Abstract
The wide and rapid adoption of Android-based devices in the last years has motivated the usage of Android apps to support a broad range of daily activities. In that sense, being the most popular mobile platform makes it an attractive target for security attacks. In fact, 1,489 security vulnerabilities have been reported in the last three years (2015-2017) for the Android OS (which is the underlying platform for Android-based devices). While there is a plethora of approaches and tools for detecting malware and security issues in Android apps, few research has been done to identify, categorize, or detect vulnerabilities in the Android OS. In this paper we present the largest study so far aimed at analyzing software vulnerabilities in the Android OS. In particular, we analyzed a total of 1,235 vulnerabilities from four different perspectives: vulnerability types and their evolution, CVSS vectors that describe the vulnerabilities, impacted Android OS layers, and their survivability across the Android OS history. Based on our findings, we propose a list of future actions that could be performed by researchers and practitioners to reduce the number of vulnerabilities in the Android OS as well as their impact and survivability.












Similar content being viewed by others
Notes
We used the base group attributes because it is the only mandatory group.
Meta-analysis is a statistical inference technique aimed at consolidating results from more than one study or experiment.
We found 129 vulnerabilities for the 2017-2 period, but we excluded this semester from the RQ5 analysis because we do not have complete data for 2017-2.
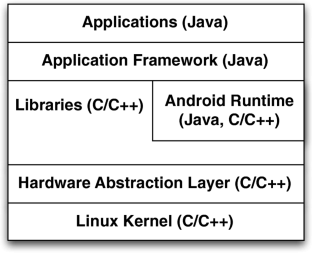
We were not able to classify the layer affected by 5 vulnerabilities.
Note that there is also an Unclear category because in six cases we were not able to identify the type of change because of the patches complexity . For instance, in CVE-2016-3751 several changes were done over 207 files, thus it was not easy to categorize the changes.
For the base group attributes in CVSS 2.0, there are 729 possible combinations of attribute values. Therefore, the 1,235 analyzed vulnerabilities cover 6.72% (49 out of 729) of all the CVSS 2.0 vectors for the base group attributes.
Compared to Linares-Vásquez et al. (2017), in our dataset we observed 354 new vulnerabilities in the Kernel that have been reported from November 2016 to August 2017.
Note that we only report numbers for vulnerabilities in the AOSP apps and reported as vulnerabilities in the NVD database.
Note that all p-values equal 1.0 after the holm correction procedure. Before that they were in any case all higher than 0.7.
References
Aosp commit cf1581c66c2ad8c5b1aaca2e43e350cf5974f46d (2017a) http://tinyurl.com/hxqdp7f
Aosp commit 8ec845c8fe0f03bc57c901bc484541bdd6a7cf80 (2017b) http://tinyurl.com/hvndh7r
Aosp commit edd4a76eb4747bd19ed122df46fa46b452c12a0d (2017c) http://tinyurl.com/hkw399d
Ahmad W, Kästner C, Sunshine J, Aldrich J (2016) Inter-app communication in android: Developer challenges. In: Proceedings of the 13th international conference on mining software repositories, MSR ’16. ACM, New York, pp 177–188. https://doi.org/10.1145/2901739.2901762
Anderson B, et al. (2016) Hpe security research. cyber risk report 2016. Tech. rep., Hewlett Packard
Armis (2017) The attack vector “blueborne” exposes almost every connected device. https://www.armis.com/blueborne/
Arzt S, Rasthofer S, Fritz C, Bodden E, Bartel A, Klein J, Le Traon Y, Octeau D, McDaniel P (2014) Flowdroid: Precise context, flow, field, object-sensitive and lifecycle-aware taint analysis for android apps. In: Proceedings of the 35th ACM SIGPLAN Conference on Programming Language Design and Implementation, PLDI ’14. ACM, New York, pp 259–269. https://doi.org/10.1145/2594291.2594299
Avdiienko V, Kuznetsov K, Gorla A, Zeller A, Arzt S, Rasthofer S, Bodden E (2015) Mining apps for abnormal usage of sensitive data. In: ICSE’15, pp 426–436. http://dl.acm.org/citation.cfm?id=2818754.2818808
Backes M, Bugiel S, Derr E (2016) Reliable third-party library detection in android and its security applications. In: Proceedings of the 2016 ACM SIGSAC conference on computer and communications security, CCS ’16. ACM, New York, pp 356–367. https://doi.org/10.1145/2976749.2978333
Bagheri H, Kang E, Malek S, Jackson D (In Press) A formal approach for detection of security flaws in the android permission system. Springer Journal on Formal Aspects of Computing
Bagheri H, Sadeghi A, Garcia J, Malek S (2015) Covert: compositional analysis of android inter-app permission leakage. IEEE Trans Softw Eng 41(9):866–886. https://doi.org/10.1109/TSE.2015.2419611
Beres D (2015) ‘cowboy adventure’ game infects up to 1 million android users with malware. http://www.huffingtonpost.com/2015/07/10/android-security_n_7765842.html
Bhosale A (2014) Precise static analysis of taint flow for android application sets. Master’s thesis, Heinz College Carnegie Mellon University
Brady P (2008) Anatomy & physiology of an android. https://sites.google.com/site/io/anatomy--physiology-of-an-android https://sites.google.com/site/io/anatomy--physiology-of-an-android
Burgess M (2016) Millions of android devices vulnerable to new stagefright exploit. http://www.wired.co.uk/article/stagefright-android-real-world-hack
Cao C, Gao N, Liu P, Xiang J (2015) Towards analyzing the input validation vulnerabilities associated with android system services. In: Proceedings of the 31st annual computer security applications conference, ACSAC 2015. ACM, New York, pp 361–370. https://doi.org/10.1145/2818000.2818033
Castellanos JH, Wuchner T, Ochoa M, Rueda S (2016) Q-floid: Android malware detection with quantitative data flow graphs. In: Singapore cyber-security conference (SG-CRC). IOS Press, pp 13–26
Christensen R (2011) Plane Answers to Complex Questions: The Theory of Linear models, 4th edn. Springer Texts in Statistics Springer, Berlin
Conover WJ (1998) Practical Nonparametric Statistics, 3rd edn. Wiley, New York
Corporation M (2017) Cve common vulnerabilities and exposures. http://cve.mitre.org
Cumming G (2011) Introduction to the new Statistics: Effect sizes, confidence intervals, and Meta-Analysis. Routledge, Evanston
Cve-2012-6636 (2017) https://www.cvedetails.com/cve/cve-2012-6636
Dimjaševic M, Atzeni S, Ugrina I, Rakamaric Z (2015) Android malware detection based on system calls
Drake JJ, Lanier Z, Mulliner C, Fora PO, Ridley SA, Wicherski G (2014) Android hacker’s handbook. Wiley, New York
Enck W, Gilbert P, Chun BG, Cox L, Jung J, McDaniel P, Sheth AN (2010) Taintdroid: an information-flow tracking system for realtime privacy monitoring on smartphones. In: Proceedings of the 9th USENIX conference on operating systems design and implementation, OSDI’10. USENIX Association, Berkeley, pp 393–407. http://dl.acm.org/citation.cfm?id=1924943.1924971
Enck W, Ongtang M, McDaniel P (2009) On lightweight mobile phone application certification. In: Proceedings of the 16th ACM conference on computer and communications security, CCS ’09. ACM, New York, pp 235–245. https://doi.org/10.1145/1653662.1653691
Fahl S, Harbach M, Muders T, Baumgärtner L., Freisleben B, Smith M (2012) Why eve and mallory love android: an analysis of android ssl (in)security. In: Proceedings of the 2012 ACM conference on computer and communications security, CCS ’12. ACM, New York, pp 50–61. https://doi.org/10.1145/2382196.2382205
Fattori A, Tam K, Khan SJ, Cavallaro L, Reina A (2014) CopperDroid: On the Reconstruction of Android Malware Behaviors. Tech. rep. Royal Holloway University of London
FIRST Organization (2019) Common vulnerability scoring system sig. https://www.first.org/cvss
for Standardization IO (2011) Iso 27005 information security risk management
Garcia J, Hammad M, Ghorbani N, Malek S (2017) Automatic generation of inter-component communication exploits for android applications. In: Proceedings of the 2017 11th joint meeting on foundations of software engineering, ESEC/FSE 2017. ACM, New York, pp 661–671. https://doi.org/10.1145/3106237.3106286
Gasior W, Yang L (2012) Exploring covert channel in android platform. In: 2012 international conference on cyber security, pp 173–177. https://doi.org/10.1109/CyberSecurity.2012.29
Ghafari M, Gadient P, Nierstrasz O (2017) Security smells in android. In: 2017 IEEE 17th international working conference on source code analysis and manipulation (SCAM), pp 121–130. https://doi.org/10.1109/SCAM.2017.24
Gilbert P, Chun BG, Cox LP, Jung J (2011) Vision: automated security validation of mobile apps at app markets. In: Proceedings of the second international workshop on mobile cloud computing and services, MCS ’11. ACM, New York, pp 21–26. https://doi.org/10.1145/1999732.1999740
Gorla A, Tavecchia I, Gross F, Zeller A (2014) Checking app behavior against app descriptions. In: ICSE’14, pp 1025–1035. https://doi.org/10.1145/2568225.2568276
Google (2016) Android security 2015 year in review. https://static.googleusercontent.com/media/source.android.com/en//security/reports/Google_Android_Security_2015_Report_Final.pdf
Google (2017a) Android security bulletins. https://source.android.com/security/bulletin/
Google (2017b) Platform architecture. https://developer.android.com/guide/platform/index.html
Graf J, Hecker MMM (2015) Jodroid: Adding android support to a static information flow control tool. In: Working conference on programming languages
Grissom RJ, Kim JJ (2005) Effect sizes for research: a broad practical approach, 2nd edn. Lawrence Earlbaum Associates, New Jersey
Hedges LV, Olkin I (1985) Statistical methods for Meta-Analysis. Academic Press, New York
Herzig K, Zeller A (2013) The impact of tangled code changes. In: Proceedings of the 10th Working Conference on Mining Software Repositories, MSR ’13, San Francisco, pp 121–130
Holm S (1979) A simple sequentially rejective Bonferroni test procedure. Scand J Stat 6:65–70
Huang H, Zhu S, Chen K, Liu P (2015) From system services freezing to system server shutdown in android: All you need is a loop in an app. In: Proceedings of the 22nd ACM SIGSAC conference on computer and communications security, CCS ’15. ACM, New York, pp 1236–1247. https://doi.org/10.1145/2810103.2813606
Jimenez M, Papadakis M, Bissyandé TF, Klein J (2016) Profiling android vulnerabilities. In: 2016 IEEE International conference on software quality, reliability and security (QRS), pp 222–229. https://doi.org/10.1109/QRS.2016.34 https://doi.org/10.1109/QRS.2016.34
Kantola D, Chin E, He W, Wagner D (2012) Reducing attack surfaces for intra-application communication in android. In: Proceedings of the second ACM workshop on security and privacy in smartphones and mobile devices, SPSM ’12. ACM, New York, pp 69–80. https://doi.org/10.1145/2381934.2381948
Kim S, James Whitehead Jr E, Zhang Y (2008) Classifying software changes: clean or buggy? IEEE Trans Softw Eng 34(2):181–196
Lal S, Sureka A (2012) Comparison of seven bug report types: a case-study of google chrome browser project. In: 2012 19th asia-pacific software engineering conference, vol 1, pp 517–526. https://doi.org/10.1109/APSEC.2012.54
Lee S, Hwang S, Ryu S (2017) All about activity injection: Threats, semantics, and detection. In: Proceedings of the 32nd IEEE/ACM international conference on automated software engineering, ASE 2017. IEEE Press, Piscataway, pp 252–262. http://dl.acm.org/citation.cfm?id=3155562.3155597
Li GK (2010) Computing inter-rater reliability and its variance in the presence of high agreement. Br J Math Stat Psychol 61(1):29–48. https://doi.org/10.1348/000711006X126600
Linares-Vásquez M, Bavota G, Escobar-Velásquez C (2017) An empirical study on android-related vulnerabilities. In: Proceedings of the 14th international conference on mining software repositories, MSR ’17. IEEE Press, Piscataway, pp 2–13. https://doi.org/10.1109/MSR.2017.60
LLC PI (2014) The security impact of mobile device use by employees. Tech. rep., Ponemon Institute
Lu L, Li Z, Wu Z, Lee W, Jiang G (2012) Chex: statically vetting android apps for component hijacking vulnerabilities. In: ACM Conference on computer and communications security, pp 229–240
Mazuera-Rozo A, Bautista-Mora J, Linares-Vásquez M, Rueda S, Bavota G (2017) Replication package: “The Android OS Stack and its Vulnerabilities: An Empirical Study”. http://ml-papers.gitlab.io/android.vulnerabilities-2017/appendix/
Mell P, Scarfone K, Romanosky S (2007) A Complete Guide to the Common Vulnerability Scoring System Version 2.0, 2.0 edn
MITRE (2017a) Cwe-120: Buffer copy without checking size of input (‘classic buffer overflow’). https://cwe.mitre.org/data/definitions/120.html
MITRE (2017b) Cwe-121: Stack-based buffer overflow. https://cwe.mitre.org/data/definitions/121.html
MITRE (2017c) Cwe-122: Heap-based buffer overflow. https://cwe.mitre.org/data/definitions/122.html
MITRE (2017d) Cwe-190: Integer overflow or wraparound. https://cwe.mitre.org/data/definitions/190.html
MITRE (2017e) Cwe-201: Information exposure through sent data. https://cwe.mitre.org/data/definitions/201.html
MITRE (2017f) Cwe-275: Permission issues. https://cwe.mitre.org/data/definitions/275.html
MITRE (2017g) Cwe-296: Improper following of a certificate’s chain of trust. https://cwe.mitre.org/data/definitions/296.html
MITRE (2017h) Cwe-326: Inadequate encryption strength. https://cwe.mitre.org/data/definitions/326.html
MITRE (2017i) Cwe-327: Use of a broken or risky cryptographic algorithm. https://cwe.mitre.org/data/definitions/327.html
MITRE (2017j) Cwe-415: Double free. https://cwe.mitre.org/data/definitions/415.html
MITRE (2017k) Cwe-787: Out-of-bounds write. https://cwe.mitre.org/data/definitions/787.html
MITRE (2017l) Cwe-840: Business logic errors. https://cwe.mitre.org/data/definitions/840.html
MITRE (2017m) Cwe-862: Missing authorization. https://cwe.mitre.org/data/definitions/862.html
MITRE (2017n) Cwe-909: Missing initialization of resource. https://cwe.mitre.org/data/definitions/909.html
MITRE (2017o) Cwe-94: Improper control of generation of code (’code injection’). https://cwe.mitre.org/data/definitions/94.html
MITRE (2017p) Common weakness enumeration http://cwe.mitre.org/
MITRE (2017q) Cve details Android vulnerabilities. https://www.cvedetails.com/product/19997/Google-Android.html
MITRE (2017r) Cve details. https://www.cvedetails.com/
Morales LV, Rueda SJ (2015) Meaningful permission management in android. IEEE Lat Am Trans 13(4):1160–1166. https://doi.org/10.1109/TLA.2015.7106371
Nickinson P (2015) The ’stagefright’ exploit: what you need to know. http://www.androidcentral.com/stagefright
NIST (2015) Common vulnerability scoring system calculator version 2. https://nvd.nist.gov/vuln-metrics/cvss/v2-calculator
NIST (2017) Nvd data feeds http://nvd.nist.gov/download.cfm#{RSS}
Novak E, Tang Y, Hao Z, Li Q, Zhang Y (2015) Physical media covert channels on smart mobile devices. In: Proceedings of the 2015 ACM international joint conference on pervasive and ubiquitous computing, UbiComp ’15. ACM, New York, pp 367–378. https://doi.org/10.1145/2750858.2804253
Park Y, Reeves DS (2013) Deriving common malware behavior through graph clustering. Comput Secur 39(PART B):419–430. https://doi.org/10.1016/j.cose.2013.09.006
Ren C, Zhang Y, Xue H, Wei T, Liu P (2015) Towards discovering and understanding task hijacking in android. In: Proceedings of the 24th USENIX conference on security symposium, SEC’15. USENIX Association, Berkeley, pp 945–959. http://dl.acm.org/citation.cfm?id=2831143.2831203
Rust (2013) https://www.rust-lang.org
Sadeghi A, Bagheri H, Malek S (2015) Analysis of android inter-app security vulnerabilities using covert. In: ICSE’15, pp 725–728. http://dl.acm.org/citation.cfm?id=2819009.2819149
Sadeghi A, Bagheri H, Garcia J, Malek S (2016) A taxonomy and qualitative comparison of program analysis techniques for security assessment of android software. IEEE Trans Softw Eng PP(99):1–1. https://doi.org/10.1109/TSE.2016.2615307
Sadeghi A, Jabbarvand R, Malek S (2017) Patdroid: Permission-aware gui testing of android. In: Proceedings of the 2017 11th joint meeting on foundations of software engineering, ESEC/FSE 2017. ACM, New York, pp 220–232. https://doi.org/10.1145/3106237.3106250
Sbîrlea D, Burke MG, Guarnieri S, Pistoia M, Sarkar V (2013) Automatic detection of inter-application permission leaks in android applications. IBM J Res Dev 57(6):2:10–2:10. https://doi.org/10.1147/JRD.2013.2284403 https://doi.org/10.1147/JRD.2013.2284403
Sliwerski J, Zimmermann T, Zeller A (2005) When do changes induce fixes? In: Proceedings of the 2005 International Workshop on Mining Software Repositories
Stefanko L (2015) Aggressive android ransomware spreading in the usa. http://www.welivesecurity.com/2015/09/10/aggressive-android-ransomware-spreading-in-the-usa/
Sufatrio Tan DJJ, Chua TW, Thing VLL (2015) Securing android: a survey, taxonomy, and challenges. ACM Comput Surv 47(4):58:1–58:45. https://doi.org/10.1145/2733306
Thomas DR (2015a) The Lifetime of Android API Vulnerabilities: Case Study on the JavaScript-to-Java Interface (Transcript of Discussion). Springer International Publishing, Cham, pp 139–144. https://doi.org/10.1007/978-3-319-26096-9_14
Thomas DR, Beresford AR, Rice A (2015b) Security metrics for the android ecosystem. In: Proceedings of the 5th annual ACM CCS workshop on security and privacy in smartphones and mobile devices, SPSM ’15. ACM, New York, pp 87–98. https://doi.org/10.1145/2808117.2808118
Tufano M, Watson C, Bavota G, Di Penta M, White M, Poshyvanyk D (2018) An empirical investigation into learning bug-fixing patches in the wild via neural machine translation. In: Proceedings of the 33rd ACM/IEEE international conference on automated software engineering, ASE 2018. ACM, New York, pp 832–837. https://doi.org/10.1145/3238147.3240732
U.S. National Institute of Standards and Technology - NIST (2012) National vulnerability database. http://nvd.nist.gov
U.S. National Institute of Standards and Technology - NIST (2012) Sp 800-30 guide for conducting risk assessments
VisionMobile: Developer economics q1 2014 (2014) State of the developer nation. Tech. rep.
Wang K, Zhang Y, Liu P (2016) Call me back!: Attacks on system server and system apps in android through synchronous callback. In: Proceedings of the 2016 ACM SIGSAC conference on computer and communications security, CCS ’16. ACM, New York, pp 92–103. https://doi.org/10.1145/2976749.2978342
Weichselbaum L, Neugschwandtner M, Lindorfer M, Fratantonio Y, Veen VVD, Platzer C (2012) ANDRUBIS: Android Malware Under The Magnifying Glass. Tech. rep., Vienna University of Technology. https://www.iseclab.org/papers/andrubis_techreport.pdf
wiki. L (2015) Android kernel features. http://elinux.org/Android_Kernel_Features
Wikipedia (2017a) Android version history https://en.wikipedia.org/wiki/Android_version_history
Wikipedia (2017b) Heartbleed https://en.wikipedia.org/wiki/Heartbleed
Wikipedia (2017c) Stagefright https://en.wikipedia.org/wiki/Stagefright_(bug)
Wu L, Grace M, Zhou Y, Wu C, Jiang X (2013) The impact of vendor customizations on android security. In: Proceedings of the 2013 ACM SIGSAC conference on computer & communications security, CCS ’13. ACM, New York, pp 623–634. https://doi.org/10.1145/2508859.2516728
Xiao X, Tillman N, Fahndrich M, DeHalleux J, Moskal M (2012) User-aware privacy control via extended static-information-flow analysis. In: IEEE/ACM international conference on automated software engineering
Xu M, Song C, Ji Y, Shih MW, Lu K, Zheng C, Duan R, Jang Y, Lee B, Qian C, Lee S, Kim T (2016) Toward engineering a secure android ecosystem: a survey of existing techniques. ACM Comput Surv 49(2):38:1–38:47. https://doi.org/10.1145/2963145
You W, Liang B, Shi W, Zhu S, Wang P, Xie S, Zhang X (2016) Reference hijacking: Patching, protecting and analyzing on unmodified and non-rooted android devices. In: Proceedings of the 38th international conference on software engineering, ICSE ’16. ACM, New York, pp 959–970. https://doi.org/10.1145/2884781.2884863
Zaman S, Adams B, Hassan AE (2011) Security versus performance bugs: a case study on firefox. In: Proceedings of the 8th working conference on mining software repositories, MSR’11. ACM, New York, pp 93–102. https://doi.org/10.1145/1985441.1985457
Zhou Y, Jiang X (2012) Android malware genome project. http://www.malgenomeproject.org/
Zhou Y, Jiang X (2012) Dissecting android malware: characterization and evolution. In: 2012 IEEE Symposium on security and privacy, pp 95–109. https://doi.org/10.1109/SP.2012.16
Zuo C, Wu J, Guo S (2015) Automatically detecting ssl error-handling vulnerabilities in hybrid mobile web apps. In: Proceedings of the 10th ACM symposium on information, computer and communications security, ASIA CCS ’15. ACM, New York, pp 591–596. https://doi.org/10.1145/2714576.2714583
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by: Lin Tan
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Mazuera-Rozo, A., Bautista-Mora, J., Linares-Vásquez, M. et al. The Android OS stack and its vulnerabilities: an empirical study. Empir Software Eng 24, 2056–2101 (2019). https://doi.org/10.1007/s10664-019-09689-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10664-019-09689-7




