et al.: Internet of things intrusion detection: centralized, on-device, or federated learning? IEEE Network 34(6), 310–317 (2020)
Jamali, J. et al.: Towards the internet of things. Springer (2020)
Jamali, M.A.J., et al.: The IoT landscape. In: Towards the Internet of Things, pp. 1–8. Springer, New York (2020)
Heidari, A. and N.J. Navimipour.: Service Discovery Mechanisms in the Cloud Computing: A Comprehensive and Systematic Literature Review. Kybernetes, (2021)
Venkatraman, S., Surendiran, B.: Adaptive hybrid intrusion detection system for crowd sourced multimedia internet of things systems. Multimedia Tools Appl. 79(5), 3993–4010 (2020)
Jamali, M.A.J. et al.: Towards the internet of things architectures, security, and applications.
Dutta, M., Granjal, J.: Towards a secure internet of things: a comprehensive study of second line defense mechanisms. IEEE Access 8, 127272–127312 (2020)
Simoglou, G., et al.: Intrusion Detection Systems for RPL Security: A Comparative Analysis. Computers & Security, p. 102219 (2021)
Boyanapalli, A., Shanthini, A.: A Comparative study of techniques, datasets and performances for intrusion detection systems in IoT. In: Artificial Intelligence Techniques for Advanced Computing Applications. Springer. pp. 225–236
Ramaiah, M., et al.: An intrusion detection system using optimized deep neural network architecture. Transactions on Emerging Telecommunications Technologies: pp. e4221
Ghobaei-Arani, M., Souri, A., Rahmanian, A.A.: Resource management approaches in fog computing: a comprehensive review. J. Grid Comput. 18(1), 1–42 (2020)
Souri, A., Ghobaei-Arani, M.: Cloud manufacturing service composition in IoT applications: a formal verification-based approach. Multimedia Tools Appl. pp. 1–20 (2021)
Jabraeil Jamali, M.A., et al.: IoT security. In: Towards the Internet of Things: Architectures, Security, and Applications, pp. 33–83. Springer International Publishing, Cham (2020)
Stojmenovic, I., et al.: An overview of fog computing and its security issues. Concurr. Comput. 28(10), 2991–3005 (2016)
Balasundaram, J., A novel optimized Bat Extreme Learning intrusion detection system for smart Internet of Things networks. Int. J. Commun. Syst. p. e4729.
Almiani, M., et al.: Deep recurrent neural network for IoT intrusion detection system. Simul. Model. Pract. Theory 101, 102031 (2020)
Heidari, A., et al.: Machine learning applications for COVID-19 outbreak management. Neural Comput. Appl. (2022)
Khraisat, A., Alazab, A.: A critical review of intrusion detection systems in the internet of things: techniques, deployment strategy, validation strategy, attacks, public datasets and challenges. Cybersecurity 4(1), 1–27 (2021)
Heidari, A., et al.: The COVID-19 epidemic analysis and diagnosis using deep learning: A systematic literature review and future directions. Comput. Biol. Med. p. 105141 (2021)
Jamali, M.A.J., et al.: IoT architecture. Towards Internet Things pp. 9–31 (2020)
Heidari, A., et al.: A privacy-aware method for COVID-19 detection in chest CT images using lightweight deep conventional neural network and blockchain. Comput. Biol. Med. p. 105461 (2022)
Yahyaoui, A., et al.: READ-IoT: reliable event and anomaly detection framework for the internet of things. IEEE Access 9, 24168–24186 (2021)
Liu, Z., et al.: Intrusion detection systems in the cloud computing: a comprehensive and deep literature review. Concurr. Comput., p. e6646 (2021)
Meng, W., Li, W., Zhou, J.: Enhancing the security of blockchain-based software defined networking through trust-based traffic fusion and filtration. Inform. Fusion 70, 60–71 (2021)
Jamali, M.A.J., et al.: Some cases of smart use of the IoT. In: Towards the internet of things, pp. 85–129. Springer, New York (2020)
Balasundaram, J.: A novel optimized Bat Extreme Learning intrusion detection system for smart Internet of Things networks. Int. J. Commun. Syst. 34(7), e4729 (2021)
Kalathiripi, R.: Regression coefficients of traffic flow metrics (RCTFM) for DDOS defense in IoT networks. Int. J. Commun Syst 34(6), e4330 (2021)
Liang, W. et al.: Data Fusion Approach for Collaborative Anomaly Intrusion Detection in Blockchain-based Systems. IEEE Internet Things J. (2021)
Heidari, A., Navimipour, N.J.: A new SLA-aware method for discovering the cloud services using an improved nature-inspired optimization algorithm. PeerJ Comput. Sci. (2021)
Sajith, P., Nagarajan, G.: Optimized intrusion detection system using computational intelligent algorithm. In: Advances in Electronics, Communication and Computing, pp. 633–639. Springer, New York (2021)
Kumar, R., Tripathi, R.: DBTP2SF: a deep blockchain‐based trustworthy privacy‐preserving secured framework in industrial internet of things systems. Trans. Emerging Telecommun. Technol. p. e4222 (2021)
Iqbal, S., et al.: On cloud security attacks: A taxonomy and intrusion detection and prevention as a service. J. Netw. Comput. Appl. 74, 98–120 (2016)
Vieira, K., et al.: Intrusion detection for grid and cloud computing. It Professional 12(4), 38–43 (2009)
Patel, A., et al.: An intrusion detection and prevention system in cloud computing: a systematic review. J. Netw. Comput. Appl. 36(1), 25–41 (2013)
Keserwani, P.K., et al.: A smart anomaly-based intrusion detection system for the Internet of Things (IoT) network using GWO–PSO–RF model. J. Reliable Intell. Environ., pp. 1–19 (2021)
Manhas, J., Kotwal, S.: Implementation of intrusion detection system for internet of things using machine learning techniques. In: Multimedia Security, pp. 217–237. Springer, New York (2021)
Hu, N., et al.: A multiple-kernel clustering based intrusion detection scheme for 5G and IoT networks. Int. J. Mach. Learn. Cybernet. pp. 1–16.
Jamali, M.A.J., et al.: Towards the Internet of Things: Architectures, Security, and Applications. Springer, New York (2019)
Wu, J.: Security and intelligent management for fog/edge computing resources. In: Fog/Edge Computing For Security, Privacy, and Applications, pp. 213–234. Springer, New York (2021)
Atul, D.J., et al.: A machine learning based IoT for providing an intrusion detection system for security. Microprocess. Microsyst. 82, 103741 (2021)
Batiha, T., Krömer, P.: Design and analysis of efficient neural intrusion detection for wireless sensor networks. Concurr. Comput. p. e6152 (2020)
Qiu, H., et al.: Adversarial attacks against network intrusion detection in IoT systems. IEEE Internet Things J. (2020)
Yang, Z., et al.: A systematic literature review of methods and datasets for anomaly-based network intrusion detection. Comput. Secur. p. 102675 (2022)
Rani, R., et al.: Towards green computing oriented security: a lightweight postquantum signature for IoE. Sensors 21(5), 1883 (2021)
Keserwani, P.K., et al.: A smart anomaly-based intrusion detection system for the Internet of Things (IoT) network using GWO–PSO–RF model. J. Reliab. Intell. Environ. 7(1), 3–21 (2021)
Du, H., Zhang, Y.: Network anomaly detection based on selective ensemble algorithm. J. Supercomput. 77(3), 2875–2896 (2021)
Irshad, M.: A systematic review of information security frameworks in the internet of things (iot). in High Performance Computing and Communications; IEEE 14th International Conference on Smart City; IEEE 2nd International Conference on Data Science and Systems (HPCC/SmartCity/DSS), 2016 IEEE 18th International Conference on. IEEE (2016)
Bahram Abadi, R.M., Rahmani, A.M., Alizadeh, S.H.: Server consolidation techniques in virtualized data centers of cloud environments: A systematic literature review. Software 48(9), 1688–1726 (2018)
Al-Samarraie, H., Saeed, N.: A systematic review of cloud computing tools for collaborative learning: opportunities and challenges to the blended-learning environment. Comput. Educ. 124(May), 77–91 (2018)
Zarpelão, B.B., et al.: A survey of intrusion detection in Internet of Things. J. Netw. Comput. Appl. 84, 25–37 (2017)
Almalawi, A., et al.: Add-on anomaly threshold technique for improving unsupervised intrusion detection on SCADA data. Electronics 9(6), 1017 (2020)
Eskandari, M., et al.: Passban IDS: An intelligent anomaly based intrusion detection system for IoT edge devices. IEEE Internet Things J. (2020)
Kim, S., Hwang, C., Lee, T.: Anomaly based unknown intrusion detection in endpoint environments. Electronics 9(6), 1022 (2020)
Gothawal, D.B., Nagaraj, S.: Anomaly-based intrusion detection system in RPL by applying stochastic and evolutionary game models over IoT environment. Wireless Pers. Commun. 110(3), 1323–1344 (2020)
Alhakami, W., et al.: Network anomaly intrusion detection using a nonparametric Bayesian approach and feature selection. IEEE Access 7, 52181–52190 (2019)
Roy, S., et al.: A lightweight supervised intrusion detection mechanism for IoT networks. Futur. Gener. Comput. Syst. 127, 276–285 (2022)
Vacca, J.R.: Computer and information security handbook. Newnes (2012)
Li, W., et al.: Designing collaborative blockchained signature-based intrusion detection in IoT environments. Futur. Gener. Comput. Syst. 96, 481–489 (2019)
Li, J., et al.: Ai-based two-stage intrusion detection for software defined iot networks. IEEE Internet Things J. 6(2), 2093–2102 (2018)
Meng, W., et al.: Towards blockchain-enabled single character frequency-based exclusive signature matching in IoT-assisted smart cities. J. Parall. Distribut. Comput. 144, 268–277 (2020)
Kumar, M., Verma, H.K., Sikka, G.: A secure lightweight signature based authentication for Cloud-IoT crowdsensing environments. Trans. Emerging Telecommun. Technol. 30(4), e3292 (2019)
Otoum, Y., Nayak, A.: AS-IDS: anomaly and signature based IDS for the Internet of Things. J. Netw. Syst. Manage. 29(3), 1–26 (2021)
Díaz-Verdejo, J., et al.: On the detection capabilities of signature-based intrusion detection systems in the context of web attacks. Appl. Sci. 12(2), 852 (2022)
Mitchell, R., Chen, I.-R.: A survey of intrusion detection techniques for cyber-physical systems. ACM Comput. Surveys (CSUR) 46(4), 55 (2014)
Quincozes, S.E., et al.: GRASP-based Feature Selection for Intrusion Detection in CPS Perception Layer. In: 2020 4th Conference on Cloud and Internet of Things (CIoT). IEEE (2020)
Spathoulas, G., Katsikas, S.: Methods for post-processing of alerts in intrusion detection: a survey. Int. J. Inform. Secur. Sci. 2(2), 64–80 (2013)
Cui, J.-F. et al.: Optimization scheme for intrusion detection scheme GBDT in edge computing center. Comput. Commun. (2020).
Sharma, V., et al.: BRIoT: behavior rule specification-based misbehavior detection for IoT-embedded cyber-physical systems. IEEE Access 7, 118556–118580 (2019)
Choudhary, G., et al.: Lightweight misbehavior detection management of embedded IoT devices in medical cyber physical systems. IEEE Trans. Netw. Serv. Manage. 17(4), 2496–2510 (2020)
Siu, J.Y., Panda, S.K.: A Specification-Based Detection for Attacks in the Multi-Area System. In: IECON 2020 the 46th Annual Conference of the IEEE Industrial Electronics Society. IEEE (2020)
Babu, M.J., Reddy, A.R.: SH-IDS: specification heuristics based intrusion detection system for IoT networks. Wireless Pers. Commun. 112(3), 2023–2045 (2020)
Violettas, G., et al.: A softwarized intrusion detection system for the RPL-based Internet of Things networks. Futur. Gener. Comput. Syst. 125, 698–714 (2021)
Santos, L., et al.: A flow-based intrusion detection framework for internet of things networks. Clust. Comput. pp. 1–21 (2021)
Davahli, A., Shamsi, M., Abaei, G.: Hybridizing genetic algorithm and grey wolf optimizer to advance an intelligent and lightweight intrusion detection system for IoT wireless networks. J. Ambient Intell. Hum. Comput. (2020)
RM, S.P., et al.; An effective feature engineering for DNN using hybrid PCA-GWO for intrusion detection in IoMT architecture. Comput. Commun. (2020)
Li, W., Meng,W., Au, M.H.: Enhancing collaborative intrusion detection via disagreement-based semi-supervised learning in IoT environments. J. Netw. Comput. Appl. pp. 102631 (2020)
Bostani, H., Sheikhan, M.: Hybrid of anomaly-based and specification-based IDS for Internet of Things using unsupervised OPF based on MapReduce approach. Comput. Commun. 98, 52–71 (2017)
Moizuddin, M., Jose, M.V.: A bio-inspired hybrid deep learning model for network intrusion detection. Knowl.-Based Syst. 238, 107894 (2022)
de Souza, C.A., et al.: Hybrid approach to intrusion detection in fog-based IoT environments. Comput. Netw. 180, 107417 (2020)
Muhammad, G., Hossain, M.S., Garg, S.: Stacked Autoencoder-based Intrusion Detection System to Combat Financial Fraudulent. IEEE Internet Things J. (2020)
Kumar, P., Gupta, G.P., Tripathi, R.: TP2SF: a trustworthy privacy-preserving secured framework for sustainable smart cities by leveraging blockchain and machine learning. J. Syst. Archit. p. 101954, (2020)
Kumar, P., Gupta, G.P., Tripathi, R.: A distributed ensemble design based intrusion detection system using fog computing to protect the internet of things networks. J. Ambient Intell. Hum. Comput. pp. 1–18 (2020)
Heartfield, R., et al.: Self-configurable cyber-physical intrusion detection for smart homes using reinforcement learning. IEEE Trans. Inf. Forensics Secur. 16, 1720–1735 (2020)
Satam, P. Hariri, S.: WIDS: an anomaly based intrusion detection system for Wi-Fi (IEEE 802.11) Protocol. IEEE Transactions on Network and Service Management (2020)
Gassais, R., et al.: Multi-level host-based intrusion detection system for Internet of things. J. Cloud Comput. 9(1), 1–16 (2020)
Singh, P. et al.: DaaS: dew computing as a service for intelligent intrusion detection in edge-of-things ecosystem. IEEE Internet Things J. (2020)
Xu, X., et al.: Towards effective intrusion detection using log-cosh conditional variational autoencoder. IEEE Internet Things J. (2020)
Sadikin, F., van Deursen, T., Kumar, S.: A ZigBee intrusion detection system for IoT using secure and efficient data collection. Internet Things 12, 100306 (2020)
D’Angelo, G., Castiglione, A., Palmieri, F.: A cluster-based multidimensional approach for detecting attacks on connected vehicles. IEEE Internet Things J. (2020)
Funding
Not applicable.
Author information
Authors and Affiliations
Corresponding authors
Ethics declarations
Conflict of interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Ethical approval
Not Applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Heidari, A., Jabraeil Jamali, M.A. Internet of Things intrusion detection systems: a comprehensive review and future directions. Cluster Comput 26, 3753–3780 (2023). https://doi.org/10.1007/s10586-022-03776-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-022-03776-z