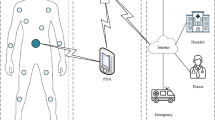
Abstract
The new and integrated technologies have changed the traditional systems and services with new and smart automation systems. Smart healthcare system is one of the example of patients monitoring systems with more smart and cost effective services to protect the people who suffered from physical or psychological diseases, illnesses, and health concerns. wireless body area network contains smart sensor nodes planted inside or outside the patient body by using sensing and monitoring capabilities. With various benefits, these networks have some serious security challenges where the patient data is compromised due to different types of security attacks. Biomedical devices and sensor nodes are communicating internally or externally and always the open and easy target for attackers. There are various types of routing protocols have been designed for security but due to their complex and heavy processes the sensor nodes energy depleted, delay and overhead occurred. Due to limited resources of sensor nodes like battery, processing, memory, and storage, these networks need special lightweight security solutions. In this context, this paper proposes an interoperability and security for data authentication scheme for body area network protocol by using different leftover features like forwarding data security and address the synchronization and key control issues. The proposed protocol provides security for both internal and external devices and protect the data from any kind of unauthorized data breach. Experiments results indicated the better performance of the proposed protocol as compared with the state-of-the-art schemes. The proposed protocol is one of the effective security addition for secure medical healthcare data transmission.









Similar content being viewed by others
Data availability
Enquiries about data availability should be directed to the authors.
References
Mukherjee, P., Mukherjee, A.: Advanced processing techniques and secure architecture for sensor networks in ubiquitous healthcare systems. In: Sensors for health monitoring, pp. 3–29. Elsevier (2019)
Anwar, M., Abdullah, A.H., Altameem, A., Qureshi, K.N., Masud, F., Faheem, M., Cao, Y., Kharel, R.: Green communication for wireless body area networks: energy aware link efficient routing approach. Sensors 18(10), 3237 (2018)
Anwar, M., Abdullah, A.H., Butt, R.A., Ashraf, M.W., Qureshi, K.N., Ullah, F.: Securing data communication in wireless body area networks using digital signatures,. Tech. J. 23(02), 50–55 (2018)
Kang, J., Fan, K., Zhang, K., Cheng, X., Li, H., Yang, Y.: An ultra light weight and secure RFID batch authentication scheme for IoMT. Comput. Commun 167, 48–54 (2021)
Xu, G., Li, X., Jiao, L., Wang, W., Liu, A., Su, C., Zheng, X., Liu, S., Cheng, X.: Bagkd: a batch authentication and group key distribution protocol for vanets. IEEE Commun. Mag 58(7), 35–41 (2020)
Qureshi, M.A., Qureshi, K.N., Jeon, G., Piccialli, F.: Deep learning-based ambient assisted living for self-management of cardiovascular conditions. Neural Comput Appl (2021). https://doi.org/10.1007/s00521-020-05678-w
Qureshi, K.N., Ahmad, A., Piccialli, F., Casolla, G., Jeon, G.: Nature-inspired algorithm-based secure data dissemination framework for smart city networks. Neural Comput Appl (2020). https://doi.org/10.1007/s00521-020-04900-z
Qureshi, K.N., Jeon, G., Piccialli, F.: Anomaly detection and trust authority in artificial intelligence and cloud computing. Comput Netw 2020,(2020)
Yetgin, H., Cheung, K.T.K., El-Hajjar, M., Hanzo, L.H.: A survey of network lifetime maximization techniques in wireless sensor networks,. IEEE Commun. Surv. Tutorials. 19(2), 828–854 (2017)
Butt, S.A., Jamal, T., Azad, M.A., Ali, A., Safa, N.S.: A multivariant secure framework for smart mobile health application. Trans Emerg Telecommun Technol 2019,(2019)
Qureshi, K.N., Din, S., Jeon, G., Piccialli, F.: Link quality and energy utilization based preferable next hop selection routing for wireless body area networks. Comput. Commun 149, 382–392 (2020)
Das, A.K., Zeadally, S., Wazid, M.: Lightweight authentication protocols for wearable devices. Comput. Electr. Eng 63, 196–208 (2017)
Sourav, S., Odelu, V., Prasath, R.: Enhanced session initiation protocols for emergency healthcare applications. In: International symposium on security in computing and communication, pp. 278–289. Springer, USA (2018)
Kumari, S., Das, A.K., Li, X., Wu, F., Khan, M.K., Jiang, Q., Islam, S.H.: A provably secure biometrics-based authenticated key agreement scheme for multi-server environments. Multimed Tools Appl 77(2), 2359–2389 (2018)
Xu, G., Qiu, S., Ahmad, H., Xu, G., Guo, Y., Zhang, M., Xu, H.: A multi-server two-factor authentication scheme with un-traceability using elliptic curve cryptography. Sensors 18(7), 2394 (2018)
Jusak, J., Mahmoud, S.S.: A novel and low processing time ecg security method suitable for sensor node platforms. Int. J. Commun Netw Inform. Secur 10(1), 213–222 (2018)
Amin, R., Islam, S.H., Biswas, G., Obaidat, M.S.: A robust mutual authentication protocol for WSN with multiple base-stations. Ad Hoc Netw 75, 1–18 (2018)
Yu, Y., Hu, L., Chu, J.: A secure authentication and key agreement scheme for IoT-based cloud computing environment. Symmetry 12(1), 150 (2020)
Shynu, P., Nadesh, R., Menon, V.G., Venu, P., Abbasi, M., Khosravi, M.R.: A secure data deduplication system for integrated cloud-edge networks. J. Cloud Comput 9(1), 1–12 (2020)
Almuhaideb, A.M., Alghamdi, H.A.: Secure and efficient WBAN authentication protocols for intra-BAN tier. J. Sens. Actu Netw 11(3), 44 (2022)
Zhang, J., Dong, C.: Secure and lightweight data aggregation scheme for anonymous multi-receivers in WBAN. IEEE Trans Netw Sci Eng 2022, 1–10 (2022)
Ostad-Sharif, A., Abbasinezhad-Mood, D., Nikooghadam, M.: A robust and efficient ECC-based mutual authentication and session key generation scheme for healthcare applications. J. Med. Syst 43(1), 1–22 (2019)
Koblitz, N.: Elliptic curve cryptosystems. Math. Comput 48(177), 203–209 (1987)
Miller, V.S.: Use of elliptic curves in cryptography. In: Conference on the theory and application of cryptographic techniques, pp. 417–426. Springer (1985)
Naresh, V.S., Sivaranjani, R., Murthy, N.V.E.S.: Provable secure lightweight hyper elliptic curve-based communication system for wireless sensor networks,. Int. J. Commun Syst. 31(15), e3763 (2018)
Li, X., Peng, J., Kumari, S., Wu, F., Karuppiah, M., Choo, K.K.R.: An enhanced 1-round authentication protocol for wireless body area networks with user anonymity. Comput. Electr. Eng 61, 238–249 (2017)
Mehmood, T.: Cooja network simulator: exploring the infinite possible ways to compute the performance metrics of iot based smart devices to understand the working of iot based compression & routing protocols. arXiv preprint arXiv:1712.08303, (2017)
Amin, R., Islam, S.H., Biswas, G., Khan, M.K., Kumar, N.: A robust and anonymous patient monitoring system using wireless medical sensor networks. Future Gener Comput Syst 80, 483–495 (2018)
Li, X., Niu, J., Kumari, S., Wu, F., Sangaiah, A.K., Choo, K.K.R.: A three-factor anonymous authentication scheme for wireless sensor networks in internet of things environments. J. Netw. Comput. Appl 103, 194–204 (2018)
Vigano, L.: Automated security protocol analysis with the AVISPA tool. Electron. Notes Theor. Comput. Sci 155, 61–86 (2006)
Zhao, Z.: An efficient anonymous authentication scheme for wireless body area networks using elliptic curve cryptosystem. J. Med. Syst 38(2), 1–7 (2014)
Funding
The authors have not disclosed any funding.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors have not disclosed any competing interests.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Kiyani, F., Qureshi, K.N., Ghafoor, K.Z. et al. ISDA-BAN: interoperability and security based data authentication scheme for body area network. Cluster Comput 26, 2429–2442 (2023). https://doi.org/10.1007/s10586-022-03823-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-022-03823-9